Currently, Lokas ransomware attacks a wide range of computers in various parts of the world. The degree of its distribution and the severity of the infection definitely requires for you to react immediately before Lokas turns all your important data into files that cannot be opened.
This article intends to assist you in deleting Lokas Virus Ransomware at no cost. Our guide also shows how any Lokas file can be restored.
Lokas – How bad is it?
Lokas can be described as a typical ransomware-type threat.
The infection originates from the Djvu ransomware family. Lokas is not much different from other ransomware samples. So it encrypts all popular file types. As soon as the certain file is encrypted users are not able to open it. Lokas sets the “.lokas” extension into each file it encrypts. For instance, the file “my-photo.jpg”, upon being encrypted by Lokas, will be changed into “my-photo.jpg.lokas”. Upon the encryption completion, Lokas generates a specific text file (for example “_readme.txt”) and puts it into every folder where the encrypted information is stored.
The scary notification produced by Lokas warning demanding for the ransom to be paid is literally the same as the alerts presented by other ransomware samples that derive from the Djvu family. It basically indicates that the data is encrypted by it and that the only remedy to decrypt it is to apply a one-of-a-kind decryption key (decryptor). It is quite regretful to admit that this is an absolutely true statement.
The variant of the cryptography method implemented by Lokas is yet not duly researched. At the same time, it is definitely true that each user whose data got encrypted may be issued a special decryption key, which is absolutely unique and there are no other variations of it. It is quite unlikely that users will manage to recover the data without the key in place.
Once Lokas is active it is impossible for people to get access to the key, which is located on a remote server controlled by the criminals related to Lokas ransomware.
In order to obtain the key and restore the necessary data users are forced to actually pay the ransom, which equals to $980. To get the payment information users are told to get in touch with the criminals by means of sending an email or by telegram.
The warning also states that the victims should contact the Lokas representatives within 72 hours beginning from the moment of data encryption. The alert indicates that by contacting within 72 hours people will be given a 50% rebate, thus the ransom figure will be decreased to $490). However, no matter what the requested sum is, you should not pay the ransom!
What about paying the Lokas ransom?
If you believe that paying the demanded ransom is the only solution, we need to mention a few things peculiar to that option. The crook who is using the Ransomware virus tool definitely wants you to believe that there is truly no other way-out to restore the data.
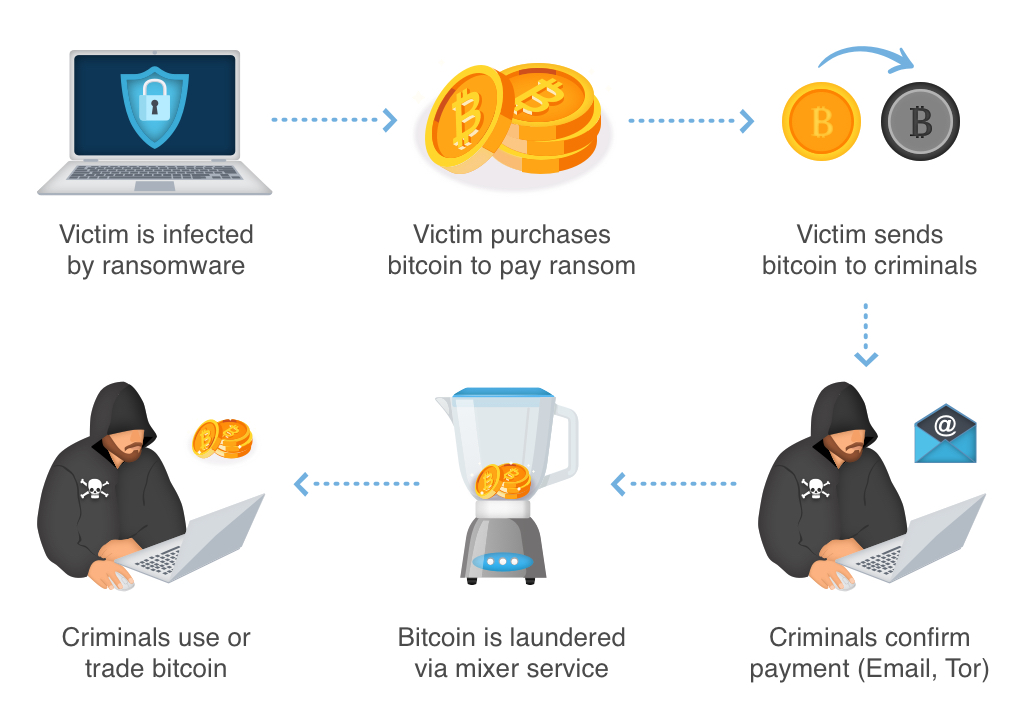
Definitely, as you might think, the ransom is generally meant to be transferred under certain specific pre-defined regulations and rules. Often this is done by means of Bitcoins as a transfer currency. The application of Bitcoins is often the preferred way by cyber frauds because such transfers are extremely unlikely to get tracked.
Due to this feature of the bitcoins, they are often applied by hackers that intend to scare the targeted users by using Ransomware. The use of such hard-to-track virtual currency is the key factor why almost all Ransomware frauds manage to remain anonymous after successfully completing their covetous fraudulent goals.
However, in many cases, even the payment of the demanded ransom might not assist the virus victims as it is quite likely that they may not get any file-decryption data. In events like these, it is very important that the user tries all other available options that might be in place – paying the money is most certainly not the good idea and must not be the main solution.
Online crooks cannot be trusted, they totally don’t care what you feel about the trouble with your data, even when you do pay the ransom. For this reason, paying the amount asked by these frauds does not bring you to the positive resolution of your problem. So, you just waste your hard-earned funds for nothing.
I definitely recommend that you do not get in touch with these frauds and do not send money into their pockets. Currently, there are no applications capable of cracking Lokas ransomware or restoring the encrypted information at no cost. Hence, the only feasible solution is to restore the lost information from the backup, as long as it is available.
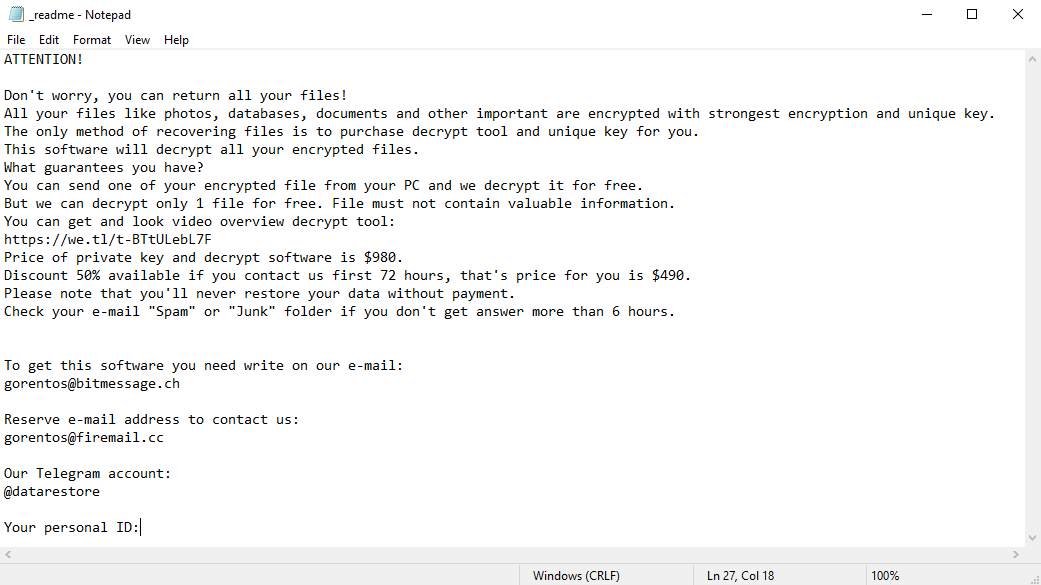
The scary alert demanding from users to pay the ransom to decrypt the compromised data contains these frustrating warnings
You ought to be aware that the online realm currently is full of infections that look pretty much the same as the Lokas virus. Hazardous applications classified as ransomware are generally developed to encrypt crucial files and to express the demand before the victim to eventually transfer the ransom amount into the pockets of the frauds standing behind them.
The feature of all such ransomware infections is that they refer to a similar mechanism for generating the standalone decryption key to decrypt the compromised data.
Hence, unless the ransomware is still under development or has some concealed flaws, manually restoring the data is something you can’t really do. The only remedy to avoid the loss of your important files is to permanently make backups of your important data.
Keep in mind that even if you make such backups, they must be immediately put into a special location not associated with your main workstation.
For example, the backup may be stored on the USB flash drive or some other external hard drive device. Alternatively, you may use the service of online (cloud) data storage.
Of course, when you keep your backup data on your regular system, it may be easily encrypted as well as other documents.
Hence, storing the backup on your main computer is definitely not a reasonable decision.
How does Lokas attack the PC?
Lokas used different methods to inject its roots into the system. It is not really certain what particular method was used to infiltrate your computer.
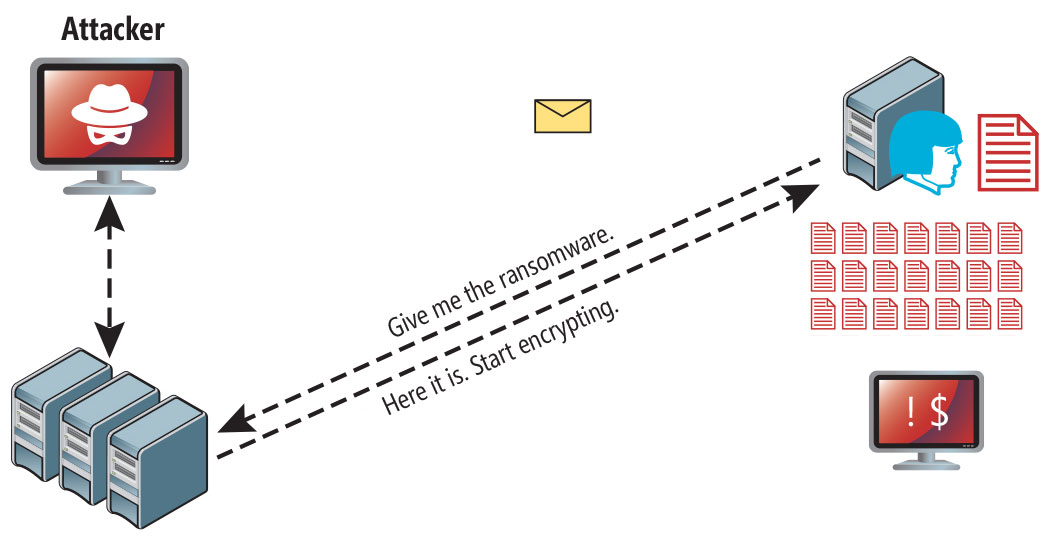
Lokas ransomware attack following a successful phishing attempt.
- concealed installation together with other programs, especially the ones promoted on a free basis;
- links to Lokas contained in unsolicited spam mail;
- online free hosting services;
- illegal crack downloads from peer-to-peer (P2P) resources.
There were instances when Lokas ransomware was introduced as some legit app, for example, in the alerts suggesting to perform some necessary software or browser updates. This is typically how some online crooks aim to convince you into injecting Lokas threat manually, through your direct role in the installation procedure.
Of course, the fake update alert will not mention that you are going to install ransomware. This installation will be masked under some claim stating that supposedly you need to update Adobe Flash Player or some other suspicious software.
Needless to mention, the cracked programs are not safe either. It is illegal to download them in the first place, but additionally, they may inject dangerous applications into your system, including Lokas ransomware.
So, what can you do to prevent Lokas from injecting its malicious roots into your system. In spite of the fact that there is no 100% guarantee to prevent your computer from getting infected. There are some recommendations I want to give you to avoid Lokas intrusion. You ought to be careful while installing free applications.
Take time to read what the installers suggest in addition to the main free software. You also need to be careful not to open insecure email attachments. Especially if you are not familiar with the sender. It is very important that your existing anti-virus software is properly updated.
As mentioned, some malicious utilities in the system may perform their dangerous functions in a secret form in your system. I recommend that you scan your system with the proper anti-malware software to identify possible leaks in your system security.
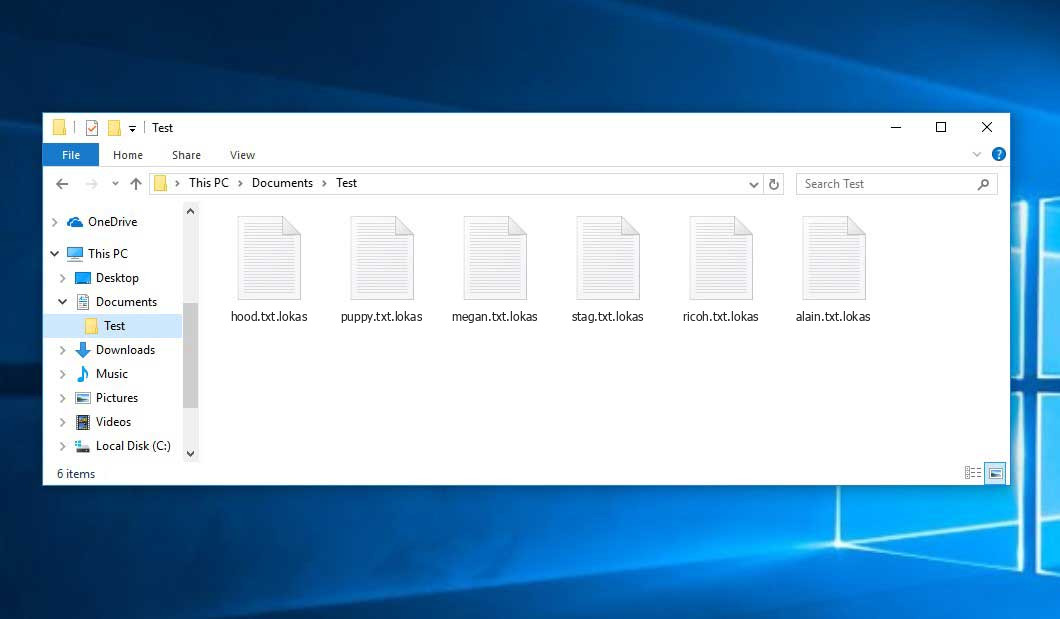
ATTENTION! Don't worry, you can return all your files! All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key. The only method of recovering files is to purchase decrypt tool and unique key for you. This software will decrypt all your encrypted files. What guarantees you have? You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information. You can get and look video overview decrypt tool: https://we.tl/t-BTtULebL7F Price of private key and decrypt software is $980. Discount 50% available if you contact us first 72 hours, that's price for you is $490. Please note that you'll never restore your data without payment. Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours. To get this software you need write on our e-mail: [email protected] Reserve e-mail address to contact us: [email protected] Our Telegram account: @datarestore Your personal ID: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXThe image below shows files with “.lokas” extension appended by the Lokas ransomware:
How to remove Lokas infection?
In addition to encode a victim’s files, the Lokas virus has also started to install the Azorult Spyware on computer to steal account credentials, cryptocurrency wallets, desktop files, and more.
Reasons why I would recommend GridinSoft
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes. Here is my short review about it:

Gridinsoft Anti-Malware Review 2025 – Is It Worth It?
In today’s digital landscape where malware evolves at breakneck speed, finding reliable protection has never been more crucial. After spending weeks testing Gridinsoft Anti-Malware, I’ve discovered a security tool that strikes an impressive balance between effectiveness and resource efficiency. While many security solutions bloat their offerings with countless features, Gridinsoft takes a refreshingly different approach. […]
Download GridinSoft Anti-Malware.
You can download GridinSoft Anti-Malware by clicking the button below:Run the setup file.
When setup file has finished downloading, double-click on the install-antimalware-fix.exe file to install GridinSoft Anti-Malware on your computer. An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your computer for Lokas infections and other malicious programs. This process can take a 20-30 minutes, so we suggest you periodically check on the status of the scan process.
Click on “Clean Now”.
When the scan has completed, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.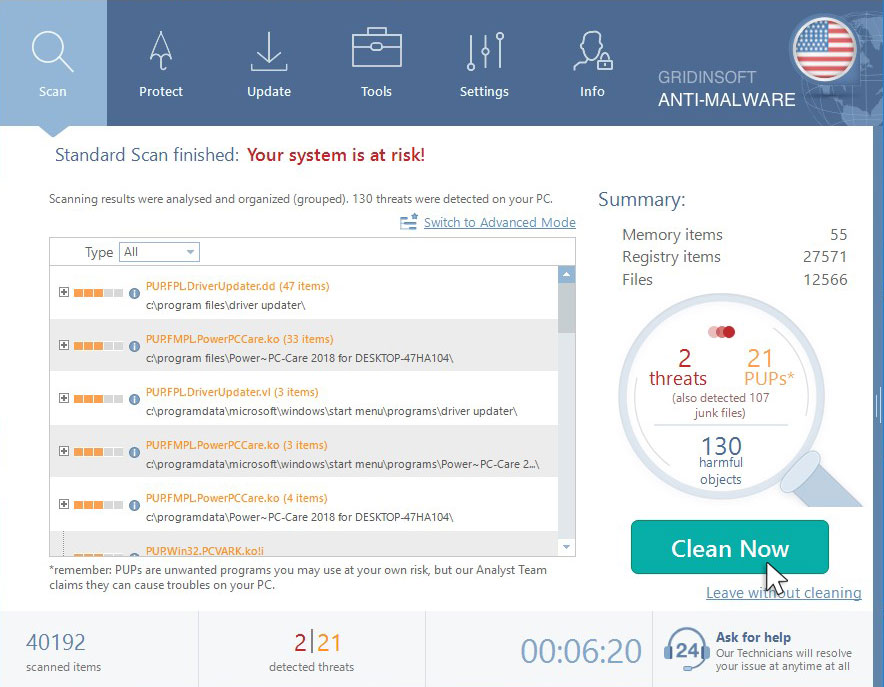
How to decrypt .Lokas files?
Encryption specialist Michael Gillespie (USA) managed to create his decoder for some versions and variants of this family ransomware (cezor, litar, nusar, and others).
It work when the lokas virus used an offline key for encryption.
You can download free decryption tool here: STOPDecrypter. This tool includes a BruteForcer only for variants which use XOR encryption, a simple symmetric cipher that is relatively easy to break. The decrypter tool requires victims to provide an encrypted and original file pair greater than 150KB.
Download STOPDecrypter tool:
Extract STOPDecrypter tool to your Desktop folder:
Run STOPDecrypter tool:
Remember: STOPDecrypter should be run as an Administrator from the Desktop.


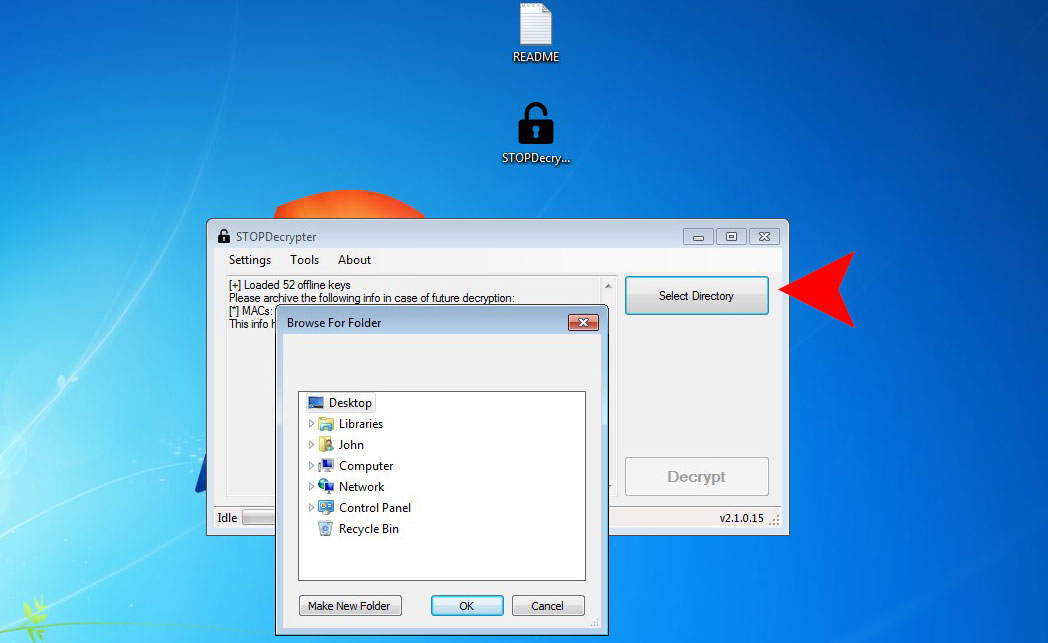
Please, save the ID, Personal ID and MAC addresses. Then make “Full scan” with GridinSoft Anti-Malware on infected system.
Next, backup all encrypted files via CryptoSearch (Link for download http://bit.ly/2JAvbyE)
If the key will found in the future, you will able to decrypt your files even using another computer.
Don’t forget change all your passwords on infected PC! Read more why you need: https://howtofix.guide/azorult-spyware-comes-with-djvu-ransomware/
[!]No keys were found for the following IDs:
[*] ID: y4FaoWle3kpRzzIDNZeHh5ekNkf1lh9OpcIHpUHC (.godes )
Please archive these IDs and the following MAC addresses in case of future decryption:
[*] MACs: 94:DE:80:49:31:6F, 50:3E:AA:0A:A9:ED, 0A:00:27:00:00:11
This info has also been logged to STOPDecrypter-log.txt