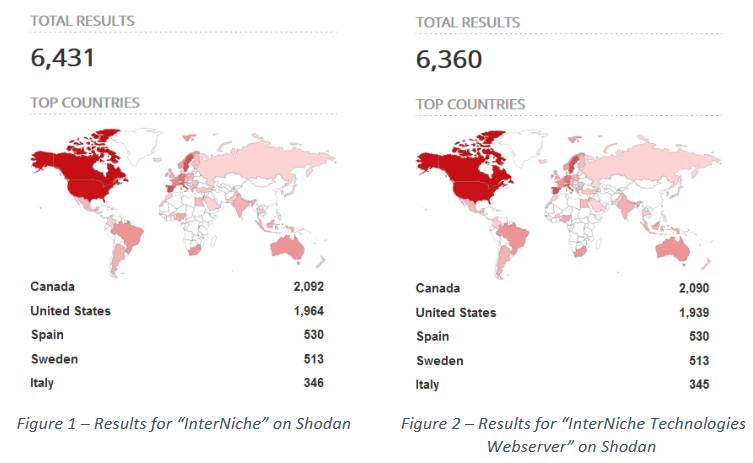
Forescout and JFrog have disclosed 14 vulnerabilities in the NicheStack TCP/IP library known as INFRA: HALT. This library is used in industrial devices from more than 200 manufacturers, and according to researchers, there are currently about 6400 vulnerable devices available on the network.
NicheStack is a small library written in C and developed by HCC Embedded. It can be added to the device’s firmware, and it can support internet connectivity and other network functions.Such TCP/IP stacks are used on almost all modern devices, but their code has not been subjected to security checks in recent decades.
After discovering the problems of URGENT/11 and Ripple20 in 2019-2020, the Forescout team launched the Memoria project, in which researchers began to study the security of all popular TCP/IP stacks today. This initiative has already helped to identify the Amnesia:33 and NUMBER:JACK bug sets, and now INFRA:HALT is the third.
Whereas experts previously focused on the more common TCP/IP stacks used with routers, IoT and web servers, Forescout and JFrog analysts have now turned their attention to a library commonly used in industrial equipment in factories, mines, pipelines, water treatment plants and others. critical infrastructure.
Some of the vulnerabilities included in INFRA: HALT scored more than 9 out of 10 on the CVSS 3.1 scale. The bugs allow remote execution of arbitrary code, lead to denial of service, information leaks, TCP spoofing and DNS cache poisoning.
Alas, many companies intentionally or accidentally make their equipment available over the Internet. For example, the researchers found more than 6400 devices available on the network and vulnerable to INFRA: HALT problems (including CVE-2020-25928 and CVE-2021-31226, which allow attackers to take full control of the device).
HCC Embedded developers have already prepared fixes for all bugs discovered by specialists. But practice shows that while these patches turn into firmware updates, and then the firmware is deployed on devices, it will take a long time, and attackers will still be able to use INFRA: HALT for their attacks.