The official Monero cryptocurrency website, GetMonero[.]Com, which provides binaries for Linux and Windows, has been hacked and distributed a malware that is able to steal user’s funds.
The incident occurred on November 18, 2019. Users first discovered something strange and hastened to report on GitHub.
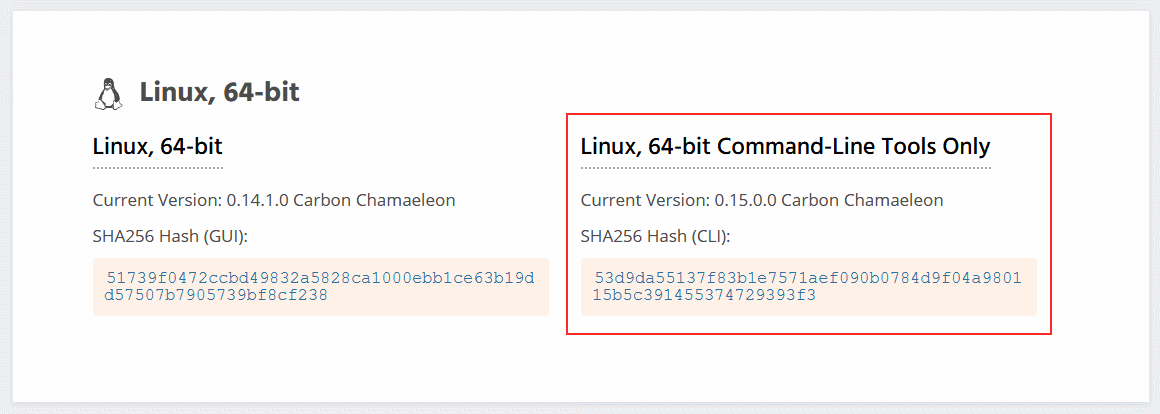
The fact is that the hash (SHA256) of the 64-bit Linux binary did not match the hash indicated on the official website, which meant that the file was changed. Soon after this message, Monero developers confirmed the fact of compromise on the official Twitter.
Everyone who downloaded the CLI wallet from the site on November 18, from 2:30 UTC and 16:30 UTC, is strongly recommended to check the hashes of the binary files. If they do not match the official ones, delete the files and download them again. Never run compromised binaries”, – warn the developers.
At least one user has already reported to Reddit about the loss of funds because of this attack, thereby confirming that the malware was aimed at stealing funds.
About nine hours after I launched the binary, one transaction emptied my wallet and withdrew all 7,000 dollars”, — the victim writes.
An analysis of Linux malware shows that after a user opens or creates a new wallet, his seed is passed to the node.hashmonero[.]Com server. Then the malware sent funds from the wallet to the servers node.xmrsupport[.]Com and 45.9.148[.]65. The malicious CLI wallet for Windows acted in much the same way.
Little is known about the attack itself, but Monero developers are already investigating what happened. How exactly the server was compromised is unclear, but it is reported that now there is nothing to fear, since all the files are distributed from the backup source.
Recommendations:
Always check the integrity of the binaries you download!
If you downloaded binaries in the last 24h, and did not check the integrity of the files, do it immediately. If the hashes do not match, do NOT run what you downloaded. If you have already run them, transfer the funds out of all wallets that you opened with the (probably malicious) executables immediately, using a safe version of the Monero wallet (the one online as we speak is safe — but check the hashes).
Read also: Adware malware masks itself as an ad blocker
More information will be posted as several people are currently investigating to get to the bottom of this.
Correct hashes are available here (check the signature).