IoT Inspector researchers in collaboration with Chip have checked the security of many popular router models from Asus, AVM, D-Link, Netgear, Edimax, TP-Link, Synology, and Linksys that are used by millions of people and found 226 potential vulnerabilities.
Unfortunately, it turned out that many routers are still vulnerable to well-known vulnerabilities, even if they are using the latest firmware versions.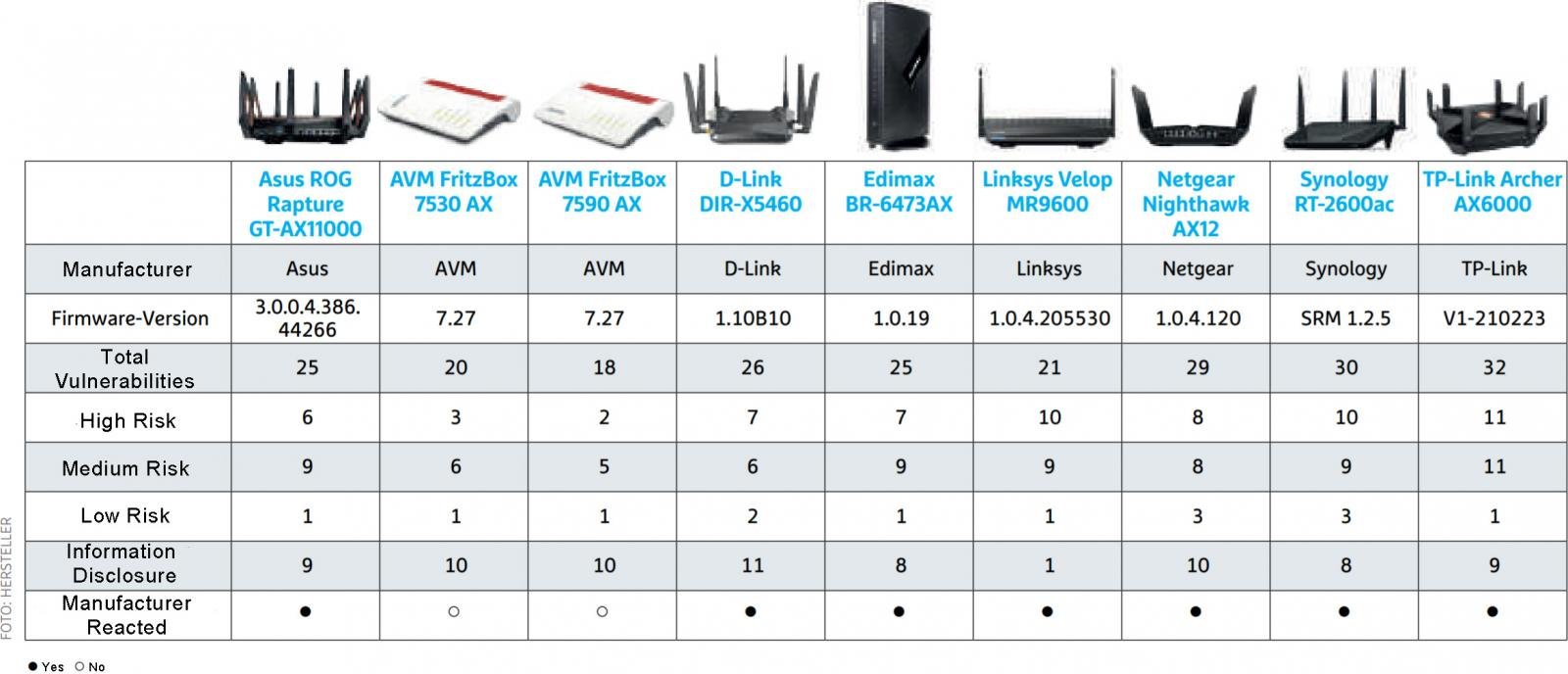
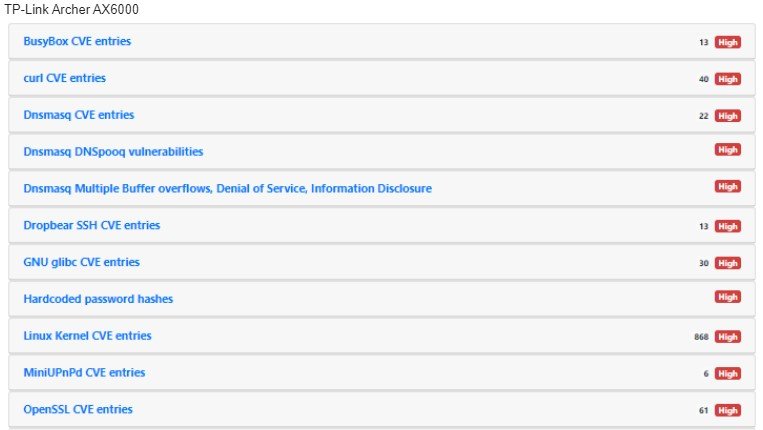
The leaders of bugs were TP-Link Archer AX6000 (32 vulnerabilities) and Synology RT-2600ac (30 vulnerabilities).
While not all of the issues found carry the same risks, the team found some common flaws that are present in most of the models tested:
- outdated Linux kernel in firmware;
- outdated multimedia and VPN features;
- overuse of old BusyBox versions;
- using weak default passwords such as admin;
- the presence of hard-coded credentials (open test).
IoT Inspector CEO Jan Wendenburg notes that one of the most important ways to protect routers is to change the default password when you first set up a device.
All manufacturers whose devices were found to be problematic responded to the study and released fixes. For example, Chip author Jörg Geiger reports that vendors have already fixed most of the problems found.
The researchers told Bleeping Computer that mostly minor vulnerabilities remained unpatched. The experts’ report contains the following data on vendor responses:
Asus studied each point of analysis and provided a detailed answer. Asus has fixed the outdated BusyBox version and also released updates for curl and webserver. They emphasized that the password problems were related to temporary files that are deleted when the process ends, and were not dangerous.
D-Link briefly thanked for the information and posted a firmware update that fixes all mentioned issues.
Edimax didn’t spend a lot of time checking the problems found, but finally they updated firmware that fixed some of the gaps.
Linksys outlined its position on all vulnerabilities that are classified as problems of “high” and “medium” severity. In the future, they do not plan to use default passwords, and also released a firmware update for the remaining bugs.
Netgear said that they worked hard and carefully studied all the problems. Netgear considered some of the “high” severity issues to be less important. Updates for DNSmasq and iPerf have been released, and other issues will be addressed soon.
Synology resolved the issues with a major Linux kernel update. BusyBox and PHP will be updated to newer versions and Synology will have certificates cleared soon. By the way, not only routers benefit from this, but also other devices of the company.
TP-Link. With updates to BusyBox, CURL and DNSmasq, the company has fixed many issues. There is no new kernel update, but more than 50 fixes are planned.
Let me remind you that we also said that Millions of IoT Devices are at Risk due to Bugs Found in Realtek Wi-Fi SDK.

