LockBit ransomware group announced the hacking of TSMC (Taiwan Semiconductor Manufacturing Company) — the world’s largest contract manufacturer of microschemes.
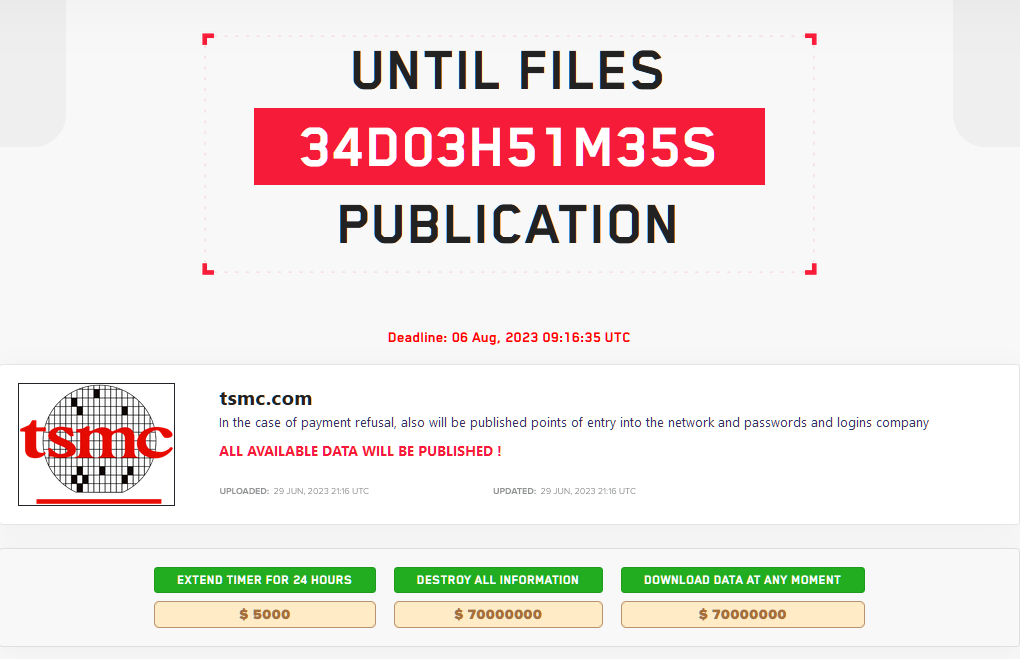
The criminals demand a ransom of 70,000,000 dollars and promise not to merge the stolen data into the network if they pay. The company denies the fact of the attack, stating that one of its suppliers encountered a «cyber incident».
I’ll remind you that we also reported that LockBit Claims to Have Hacked a Foxconn Plant in Mexico, and also that the New LockBit attack lasted for half a year.
Media also wrote that LockBit Releases World’s First macOS Ransomware.
Last week, an attacker associated with the LockBit group, known as Bassterlord, started tweeting about an extortion attack on TSMC, publishing screenshots with information about the company. These screenshots demonstrated that hackers had access to systems presumably belonging to TSMC, access to applications, and also contained account data for various internal systems and email addresses.
Although this thread was soon deleted from Twitter, a new entry dedicated to TSMC actually appeared on the LockBit site in the darknet. The hackers declared that they stole data from the company and demanded 70 million dollars, otherwise they threatened to publish the stolen information in the open, including account data for the semiconductor giant’s systems.
TSMC representatives have already responded to the attackers’ statements and told the media that the information about the hack does not correspond to reality. The company explained that the incident affected the systems of one of TSMC’s IT equipment suppliers, Kinmax Technology.
TSMC also emphasized that right after the incident, the company “immediately terminated the exchange of data with the affected supplier”. The producer reports that the investigation of the incident is still ongoing, and law enforcement agencies are already participating in it.
Shortly after this, representatives of Kinmax Technology released their own statement, saying that on June 29, 2023, a compromise of some test environment was discovered, and the attackers really managed to steal data, mainly related to the installation information that the company provides to customers along with the installation manuals.
Kinmax Technology writes that after detecting the attack, it immediately disabled the compromised system and notified the affected client about what happened.

