ZDNet reports that according to unnamed sources close to the investigation, the recent hack of Mitsubishi Electric and the subsequent data leak related to the exploitation of the 0-day vulnerability in the Trend Micro antivirus.
Recall that last week it was reported about the compromise of Mitsubishi Electric, one of the world’s largest manufacturers of electronics and electrical equipment. Although the incident occurred last year, on June 28, 2019, a formal internal investigation did not begin until September, and details of what happened were disclosed only recently.In an issued official statement, Mitsubishi Electric does not deny the fact of data theft, it only emphasizes that the hackers did not receive any information about the company’s business partners and defense contracts. So far, the company is still investigating the incident, but, apparently, the attackers swept their tracks by deleting the logs, which slows down the work of investigators”, – says the publication ZDNet.
Hackers stole confidential data from the company’s internal network. In particular, they hacked “dozens of computers and servers in Japan and abroad”, from where they stole about 200 MB of files (mainly business documents, information about employees and job candidates).
After fact of hacking was reported to the public, the Japanese media began to study the situation. According to them, the hacking occurred in the Chinese branch of Mitsubishi Electric, and then spread to 14 other divisions of the company. The intrusion was discovered after Mitsubishi Electric employees noticed a suspicious file on one of the servers.
Also, Japanese media report that the responsibility for this incident lies with the state-sponsored Chinese cyber-espionage group Tick.
The Tick hacking group is known for carrying out a large number of hacking campaigns aimed at targets all over the world over the past few years. Currently, it is unclear if the group also used the OfficeScan zero-day against other targets”, — report ZDNet journalists.
So far, Mitsubishi Electric representatives have not commented on these new details, and known only one technical detail: hackers exploited a vulnerability in one of the antivirus products that the company used.
A source told ZDNet that the attackers used the CVE-2019-18187 bug, a vulnerability related to directory traversal and arbitrary file downloading, in Trend Micro OfficeScan antivirus.
Affected versions of OfficeScan could be exploited by an attacker utilizing a directory traversal vulnerability to extract files from an arbitrary zip file to a specific folder on the OfficeScan server, which could potentially lead to remote code execution (RCE)”, — reported in security recommendations, spread by Trend Micro in October 2019.
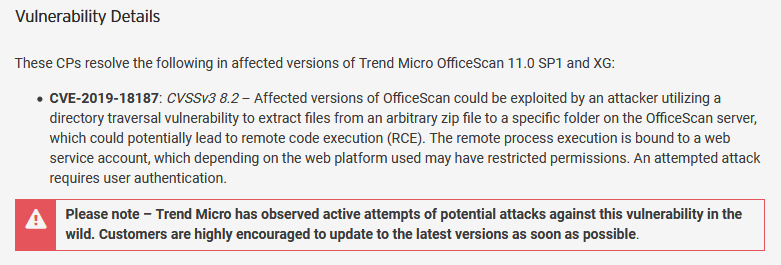
This problem has already been fixed, but in October last year, Trend Micro developers wrote that a directory traversal vulnerability could be used to extract ZIP archive files to a folder on the OfficeScan server, which could potentially lead to remote code execution. Even worse, then Trend Micro warned its customers that hackers already actively used the vulnerability.
While Chinese government hackers were hacking into a Japanese corporation, IT pros from Saudi Arabia, using spyware acquired in Israel, hacked Jeff Bezos’s smartphone. O tempora, o mores!