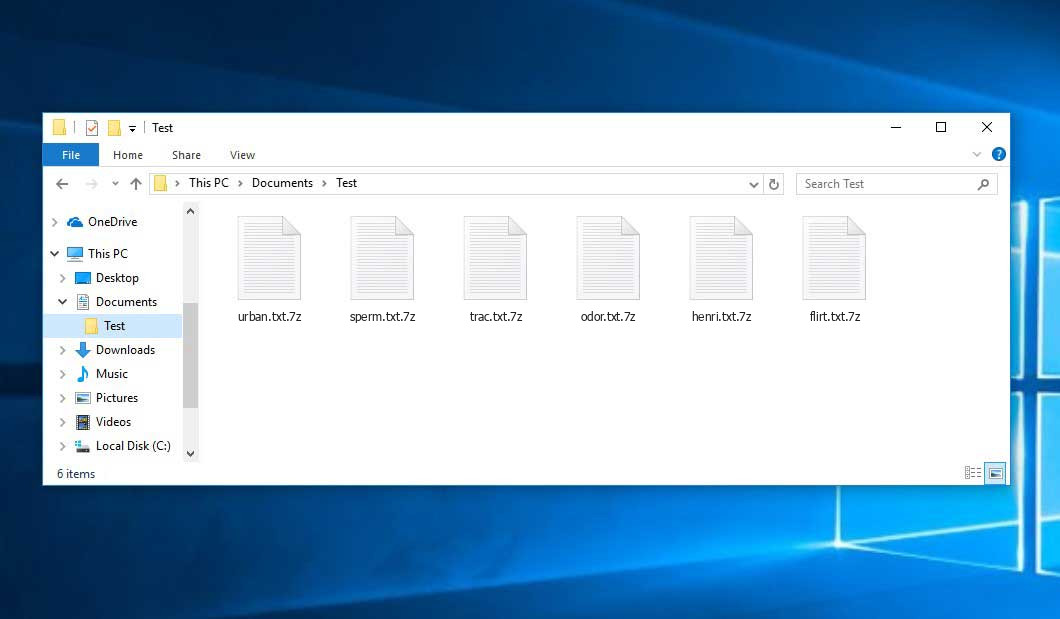
The Qnap NAS Ransomware belongs to the Qlocker family. This ransomware zip (by 7zip tool) all user’s data on the PC (photos, documents, excel tables, music, videos, etc), adds extension to every file, and creates the !!!READ_ME.txt files in every folder which contains encrypted files.
Qnap NAS Ransomware
☝️ Qnap NAS can be correctly identify as a Qlocker ransomware-type infection.
Qnap NAS adds its specific “.7z” extension to the name of every file. For example, your photo named as “my_photo.jpeg” will be transformed into “my_photo.jpeg.7z“, report in Excel tables named “report.xlsx” – to “report.xlsx.7z“, and so on.
!!!READ_ME.txt file, which can be found in every folder that contains the encrypted files, is a ransom money note. Inside of it, you can find information about ways of contacting Qnap NAS ransomware developers, and some other info. Inside of the ransom note, there is usually an instruction saying about purchasing the decryption tool. This decryption tool is created by ransomware developers.
Here is a summary for the Qnap NAS Ransomware:
| Name | Qnap NAS Ransomware |
| Ransomware family1 | Qlocker ransomware |
| Extension | .7z |
| Ransomware note | !!!READ_ME.txt |
| Detection | Generik.EEALKMM, Trojan.Ransom.CerberKD.6096905, Win32/Kryptik.GEHH |
| Symptoms | Your files (photos, videos, documents) have a .7z extension and you can’t open it. |
| Fix Tool | See If Your System Has Been Affected by Qnap NAS Ransomware |
The !!!READ_ME.txt file by the Qnap NAS ransomware states the following frustrating information:
!!! All your files have been encrypted !!! All your files were encrypted using a private and unique key generated for the computer. This key is stored in our server and the only way to receive your key and decrypt your files is by making a Bitcoin payment. To purchase your key and decrypt your files, please follow these steps: 1. Dowload the Tor Browser at “https://www.torproject.org/”. If you need help, please Google for “access onion page”. 2. Visit the following pages with the Tor Browser: gvka2m4qt5fod2fltkjmdk4gxh5oxemhpgmnmtjptms6fkgfzdd62tad.onion 3. Enter your Client Key: KU1o8mGG4p8moefySdZSI85HX6C2HrkK+bxGuHnuXSbStdiDiGsOyl2BsIZA1x2/d+yiEVnRnJ3TVu1g2C1v8MLKuykVkIhCnCBM/im9MvPs74klClQaL8DxUDLznCwiC0k/0KK3r+usGQXDYarxF34da5kXweU+vv7rS4q9fRUzKW30UDBE9OqpYs3bPENspssr8C2hcEqJxNPtPY2nswVC95tgVlDXdET3w+TIqEIzzQEVxUc7TN55GW8ajyu2d1EO3QVxkTKreoMVED5qDuMXryZe24NfOGuJoNN644JkTChwemiahcdMI77NPa47SDmK8uFiAIHSEXGOR/soqg==
The image below gives a clear vision of how the files with “.7z” extension look like:
How did I get Qnap NAS ransomware on my computer?
That was a huge number of different ways of ransomware injection.
However, nowadays there are only two ways of Qnap NAS injection – email spam and trojans. You may see a lot of messages on your email, stating that you need to pay different bills or to get your parcel from the local FedEx department. But all such messages are sent from unknown email addresses, not from familiar official emails of these companies. All such letters contain the attached file, which is used as a ransomware carrier. If you open this file – your system will get infected by Qnap NAS.
In case of trojans presence, you will be offered to download and install ransomware on your PC under the guise of something legit, like a Chrome update, or update for the software you are storing on your computer. Sometimes, trojan viruses can be masked as legit programs, and ransomware will be offered for download as an important update, or a big pack of extensions that are essential for proper program functioning.
There is also the third way of ransomware injection, however, it becomes less and less popular day-to-day. I am talking about peering networks, such as torrents or eMule. No one can control which files are packed in the seeding, so you can discover a huge pack of different malware after downloading. If circumstances force you to download something from peering networks – scan every downloaded folder or archive with antivirus software.
How to restore files?
WARNING! DO NOT WRITING/CHANGE/DELETE/CRTEATE FILES AFTER ENCRYPTION ATTACK! MAKE SURE THE NAS IS NOT AVAILABLE IN THE INTERNET, DELETE ALL EXPOSED HOST RULES ON YOUR ROUTER!
The files are deleted after archiving and encrypting with 7z and exists in the not-allocated space of your disk. You need to have access to the ssh terminal of your QNAP NAS (you can activate it over the GUI it doesn’t change your data).
- Create a samba share on your windows computer. You should use your Windows account with a password (if your account haven’t one, create it. You can delete it after recovering)
- Login over SSH (Putty on Windows) on your NAS. You should use your admin credentials to login.
- After Login you get a screen with some option. You didn’t need it and press only ‘Q’. (Confirm it with ‘Y’) You should get a shell.
- Connect to your samba share:
mkdir /mnt/rescue-share sudo mount -t cifs -o user=
//XXX.XXX.XXX.XXX/ /mnt/rescue-share cd /mnt/rescue-share - look for your architecture (uname -a) for i386 or x86_64:
Linux NAS-XXXX 4.14.24-qnap #1 SMP Tue Mar 2 06:10:10 CST 2021 x86_64 GNU/Linux
- Download testdisk:
i386: wget https://www.cgsecurity.org/testdisk-7.2-WIP.linux26.tar.bz2 -O testdisk.tar.bz2 x86_64: wget https://www.cgsecurity.org/testdisk-7.2-WIP.linux26-x86_64.tar.bz2 -O testdisk.tar.bz2
- Untar testdisk, go to the directory and change the permissions of the executable:
tar -xvf testdisk.tar.bz2 cd testdisk* chmod +x ./photorec_static
- Search for your volume. Looks like a ‘/dev/mapper/cachedev1‘ (You can use df -h for it) and note it:
Filesystem Size Used Available Use% Mounted on none 300.0M 272.7M 27.3M 91% / devtmpfs 938.4M 8.0K 938.4M 0% /dev tmpfs 64.0M 3.1M 60.9M 5% /tmp tmpfs 949.7M 156.0K 949.6M 0% /dev/shm tmpfs 16.0M 0 16.0M 0% /share /dev/mmcblk0p5 7.7M 46.0K 7.7M 1% /mnt/boot_config tmpfs 16.0M 0 16.0M 0% /mnt/snapshot/export /dev/md9 493.5M 140.1M 353.4M 28% /mnt/HDA_ROOT cgroup_root 949.7M 0 949.7M 0% /sys/fs/cgroup /dev/mapper/cachedev1 898.3G 573.5G 324.3G 64% /share/CACHEDEV1_DATA /dev/md13 417.0M 387.7M 29.3M 93% /mnt/ext tmpfs 48.0M 72.0K 47.9M 0% /share/CACHEDEV1_DATA/.samba/lock/msg.lock tmpfs 16.0M 0 16.0M 0% /mnt/ext/opt/samba/private/msg.sock //XXX.XXX.XXX.XXX/share 1.8T 104.7G 1.7T 6% /mnt/samba_spar_abo_share - Open photorec_static with ‘sudo ./photorec_static‘.
- Choose the /dev/mapper/cachedev1 disk (it should be the disk from step 8).
- Choose the ext2/3/4 partition.
- Choose ext2/ext3 option.
- Choose FREE option.
- Chosse the directory you want on the share (if you follow exactly the steps, you only need to select once ‘..’ and after it press ‘C’)
- Wait and the files would be recovered in folders named ‘recup_dir.X’ on the share.
How to remove Qnap NAS ransomware?
In addition to encode a victim’s files, the Qnap NAS virus has also started to install the Azorult Spyware on system to steal account credentials, cryptocurrency wallets, desktop files, and more.
To ensure the user that ransomware distributors really have the decryption tool, they may offer to decrypt several encrypted files. And they are the single owners of this decryption program: Qnap NAS ransomware is a completely new type, so there is no legit program from anti-malware vendors, which can decrypt your files. But such a situation is in momentum: decryption tools are updating every month.
However, paying the ransom is a bad decision, too. There is no guarantee that Qnap NAS ransomware developers will send you the decryption tool and a proper decryption key. And there are a lot of cases when ransomware distributors deceived their victims, sending the wrong key or even nothing. In the majority of cases, there is a way to recover your files for free. Search for available backups, and restore your system using it. Of course, there is a chance that the backup you found is too old, and does not contain a lot of files you need. But, at least you will be sure that there is no malware in your system. However, to ensure that there are no malicious programs in your system after the backup, you need to scan your PC with anti-malware software.
Qnap NAS ransomware is not unique. There are more ransomware of this type: Bentley, Btcry_zip, Harma. These examples of ransomware act in a similar way: encrypting your files, adding a specific extension, and leaving a great number of ransom money notes in every folder. But there are two things that make difference between these ransomware – cryptography algorithm, which is used for file encryption, and ransom amount. In some cases, victims are able to decrypt their files without any payments, just using free solutions produced by several anti-malware vendors, or even with the decryption tool which is offered by ransomware creators. The last scenario is possible when ransomware distributors have typed your decryption key inside of a ransom money note. However, as you can already guess, such luck is a very rare thing. Ransomware is created for money gaining, not for jokes or scaring.
Reasons why I would recommend GridinSoft2
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes3.
Download Removal Tool.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your system.
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Qnap nas infections and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
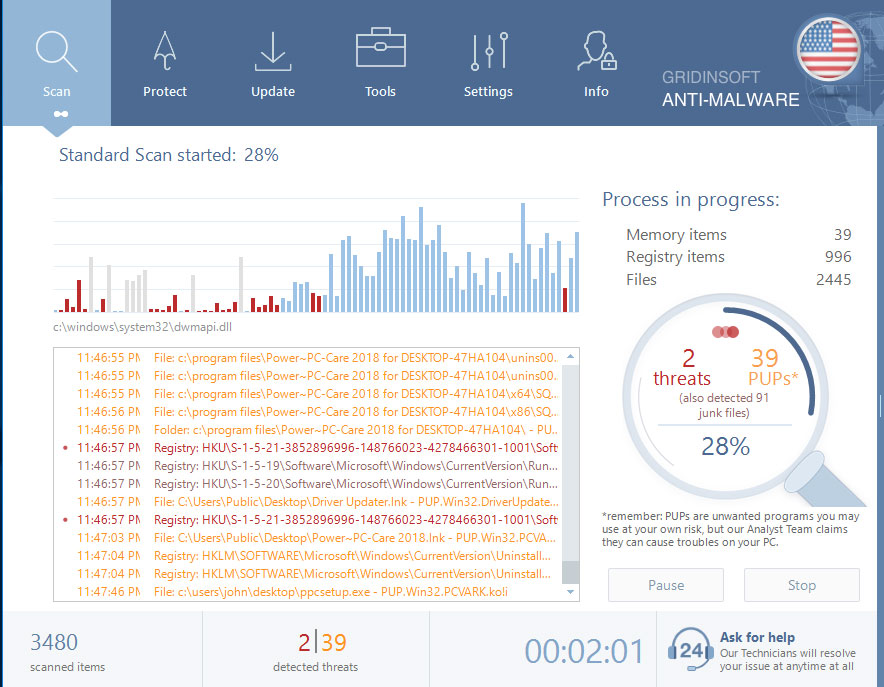
Click on “Clean Now”.
When the scan has completed, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
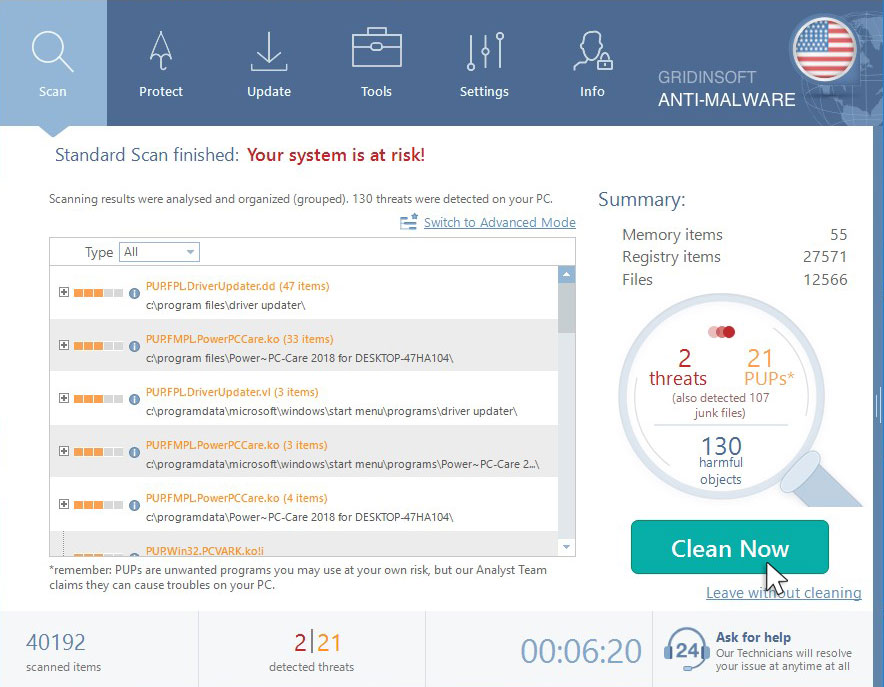
Frequently Asked Questions
If you are suffering from the encryption and the proces is still running you can still get the encryption key by running this command:
cd /usr/local/sbin; printf '#!/bin/sh \necho $@\necho $@>>/mnt/HDA_ROOT/7z.log\nsleep 60000' > 7z.sh; chmod +x 7z.sh; mv 7z 7z.bak; mv 7z.sh 7z;
The encryption key would be stored in /mnt/HDA_ROOT/7z.log which you can then use to decrypt
You can try to find a copy of an original file that was encrypted:
- Files you downloaded from the Internet that were encrypted and you can download again to get the original.
- Pictures that you shared with family and friends that they can just send back to you.
- Photos that you uploaded on social media or cloud services like Carbonite, OneDrive, iDrive, Google Drive, etc)
- Attachments in emails you sent or received and saved.
- Files on an older computer, flash drive, external drive, camera memory card, or iPhone where you transferred data to the infected computer.
Also, you can contact the following government fraud and scam sites to report this attack:
- In the United States: On Guard Online;
- In Canada: Canadian Anti-Fraud Centre;
- In the United Kingdom: Action Fraud;
- In Australia: SCAMwatch;
- In New Zealand: Consumer Affairs Scams;
- In France: Agence nationale de la sécurité des systèmes d’information;
- In Germany: Bundesamt für Sicherheit in der Informationstechnik;
- In Ireland: An Garda Síochána;
To report the attack, you can contact local executive boards. For instance, if you live in USA, you can have a talk with FBI Local field office, IC3 or Secret Service.
How сan I avoid ransomware attack?
Qnap NAS ransomware doesn’t have a superpower.
You can easily protect yourself and your QNAP NAS from injection in several easy steps:
- Ignore all emails from unknown mailboxes with a strange unknown address, or with content that has likely no connection to something you are waiting for (can you win in a lottery without taking part in it?). If the email subject is likely something you are waiting for, check carefully all elements of the suspicious letter. A fake email will surely contain a mistake.
- Do not use cracked or untrusted programs. Trojans are often distributed as a part of cracked software, possibly under the guise of “patch” which prevents the license check. But untrusted programs are very hard to distinguish from trustworthy software, because trojans may also have the functionality you need. You can try to find information about this program on the anti-malware forums, but the best solution is not to use such programs.
- And to be sure about the safety of the files you downloaded, use GridinSoft Anti-Malware. This program will surely be a perfect shield for your personal computer.
I need your help to share this article.
It is your turn to help other people. I have written this guide to help people like you. You can use the buttons below to share this on your favorite social media Facebook, Twitter, or Reddit.
Brendan SmithHow to Remove QNAP NAS Ransomware & Recover PC

Name: QNAP NAS Virus
Description: QNAP NAS Virus is a ransomware-type infections. This virus encrypts important personal files (video, photos, documents). The encrypted files can be tracked by a specific .7z extension. So, you can't use them at all.
Operating System: Windows
Application Category: Virus
User Review
( votes)References
- My files are encrypted by ransomware, what should I do now?
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison