WebArx specialists reported about dangerous vulnerabilities in the WordPress plugins WP Time Capsule and InfiniteWP. Both plugins have already received patches from the developer this month.
According to the researchers, in both cases the attacker was able to bypass authentication. The causes of vulnerabilities boiled down to “logical problems” in the code, exploiting which, an attacker could gain administrator access without having to enter a password.Because authentication bypass vulnerabilities are often logical mistakes in the code and don’t actually involve a suspicious-looking payload, it can be hard to find and determine where these issues come from”, — report WebArx specialists.
Analysts write that the InfiniteWP plugin is currently installed on 300,000 sites, while the official website of the product claims 513,000 installations.
The vulnerability in the plugin was fixed by the developer (Revmakx) on January 8, 2020, with the release of InfiniteWP Client 1.9.4.5. Currently about 167,000 users have installed the patch, however, approximately 130,000 sites are still vulnerable to potential attacks.
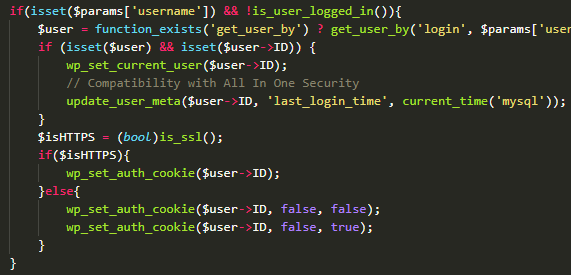
The problem was discovered in the init.php file, in the iwp_mmb_set_request function, designed to verify the authentication of actions that the user is trying to take. However, readd_site and add_site did not perform an authorization check, which allowed any user to obtain administrator rights.
To make the request even reach the vulnerable part of the code, you must first encrypt the payload using JSON, then Base64, and then send it in its original form to the site in a POST request. All you need to know is the username of the site administrator. After sending the request, you will automatically log in as a user”, — write WebARX specialists.
Another authentication bypass, allowing users to log in as administrators, was discovered in another plugin – WP Time Capsule. This plugin is also created by Revmakx and is active on more than 20,000 sites.
The exploitation of the vulnerability in this case was also narrowed to sending a POST request, even without the need for encrypt he payload. The developers also fixed the vulnerability in it on January 8, 2020, and since then almost all users (approximately 19,180) have already updated their installations.
The most effective way to secure a site is to update vulnerable plugins.
Do not limit yourself to WordPress patches and install Windows updates on Tuesday. Judging by the panic in US government agencies and secret agencies, all versions of Windows were open to hacker attacks due to an extremely dangerous vulnerability in cryptographic components.