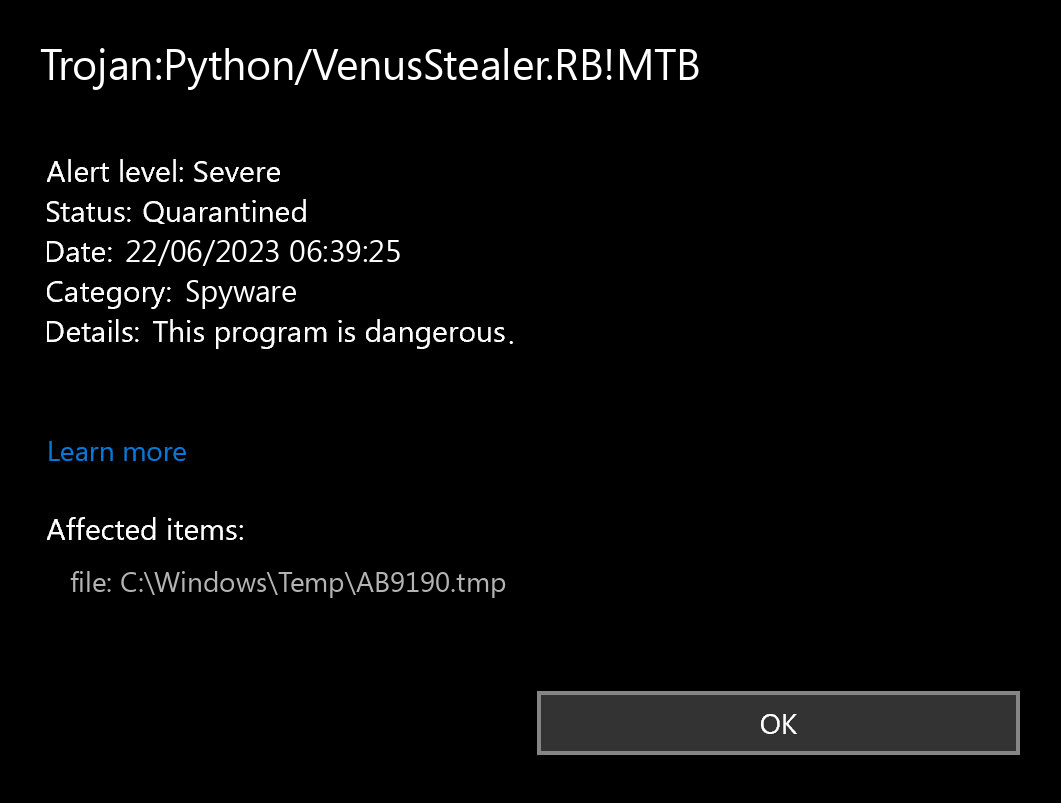
If you spectate the alert of Trojan:Python/VenusStealer.RB!MTB detection, it appears that your computer has a problem. All malicious programs are dangerous, with no exceptions. VenusStealer is malicious software that targets on collecting different types of data from your computer. It applies a lot of hacks to evade security software detection, and uses secured connections to send data to the command server. The activity of this malware usually ends up with losing access to your accounts, and compromising your identity. Moreover, some samples are also able to deliver other malicious programs to the system.
Any type of malware exists with the only target – generate profits on you. And the developers of these things are not thinking about ethicality – they use all possible tactics. Stealing your personal data, getting the comission for the ads you watch for them, utilizing your PC to mine cryptocurrencies – that is not the full list of what they do. Do you want to be a riding equine? That is a rhetorical question.
What does the pop-up with Trojan:Python/VenusStealer.RB!MTB detection mean?
The Trojan:Python/VenusStealer.RB!MTB detection you can see in the lower right corner is demonstrated to you by Microsoft Defender. That anti-malware software is good at scanning, however, prone to be generally unreliable. It is prone to malware invasions, it has a glitchy interface and bugged malware removal capabilities. For this reason, the pop-up which says about the VenusStealer is rather just a notification that Defender has actually identified it. To remove it, you will likely need to make use of a separate anti-malware program.
Having Trojan:Python/VenusStealer.RB!MTB malware in your system is a bad thing from any point of view. The worst problem is that you will not find anything wrong. Key speciality of any spyware is being as secretive as possible. Some VenusStealer samples also can perform self-deletion after gathering all the data available on the computer. After that, it will be almost impossible to uncover the flow of events and understand how your accounts were hacked. Long-residing variants of spyware can target the specific folder in the system or file type. Files grabbed in that way will be put for sale on the Darknet – at one of its numerous forums with stolen data.
Spyware Summary:
| Name | VenusStealer Spyware |
| Detection | Trojan:Python/VenusStealer.RB!MTB |
| Damage | Steal personal data contained in the attacked system. |
| Similar | [LINK1], [LINK2], [LINK3], [LINK4], [LINK5], [LINK6], [LINK7], [LINK8] |
| Fix Tool | See If Your System Has Been Affected by VenusStealer Spyware |
Is Trojan:Python/VenusStealer.RB!MTB dangerous?
As I said before, any malware is harmful. And Trojan:Python/VenusStealer.RB!MTB is not even close to being more annoying than dangerous. The most deceptive characteristic of this malware is the fact you cannot see its activity in any way, other than with the use of anti-malware software scanning. And while you are having no clue, crooks who implemented their nasty thing to your PC are starting to count the money. Darknet forums offer numerous opportunities to sell spyware logs for a large sum – especially when these logs are newly-collected. And you’d better not imagine what will happen to your accounts when other rascals will put their hands on your credentials.
However, situation may have much faster turnover. In some cases, hackers are deploying their virus precisely to the user they are attempting to steal from. Spyware is invaluable when it comes to grabbing credentials, and some examples target precisely at online banking accounts or crypto wallets. One may say, giving spyware a run is the same as sending all your money to criminals.
How did I get this virus?
It is difficult to trace the sources of malware on your computer. Nowadays, things are mixed, and distribution methods utilized by adware 5 years ago may be used by spyware nowadays. But if we abstract from the exact distribution way and will think of why it has success, the answer will be quite basic – low level of cybersecurity understanding. Individuals press on ads on weird websites, click the pop-ups they receive in their browsers, call the “Microsoft tech support” thinking that the weird banner that says about malware is true. It is very important to know what is legitimate – to stay away from misunderstandings when trying to figure out a virus.
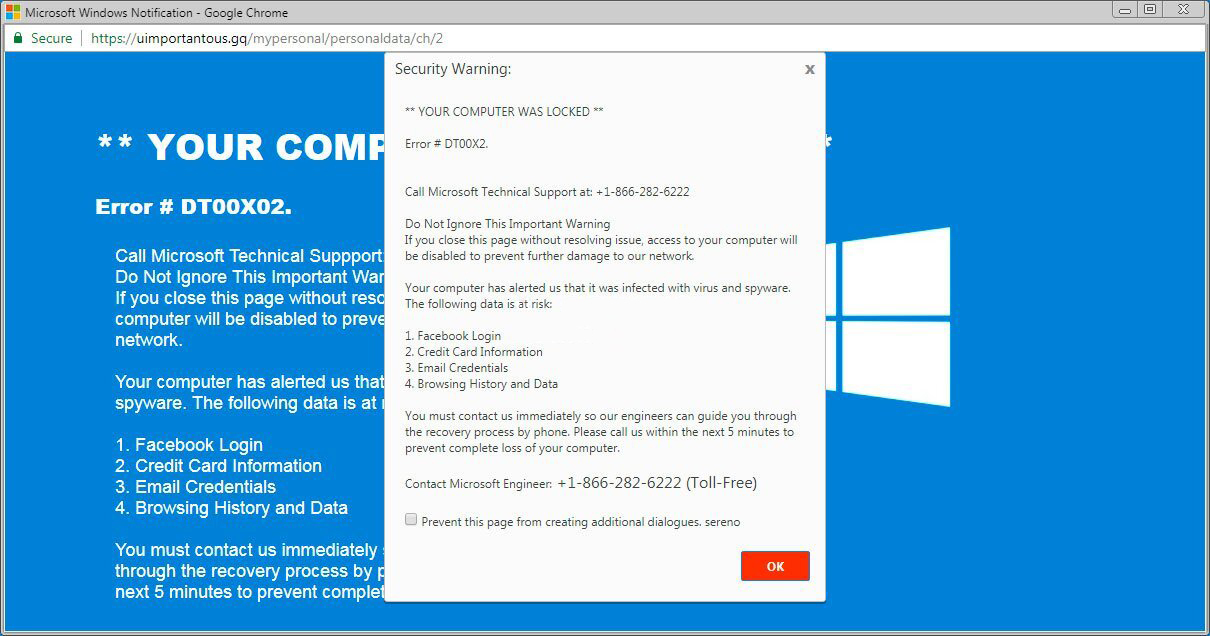
The example of Microsoft Tech support scam banner
Nowadays, there are two of the most widespread methods of malware distribution – lure emails and injection into a hacked program. While the first one is not so easy to evade – you must know a lot to understand a fake – the 2nd one is simple to address: just don’t utilize cracked apps. Torrent-trackers and other sources of “free” applications (which are, in fact, paid, but with a disabled license checking) are just a giveaway point of malware. And Trojan:Python/VenusStealer.RB!MTB is simply within them.
How to remove the Trojan:Python/VenusStealer.RB!MTB from my PC?
Trojan:Python/VenusStealer.RB!MTB malware is incredibly difficult to delete manually. It stores its documents in multiple places throughout the disk, and can restore itself from one of the elements. Additionally, countless modifications in the windows registry, networking settings and Group Policies are pretty hard to identify and return to the initial. It is far better to use a special tool – exactly, an anti-malware tool. GridinSoft Anti-Malware will fit the most ideal for virus elimination reasons.
Why GridinSoft Anti-Malware? It is pretty lightweight and has its detection databases updated practically every hour. In addition, it does not have such bugs and exploits as Microsoft Defender does. The combination of these details makes GridinSoft Anti-Malware ideal for clearing away malware of any form.
Remove the viruses with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of VenusStealer the default option is “Delete”. Press “Apply” to finish the malware removal.



How to Remove Trojan:Python/VenusStealer.RB!MTB Malware

Name: Trojan:Python/VenusStealer.RB!MTB
Description: If you have seen a message showing the “Trojan:Python/VenusStealer.RB!MTB found”, it seems that your system is in trouble. The VenusStealer virus was detected, but to remove it, you need to use a security tool. Windows Defender, which has shown you this message, has detected the malware. However, Defender is not a reliable thing - it is prone to malfunction when it comes to malware removal. Getting the Trojan:Python/VenusStealer.RB!MTB malware on your PC is an unpleasant thing, and removing it as soon as possible must be your primary task.
Operating System: Windows
Application Category: Spyware