Trend Micro specialists found that in the official Google Play store at once three applications (Camero, FileCrypt Manager and callCam) are associated with the Sidewinder group, specializing in cyber-spyware attacks.
SideWinder is a group that has been active since 2012; it is known threat and has reportedly targeted military entities ’Windows machines.According to experts, these applications have used the critical vulnerability CVE-2019-2215 at least since March 2019.
The three malicious apps were disguised as photography and file manager tools. We speculate that these apps have been active since March 2019 based on the certificate information on one of the apps”, — write Trend Micro researchers.
Therefore, attacker exploited the vulnerability more than seven months before information security specialists first discovered it.
Recall that this vulnerability represents a local privilege escalation and can help an attacker gain root access to the target device. Additionally, the bug can be used remotely in combination with other bugs.
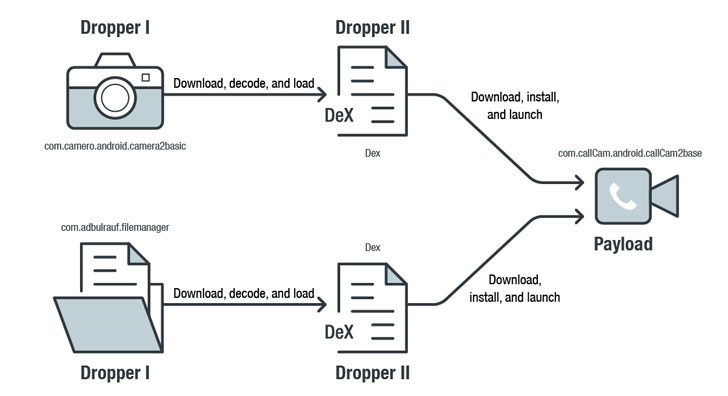
According to Trend Micro, the FileCrypt Manager and Camero applications act as droppers, that is, they connect to a remote attacker server to download the DEX file, which then downloads the callCam application and tries to install it using vulnerabilities to elevate privileges or abuse the Accessibility Service.
In addition to CVE-2019-2215, malicious applications also try to exploit the vulnerability in the MediaTek-SU driver to obtain root privileges and trying to gain a foothold in the system.
The attack occurs without the intervention of the user and his awareness. To avoid detection, criminals used obfuscation, data encryption, and so on.
After installation, the callCam application hides its icon from the user, collects and steals the following information from the hacked device, then transferring it to the management server:
- location data;
- battery level data;
- information about files on the device;
- list of installed applications;
- device information;
- sensor information;
- camera information;
- screenshots;
- account information;
- Wi-Fi information;
- data from WeChat, Outlook, Twitter, Yahoo Mail, Facebook, Gmail.
Based on information about the control servers of the malware, researchers attributed this malicious campaign to the Sidewinder spy group. It is considered to be Indian and usually attacks organizations associated with the Pakistani military.
Currently, all three applications have already been removed from Google Play.
At the same time, Microsoft went further in its fight against international cybercriminal groups and spy organizations: recently, the tech giant took control over 50 domains previously owned by the North Korean Thallium group (APT37) and used for its operations.