The cybersecurity researcher, known by the pseudonym Nusenu, claims that he had identified the hack group KAX17, which was controlling thousands of malicious Tor nodes (including entry, intermediate and exit). The expert believes that attackers have been active since at least 2017 and are trying to de-anonymize Tor users.
At its peak, KAX17 was running over 900 malicious servers on the Tor network, which typically has 9,000 to 10,000 active servers per day.Under normal circumstances, servers on the Tor network must contain contact information (such as an email address) so that administrators and law enforcement agencies can contact their operators in the case of misconfiguration or report abuse. Alas, despite this rule, the Tor network often contains servers without contact information, since there is no strict control over this.
Nusenu noted a certain pattern among servers without contact information. For the first time, a researcher drew attention to this back in 2019 and came to the conclusion that activity has continued since at least 2017.
The expert says that this is strange, since most attackers tend to focus on the exit nodes, which allows them to interfere with traffic. For example, an attacker tracked by Nusenu under the ID BTCMITM20 launched thousands of malicious Tor exit nodes to spoof Bitcoin wallet addresses and intercept user payments.
The behaviour of KAX17 led the expert to believe that the group is trying to collect information about users connecting to the Tor network. Nusenu writes in its research that at the some point 16% of users connected to the Tor network through one of the KAX17 servers. The chances of getting to the intermediate node of the attackers was 35%, and to the exit node – 5%.
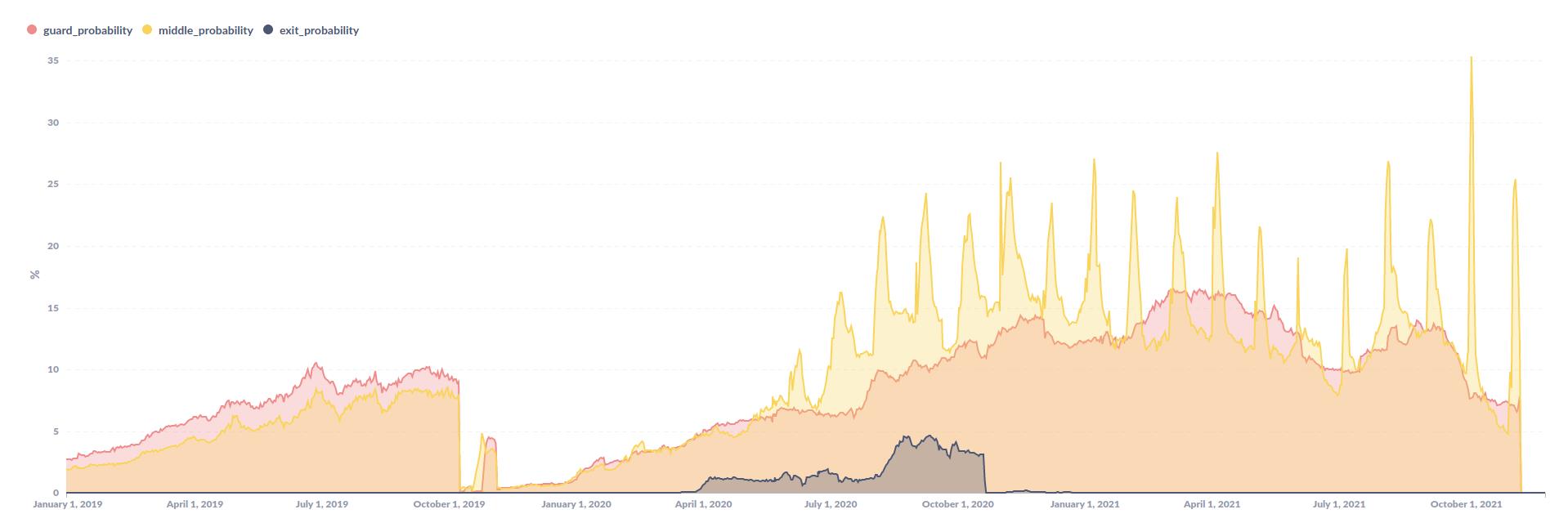
Nusenu says it has been notifying the Tor Project developers since last year, and in the fall of 2020, they removed all of the KAX17 servers. However, the next batch of malicious nodes started working almost immediately after that, and it was not possible to identify it quickly. As a result, several hundred malicious servers were removed only in October and November of this year.
What exactly is KAX17, and who is behind this activity, Nusenu and the Tor Project can only guess. So far, all the signs point to some “government hackers” who are well resourced and can rent hundreds of servers around the world without receiving direct financial benefits from their operation.