The Still Sherpa search hijacker is an illustration of a basic unwanted program; such programs are promoted enormously these days. In this article you will see the comprehensive guidance of “Still Sherpa” hijacker elimination in several methods: utilizing anti-malware software and also hand-operated elimination method.
Still Sherpa – What is it?
“Still Sherpa” search hijacker is a potentially unwanted application (PUA)1, that is spread as a plugin for your web browser. It is usually shared as an add-on for Chrome or Firefox, that helps to search some specific info, as an example, about sport events, make your browser far more safe, allow downloading of any kind of web video, and so on. Also, this app adds the “Managed by your organization” feature (on Chrome browsers).
Nevertheless, the “Still Sherpa” plugin is rather ineffective since all such functions are already built-in to your web browser and/or system. Such marketing mottos are targeted at low-skilled computer users, such as pensioners or schoolchildren. But often even experienced users are getting caught on such an attraction. In certain cases, this hijacker is dispersed along with free software.
Here is a info for the Still Sherpa hijacker
| NAME | Still Sherpa |
| Site | Stillsherpa.com |
| Hosting | AS13335 Cloudflare, Inc. United States, San Francisco |
| Infection Type | Browser Hijacker, Unwanted Application |
| IP Address | 172.67.145.211 |
| Symptoms | Changed search engine; search queries redirection |
| Similar behavior | Find, Justvideosearch, Adblock |
| Fix Tool | To remove possible virus infections, try to scan your PC |
How harmful is Still Sherpa hijacker?
Besides its impracticality, Still Sherpa hijacker is also quite unsafe for web browser utilization. It modifies your search engine to its specific – Stillsherpa.com, and also changes your background, adding its watermark on your wallpaper (or, sometimes, changing it to default with the specified symbol).
Aside from viewable adjustments done by Still Sherpa hijacker, you might see that some of your search inquiries are redirecting to the unknown web pages, full of links and ads – so-called doorway sites. Such websites can include links for malware downloads. The possibility of redirecting boosts if you attempt to launch Google search page forcibly.
But all these actions are much more annoying than really hazardous. The largest threat, primarily for people who have a great deal of secret information in their browsers, is embedded in data collecting capabilities. Cookie files, chats, often-visited web pages, as well as other activities are simply collected by Still Sherpa hijacker.
How to remove Still Sherpa search hijacker?
- Download and install GridinSoft Anti-Malware.
- Open GridinSoft Anti-Malware and perform a “Standard scan“.
- “Move to quarantine” all items.
- Open “Tools” tab – Press “Reset Browser Settings“.
- Select proper browser and options – Click “Reset”.
- Restart your computer.
Browser hijackers are usually quite easy to remove. In most cases, they have a separate app that can be seen in the list of installed applications. Because of the certain distribution tactic of Still Sherpa hijacker, it can be easily tracked and erased by hand. However, if you got Still Sherpa in the bundle with a free applications, your system can be contaminated with a lot more severe malware – trojans, spyware and even ransomware. That’s why I’d suggest you make use of anti-malware programs to delete the Still Sherpa PUA and all various other malware.
You can make use of Microsoft Defender2 – it is capable of discovering and clearing away different malware, including named hijacker. Nevertheless, major malware, that can be present on your personal computer in the specified situation, can disable the Windows antimalware program by editing the Group Policies. To prevent such scenarios, it is far better to utilize GridinSoft Anti-Malware.
To detect and eliminate all unwanted programs on your computer with GridinSoft Anti-Malware, it’s better to utilize Standard or Full scan. Quick Scan is not able to find all the malicious programs, because it checks only the most popular registry entries and folders.
You can spectate the detected viruses sorted by their possible hazard during the scan process. But to perform any actions against malicious apps, you need to hold on until the scan is over, or to stop the scan.
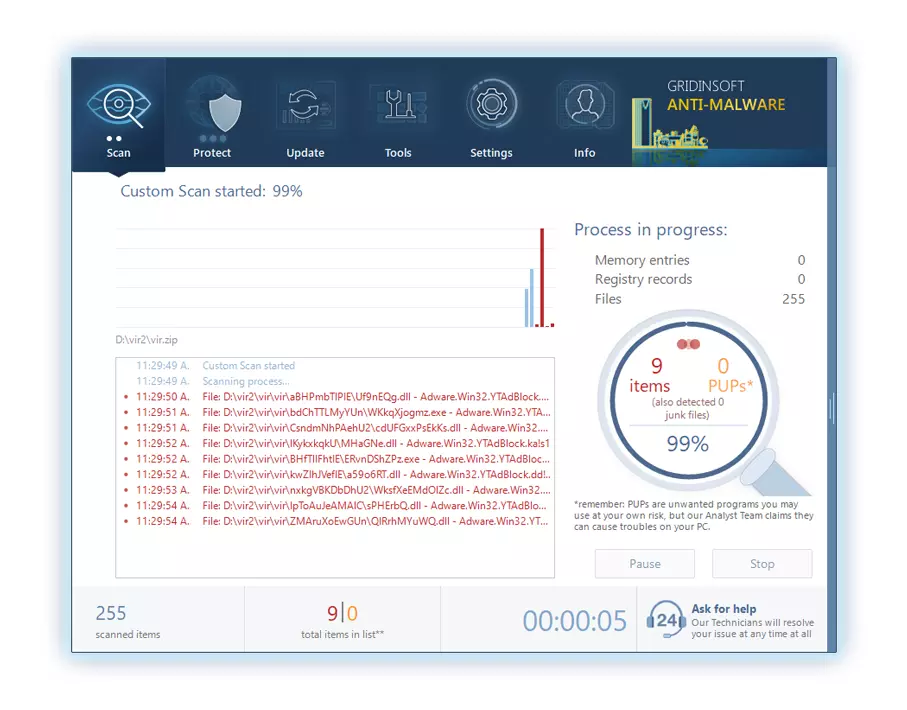
To set the action for every detected virus or unwanted program, click the arrow in front of the name of the detected malicious app. By default, all malware will be removed to quarantine.
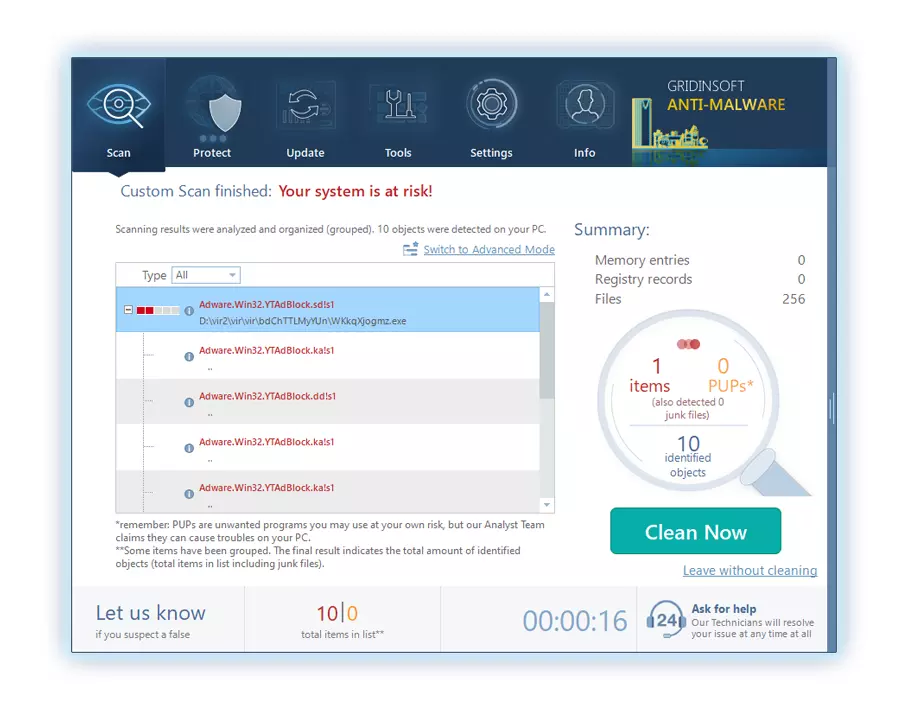
Reverting browser settings to original ones
To revert your browser settings, you need to use the Reset Browser Settings option. This action is not able to be intercepted by any malicious program, hence, you will surely see the result. This action can be found in the Tools tab.
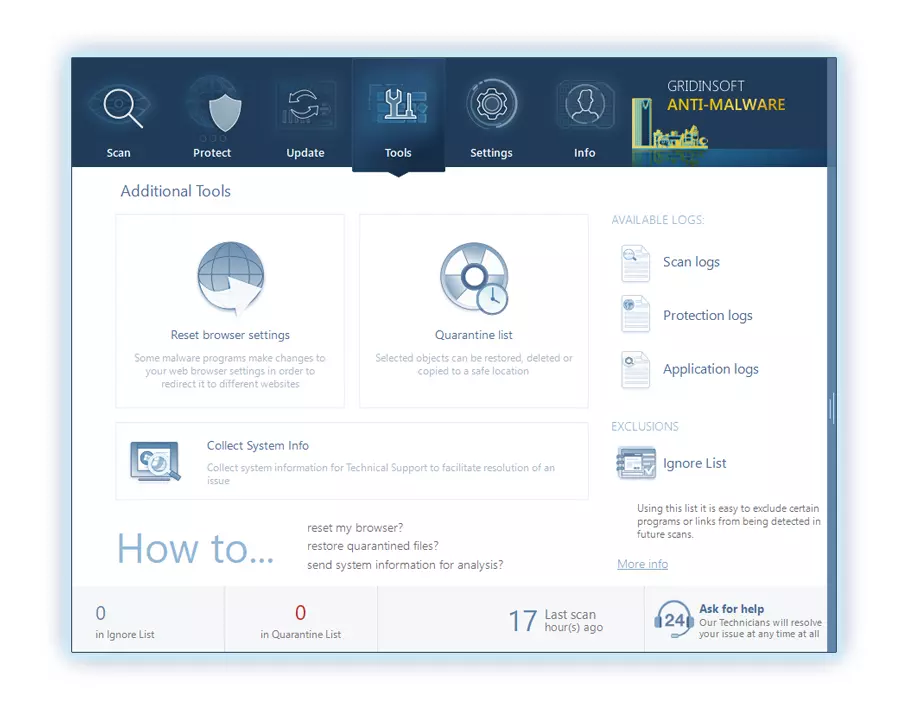
After pressing the Reset Browser Settings option, the menu will be shown, where you can choose, which settings will be reverted to the original.
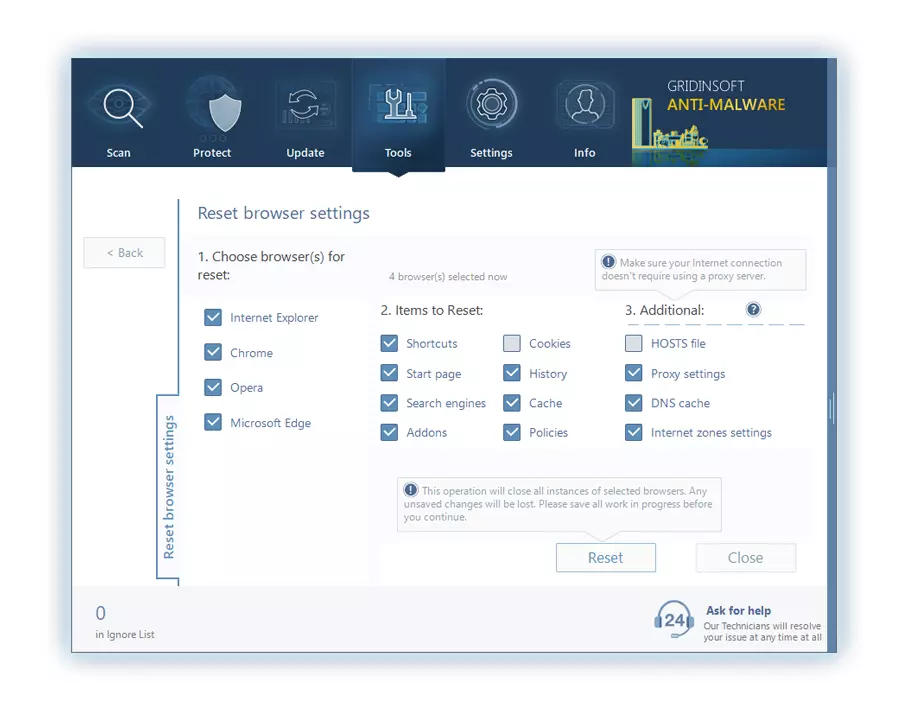
Deleteing Still Sherpa hijacker manually
Besides using anti-malware software for browser restoration, you may choose the “Reset browser settings” function, which is usually embedded in all popular browsers.
To reset Edge, do the following steps :
- Open “Settings and more” tab in upper right corner, then find here “Settings” button. In the appeared menu, choose “Reset settings” option :
- After picking the Reset Settings option, you will see the following menu, stating about the settings which will be reverted to original :
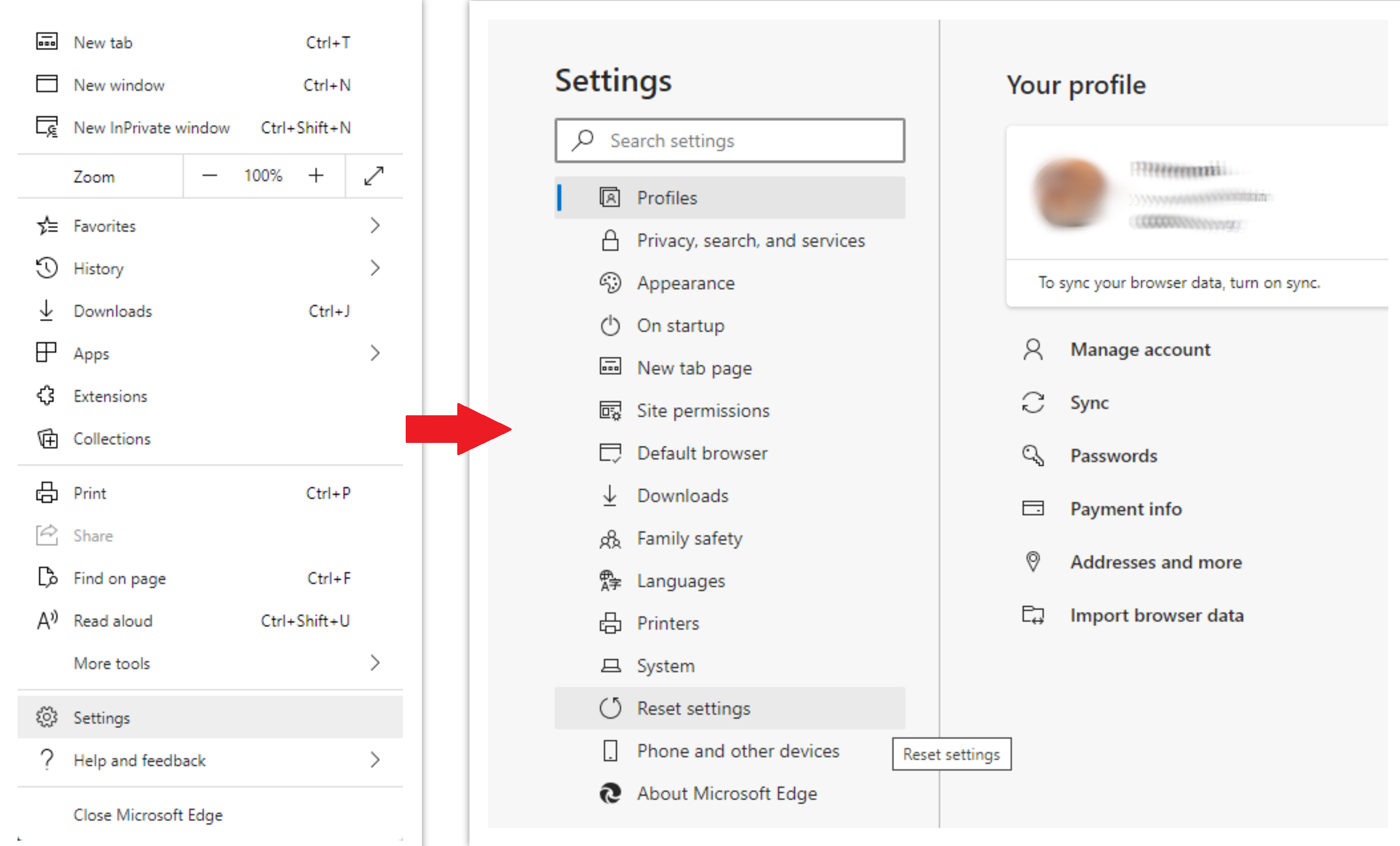
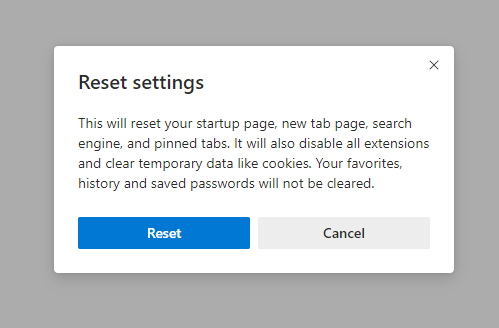
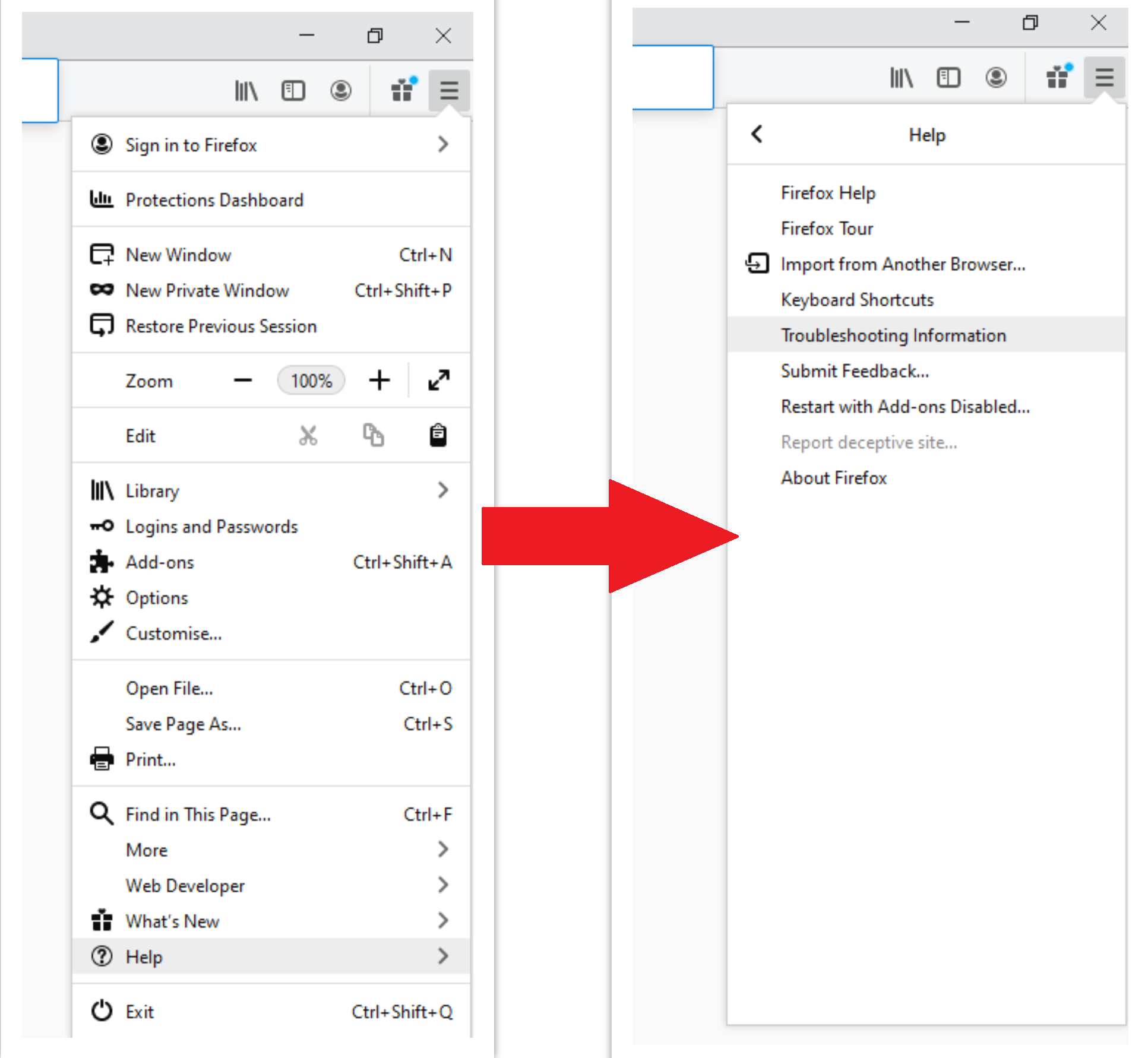
For Mozilla Firefox, do the next actions :
- Open Menu tab (three strips in upper right corner) and click the “Help” button. In the appeared menu choose “troubleshooting information” :
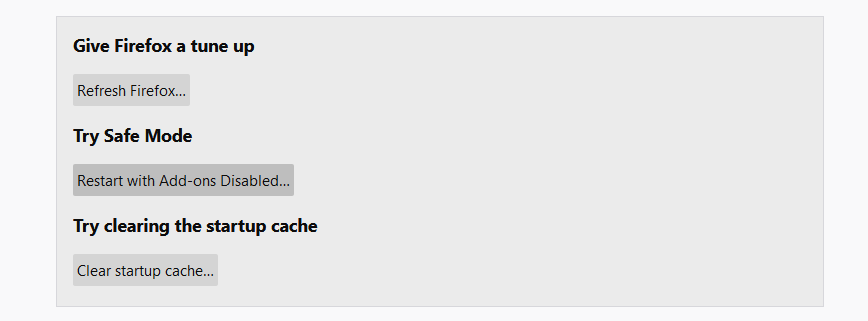
- In the next screen, find the “Refresh Firefox” option :
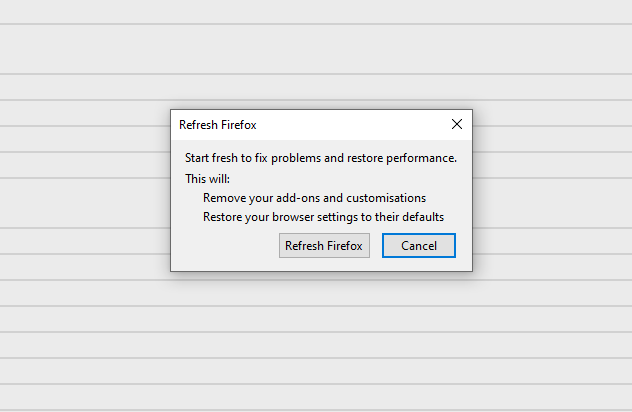
After choosing this option, you will see the next message :
If you use Google Chrome
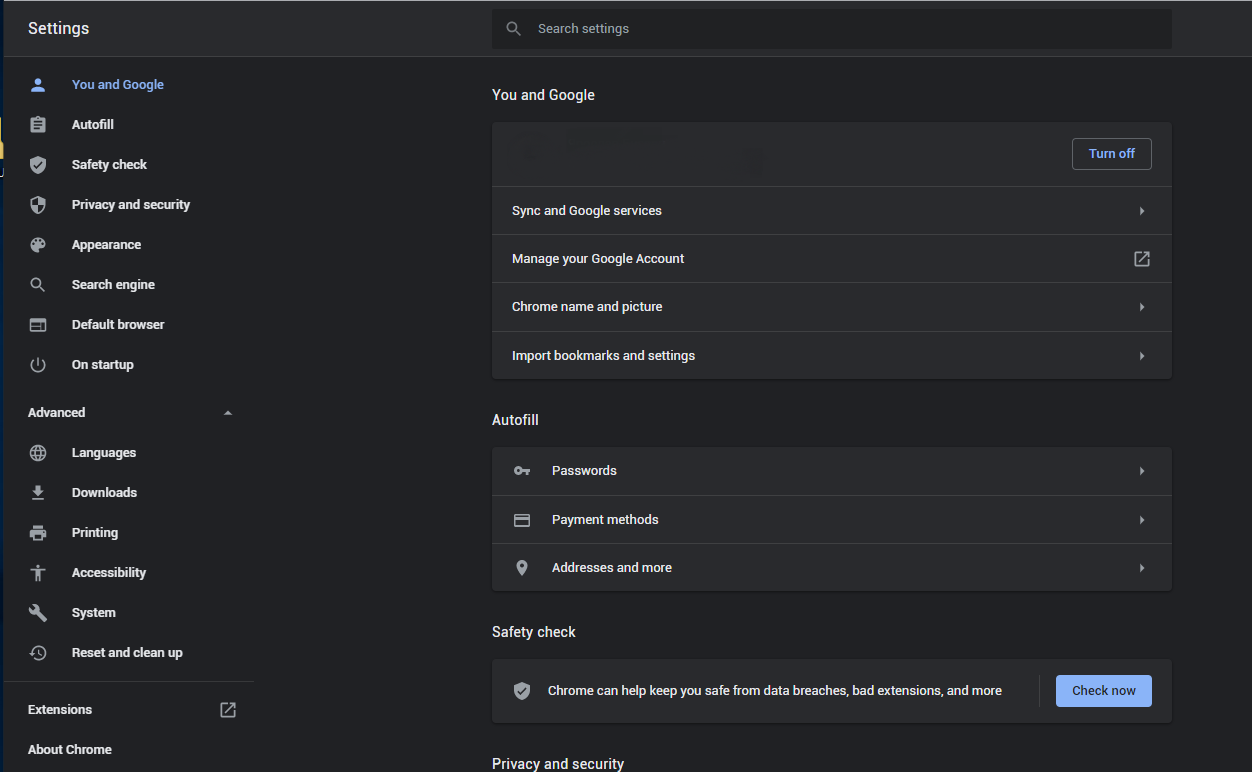
- Open Settings tab, find the “Advanced” button. In the extended tab choose the “Reset and clean up” button :
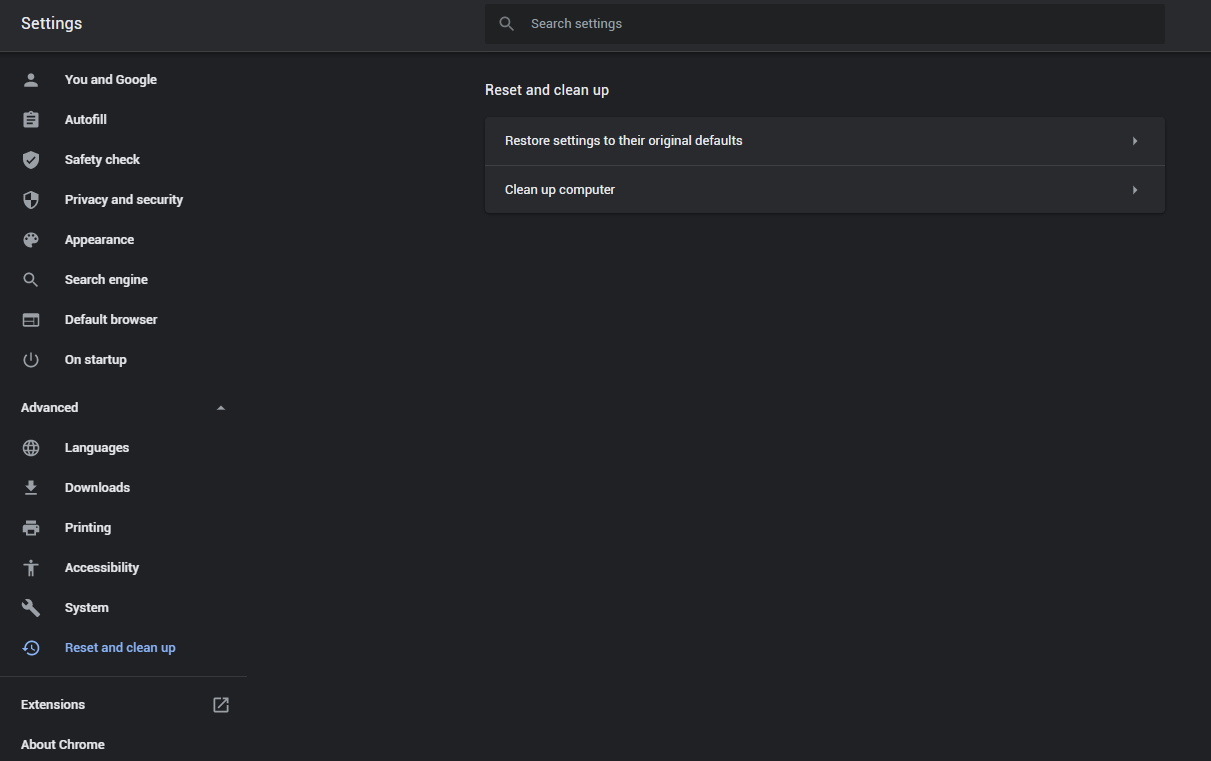
- In the appeared list, click on the “Restore settings to their original defaults” :
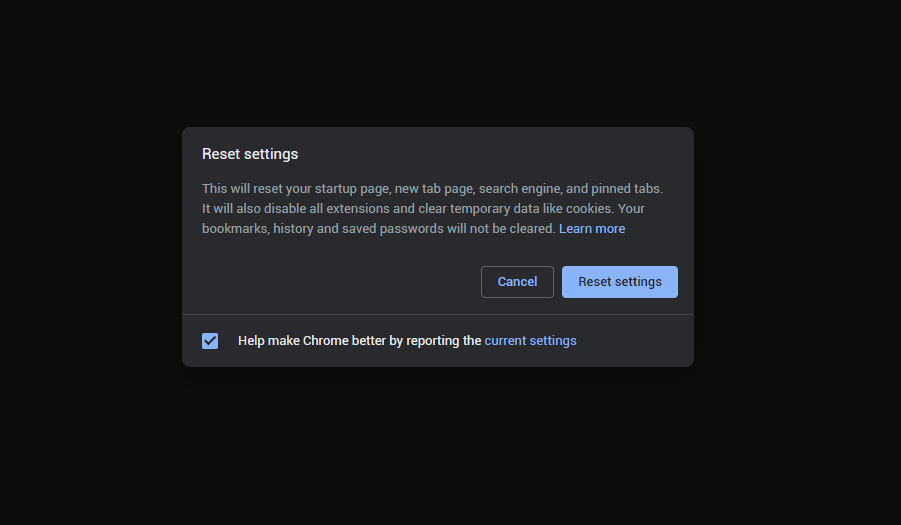
- Finally, you will see the window, where you can see all the settings which will be reset to default :
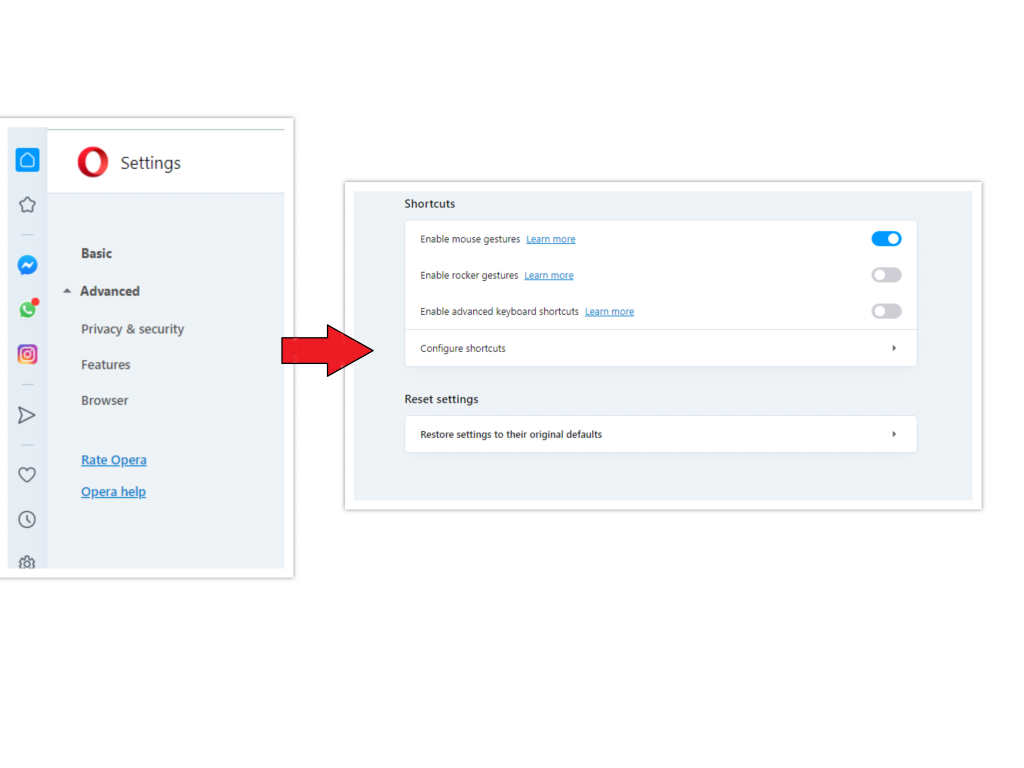
Opera can be reset in the next way
- Open Settings menu by pressing the gear icon in the toolbar (left side of the browser window), then click “Advanced” option, and choose “Browser” button in the drop-down list. Scroll down, to the bottom of the settings menu. Find there “Restore settings to their original defaults” option :
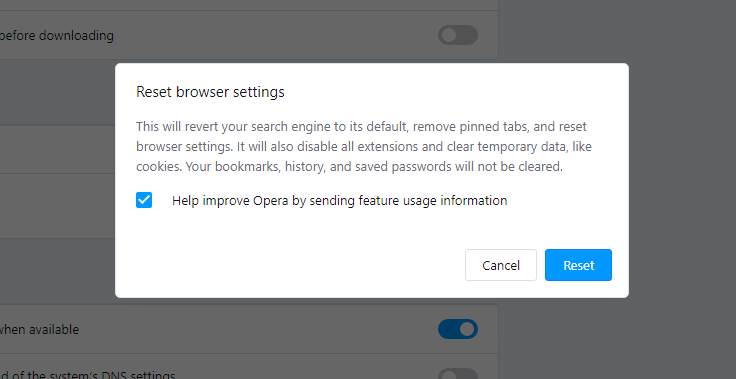
- After clicking the “Restore settings…” button, you will see the window, where all settings, which will be reset, are shown :
As an afterword, I want to say that time plays against you and your PC. The activity of browser hijacker must be stopped as soon as possible, because of the possibility of other malware injection. This malware can be downloaded autonomously, or offered for you to download in one of the windows with advertisements, which are shown to you by the hijacker. You need to act as fast as you can.
I need your help to share this guide.
Browser hijackers are among the largest and also disruptive kinds of malware. I published this article to help you, so I wish you will help me to make the computer world completely clean of malware. Please, share this article in the social networks you use – Twitter, Reddit, Facebook – wherever.
.
Wilbur WoodhamHow to Remove Still Sherpa?

Name: Still Sherpa
Description: Still Sherpa - a lot of users became a victim of browser hijacker. I have a lot of friends who literally bombed me with the questions like “how to remove Still Sherpa?”. In this article we will show you how to deal with Still Sherpa (Stillsherpa.com), which may corrupt your browser’s correct performance, and create a lot of troubles while you are working.
Operating System: Windows
Application Category: Browser Hijacker
User Review
( votes)References
- More information about PUAs
- Detailed review of Microsoft Defender