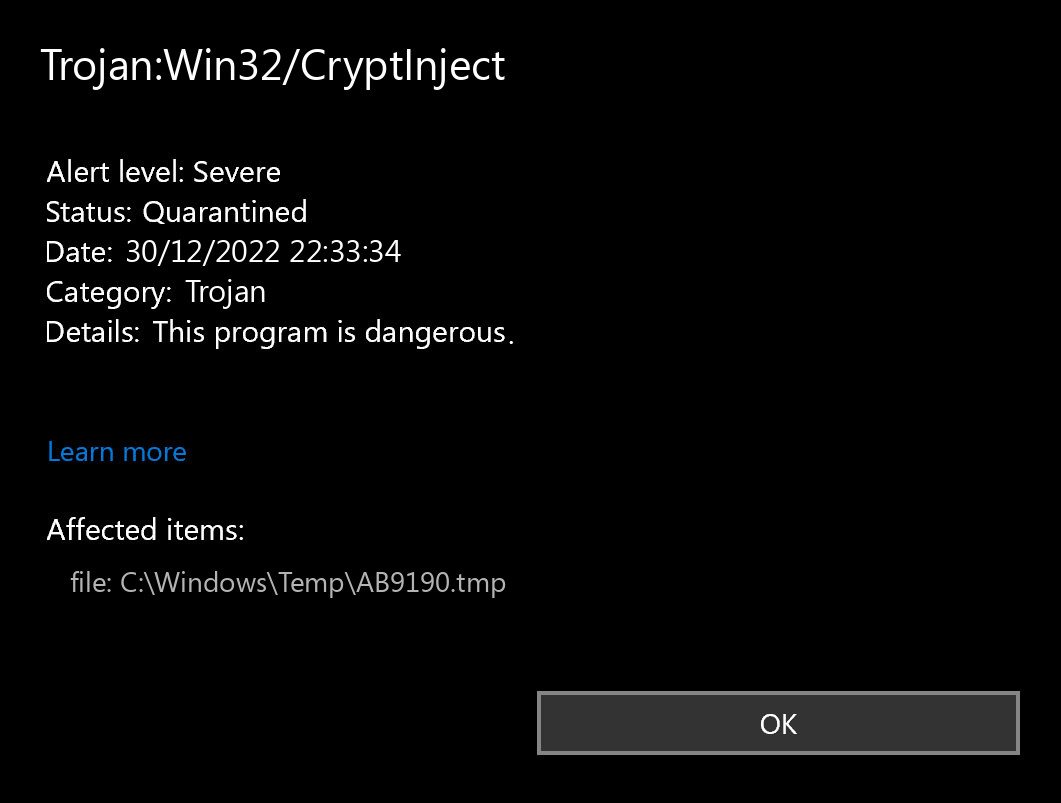
Antivirus software uses the detection name Trojan:Win32/CryptInject to identify a particular variant or occurrence of a Trojan horse malware specifically crafted to inject malicious code into genuine processes on Windows systems.
Trojan horses are a form of malware that masquerade as legitimate files or software to deceive users and carry out nefarious activities on compromised systems. In the instance of Trojan:Win32/CryptInject, its main objective is to inject or alter code within legitimate processes, enabling it to accomplish various malicious intentions.
Trojan:Win32/CryptInject injects code into legitimate processes on Windows systems using various techniques. Here are some common methods employed by CryptInject for code injection:
- Process Hollowing: Trojan:Win32/CryptInject creates a new instance of a legitimate process and replaces its code with its malicious payload. It then starts the modified process, effectively executing the injected code.
- DLL Injection: CryptInject injects a malicious dynamic-link library (DLL) into a legitimate process. The injected DLL is then loaded and executed within the context of the targeted process, allowing the malware to perform its malicious actions.
- Thread Injection: Trojan:Win32/CryptInject creates a new thread within a legitimate process and injects its malicious code into the newly created thread. By executing within the context of a trusted process, the injected code can evade detection and carry out its malicious activities.
- Code Cave Injection: CryptInject searches for unused or empty areas within a legitimate process’s memory space, known as code caves. It then injects its malicious code into these code caves, effectively hiding its presence within the legitimate process.
- Reflective DLL Injection: Trojan:Win32/CryptInject uses a technique called reflective DLL injection, where it loads a DLL directly from memory without writing it to disk. This technique allows the malware to bypass traditional security measures that monitor file access and execution.
These code injection techniques enable CryptInject to blend in with legitimate processes and execute its malicious code, making it challenging to detect and remove.
Trojan:Win32/CryptInject – What is it?
The Trojan:Win32/CryptInject detection you can see in the lower right side is shown to you by Microsoft Defender. That anti-malware software is quite OK at scanning, but prone to be mainly unreliable. It is vulnerable to malware invasions, it has a glitchy interface and bugged malware removal capabilities. Thus, the pop-up which says about the CryptInject is just a notification that Defender has actually detected it. To remove it, you will likely need to use a separate anti-malware program.
The exact Trojan:Win32/CryptInject infection is a very nasty thing. It is present into your PC disguised as a part of something benevolent, or as a part of the application you have got on a forum. After that, it makes all possible steps to weaken your system. At the end of this “party”, it downloads other viruses – ones which are wanted by cybercriminals who control this virus. Hence, it is impossible to predict the effects from CryptInject actions. And the unpredictability is one of the baddest things when it comes to malware. That’s why it is better not to choose at all, and don’t give it even a single chance to complete its task.
Threat Summary:
| Name | CryptInject Trojan |
| Detection | Trojan:Win32/CryptInject |
| Details | CryptInject tool that looks legitimate but can take control of your computer. |
| Fix Tool | See If Your System Has Been Affected by CryptInject Trojan |
Is Trojan:Win32/CryptInject dangerous?
As I have mentioned before, non-harmful malware does not exist. And Trojan:Win32/CryptInject is not an exclusion. This malware alters the system setups, modifies the Group Policies and Windows registry. All of these components are critical for correct system functioning, even when we are not talking about PC safety. Therefore, the virus which CryptInject carries, or which it will download after some time, will squeeze out maximum revenue from you. Cybercriminals can grab your personal information, and then sell it on the Darknet. Using adware and browser hijacker functionality, built in Trojan:Win32/CryptInject malware, they can make money by showing you the ads. Each view gives them a penny, but 100 views per day = $1. 1000 victims who watch 100 banners per day – $1000. Easy math, but sad conclusions. It is a bad choice to be a donkey for crooks.
How did I get this virus?
It is difficult to trace the sources of malware on your PC. Nowadays, things are mixed, and spreading methods used by adware 5 years ago may be utilized by spyware nowadays. However, if we abstract from the exact spreading tactic and will think of why it works, the reply will be really basic – low level of cybersecurity awareness. People click on promotions on strange websites, open the pop-ups they get in their web browsers, call the “Microsoft tech support” assuming that the odd banner that states about malware is true. It is necessary to understand what is legitimate – to avoid misunderstandings when trying to determine a virus.
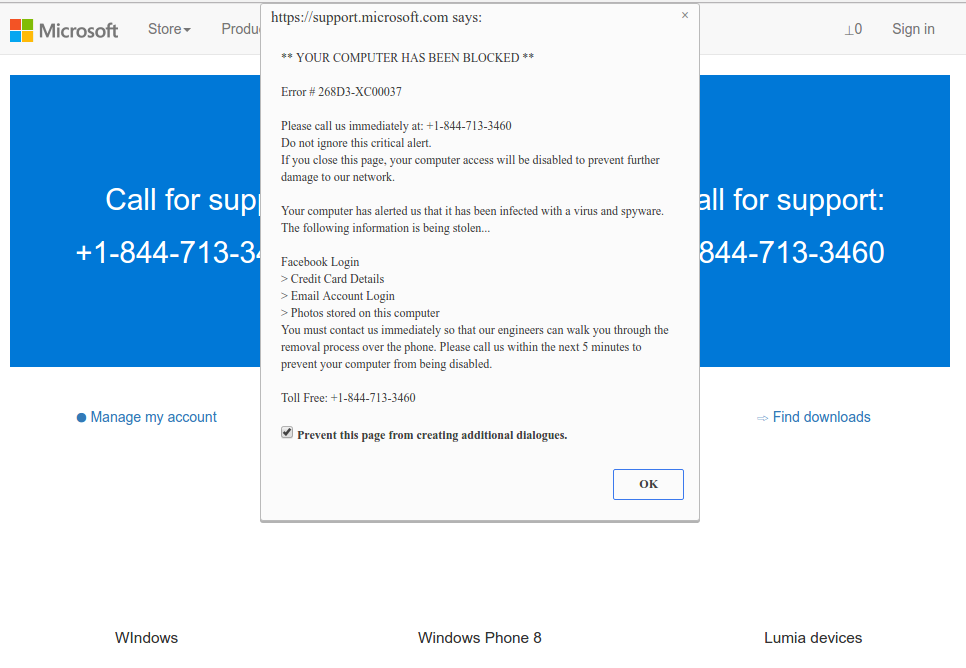
Microsoft Tech Support Scam
Nowadays, there are two of the most common tactics of malware distribution – lure e-mails and also injection into a hacked program. While the first one is not so easy to evade – you should know a lot to recognize a counterfeit – the 2nd one is simple to get rid of: just do not use hacked apps. Torrent-trackers and various other providers of “totally free” applications (which are, actually, paid, but with a disabled license checking) are really a giveaway point of malware. And Trojan:Win32/CryptInject is simply within them.
How to remove the Trojan:Win32/CryptInject from my PC?
Trojan:Win32/CryptInject malware is very hard to erase manually. It stores its files in numerous places throughout the disk, and can restore itself from one of the parts. Furthermore, a range of changes in the registry, networking setups and also Group Policies are quite hard to locate and change to the initial. It is far better to use a specific tool – exactly, an anti-malware app. GridinSoft Anti-Malware will definitely fit the most ideal for virus removal objectives.
Why GridinSoft Anti-Malware? It is very light-weight and has its detection databases updated just about every hour. Additionally, it does not have such problems and exploits as Microsoft Defender does. The combination of these facts makes GridinSoft Anti-Malware suitable for removing malware of any form.
CryptInject Manual Removal
Step 1
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 2
Restart in Safe Mode
Step 3
Identify and terminate files detected as CryptInject
Windows Task Manager may not display all running processes. In this case, please use a third-party process viewer, preferably Process Explorer, to terminate the malware/grayware/spyware file. You may download the said tool here.
If the detected file is displayed in either Windows Task Manager or Process Explorer but you cannot delete it, restart your computer in safe mode. To do this, refer to this link for the complete steps.
If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps.
Step 4
Search and delete these components
There may be some components that are hidden. Please make sure you check the Search Hidden Files and Folders checkbox in the “More advanced options” option to include all hidden files and folders in the search result.
- %AppDataLocal%\GDIPFONTCACHEV1.DAT
- %System Root%\QQ_H40_VC06\rrinstaller\igfxEM.scr
Step 5
Search and delete these folders
Please make sure you check the Search Hidden Files and Folders checkbox in the More advanced options option to include all hidden folders in the search result.
- %System Root%\QQ_H40_VC06\rrinstaller
- %System Root%\QQ_H40_VC06
Step 6
Restart in normal mode and scan your computer.
Remove the viruses with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of CryptInject the default option is “Delete”. Press “Apply” to finish the malware removal.



Trojan:Win32/CryptInject FAQ
Trojan:Win32/CryptInject is a specific detection name used by Windows Defender for a type of Trojan horse malware. It is designed to inject malicious code into legitimate processes on a Windows system, allowing it to execute unauthorized actions, such as downloading additional malware or stealing sensitive information.
Trojan:Win32/CryptInject can infect systems through various means, including malicious email attachments, drive-by downloads from compromised websites, exploit kits, or via file-sharing networks. It often relies on social engineering techniques to trick users into executing the malicious code.
Signs of a Trojan:Win32/CryptInject infection may include system slowdowns, unusual network traffic, unauthorized modifications to files or settings, frequent crashes or system errors, and the presence of unknown or suspicious processes in the task manager.
To remove Trojan:Win32/CryptInject, it is recommended to use a reputable antivirus or anti-malware software. Perform a full system scan and follow the software’s instructions to quarantine or remove any detected threats. Additionally, ensure that your operating system and security software are up to date to prevent future infections.
Manual removal of Trojan:Win32/CryptInject is not recommended for inexperienced users, as it involves identifying and deleting malicious files and registry entries, which can be complex and risky. It is safer and more efficient to rely on specialized security software for thorough and reliable removal.
To reduce the risk of Trojan:Win32/CryptInject infections, follow these preventive measures:
- Keep your operating system, antivirus software, and other applications up to date with the latest security patches.
- Exercise caution when opening email attachments or clicking on suspicious links, especially from unknown or untrusted sources.
- Be cautious when downloading and installing software, ensuring it comes from reputable sources.
- Use a reliable firewall and enable real-time protection provided by your antivirus software.
- Regularly back up your important files to an external storage device or cloud storage service.
If you suspect your system is infected with Trojan:Win32/CryptInject, immediately disconnect from the internet and run a thorough scan using reputable antivirus software. Follow the recommended steps provided by the software to remove the infection. If you are unsure or need further assistance, it is advisable to consult with a professional or seek guidance from a trusted cybersecurity resource.
Remember, maintaining a proactive and layered approach to cybersecurity is crucial in preventing and mitigating the risks posed by threats such as Trojan:Win32/CryptInject.
How to Remove Trojan:Win32/CryptInject Malware
Name: Trojan:Win32/CryptInject
Description: If you have seen a message showing the “Trojan:Win32/CryptInject found”, it seems that your system is in trouble. The CryptInject virus was detected, but to remove it, you need to use a security tool. Windows Defender, which has shown you this message, has detected the malware. However, Defender is not a reliable thing - it is prone to malfunction when it comes to malware removal. Getting the Trojan:Win32/CryptInject malware on your PC is an unpleasant thing, and removing it as soon as possible must be your primary task.
Operating System: Windows
Application Category: Trojan