Magniber (MyDecryptor) ransomware is a ransomware gang that has shown episodic activity in the last several years. It injects your PC using security breaches in the programs you use and cipher your files. For the decryption, this ransomware asks for a pretty typical sum – about $1000 in Bitcoins.
What is Magniber ransomware?
Magniber ransomware starts its history in 2017 when it ciphered its first victims in South Korea. However, the exploit kit it used (and sometimes still uses) in the attacks – Magnitude – appeared in 2013. Since 2017, its activity has become episodic. After a long “silence period”, which lasted since 2019, it struck again in summer 2021. Then, it went offline for about 6 months to be back in February 2022.
In April, 2022, it applied the new spreading tactics. Now Magniber ransomware infiltrates its victims under the guise of Windows 10 update. Several large forums reported numerous complaints about ransomware attacks after installing the file was recognized as Windows update. These fake patches were also spotted on pseudo-knowledgebase sites, that contain the “solutions” for certain problems with the operating systems. Such an approach differs from what Magniber distributors used earlier. Here is the list of names applied to these fake Windows updates:
- System.Upgrade.Win10.0-KB66846525.msi
- System.Upgrade.Win10.0-KB18062410.msi
- System.Upgrade.Win10.0-KB47287134.msi
- System.Upgrade.Win10.0-KB82260712.msi
- Security_Upgrade_Software_Win10.0.msi
- Win10.0_System_Upgrade_Software.msi
This ransomware family is distinctive by the extension it uses. For each small group of victims it ciphers, Magniber (MyDecryptor) ransomware applies the extension that consists of up to 10 random letters. For example, the file “dancer.mp3” will turn into “dancer.mp3.wmfxdqz”. There are already 284 variants of extensions (i.e. 284 groups of victims). Such division is done to make searching on the Internet ineffective: too few people will have the same problem, so neither forums nor anti-malware portals will give you an answer.
The list of Magniber variants observed by malware analysts:
After the encryption, this ransomware leaves a README.html file on the desktop. Some of the early Magniber variants were posting a .txt file instead of .html. The plain text file had the name “_HOW_TO_DECRYPT_MY_FILES_[random_letters]_.txt”, and contained the classic ransom note (see the text on the screenshot below).
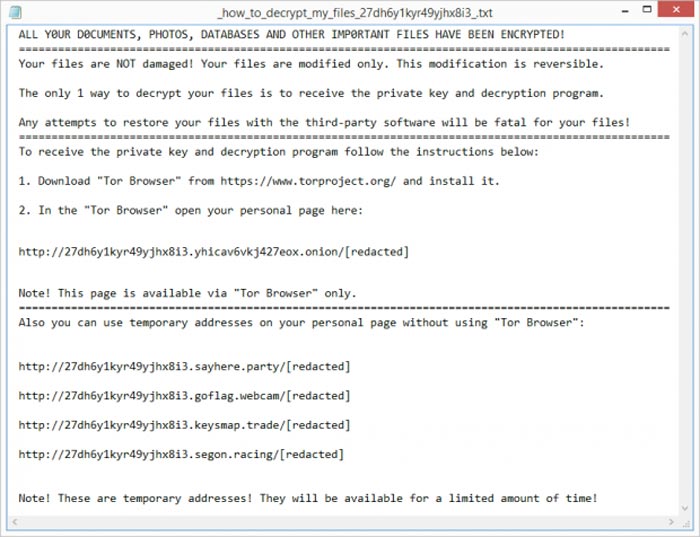
ALL Y0UR D0CUMENTS, PHOTOS, DATABASES, AND OTHER IMP0RTANT FILES HAVE BEEN ENCRYPTED!
==========================
Your files are NOT damaged! Your files are modified only. This modification is reversible.
The only 1 way to decrypt your files is to receive the private key and decryption program.
Any attempts to restore your files with the third-party software will be fatal for your files!
============================
To receive the private key and decryption program follow the instructions below:
1. Download "Tor Browser" from hxxps://www.torproject.org/ and install it.
2. In the "Tor Browser" open your personal page here:
hxxp://27dh6y1kyr49yjhx8i3.yhicav6vkj427eox.onion/
Note! This page is available via "Tor Browser" only.
==============================
Also you can use temporary addresses on your personal page without using "Tor Browser":
hxxp://27dh6y1kyr49yjhx8i3.sayhere.party/
hxxp://27dh6y1kyr49yjhx8i3.goflag.webcam/
hxxp://27dh6y1kyr49yjhx8i3.keysmap.trade/
hxxp://27dh6y1kyr49yjhx8i3.segon.racing/
Note! These are temporary addresses! They will be available for a limited amount of time!
The .pdf file has the other text, that is more similar to the ones used by other ransomware groups. Usage of the .pdf file instead of the .txt one points at the wish for the note to be seen and read. Some victims, especially ones that start the panic after discovering their files encrypted, may easily miss the solitary ransom note. But the banner in the web browser will surely attract attention. Here is what will you see:
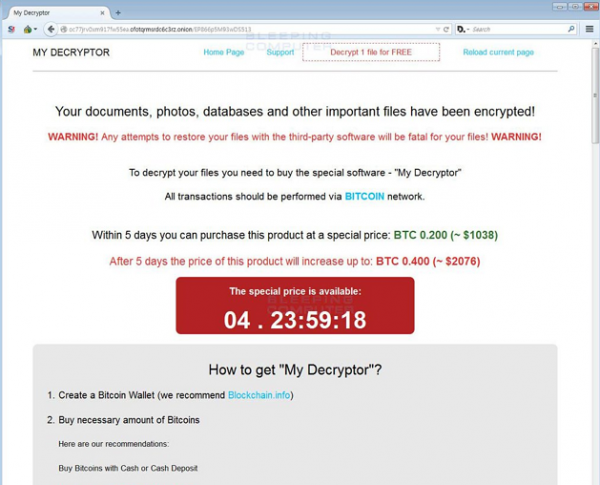
MY DECRYPTOR
Your documents, photos, databases and other important files have been encrypted!
WARNING! Any attempts to restore your files with the third-party software will be fatal for your files! WARNING!
To decrypt your files you need to buy the special software - "My Decryptor"
All transactions should be performed via BITCOIN network.
Within 5 days you can purchase this product at a special price: BTC 0.200 (~ $1141)
After 5 days the price of this product will increase up to: BTC 0.400 (~ $2282)
How to get "My Decryptor"?
1. Create a Bitcoin Wallet (we recommend Blockchain.info)
2. Buy necessary amount of Bitcoins
3. Send BTC 0.200 to the following Bitcoin address:
18TALbvcZucFZqhui1rowZYiRK5kkwBP1V
4. Control the amount transaction at the "Payments History" panel below
5. Reload current page after the payment and get a link to download the software
At the moment, we have received from you: BTC 0.000 (left to pay BTC 0.200)
How to remove Magniber Ransomware from my PC?
Same as with any other complicated malware, it is better to use anti-malware software to detect and remove Magniber from your device. Since the last variants of this ransomware modify your web browser, it is also required to reset your browser settings. The perfect anti-malware tool that can satisfy both needs is GridinSoft Anti-Malware. It is perfect for system cleaning, thanks to very often database updates. And it can either fix your web browsers after the malware attack.
Removing Magniber ransomware with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of ransomware the default option is “Delete”. Press “Apply” to finish the malware removal.



Now, when the computer is clean of viruses, we can proceed to the browser reset. To speed things up, I’d recommend doing it with GridinSoft Anti-Malware.
Reset your browser settings with GridinSoft Anti-Malware
To reset your browser with GridinSoft Anti-Malware, open the Tools tab, and click the “Reset browser settings” button.
You can see the list of the options for each browser. By default, they are set up in a manner that fits the majority of users. Press the “Reset” button (lower right corner). In a minute, your browser will be as good as new.
The browser reset is better to perform through the antivirus tool by GridinSoft because last can also reset the HOSTS file without any additional commands.
How to decrypt Magniber (MyDecryptor) ransomware?
Fortunately, you can decrypt some of the variants of Magniber ransomware. The special free tool from AhnLab will help you to get your files back. Thanks to the leaked decryption keys, this program allows you to get your files back without any problems. The tool can decipher 14 variants of Magniber ransomware. If you don’t see your extension in this list – you may wait or try out other ways to get your files back.
One of the most successful ways to get your files back after the ransomware attack is to scan your disk with file recovery tools. Since this malware does not overwrite your files but removes the original files and substitutes them with the ciphered copy, the residue of your files is still on your disk. To recover the entity in the file system, file recovery tools are needed. You may use a free, open-source tool PhotoRec for that purpose.
IMPORTATN NOTE: Before the decryption or file recovery, it is important to get rid of the exact ransomware. Although it will try to prevent you from succeeding in the decryption, ransomware will also cipher your files back as soon as you get them back. Hence, we recommend you scan your device with anti-malware software before all other operations.
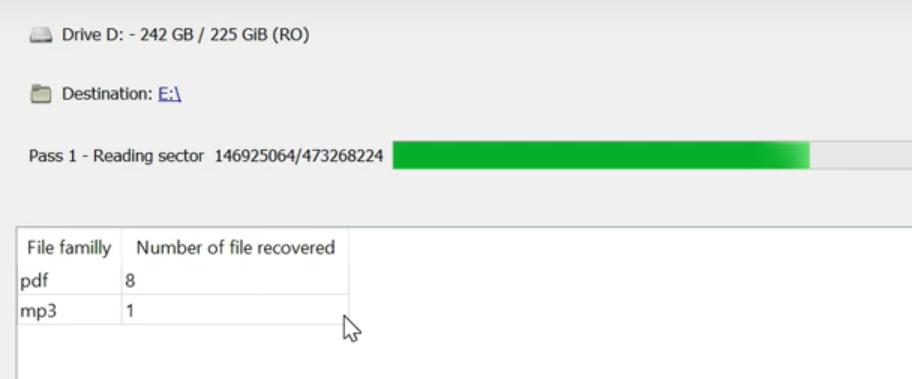
Recovering your files with PhotoRec file recovery tool
At first, you need to download this app. It is 100% free, but the developer states that there is no guarantee that your files will be recovered. PhotoRec is distributed in a pack with another utility of the same developer – TestDisk. The archive will have the TestDisk name, but don’t worry. PhotoRec files are right inside.
To open PhotoRec, you need to find and open “qphotorec_win.exe” file. No installation is required – this program has all the files it need inside of the archive, hence, you can fit it on your USB drive, and try to help your friend/parents/anyone who was been attacked by DJVU/STOP ransomware.
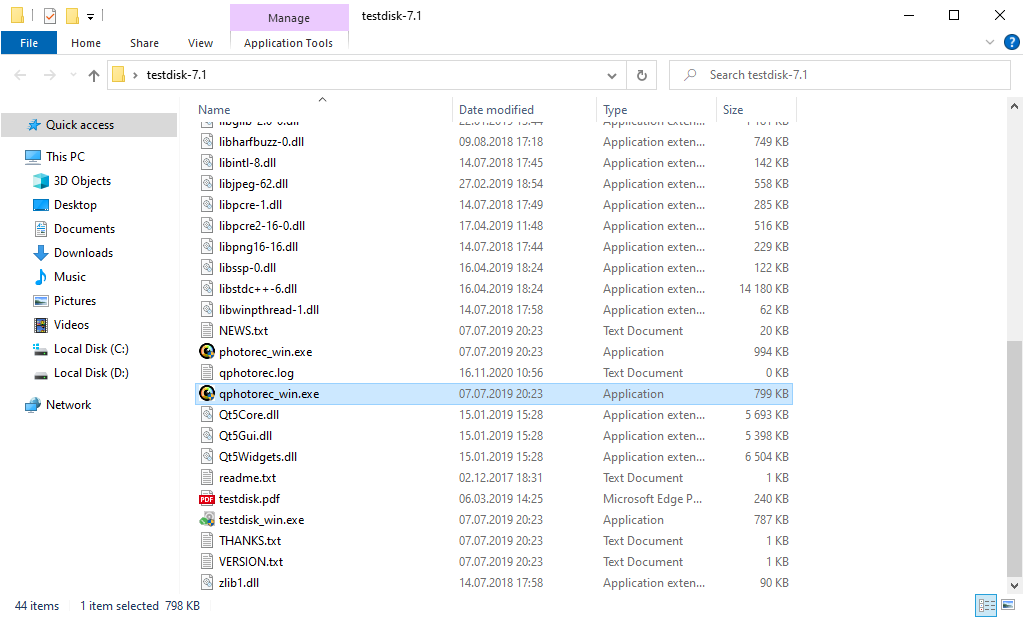
After the launch, the screen shows you the complete list of your disk spaces. However, this information is likely useless because the required menu is higher. Click this bar, then choose the disk which was attacked by ransomware.
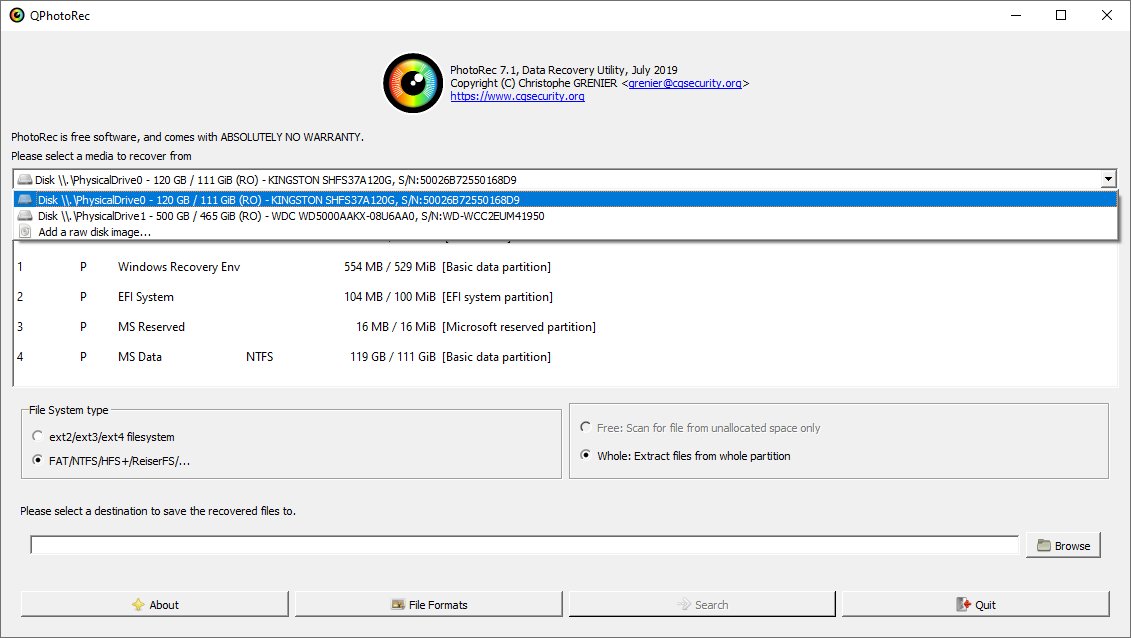
After choosing the disk, you need to choose the destination folder for the recovered files. You can find that menu at the lower part of the PhotoRec window. The best desicion is to export them on USB drive or any other type of removable disk.
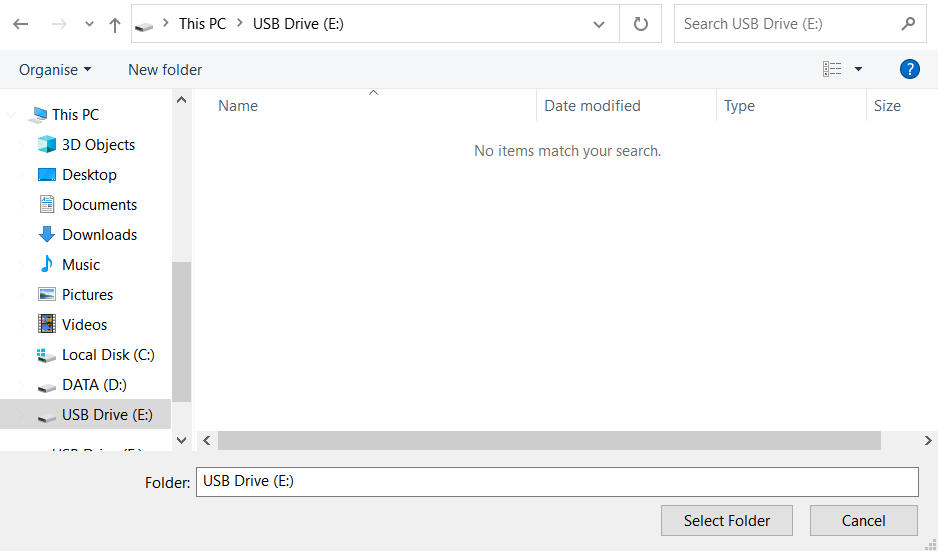
Then, you need to specify the file formats. This option is located at the bottom, too. As was mentioned, PhotoRec can recover files of about 400 different formats.
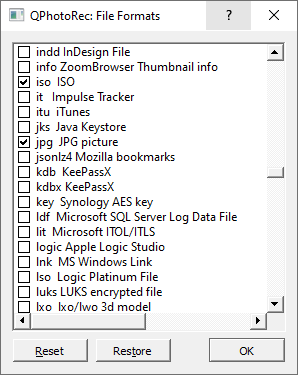
Finally, you can start files recovery by pressing the “Search” button. You will see the screen where the results of the scan and recovery are shown.
How did Magniber ransomware appear on my PC?
Most of the reported Magniber (MyDecryptor) ransomware cases were related to exploiting the application software vulnerabilities. In particular, modern versions of that ransomware aim for the exploits in Chromium-based web browsers. In the summer of 2021, it was making its way through the security of your PC via PrintNightmare vulnerability. And while in 2021, it required some tricks with scripts and privileges escalation, in 2022, it managed to trick the users into doing all the dirty jobs by themselves.
The compromised website that offers the user to update the browser (usually Chrome or Edge) contains the link to Magniber downloading. The .appx file downloaded after pressing that button is recognized as a browser extension and thus ignored by security systems. For more confidence, crooks managed to counterfeit the certificate of that plugin – in order if the web browser would try to check it. After launching in the browser, it drops the .dll file into C:\ProgramFiles\WindowsApps and starts the ciphering.

Using the PrintNightmare vulnerability, however, usually took much more steps to start the action. The main peculiarity of this injection was in the exact vulnerability. In addition to the PrintNightmare (i.e. CVE-2021-34527), it exploited a chain of smaller breaches related to the printing devices management in Windows. That made this threat more persistent since malware can deploy the payload even after the patch installation. Fixing the driver-related issues requires installing new drivers, and system updates could barely help it.1
How to be safe?
Preventing the Magniber ransomware infiltration is pretty easy. It does not use 0-day vulnerabilities for injection, so all breaches are likely well-known. Keep your system and applications updated, and you will likely never meet with that attacker again. Both Windows and web browsers receive security updates almost every week. When analysts detect a critical vulnerability, its hotfix may appear even the next day. So check for updates regularly, especially if you are hearing something about a new trending vulnerability.
Nonetheless, there are particular cases when you cannot keep your software updated. For example, users of old systems will not receive the latest security patches. Windows 11 users who installed this version through a trick will never see any updates – Microsoft officially denied supporting incompatible systems. The only solid advice for that category of users is to follow the computer hygiene rules. Dubious websites with pirated software, Windows activators, and “browser optimizer add-ons” are not your friends.
References
- More details on how Magniber ransomware exploited the PrintNightmare vulnerability in Windows.

![What is the Win32:Evo-gen [Trj] virus?](https://howtofix.guide/wp-content/uploads/2019/11/trojan-ransom-380x260.jpg)
