A group of experts from the Ruhr University in Bochum and the University of Applied Sciences of Münster published a report saying that vulnerabilities in some email clients allowed attacks through mailto links.
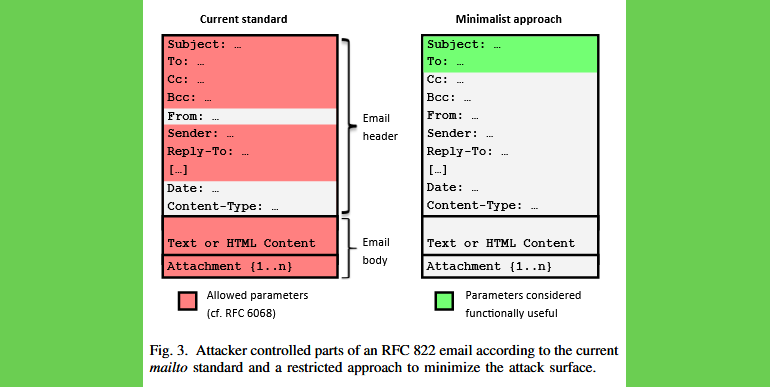
It turned out that some desktop clients have strange mode of work with maito links, which can eventually lead to the theft of local files that can be sent to an attacker as attachments.The root of the problem is in the mode, in which the affected clients implement the RFC6068 standard for the mailto URI scheme.
These links are usually maintained by email clients and browsers, and clicking on them leads a new window for composing an email (or reply), rather than a new page or site”, – remind the researchers.
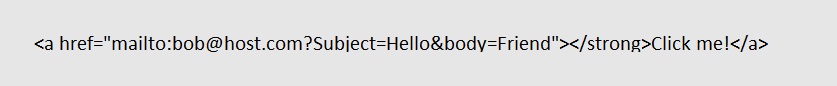
According to RFC6068, mailto links can support various parameters that can be used to prepopulate a new email window with predefined content. For example, a link of the form:
will open a new window for creating an email with the recipient’s email address bob@host.com, the subject will be “Hello” and the text will start with “Friend”.
Although RFC6068 has many configurable options, developers are generally advised to stick to only a few safe options. So, according to a recent report, some email clients support very exotic parameters, which puts their users at risk.
Specifically, the talk is about the attach or attachment parameters, which allow mailto links to open new windows with an already attached file. As a result, attackers can send e-mails containing disguised mailto links to victims, or post malicious mailto links on websites. When user clicks on such links, confidential files can be automatically added to email attachments.
If the user does not notice the attached file, an attacker can get access to sensitive data, including SSH and PGP keys, configuration files, cryptocurrency wallet files, passwords, or important business documents (provided that the paths for these files are known to the hacker).
The researchers tested several scenarios for such an attack:
- using exact paths to the required files;
- using “*” signs to steal several files at once;
- using URL addresses for internal network resources (\\company_domain\file);
- using URLs that lead the victim to the attacker’s SMB server, which leaks the victim’s NTLM hash (\\evil.com\dummyfile);
- using IMAP links to steal all email from the user’s IMAP box (imap:///fetch>UID>/INBOX).
As a result of checking 20 mail clients, it was found that 4 of them are vulnerable to attacks via mailto links (currently all vulnerabilities have already been fixed):
- Evolution, the default GNOME mail client (CVE-2020-11879);
- KMail, the default KDE email client (CVE-2020-11880);
- IBM/HCL Notes for Windows (CVE-2020-4089);
- old versions of Thunderbird for Linux.
Let us also recall that, for example, Raccoon malware can steal data from 60 different applications, including those from email clients.