The Mailto (NetWalker) ransomware family has learned how to deploy and run its own malicious code in a legitimate Windows Explorer system process.
Due to this tactic, the ransomware successfully bypasses detection with antivirus tools.
A strain of the Mailto (NetWalker) ransomware can inject malicious code right into Windows Explorer, researchers at security solutions company Quick Heal discovered. By using a technique of “process hollowing” to achieve this process code injection, the ransomware actors hope to evade detection”, — writes Forbes IS-observer Davey Winder.
For the first time, cybersecurity researchers spotted Mailto in August 2019. The ransomware got its name because of the extension that it adds to encrypted files.
After delving into the analysis of the malware, experts came to the conclusion that its authors call it otherwise – “NetWalker“. Additionally, experts said that Mailto attacks not only ordinary users, but also seeks to penetrate corporate networks, and then to encrypt all connected devices.
More recently, cryptographic developers have equipped their brainchild with the ability to hide code in the Windows Explorer process.
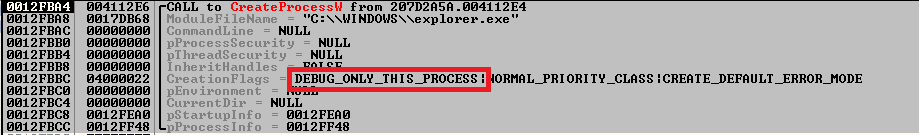
To do this, the malware uses an interesting technique: Mailto starts the process in debug mode, after which it uses a special API like WaitForDebugEvent to inject malicious code. As a result, the completely legitimate system process explorer.exe will execute a malicious load.
All of which is bad news, as NetWalker is as nasty as it is sophisticated, targeting both home and business Windows users alike. After the ransomware runs its encryption routines, “explorer.exe kills the parent process and deletes the original sample,” the file that has been dropped as well the RUN entry, the researchers said, “eradicating the traces of its existence”, — writes Davey Winder.
Researchers at Quick Heal shared a screenshot that clearly shows the ransomware code injection:
Viruses and ransomware quickly “grow wiser” that causes anxiety of IS experts: just recently we wrote that, for example, Ryuk ransomware uses Wake-on-LAN to “awake” devices before attack.
How to avoid the Mailto threat (NetWalker)?
Although the infection method for this NetWalker ransomware strain has not yet been detected, it is believed that spam and phishing emails will be the most likely route. Thus,we can give the usual tips to avoid the threat:
- Be careful when opening attachments and when clicking on links in suspicious letters.
- In protecting your systems from such attacks may also be useful security solutions using behavioral detection methodologies.
- In addition, regularly back up files using a combination of methods including at least one remote site.