What is Trojan.Dropper infection?
In this short article you will locate about the meaning of Trojan.Dropper as well as its negative influence on your computer system. Such ransomware are a type of malware that is elaborated by on the internet fraudulences to require paying the ransom money by a sufferer.
Most of the situations, Trojan.Dropper infection will certainly advise its sufferers to initiate funds transfer for the purpose of reducing the effects of the changes that the Trojan infection has actually introduced to the sufferer’s gadget.
Trojan.Dropper Summary
These adjustments can be as complies with:
- Executable code extraction. Cybercriminals often use binary packers to hinder the malicious code from reverse-engineered by malware analysts. A packer is a tool that compresses, encrypts, and modifies a malicious file’s format. Sometimes packers can be used for legitimate ends, for example, to protect a program against cracking or copying.
- Possible date expiration check, exits too soon after checking local time;
- Creates RWX memory. There is a security trick with memory regions that allows an attacker to fill a buffer with a shellcode and then execute it. Filling a buffer with shellcode isn’t a big deal, it’s just data. The problem arises when the attacker is able to control the instruction pointer (EIP), usually by corrupting a function’s stack frame using a stack-based buffer overflow, and then changing the flow of execution by assigning this pointer to the address of the shellcode.
- A process attempted to delay the analysis task.;
- Reads data out of its own binary image. The trick that allows the malware to read data out of your computer’s memory.
Everything you run, type, or click on your computer goes through the memory. This includes passwords, bank account numbers, emails, and other confidential information. With this vulnerability, there is the potential for a malicious program to read that data.
- Drops a binary and executes it. Trojan-Downloader installs itself to the system and waits until an Internet connection becomes available to connect to a remote server or website in order to download additional malware onto the infected computer.
- Performs some HTTP requests;
- Unconventionial language used in binary resources: Chinese (Simplified);
- Detects Sandboxie through the presence of a library;
- Attempts to modify proxy settings. This trick used for inject malware into connection between browser and server;
- Anomalous binary characteristics. This is a way of hiding virus’ code from antiviruses and virus’ analysts.
- Ciphering the documents situated on the victim’s hard disk drive — so the victim can no more use the data;
- Preventing routine access to the target’s workstation. This is the typical behavior of a virus called locker. It blocks access to the computer until the victim pays the ransom.
Similar behavior
Related domains
| z.whorecord.xyz | Trojan-Ransom.Win32.PornoBlocker.elbv |
| a.tomx.xyz | Trojan-Ransom.Win32.PornoBlocker.elbv |
| wg.200my.com | Trojan-Ransom.Win32.PornoBlocker.elbv |
| open.baidu.com | Trojan-Ransom.Win32.PornoBlocker.elbv |
Trojan.Dropper
The most normal channels whereby Trojan.Dropper Trojans are injected are:
- By ways of phishing emails;
- As an effect of individual ending up on a source that hosts a malicious software application;
As quickly as the Trojan is efficiently injected, it will either cipher the data on the victim’s computer or stop the device from operating in an appropriate way – while additionally positioning a ransom note that mentions the requirement for the sufferers to effect the settlement for the purpose of decrypting the documents or bring back the documents system back to the preliminary condition. In a lot of circumstances, the ransom note will certainly turn up when the customer restarts the COMPUTER after the system has already been damaged.
Trojan.Dropper distribution channels.
In various corners of the globe, Trojan.Dropper grows by leaps and also bounds. However, the ransom money notes and also techniques of obtaining the ransom quantity may vary depending on particular neighborhood (regional) setups. The ransom notes and techniques of obtaining the ransom money amount may differ depending on particular local (local) setups.
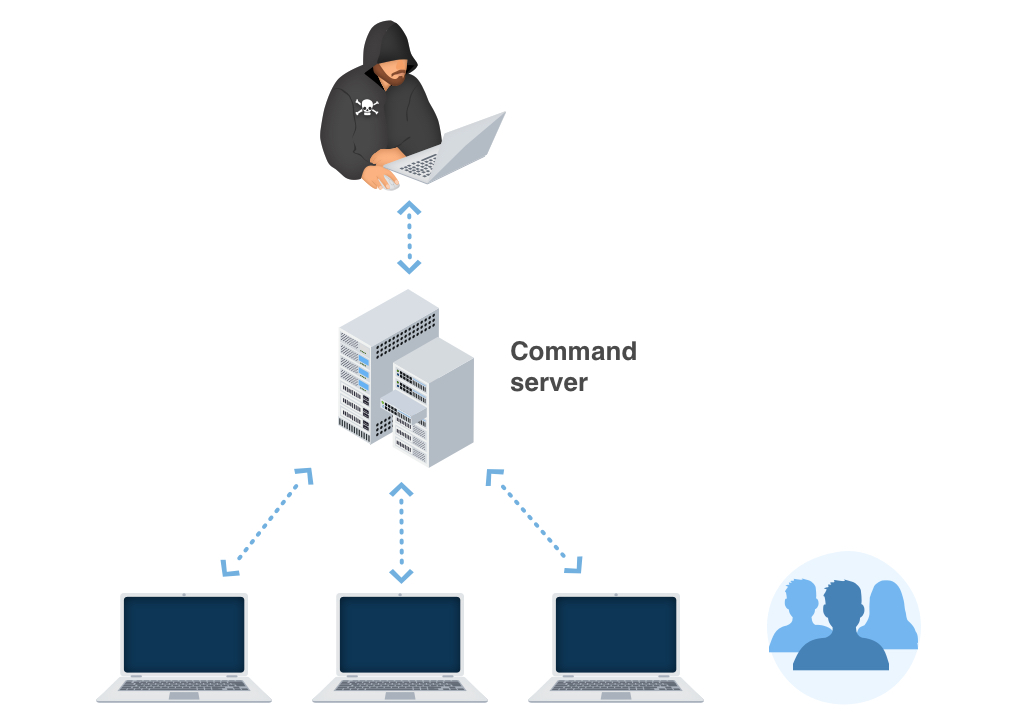
For instance:
Faulty signals concerning unlicensed software application.
In particular locations, the Trojans often wrongfully report having identified some unlicensed applications enabled on the victim’s tool. The alert then requires the customer to pay the ransom.
Faulty declarations about prohibited material.
In countries where software application piracy is much less prominent, this approach is not as reliable for the cyber fraudulences. Alternatively, the Trojan.Dropper popup alert may wrongly claim to be stemming from a law enforcement organization and will report having located kid porn or various other illegal data on the gadget.
Trojan.Dropper popup alert may wrongly claim to be deriving from a regulation enforcement organization and will report having located kid porn or other illegal data on the device. The alert will likewise consist of a requirement for the individual to pay the ransom money.
Technical details
File Info:
crc32: EF276B61md5: a714f152846ced930cd445d8d6ce5d36name: 001my6.9.exesha1: e2fc949f6f042df3c8eeb7b651c2c3a3e47724d2sha256: 9c54cc621ff457e4189aa0eaf6b817e2572f5fa38f9b6bdf9334da95d130befcsha512: 690935d3c82473b871d16f0ba7f7622da0d769f8a682d0a79138c428ab21d593aa12b147bc68d7881cc7972ec487a304eaaa7afe8e339e2e3b34cc8cd7498041ssdeep: 98304:7Z9w9x+bWluEu+ftmJbo35gr51pluDdSdwsYkrWW3IzpyWk:NGibwrftmUir5/YUwCI1yWtype: PE32 executable (GUI) Intel 80386, for MS WindowsVersion Info:
0: [No Data]
Trojan.Dropper also known as:
| GridinSoft | Trojan.Ransom.Gen |
| Bkav | HW32.Packed. |
| DrWeb | Trojan.MulDrop.32183 |
| MicroWorld-eScan | Trojan.GenericKD.31925965 |
| FireEye | Generic.mg.a714f152846ced93 |
| CAT-QuickHeal | Trojan.Occamy |
| McAfee | Artemis!A714F152846C |
| Cylance | Unsafe |
| VIPRE | Trojan.Win32.Generic!BT |
| Sangfor | Malware |
| K7AntiVirus | Trojan ( 000910c91 ) |
| BitDefender | Trojan.GenericKD.31925965 |
| K7GW | Trojan ( 000910c91 ) |
| Cybereason | malicious.2846ce |
| TrendMicro | Trojan.Win32.Dropper.AH |
| BitDefenderTheta | Gen:NN.ZelphiF.33550.3JZ@a8S3lZdb |
| Cyren | W32/Agent.FI.gen!Eldorado |
| Symantec | ML.Attribute.HighConfidence |
| APEX | Malicious |
| Avast | Win32:Malware-gen |
| ClamAV | Win.Malware.Johnnie-6858836-0 |
| GData | Trojan.GenericKD.31925965 |
| Kaspersky | Trojan-Ransom.Win32.PornoBlocker.elbv |
| Alibaba | Ransom:Win32/PornoBlocker.0941dece |
| NANO-Antivirus | Trojan.Win32.PornoBlocker.elczem |
| ViRobot | Trojan.Win32.Z.Pornoblocker.4047748 |
| AegisLab | Trojan.Win32.PornoBlocker.j!c |
| Rising | Trojan.Generic@ML.80 (RDMK:32SG3TKxW1Pm40IqTExJqg) |
| Ad-Aware | Trojan.GenericKD.31925965 |
| Sophos | Mal/Generic-S |
| Comodo | Malware@#qi1ibdyzofb5 |
| Invincea | heuristic |
| McAfee-GW-Edition | BehavesLike.Win32.Dropper.wc |
| Trapmine | malicious.moderate.ml.score |
| CMC | Trojan-Ransom.Win32!O |
| Emsisoft | Trojan.GenericKD.31925965 (B) |
| Ikarus | Trojan.Win32.Skeeyah |
| Jiangmin | Trojan.Qhost.it |
| Webroot | W32.Trojan.GenKD |
| MAX | malware (ai score=100) |
| Endgame | malicious (high confidence) |
| Arcabit | Trojan.Generic.D1E726CD |
| ZoneAlarm | Trojan-Ransom.Win32.PornoBlocker.elbv |
| Microsoft | TrojanDropper:Win32/Agent.DO |
| AhnLab-V3 | Malware/Win32.RL_Generic.R277022 |
| Acronis | suspicious |
| ALYac | Trojan.GenericKD.31925965 |
| VBA32 | BScope.Trojan.Qhost |
| Malwarebytes | Trojan.Dropper |
| Panda | Trj/CI.A |
| ESET-NOD32 | a variant of Win32/TrojanDropper.Agent.OBM |
| TrendMicro-HouseCall | Trojan.Win32.Dropper.AH |
| Tencent | Malware.Win32.Gencirc.10b4108a |
| Yandex | Trojan.PornoBlocker!Yq6j+BwMTzU |
| Fortinet | W32/PornoBlocker.ELBV!tr |
| AVG | Win32:Malware-gen |
| Paloalto | generic.ml |
| CrowdStrike | win/malicious_confidence_80% (W) |
How to remove Trojan.Dropper virus?
Unwanted application has ofter come with other viruses and spyware. This threats can steal account credentials, or crypt your documents for ransom.
Reasons why I would recommend GridinSoft1
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes.2.
Download GridinSoft Anti-Malware.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the install-antimalware-fix.exe file to install GridinSoft Anti-Malware on your system.
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

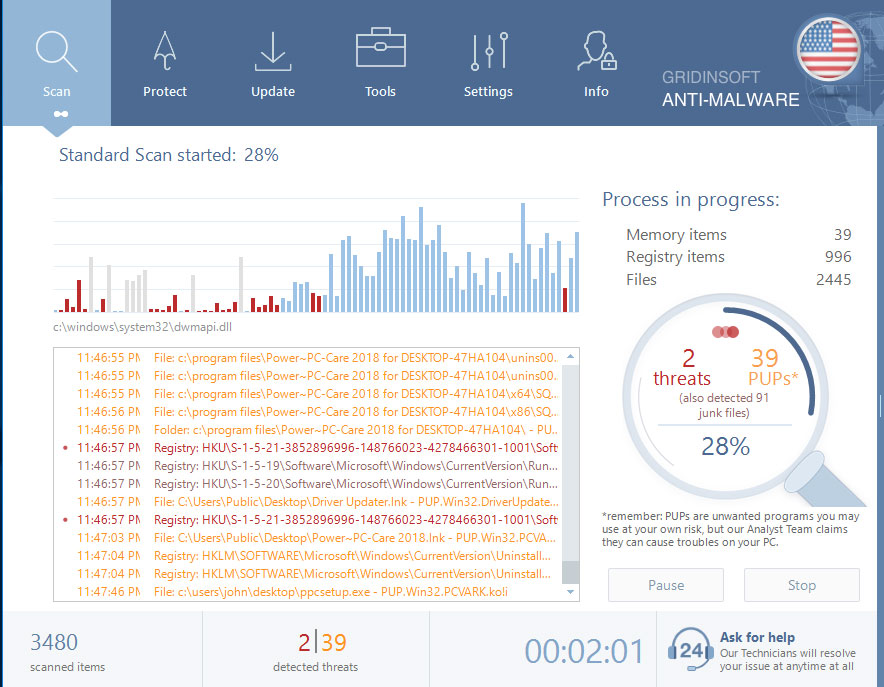
Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Trojan.Dropper files and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
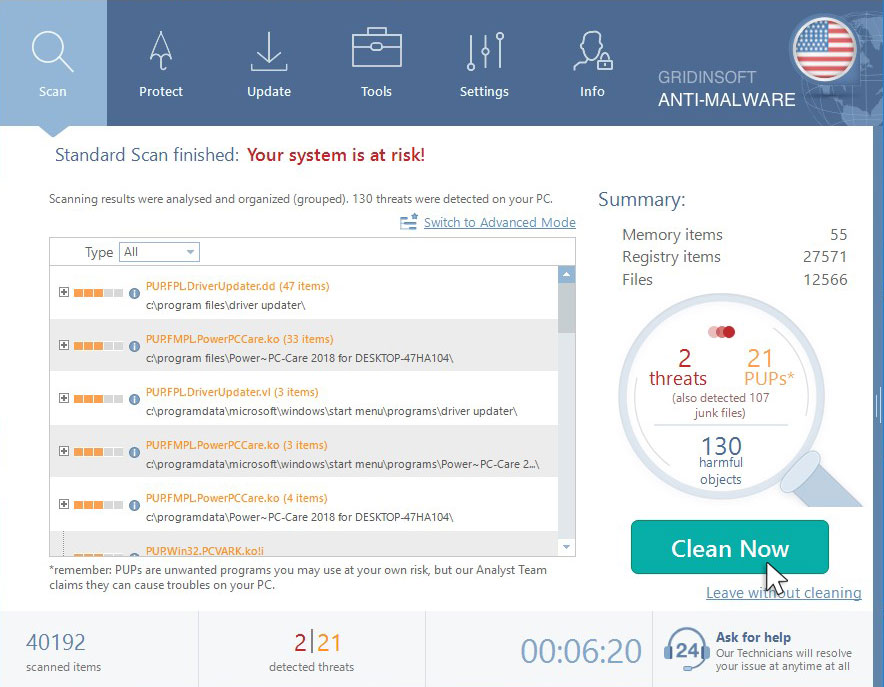
Click on “Clean Now”.
When the scan has finished, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
Are Your Protected?
GridinSoft Anti-Malware will scan and clean your PC for free in the trial period. The free version offer real-time protection for first 2 days. If you want to be fully protected at all times – I can recommended you to purchase a full version:
If the guide doesn’t help you to remove Trojan.Dropper you can always ask me in the comments for getting help.
User Review
( votes)References
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison

![What is the Win32:Evo-gen [Trj] virus?](https://howtofix.guide/wp-content/uploads/2019/11/trojan-ransom-1140x760.jpg)