Engineers from the Canadian company MoFi Network have reported fixing six vulnerabilities in their devices, but there are several more backdoors available for attack.
Four issues found by researchers in May 2020 remain unresolved, including three hard-coded backdoors and one issue related to command injection. These bugs are dangerous for devices of the MOFI4500-4GXeLTE business series.
CRITICAL START specialists discovered the problems in the firmware of MoFi Network routers, but have now disclosed the details of the vulnerabilities in their blog, and previously notified US-CERT about their findings.
Multiple critical vulnerabilities have been discovered in the MoFi4500 router, an OpenWRT-based wireless router that provides Internet access via LTE. The initial vulnerabilities were reported to the vendor and patches were made available; however new critical vulnerabilities were subsequently introduced as a result. Several firmware versions have been released, but some of the vulnerabilities have not been fully patched”, — write CRITICAL START company specialists.
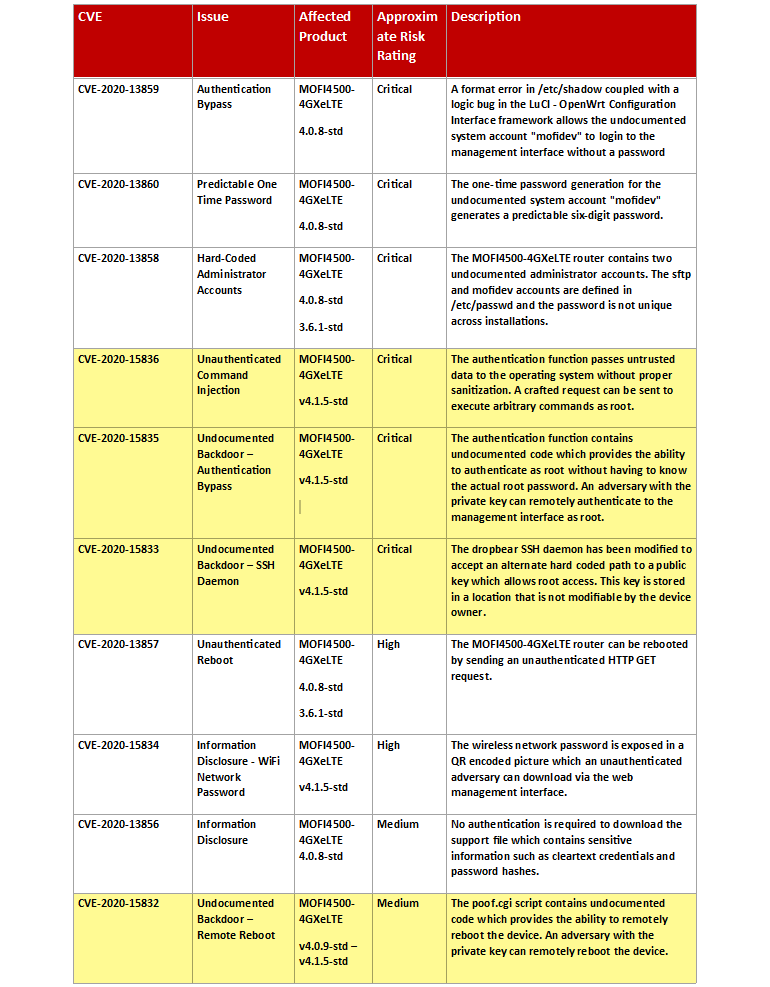
As you can see in the table below, most of the discovered bugs found were critical, including bypassing authentication, generating predictable passwords, leaking information, and so on. Issues with no fixes are highlighted in yellow. At the same time, the developer company does not comment on the situation in any way, that is, it is unclear when to expect the release of patches (if they appear at all).
CRITICAL START researchers note that majority of unpatched bugs are backdoors, which means that they can be very attractive to botnet operators.
To exploit these issues, an attacker would need to have a direct connection to the device’s web-based management interface, which the researchers said is accessible by default over both the LAN and WAN”, – say CRITICAL START specialists.
It is noted that Internet providers often use MOFI4500-4GXeLTE devices, some of which have minimal protection that blocks attacks from intruders, but, unfortunately, this also does not completely protect against attacks. For example, in some cases, a vulnerability can be used indirectly: if a user clicks on a link or visits a malicious website.
One of the scenarios for such an attack is the injection of malicious code into advertising. When an employee of an ISP contacts a website with an advertisement of the attackers, the malicious code will run inside their browser located on the ISP’s local network, and the MOFI4500-4GXeLTE router will still be compromised.
CRITICAL START specialists noticed that since June 25, 2020, the number of MOFI4500-4GXeLTE devices available via the Internet has decreased by more than 40% (from 14,000 to 8,200 devices), despite the absence of patches. Researchers believe this is the result of US-CERT’s work with ISPs.
Recall that we recently talked about how hundreds of millions of IoT devices are in danger due to the vulnerabilities of Ripple20.