The Bleeping Computer magazine reports that the Advanced Intelligence information security specialist Vitali Kremez studied the new version of the famous TrickBot malware and found an interesting bug in it, due to which the banker accidentally notified its victims about the infection.
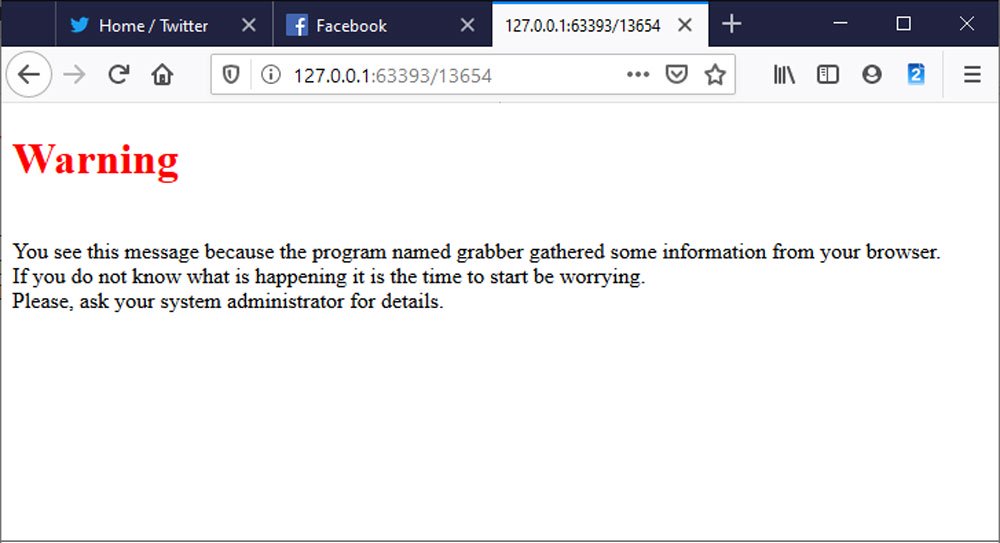
It turned out that the test version of the module for stealing passwords grabber.dll, most likely included in the malware by mistake, warns victims of compromise.So, after loading, this module displays a warning in the default browser. It states that the grabber program collects information from the browser, and the victim urgently needs to contact his system administrator.
Bleeping Computer notes that on Reddit you can already find complaints from users infected with the latest version of TrickBot who are perplexed why Firefox suddenly began to warn them about some grabber program.
The grabber.dll module, as you might guess from its name, is designed to steal passwords and cookies from the browsers Chrome, Edge, Internet Explorer and Firefox. Hackers log into victims’ accounts and can use data stolen in this way.
Vitaly Kremez believes that the TrickBot developers themselves created this module, as part of the code matches the other components of the malware.
Advanced Intelligence assesses with high confidence that this module was likely a test module deployed mistakenly alerting on the malware activity during the testing phase”, — writes Vitali Kremez.
Apparently, hackers checked the new version of malware and simply forgot to remove the test iteration of the module from it when the release took place.
Let me remind you that the TrickBot malware is mainly distributed through spam emails. After installing on the victim’s machine, the malware downloads various additional modules that perform a variety of tasks: stealing the Active Directory Services database, collecting passwords and cookies from the browser, stealing OpenSSH keys, and further distribution throughout the network, including using infected systems for brute force RDP.
Even worse, finally, TrickBot gives Ryuk and Conti ransomware operators access to infected systems. Let me remind you that TrickBot even had its own malicious Android application.
Recommendations & Possible Mitigations
- The immediate disconnect of the affected machine from the network when observed the fraud message as displayed.
- Full password reset from browsers for any internal and external assets.
- Logged-in session reset to prevent reuse of stolen cookies.