The Agniane malware is a stealer created to extract and exfiltrate sensitive information from compromised machines. This particular stealer focuses intensely on pilfering cryptocurrency-related data.
What is Agniane Malware?
Once it infiltrates a system, Agniane initiates the collection of device data, including device name, CPU, GPU, RAM, screen resolution, OS version, IP address/geolocation, installed anti-virus software, and more.
As stated earlier, this malware’s objective is to pilfer from cryptocurrency-related platforms, targeting over seventy crypto-extensions and more than ten crypto-wallets. Some of the targeted platforms comprise MetaMask, Binance Chain, Brave Wallet, Coinbase, Equal Wallet, Guarda, Math Wallet, Nifty Wallet, TronLink, and others.
Moreover, Agniane possesses the capability to extract other forms of data. From web browsers, it aims to seize Internet cookies and saved log-in credentials, such as usernames and passwords. Additionally, Agniane sets its sights on data linked to messaging protocols, encompassing sessions from Telegram and Kotatogram, as well as Discord tokens.
Similarly, this program strives to gain access to sessions on the Steam video game service platform, along with targeting OpenVPN information.
Importantly, malware developers often enhance their creations and techniques. Therefore, potential future iterations of the Agniane stealer might encompass additional or different targets, capabilities, or features.
| Name | Agniane Stealer |
| Detection | Trojan:MSIL/Polazert.ADF!MTB |
| Damage | steal sensitive information, including cryptocurrency-related data, from infected devices, leading to financial losses, privacy breaches, and identity theft. |
| Fix Tool | See If Your System Has Been Affected by Agniane Virus |
To sum up, the presence of software like Agniane on devices can result in multiple system infections, grave privacy concerns, data loss, significant financial damages, and identity theft.
Examples of Stealer-Type Malware
Through the examination of thousands of malware samples, we’ve encountered various stealers, including Lumma, RATRUN, Qwixx, RootTeam, and Muggle. Information-stealing software can be tailored to focus on specific details or a wide array of data.
Stealers can also possess diverse functionalities, such as file retrieval, audio/video recording, keylogging, and more. However, regardless of the mode of operation, the presence of malware on a system jeopardizes device integrity and user privacy. Swift removal of all threats upon detection is therefore imperative.
How Did Agniane Infiltrate My Computer?
Cybercriminals frequently employ phishing and social engineering tactics. Malicious programs are often camouflaged as or bundled with regular software or media files. These can take the form of archives (RAR, ZIP, etc.), executables (.exe, .run, etc.), documents (Microsoft Office, Microsoft OneNote, PDFs, etc.), JavaScript, and similar formats. Execution, running, or opening of a malicious file triggers the infection process (i.e., malware download and installation).
The primary channels for malware distribution encompass stealthy drive-by downloads, online scams, malicious attachments/links in spam emails and messages, malvertising, dubious download sources (e.g., freeware and free file-hosting websites, Peer-to-Peer sharing networks, etc.), illegal software activation tools (“cracks”), and fraudulent updates.
Furthermore, some malicious programs can propagate themselves via local networks and removable storage devices (e.g., external hard drives, USB flash drives, etc.).
How Can I Avoid Installing Agniane Malware?
We strongly urge vigilance while browsing, as fraudulent and malicious online content often presents itself as genuine and harmless. Caution is also warranted when dealing with incoming emails and messages. We advise against opening attachments or links from suspicious or irrelevant sources, as they might contain infections.
Another prudent step is to exclusively download content from official and verified sources. Additionally, all programs should be activated and updated using legitimate functions and tools, as third-party sources can potentially harbor malware.
We underscore the importance of having a reputable anti-virus program installed and regularly updated. Security software should be used for routine system scans to identify and remove detected threats. In the event of suspected infection, we recommend running a scan with Gridinsoft Anti-Malware to automatically eliminate any infiltrated malware.
Remove Agniane with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common Stealers as shown from our tests with the software, and we assure you that it can remove Agniane as well as other malware hiding on your computer.
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file.
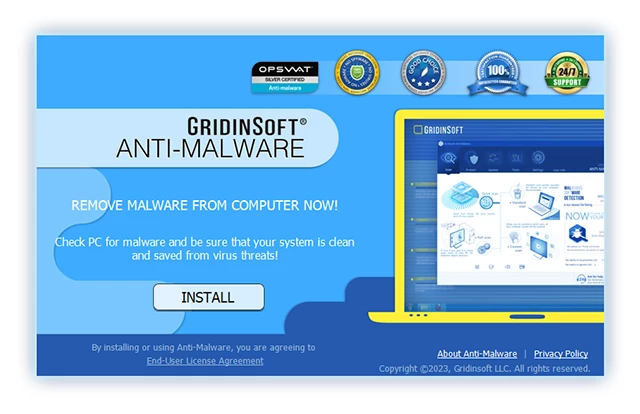
3.Follow the installation setup wizard's instructions diligently.
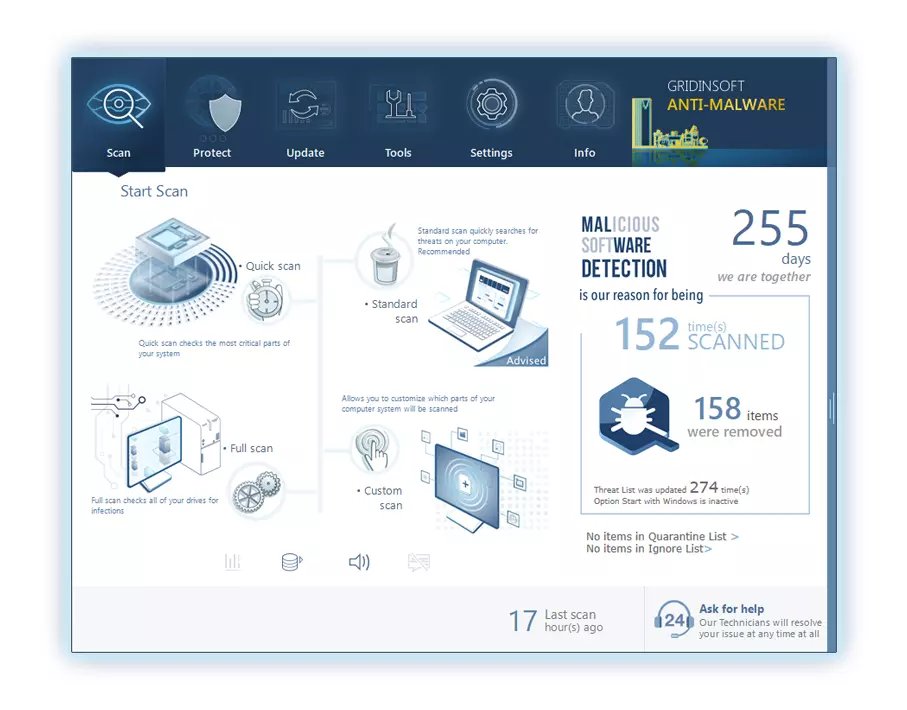
4. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
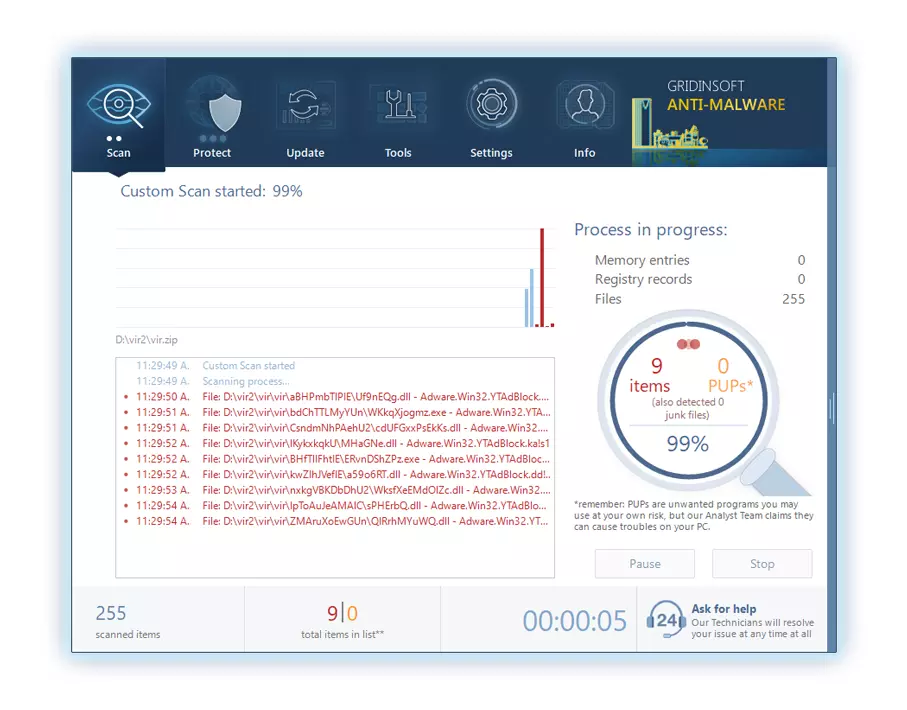
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
5. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
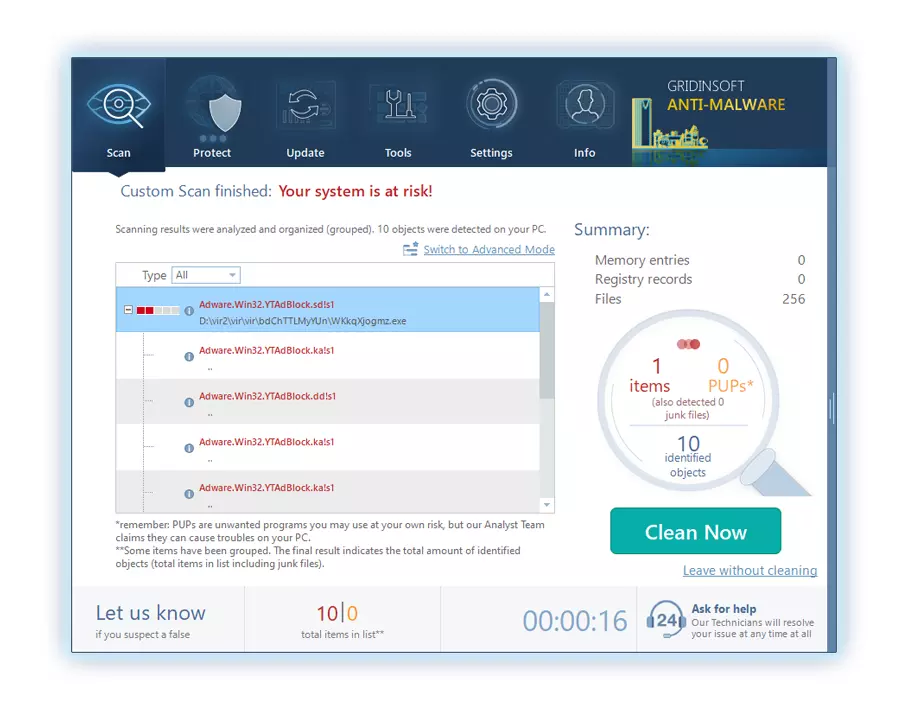
6. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
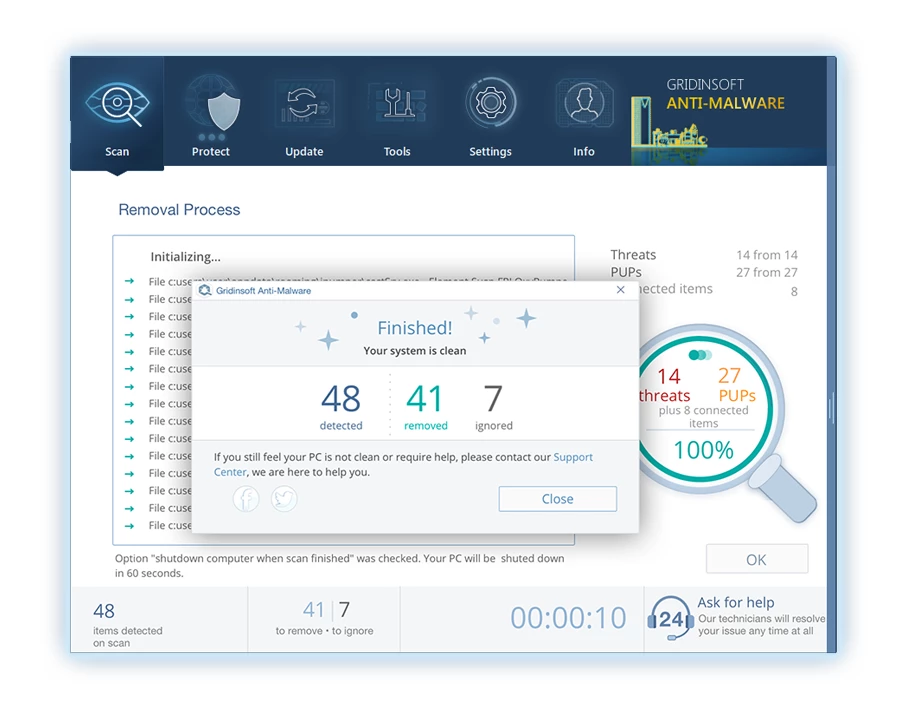
8. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.
Trojan Killer for “Agniane” removal on locked PC
In situations where it becomes impossible to download antivirus applications directly onto the infected computer due to malware blocking access to websites, an alternative solution is to utilize the Trojan Killer application.
There is a really little number of security tools that are able to be set up on the USB drives, and antiviruses that can do so in most cases require to obtain quite an expensive license. For this instance, I can recommend you to use another solution of GridinSoft - Trojan Killer Portable. It has a 14-days cost-free trial mode that offers the entire features of the paid version. This term will definitely be 100% enough to wipe malware out.
Trojan Killer is a valuable tool in your cybersecurity arsenal, helping you to effectively remove malware from infected computers. Now, we will walk you through the process of using Trojan Killer from a USB flash drive to scan and remove malware on an infected PC. Remember, always obtain permission to scan and remove malware from a computer that you do not own.
Step 1: Download & Install Trojan Killer on a Clean Computer:
1. Go to the official GridinSoft website (gridinsoft.com) and download Trojan Killer to a computer that is not infected.
2. Insert a USB flash drive into this computer.
3. Install Trojan Killer to the "removable drive" following the on-screen instructions.
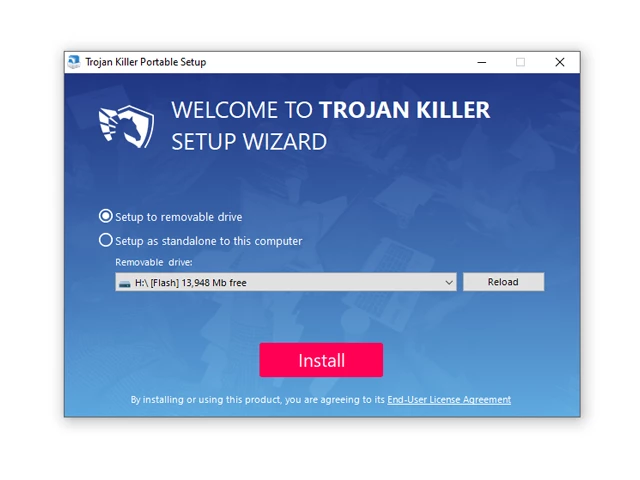
4. Once the installation is complete, launch Trojan Killer.
Step 2: Update Signature Databases:
5. After launching Trojan Killer, ensure that your computer is connected to the Internet.
6. Click "Update" icon to download the latest signature databases, which will ensure the tool can detect the most recent threats.
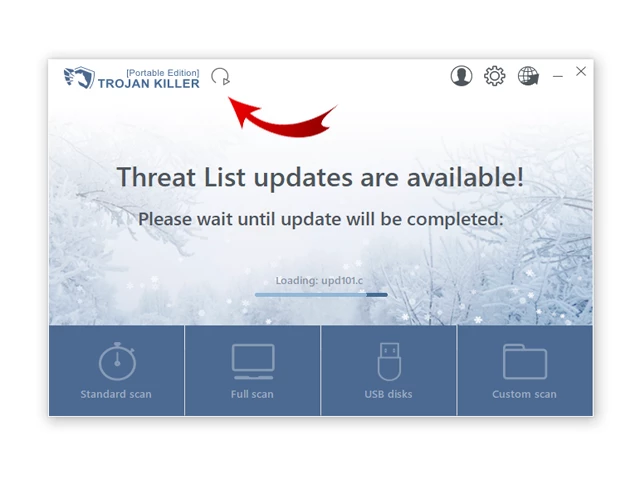
Step 3: Scan the Infected PC:
7. Safely eject the USB flash drive from the clean computer.
8. Boot the infected computer to the Safe Mode.
9. Insert the USB flash drive.
10. Run tk.exe
11. Once the program is open, click on "Full Scan" to begin the malware scanning process.
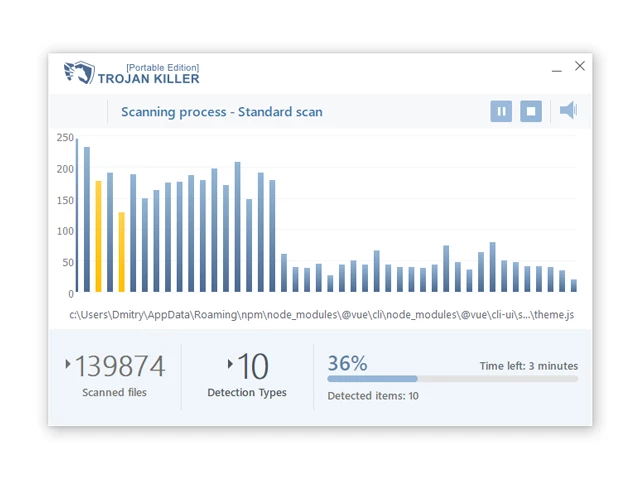
Step 4: Remove Found Threats:
12. After the scan is complete, Trojan Killer will display a list of detected threats.
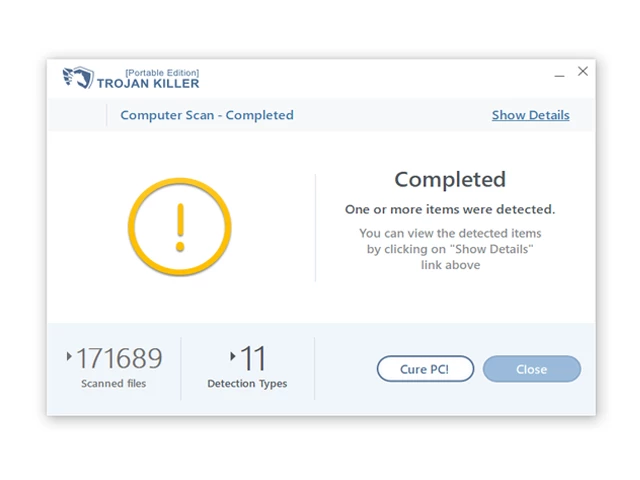
13. Click on "Cure PC!" to remove the identified malware from the infected PC.
14. Follow any additional on-screen prompts to complete the removal process.
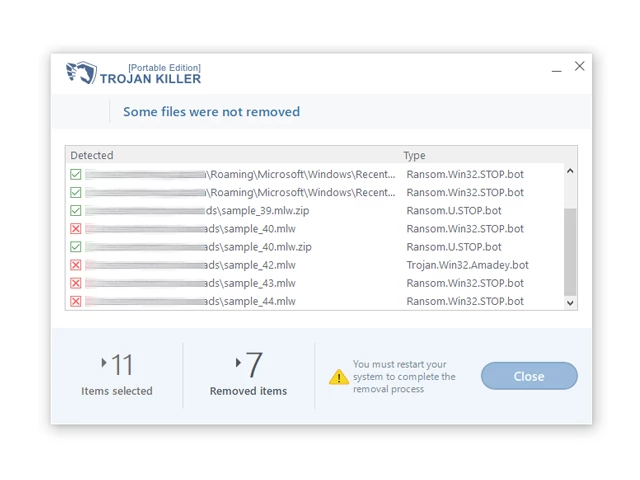
Step 5: Restart Your Computer:
15. Once the threats are removed, click on "Restart PC" to reboot your computer.
16. Remove the USB flash drive from the infected computer.
Congratulations on effectively removing Agniane and the concealed threats from your computer! You can now have peace of mind, knowing that they won't resurface again. Thanks to Gridinsoft's capabilities and commitment to cybersecurity, your system is now protected.
Frequently Asked Questions (FAQ)
Agniane is a type of malicious software, categorized as a “stealer” malware, designed to illicitly gather sensitive information, primarily focusing on cryptocurrency-related data.
Agniane infiltrates systems and begins collecting device-specific information, such as device name, CPU, GPU, RAM, screen resolution, OS version, IP address/geolocation, and installed antivirus software.
Agniane’s main objective is to steal data from cryptocurrency-related platforms. It targets crypto-wallets and crypto-extensions, aiming to extract credentials, session data, and other valuable information.
Agniane focuses on various cryptocurrency platforms, including MetaMask, Binance Chain, Brave Wallet, Coinbase, Equal Wallet, Guarda, Math Wallet, Nifty Wallet, TronLink, and more.
Apart from cryptocurrency-related data, Agniane targets internet cookies, saved login credentials from web browsers, data from messaging protocols (e.g., Telegram, Discord), information from the Steam gaming platform, and OpenVPN credentials.
Agniane’s presence on a device can lead to multiple negative outcomes, including system infections, privacy breaches, data loss, significant financial losses, and identity theft.
Yes, malware developers often enhance their creations. Future iterations of Agniane might have different targets, capabilities, and features.
Agniane is typically spread through phishing and social engineering tactics, often disguised as or bundled with regular software or media files. It can also be distributed via malicious attachments, links, malvertising, and fake updates.
Users should exercise caution while browsing, avoid opening attachments or links from suspicious sources, download only from verified channels, use genuine activation and updating methods, and maintain updated antivirus software.
If you believe your system is infected, it’s crucial to run a scan using reputable anti-malware software like Gridinsoft Anti-Malware to identify and remove the malware promptly.
Agniane poses a significant threat by compromising device security, risking sensitive data exposure, and potentially leading to severe financial and privacy consequences.
As Agniane evolves, it may become more sophisticated, targeting new platforms and data types, making it harder to detect and defend against.
Yes, cybersecurity researchers continuously analyze malware like Agniane to develop better defenses, but staying vigilant and adopting preventive measures is equally important.
Regularly update software and antivirus programs, educate employees about phishing, employ strong security practices, and monitor for suspicious activity to minimize the risk of Agniane infection.
How to Remove Agniane Malware
Name: Agniane
Description: The Agniane malware is a type of malicious software that falls into the category of "stealer" malware. Stealer malware, as the name suggests, is designed with the intention of stealing sensitive and valuable information from infected computers. Agniane specifically focuses on stealing cryptocurrency-related data. Once Agniane infiltrates a system, it starts collecting various types of information from the infected device. This can include device-specific details like the device's name, information about its hardware components (CPU, GPU, RAM), screen resolution, operating system version, IP address, geolocation, installed antivirus software, and more.
Operating System: Windows
Application Category: Malware

