Open-Source Intelligence (OSINT) is a valuable tool that has become increasingly important in modern surveillance, cyber warfare, and law enforcement. OSINT refers to the collection, analysis, and dissemination of publicly available information. This includes data from social media platforms, news articles, online forums, blogs, and other online and offline sources. The purpose of OSINT is to gather and analyze information that can be used to make informed decisions. These days, that kind of surveillance sees application in a variety of places, from geopolitical conflicts to cyber threats.

Methods and Objects of OSINT
The methods used to collect OSINT vary, but they often include using specialized search engines, web crawlers, and other software tools. All these are needed to weed out unrelated things and have to deal only with relevant information. Analysts may also use social engineering techniques to gather information from individuals or groups. Particular practices of this stream sometimes fall into phishing attacks or impersonation. OSINT analysts also apply traditional investigative techniques, such as interviewing witnesses or using public records.
The example of data that can be gathered from a sole Twitter profile header
The objects of OSINT can vary widely depending on the context in which it is being used. In cyber warfare, open-source intelligence is useful for identifying vulnerabilities in an adversary’s network or gathering information about their personnel and infrastructure. Law enforcement, on the other hand, uses OSINT to track down fugitives, or gather evidence for investigations. However, the range of possible data is much wider for state-backed intelligence. Considering that professional reconnaissance agencies may have interests in different areas, info gathered with OSINT may be related to certain persons and the overall situation in a particular country.
If we go to even lower object levels, OSINT targets will include data from social media, email letters and messengers. These categories of information are the easiest to obtain. Harder things suppose using certain software to extract such data from files. One particular category that can sometimes tell a lot about the target is pictures, which commonly contain metadata. That goes on top of the fact that the exact image may contain a lot of valuable information.
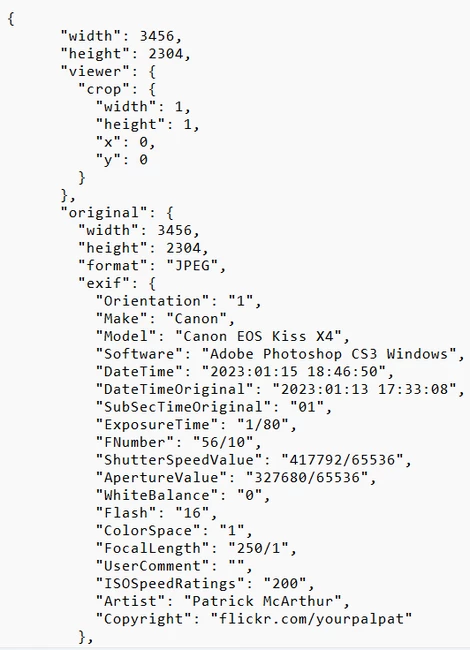
Metadata dumped from a random image. The camera, lens, date, and time are all available in just a couple of clicks
Legal Considerations
It is important to note that the use of OSINT is subject to legal and ethical considerations. In many cases, the collection and use of publicly available information are legal, but there are limits to what can be done with this information. For example, it is illegal to use OSINT to stalk or harass individuals or to conduct surveillance without a warrant. It is also important to ensure that the information collected is accurate and that privacy rights are respected.
Is OSINT comparable to spying?
Some people, especially ones paranoid about their privacy, consider OSINT a sort of spying technique. This, however, is true only in a particular case of using phishing-like tactics to get the needed information. However, phishing itself is not legal. Thus, that is what gives open-source intelligence such a negative coloration in that case. Putting to use only legit, or at least not illegal means, OSINT operations are getting incomparable to spying. Assuming that there are key takeaway points in OSINT and spying differences:
- OSINT is based on the collection and analysis of information that is publicly available. Data people are used to sharing online is the main source of information in this case. Spying, on the other hand, typically involves the collection of information through less than legit means.
- Tools used for OSINT are legal and often open-source, which makes it easier to analyze what exactly the application does. Paid ones still offer technical documentation that describes the capabilities of the software in detail. Meanwhile, spying relies mostly on illegal approaches, like specific types of malware and the aforementioned phishing and impersonation.
- Open-source intelligence is often conducted in an open and transparent manner, with the goal of promoting greater understanding and knowledge-sharing. Spying is generally done in secret and creates a significant resonance when uncovered.
Software Solutions Used in Open-Source Intelligence
There are a variety of software tools and platforms that can be used for OSINT. Some of the most commonly used tools include search engines such as Google and Bing. The only difference to normal use is applying specific filters to each request, called dorks. There are also social media monitoring tools and specialized OSINT software. Most of the specialized tools are created only for Linux platforms, which makes them less accessible. These tools can be used to collect and analyze information from a wide range of online sources. Actually, the list of tools goes further, including dozens of possible solutions, both one’s wiht wide capabilities and narrow-oriented.
Examples of application software used for OSINT operations
| Name | Description |
|---|---|
| Maltego | Maltego is a data visualization tool that allows users to gather and analyze information from a wide range of online sources. It captures data from social media platforms, online forums, and databases. The tool is particularly useful for identifying relationships between different entities. |
| Shodan | Shodan is a search engine that allows users to search for internet-connected devices, such as routers, cameras, and servers. This tool is particularly useful for identifying vulnerable or insecure devices that may be at risk of cyber attacks. |
| Hunchly | Hunchly is a web capture tool that allows users to capture and preserve online content, such as web pages and social media posts. This tool is particularly useful for investigators and researchers who need to document and preserve content. |
| IntelTechniques | IntelTechniques is a suite developed by privacy expert Michael Bazzell. The suite includes various tools for data collection and analysis, including search engines, social media monitoring tools, and email tracking tools. |
| Foca | Foca is a tool that allows users to extract metadata from various types of digital files, such as documents, images, and videos. This tool is particularly useful for analyzing and identifying the sources of leaked documents and other sensitive information. |
OSINT Role in Intelligence and Warfare
Reconnaissance became a major part of any warfare long ago. With time, information transferred from paper documents to electronic form, making it easier to protect – and harder to get your hands on. However, a global network allows anyone to gather a huge volume of information without even leaving a room. Moreover, such information is not less useful than one collected by espionage operations or hackery. Using one or a set of tools from the ones we mentioned above, it is possible to get information about enemy losses, location of troops, headquarters, and so on.
The ongoing Russia-Ukraine war revealed these almost endless capabilities of open-source intelligence application for classic intelligence. Both sides managed to use OSINT to locate the troops, repair workshops, dormitories, ammo warehouses – essential things that should before be found by sending recon troops. Same approach is applied to correct shellings and missile strikes. A major part of the OSINT efficiency is provided because war is considered the most widely displayed in social media. Each day new and new footage appears – and open-source recon specialists will take advantage of that if possible.
