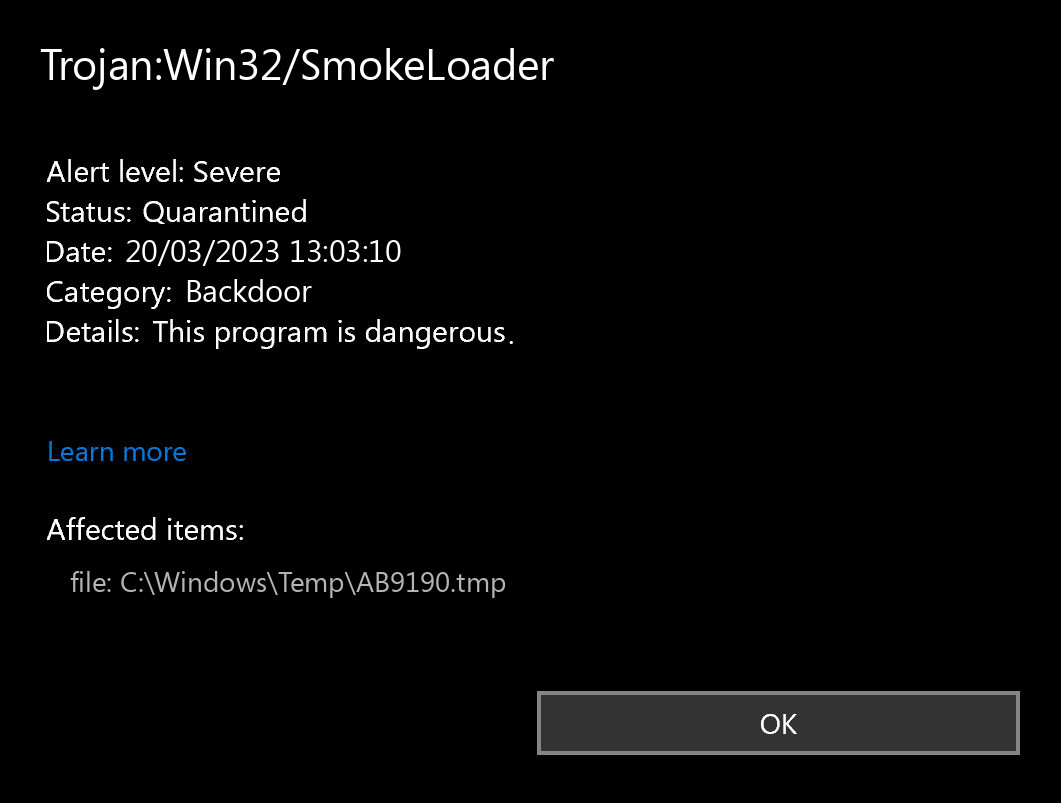
SmokeLoader is a sophisticated backdoor malware known for its modular design, granting it a diverse range of malicious capabilities contingent on the specific modules included in its version. Often linked with criminal activities, this malware is deployed through various methods, such as exploiting software vulnerabilities or utilizing phishing techniques to deceive users into executing its payload.
Notably, SmokeLoader employs tactics to conceal its command and control (C2) activities, including generating requests to legitimate websites like microsoft.com and bing.com, aiding its efforts to avoid detection. Despite its 404 error responses from these sites, the response body still contains data relevant to the malware’s operations. These attributes collectively contribute to SmokeLoader’s effectiveness in facilitating unauthorized access, data theft, and other cybercriminal endeavors.
SmokeLoader backdoor is often distributed through various means, including spam emails, malicious websites, or social engineering techniques. Once it infiltrates a system, it establishes persistence and attempts to contact remote command-and-control servers to receive further instructions and download additional malware.
The specific actions performed by Trojan:Win32/SmokeLoader can vary depending on the version and configuration of the malware. Common activities associated with SmokeLoader include:
- Downloading and installing other malware, such as banking Trojans, ransomware, or information stealers.
- Modifying system settings to achieve persistence and evade detection by security software.
- Capturing sensitive information, such as login credentials, keystrokes, or personal data.
- Updating itself or receiving new instructions from command-and-control servers.
Trojan:Win32/SmokeLoader poses a significant threat to the security and privacy of infected systems. It is essential to have up-to-date antivirus software installed and regularly scan your system for any signs of malware. Additionally, practicing safe browsing habits, being cautious with email attachments and downloads, and keeping your operating system and applications patched can help mitigate the risk of infection.
SmokeLoader Description
SmokeLoader backdoor first appeared in 2014 – at the very beginning of the ransomware era. Only a few other malware can boast of remaining active through 8 years after their launch. This backdoor has a lot of features that allow it to remain actual despite being so old. First and foremost, it is extremely small – the payload is only about 30 kilobytes. Regular malware of that type usually has a file size of at least 100 KB, usually around 150-200 kilobytes. That already makes it way easier to handle in a protected system, as some YARA rules used for malware detection pay attention to the file size.
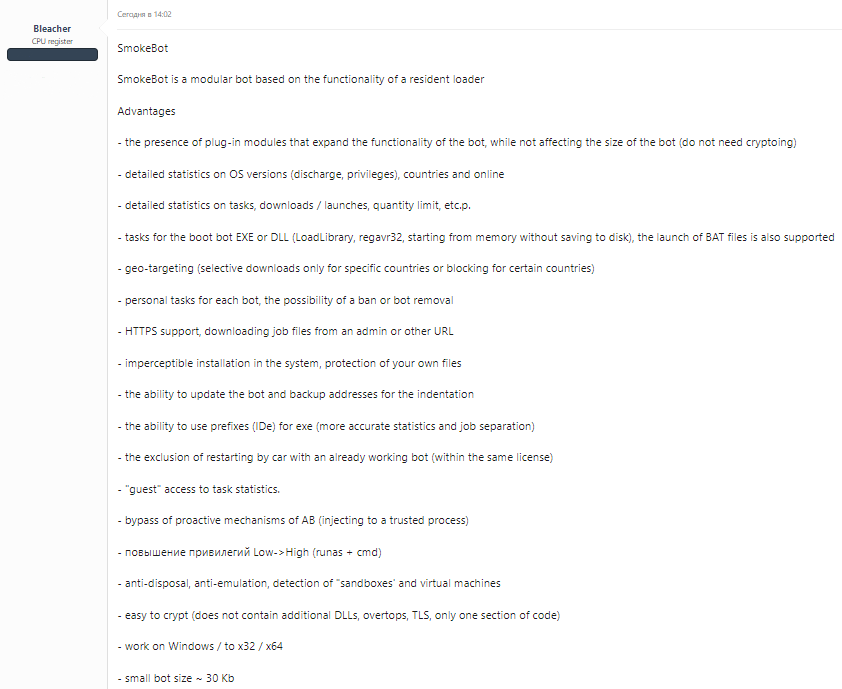
Offer to purchase SmokeLoader on the Darknet forum
Another feature, that distinguishes it among others, is that it is written in C and Assembly languages. Both of them are low-level, which points to their ability to dig very deep into the system. The exact code of this backdoor is heavily obfuscated. It was an effective measure against anti-malware programs, but these days any kind of obfuscation detected is considered hazardous. These days, it just makes reverse engineering this malware much more difficult.
Key features of this backdoor are wrapped around its loader functions, as you may have supposed from its name. The vast majority of time, SmokeLoader is used to deliver other malware to the infected system. Still, it is not the sole purpose of this malware – continuous development brought the ability to use it as a stealing tool. It also suits botnet deployment – but there are only a few cases of such usage. It still receives updates each year, so its functionality may extend in future.
What is backdoor malware?
Before getting into SmokeLoader analysis, let’s have a look at what backdoors are. This malware type has a long and curved story, and these days is an eminence grise. The key target of backdoor malware is to create a way for cybercriminals to remotely connect to the target PC and perform any possible actions. For that purpose, they never disdain to use vulnerabilities in the targeted system, along with injecting into the system as a trojan.
The main use for backdoor-infected computers is their participation in the botnet. Huge networks of zombie systems that perform DDoS attacks, send spam emails and do other nefarious activities are well known over the last decade. For that purpose scoundrels use automated backdoors – the ones which require minimum commands from the command and control server and may run on their own. The other application of a backdoor – exactly, the manually-controlled one – is data stealing and malware implementation. As in the latter case backdoor acts as a locomotive for malicious payload, it is sometimes classified as a worm.
SmokeLoader tech analysis
The initial package of SmokeLoader malware contains only basic functionality – providing the remote connection to the infected PC. Data grabbing, process monitoring, DDoS module and so forth should be installed afterwards. Overall, reverse engineering shows that there are 9 different modules that SmokeLoader can handle simultaneously.
| Module name | Functionality |
| Form grabber | Watches for forms in the open windows in order to grab the credentials |
| Password sniffer | Monitors the incoming and outgoing Internet packages to sniff the credentials |
| Fake DNS | Module for counterfeiting the DNS request. Leads to traffic redirection to the site you need |
| Keylogger | Logs all keystrokes in the infected environment |
| Procmon | Process monitoring module, logs the processes running in the system |
| File search | File searching tool |
| Email grabber | Grabs the Microsoft Outlook address book |
| Remote PC | Ability to establish a remote control similar to remote-access utilities (like TeamViewer) |
| DDoS | Forcing the infected PC to take part in DDoS-attacks on the designated server |
Payload of this malware always comes packed in a unique way. A single sample is used by a small group of its users, hence meeting the same samples in the real world is not that easy. Still, that technology is not something new – most malware does the same thing, and some even generate a uniquely-packed sample for each attack. Moreover, over the initial packing, there is a requirement from its distributors to make an additional compression or encryption before injection. That is, exactly, the other chain of anti-detection measures.
Target system receives the fully-packed SmokeLoader sample – it is what is on the disk. All following stages are executed in the system memory, hence the scans with legacy anti-malware software will only detect a deeply-packed sample. The first stage of SmokeLoader execution includes an important obligatory checkup – the location of the attacked system. This malware cannot be run in the Commonwealth of Independent States, regardless of the settings you did before the injection. Other checkups include scanning for virtual machines and sandbox detection. If all things are passed, the malware gets completely unpacked and launches in its usual manner.
While running, SmokeLoader applies a pretty unique technique of obfuscation. It holds almost 80% of its code encrypted over the entire period of execution. Once it needs to use another function, it deciphers it while ciphering the element it used previously. YARA rules, along with classic reverse engineering, are rendered to be almost useless against such a trick. It has 32-bit and 64-bit payloads that are loaded in the systems with corresponding architectures during the checkup from initial stage to final execution.
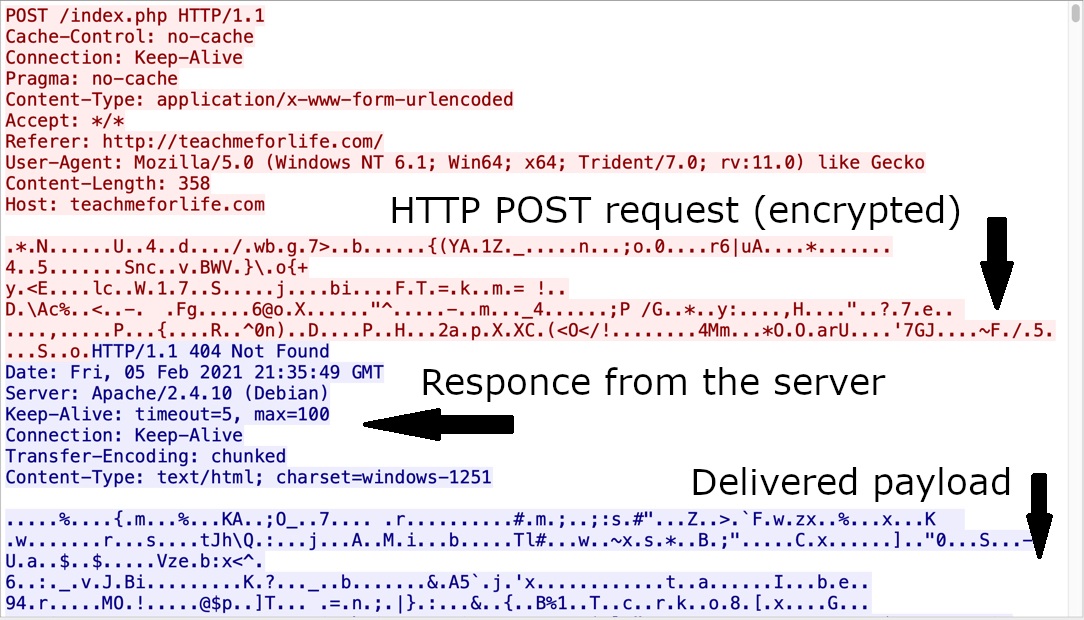
Code encryption in SmokeLoader
The exact file which is kept in the memory while executing the SmokeLoader is not a valid executable file, as it lacks the PE header. In fact, the backdoor’s code is represented as a shell code – and thus should find a way to get executed manually. Generally, the routine commands executed by SmokeLoader, such as calls to C&C or downloads are made through the DLL injections. Obviously, that is required to retain stealthiness. Most often this step includes DLL injection or console calls that are made from the name of another program. Hackers who manage the SmokeLoader may either send the .exe file of malware they wish to install and just specify the URL where the backdoor can get this file.
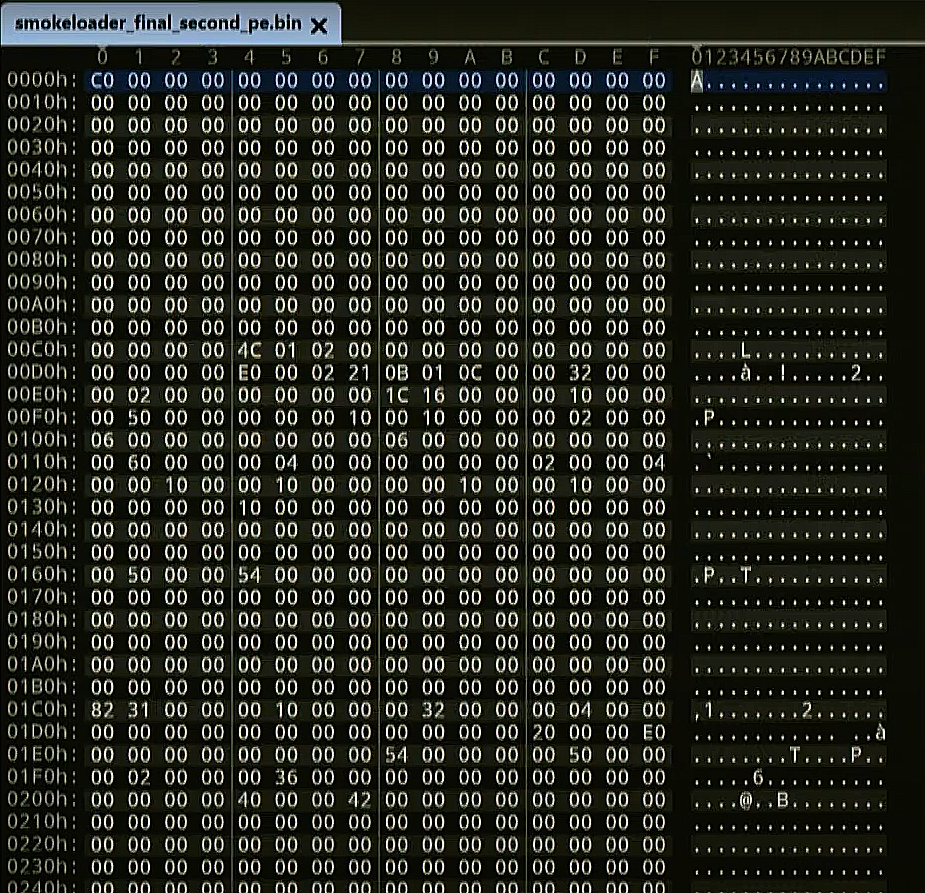
The header of SmokeLoader .exe file is absent – it is not a valid executable file
What is Trojan:Win32/SmokeLoader detection?
The Trojan:Win32/SmokeLoader detection you can see in the lower right side is demonstrated to you by Microsoft Defender. That anti-malware program is quite OK at scanning, but prone to be basically unreliable. It is unprotected to malware attacks, and it has a glitchy user interface and bugged malware removal features. Therefore, the pop-up which states concerning the SmokeLoader is rather just a notification that Defender has recognized it. To remove it, you will likely need to use another anti-malware program.
The exact Trojan:Win32/SmokeLoader malware is a very unpleasant thing. This malware is made to be a sneaky burglar, which functions as a remote-access tool. When you give someone remote access willingly, it is alright, however, SmokeLoader will not ask you if you wish to give it. After connecting to your computer, crooks are free to do whatever they want – snatching your files, checking out your messages, gathering personal data, et cetera. Backdoors frequently bring a supplementary stealer – the virus that is made to collect all available information about you. However, far more common use of the backdoors is forming the botnet. After that, the network of infected computers can be put to use to perform DDoS attacks or to inflate the vote results on various websites.
Backdoor Summary:
| Name | SmokeLoader Backdoor |
| Detection | Trojan:Win32/SmokeLoader |
| Damage | Gain access to the operating system to perform various malicious actions. |
| Similar | Msil Androme, Lotok, Quasarrat, Asyncrat, Msil Dcrat, Rewritehttp, Msil Darkcommet |
| Fix Tool | See If Your System Has Been Affected by SmokeLoader backdoor |
Specific characteristics of SmokeLoader Backdoor
- The binary likely contains encrypted or compressed data. In this case, encryption is a way of hiding virus code from antiviruses and virus analysts.
- The executable is compressed using UPX;
- Anomalous binary characteristics. This is a way of hiding virus code from antiviruses and virus analysts.
Shortly about backdoors
Backdoors are viruses that may acquire both separated and integrated forms. Once you can discover that a legitimate program from a famous developer has a capability that enables somebody to connect to your PC. Will it be someone from the creators or a third party – nobody knows. But the scandal when this detail is found in a legitimate program is probably impossible to miss. There is additionally chatter that there is a hardware-based backdoor in Intel CPUs1.
Is Trojan:Win32/SmokeLoader dangerous?
As I have stated , non-harmful malware does not exist. And Trojan:Win32/SmokeLoader is not an exception. This backdoor does not deal a lot of damage just after it introduces. However, it will likely be a really bad surprise when a random forum or page in the Web will not let you in, due to the fact that your IP-address is banned after the DDoS attack. However, even if it is not crucial for you – is it positive at all to realise that someone else can easily access your computer, read your conversations, open your documents, and spectate what you do?
The spyware that is often present as a supplement to the Trojan:Win32/SmokeLoader virus will likely be just another argument to remove it as fast as you can. Nowadays, when users’ information is priced extremely high, it is too goofy to give the burglars such a chance. Even worse if the spyware will somehow handle to steal your financial information. Seeing 0 on your savings account is the worst headache, in my opinion.
Distribution of SmokeLoader malware
SmokeLoader’s key spreading ways rely upon email spam, pirated software and keygens. The former is prevalent, as it is much easier and still pretty effective. In that case, malware hides inside the attachment – usually an MS Word or MS Excel file. That file contains macros, and if you allow macros execution as requested, it will connect to a command server and receive the payload (actually, only a SmokeBot). However, analysts say that SmokeLoader appears more often through the malicious link attached to such a message. The site by that link may contain an exploit, in particular a cross-site scripting technique.
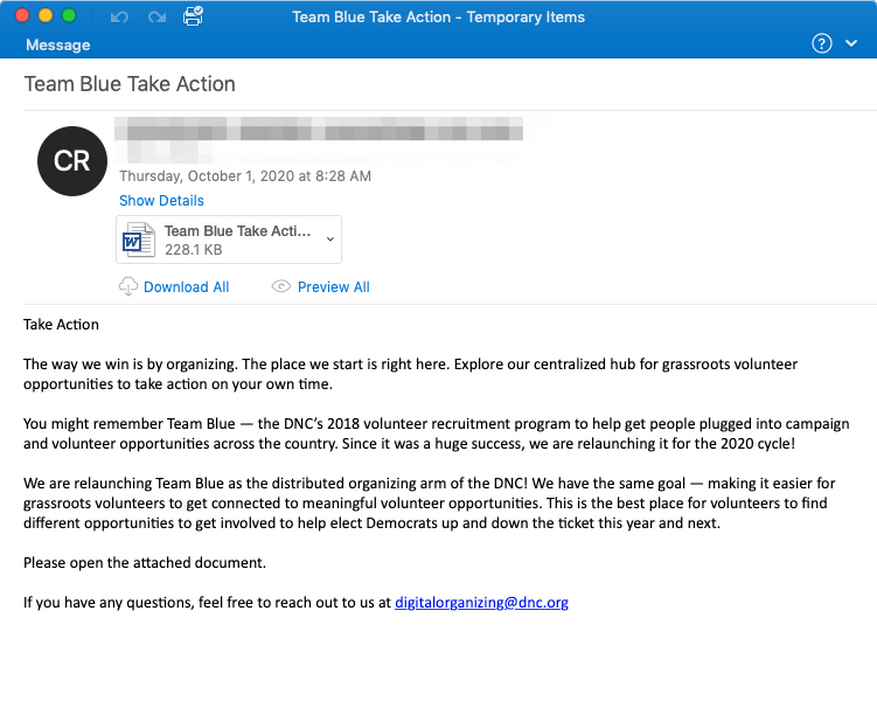
Email spam example. The file contains malicious macro
Hiding malware inside of cracked applications or keygens/hacktools is slightly harder but has way wider potential. As unlicensed software usage is still widespread, a lot of people may be endangered. Not each cracked app contains malware – but all of them are illegal, for both users and creators. Using it, you may end up facing lawsuits for copyright violations. And being infected with malware in that case is even more unpleasant.
When it comes to malware infection, SmokeLoader appearance usually leads to the installation of various other malicious apps. Crooks who managed to create a botnet then offer other malware distributors to infect those computers with whatever they want. That can be adware, browser hijackers, spyware, ransomware – there are literally no restrictions. Behind a huge pile of viruses, cybersecurity experts often miss the origin of all this mess – thus SmokeLoader remains undetected.
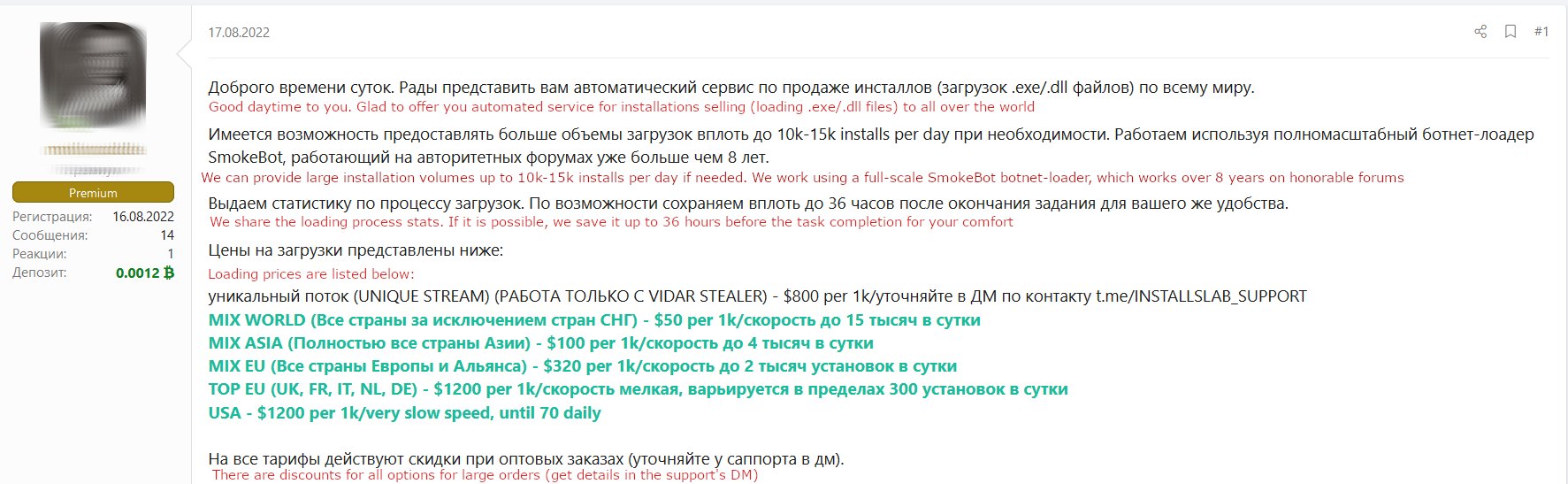
SmokeLoader is offered as a malware delivery tool on forums
A separate spreading case, where SmokeLoader acts not as a precursor, is its combination with STOP/Djvu ransomware. Exactly, the bundle of malware delivered to the device includes RedLine and Vidar stealers. The former aims at banking credentials, the former – cryptowallets info. This or another way, Djvu generates a significant share in SmokeLoader prevalence, since it is one of the most widespread ransomware in its class.
How to remove SmokeLoader?
Trojan:Win32/SmokeLoader malware is very difficult to remove manually. It places its files in a variety of places throughout the disk, and can restore itself from one of the parts. Additionally, countless modifications in the windows registry, networking configurations and also Group Policies are pretty hard to locate and revert to the initial. It is better to use a specific tool – exactly, an anti-malware app. GridinSoft Anti-Malware will definitely fit the most ideal for malware removal purposes.
Why GridinSoft Anti-Malware? It is really lightweight and has its detection databases updated just about every hour. Additionally, it does not have such problems and vulnerabilities as Microsoft Defender does. The combination of these details makes GridinSoft Anti-Malware perfect for removing malware of any form.
Remove the viruses with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of SmokeLoader the default option is “Delete”. Press “Apply” to finish the malware removal.



SmokeLoader IoC
| Indicator | Value |
| С2 URL Addresses | azarehanelle19[.]top quericeriant20[.]top xpowebs[.]ga venis[.]ml paishancho17[.]top mizangs[.]tw mbologwuholing[.]co[.]ug Quadoil[.]ru ydiannetter18[.]top tootoo[.]ga eyecosl[.]ga host-file-host6[.]com host-host-file8[.]com fiskahlilian16[.]top bullions[.]tk |
| IP addresses | 216.128.137.31 8.209.71.53 |
| SHA-256 Hashes | 5318751b75d8c6152d90bbbf2864558626783f497443d4be1a003b64bc2acbc2 79ae89733257378139cf3bdce3a30802818ca1a12bb2343e0b9d0f51f8af1f10 Ebdebba349aba676e9739df18c503ab8c16c7fa1b853fd183f0a005c0e4f68ae Ee8f0ff6b0ee6072a30d45c135228108d4c032807810006ec77f2bf72856e04a D618d086cdfc61b69e6d93a13cea06e98ac2ad7d846f044990f2ce8305fe8d1b 6b48d5999d04db6b4c7f91fa311bfff6caee938dd50095a7a5fb7f222987efa3 B961d6795d7ceb3ea3cd00e037460958776a39747c8f03783d458b38daec8025 F92523fa104575e0605f90ce4a75a95204bc8af656c27a04aa26782cb64d938d 02083f46860f1ad11e62b2b5f601a86406f7ee3c456e6699ee2912c5d1d89cb9 059d615ce6dee655959d7feae7b70f3b7c806f3986deb1826d01a07aec5a39cf |
User Review
( vote)References
- Gossip about the backdoor in Intel processors on Reddit.
![]() German
German ![]() Japanese
Japanese ![]() Spanish
Spanish ![]() Portuguese (Brazil)
Portuguese (Brazil) ![]() French
French ![]() Turkish
Turkish ![]() Chinese (Traditional)
Chinese (Traditional) ![]() Korean
Korean ![]() Indonesian
Indonesian ![]() Hindi
Hindi ![]() Italian
Italian