Fortinet developers have warned that a recently patched 0-day vulnerability in FortiOS has been used by attackers in targeted attacks against government and government-related organizations.
Let me remind you that we wrote that A PoC Exploit Is Already Available for a Critical RCE Problem in Fortinet Products, and also that Fortinet Informs Customers about a Critical Vulnerability.By the way, Fortinet research: cybercriminals work Monday to Friday and follow the trends.
On March 7, 2023, Fortinet released patches that fix a serious vulnerability CVE-2022-41328, which allowed attackers to execute arbitrary code and commands. This is a path traversal issue, and the company warned that on FortiOS, this bug could allow a privileged attacker to read and write arbitrary files using specially crafted CLI commands.
The list of vulnerable products includes FortiOS versions 6.4.0-6.4.11, FortiOS versions 7.0.0-7.0.9, FortiOS versions 7.2.0-7.2.3, and all versions of FortiOS 6.0 and 6.2.
The company’s original report did not mention that this vulnerability was a 0-day one and it was actively used in hacker attacks even before the patches were released. Now, Fortinet engineers have reported that CVE-2022-41328 exploits have already been used to break into and disable FortiGate devices owned by one of its customers.
All compromised Fortigate devices reportedly shut down with “System enters error-mode due to FIPS error: Firmware Integrity self-test failed” and failed to boot again.
According to Fortinet, the attackers compromised vulnerable FortiGate devices using FortiManager on the victim’s network, as all devices stopped working at the same time, all were compromised in the same way, and the path traversal exploit was applied simultaneously with the execution of scripts through FortiManager.
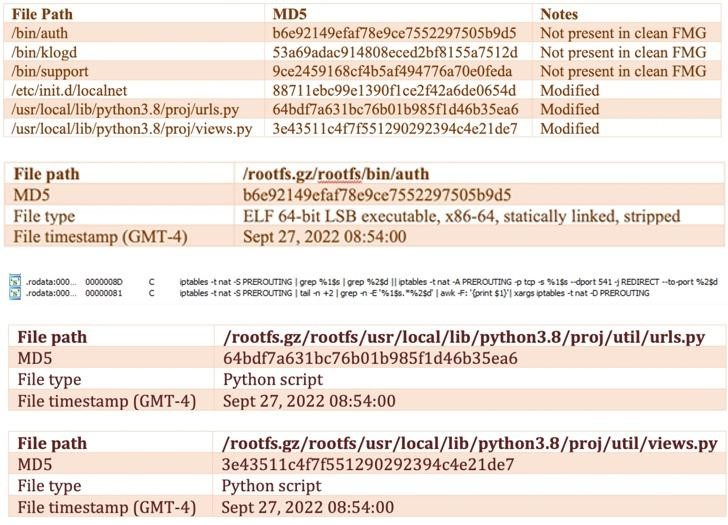
It is assumed that in this way the attackers tried to replace the legitimate Linux utility and run it using the command line.
Further analysis of the incident showed that the attackers modified the firmware image (sbin/init) to include a new payload (/bin/fgfm) so that it always starts before the boot process starts. The malware was designed to establish a connection with a remote server to download files, steal data from a hacked host, and provide remote shell access.
The changes made to the firmware are said to have given attackers permanent access and control, not to mention disabling firmware verification at startup.
Fortinet emphasizes that the attack was targeted and aimed at government or government-related organizations.
The company’s engineers write that given the complexity of the exploit, the attackers are clearly “deeply versed in FortiOS and hardware,” and also have advanced capabilities for reverse engineering various aspects of FortiOS.

