The REvil group is in the spotlight through the last two weeks. Compromised servers, claims about the complete shutdown, and now – deanonymizing of their key persons. Is that just a coincidence, or the result of well-planned actions from executive authorities?
What’s happening with REvil?
Throughout the last two weeks, REvil gang appeared on the titles of newsletters for two times. First, on October 17, one of the REvil members claimed that somebody have compromised their servers. That person (or group) held a backup copy of REvil’s facilities for money extortion and data publishing in Darknet. In just four days, another gang actor said that they decided to shut down their activity completely.
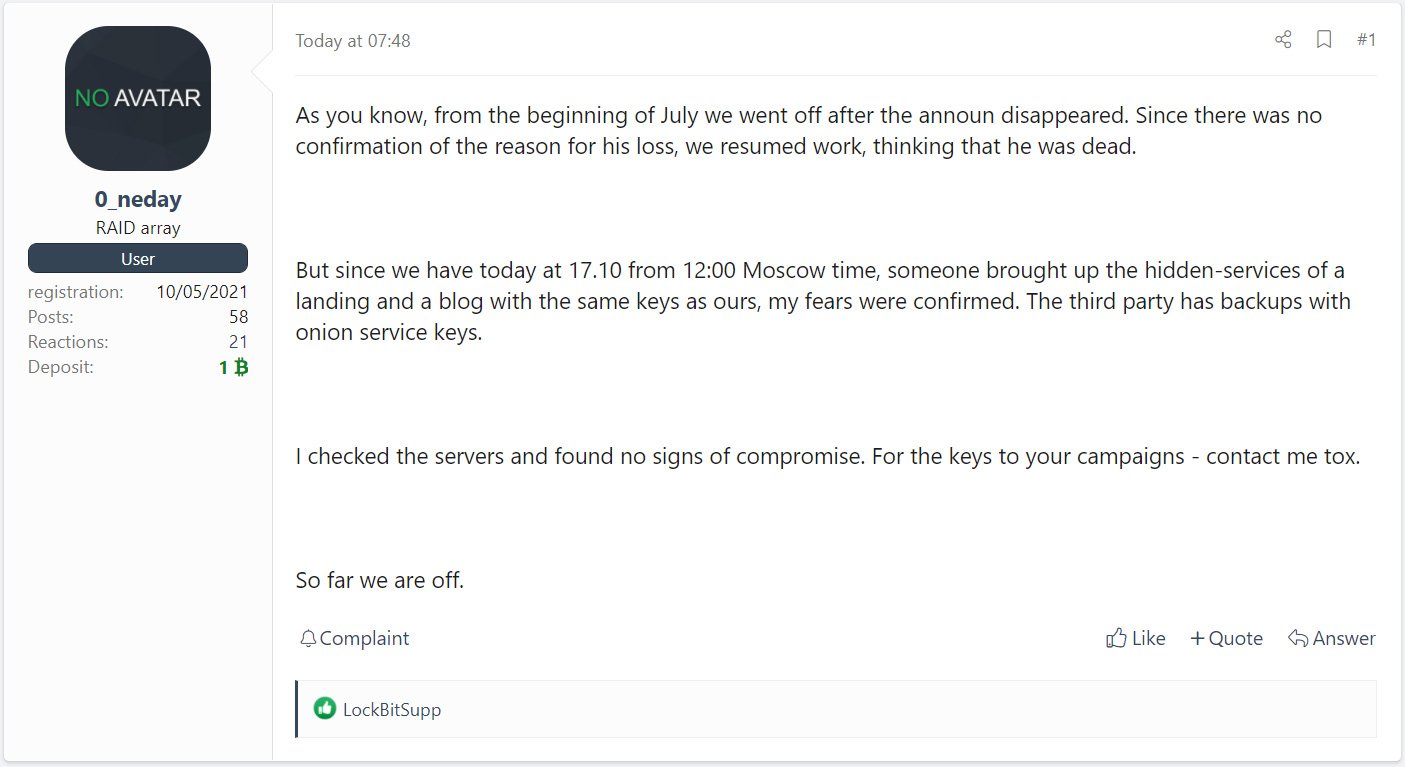
Message on the Darknet forum where REvil decided to shut down their activity
All of these actions look like the final accords of all “show” that had happened to this cybercriminal group since July 2021. After their failure during the attack on Kaseya, a lot of gossips appeared that the FBI got the universal decryption key for REvil ransomware1. The group refuted this gossip by saying that only the key for Kaseya’s network was leaked. Nonetheless, one of their actors, known as UNKNWN, disappeared after that event.
REvil group was deanonymized
Soon after the news about the ransomware group shutdown, another piece of bad news came out. EU intelligence services detected one of the group members near Antalya, Turkey – resting on the rented yacht with his spouse. The video on the wife’s Instagram acted as a base for this investigation. She has a lot of pictures of other luxury resorts she visited with her husband. Last runs his own IG account, but it is restricted to not-friended users. Nonetheless, his short slogan is visible to anyone. In it, he claims that all profits he has he receives from operations with cryptocurrencies. One thing he missed is that he receives these cryptocurrencies by extorting them from victims.

The exact yacht renting is not a cheap thing – prices for that exact vessel starts from €1,300 per 1 day. But such a luxury vacation is not the only expensive thing in his life. Exclusive watches – Vanguard Encrypto – with Bitcoin wallet address engraved on it, cost about €70,000. Sumptuous clothes, BMW sports car – all attributes of a rich self-made man. But only several people know the real source of all this wealth.
Assuming the report
It seems that tracking this man was not pretty easy, but special services did their job perfectly. Reportedly, the investigators have got his email address (real, not single-time), and a lot of related information. They have also figured out his phone number and the Telegram account he has registered this number. If so, there is nothing strange about this deanonymization. That was only the question of time – sooner or later, such a rich and careless person will appear in the spotlight. And assuming the increased interest from the FBI to REvil group, it happened rather sooner.
Also, it is not obvious if this deanonymization has any immediate effects on crooks. For sure, that creates a ton of psychological pressure on each group member. Understanding that this or other day your face can appear in the newsletters makes the fraudster nervous. And the more nervous he is – the bigger the chance of making a wrong decision. Now, when the group is inactive, the FBI can just make fun of the group, playing with it like a cat with a mouse. Possibly, REvil heads may report each other to the executive authorities, trying to decrease their term in prison by cooperating with the investigation.
Russian lawlessness serves the ransomware
Regardless of the fact that REvil is not operating anymore, and their operators are afraid of capturing, the heads of this group have to respond for their crimes. The executive authorities and cybersecurity experts made a lot of trustworthy statements on this group. According to them, REvil is “based” in Russia, and one of the “heads” – Maxim Yakubets – is likely a relative of a Russian FSS colonel. Such an immunity to any sort of punishment gave him the feeling of freedom – he drives the exclusive Lamborghini with a personal number plate “ВОР” (“thief” in Russian), and does not even hide his criminal sources of money. Of course, he is wanted by Europol, but Russian authorities do not hasten to give him up.

The FBI dossier on Maxim Yakubets
Moreover – they even do everything to avoid his extradition to the EU. After the loud claims from Ilya Sachkov, the CEO of cybersecurity company IB-Group, Russian FSS started the investigation against him and his company. Ilya said that all heads in the Russian MIA and FSS know who the REvil heads are, but no one takes any action. The IB-Group was soon blamed for spying on Russia’s secrets for foreign organizations, and Sachkov was captured for treason. None of these blames are backed by any facts or proofs. However, the working process in the IB-Group office is not too comfortable – the company suffered two searches from the FSS during October 20212. Isn’t that a proof that REvil is government-backed ransomware?
What’s next?
It was very interesting to see how the “empire” of REvil ransomware disintegrates in less than 6 months. After their “peak point” – the attack on Acer Corp, when they asked for $50 million ransom, their things were getting worse and worse. Nowadays, they have nothing besides the money they have already got on their BTC wallets – and the FBI laser point on their heads. It seems that soon any careless step of any of the group members will turn into capturing. The “new Cold War” is now happening online, and the Western world’s executive authorities have successfully destroyed one of Russia’s main guns. Will the next step be destroying the ammunition factories? Or blocking the front line?
User Review
( votes)References
- More detailed report on the rumors that were circulating that time.
- More information on the searches in the IB-Group office.


