Evolution Gaming specialist Oscar Vegeris described how at the beginning of 2020 he found a number of critical vulnerabilities in Slack, which made it possible to easily execute arbitrary code on the user’s machine.
As it became known now, when the details of the vulnerabilities were disclosed, and the problems themselves were eliminated, the company paid the specialist only $1,750, after which it was sharply criticized by the information security community.In the five-second demo that the researcher attached to his HackerOne report, it can be seen that he is using a JSON file to trigger a calculator to run via Slack on the victim’s machine.
In the report, the specialist lists several ways to maliciously exploit Slack applications, but the final result is the execution of arbitrary code on the client side, that is the user’s computer. Desktop versions of Slack (4.2, 4.3.2) for Mac, Windows and Linux were called vulnerable.
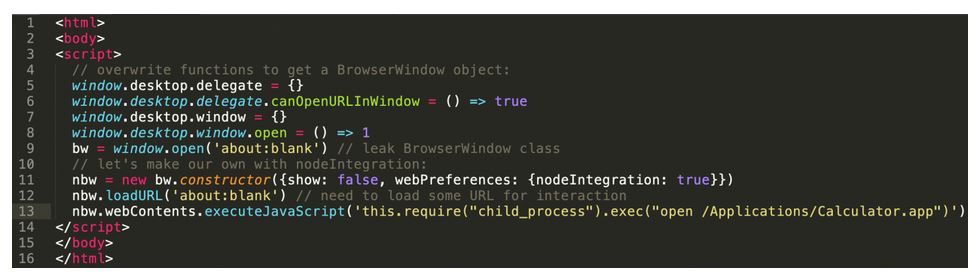
In essence, the detected bugs could be used by an attacker to perform HTML injection, arbitrary code execution, and XSS attacks due to an issue on files.slack.com. The HTML/JavaScript PoC exploit posted by Vigeris demonstrates how easy it is to launch a calculator app or something else through Slack.
The URL link in the area tag contains an HTML/JS exploit for the Slack Desktop application, which executes any command provided by an attacker”, — explains the expert.
However, in this case, it is not only the vulnerabilities discovered by Vigeris that are interesting, but the fact that the company paid him only $1,750. The cybersecurity community has already condemned Slack, which is used by more than 10,000,000 people every day, and many experts note that if someone sold such an exploit on the darknet, they would have made much more than $1,750.
It’s just ridiculous, honestly. My feeling it’s almost trolling the researcher in this case. And then people seriously be annoyed by “unresponsible” disclosures. I wonder who is unresponsible in the first place. Most companies get what they deserve for their shitty behaviour”, — write, for instance, @mitp0sh.
It has also now become known that two months ago, there was a promotional post on the Slack blog about the app sandbox. But the developers did not mention in the text the details of the vulnerabilities that led to its development, and also forgot to refer to Vigeris, who found the problem.
The company has now apologized to the researcher, corrected the same post, and promised to take all the necessary steps to ensure that everyone who contributes to improving the security of Slack is recognized.
Recall that, for example, Microsoft spent twice more than Google on bug bounty programs last year and this sum consists $13,700,000.