Calling themselves “Memento team“, actors use Python-based ransomware that they reconfigured after setbacks.
Operators of the new ransomware have figured out how to block files when the victim uses special protection against such malware.
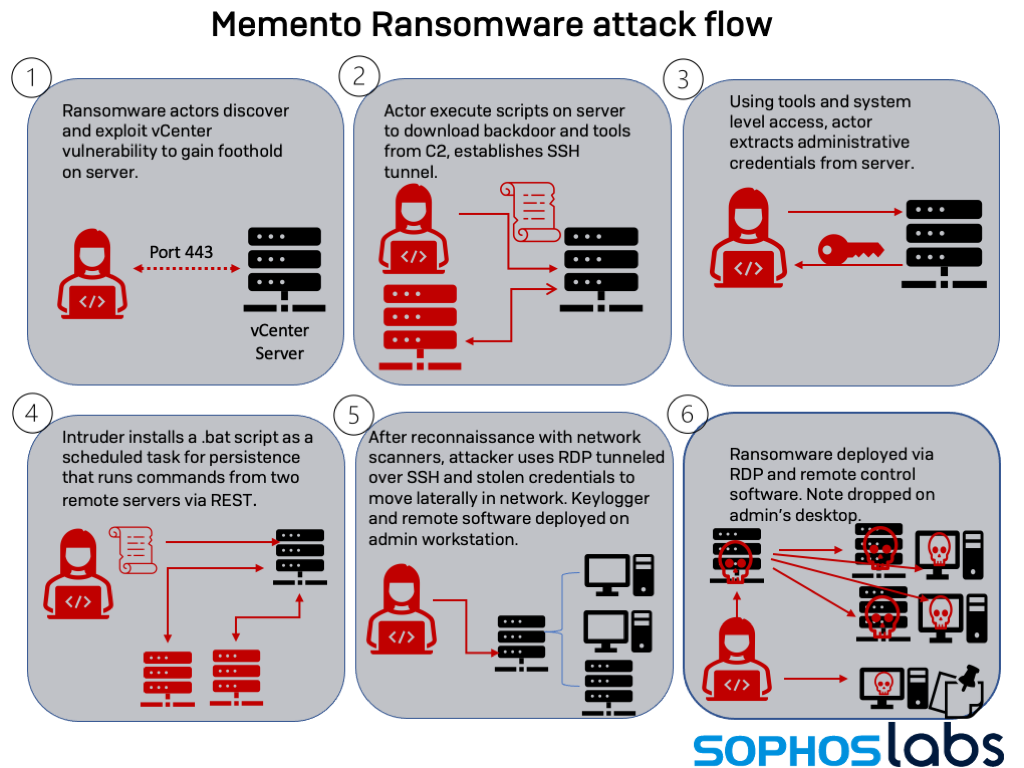
Analysis of the October attacks in Sophos showed that in order to avoid such interference, attackers now archive targeted data using WinRAR and set an access password. Memento penetrates the target network using the CVE-2021-21972 exploit for VMware vCenter. The patch for this RCE vulnerability was released back in February, but not all users bothered to install it.
Having secured themselves on the compromised server, the attackers create an SSH tunnel, extract the admin credentials, and begin to move through the network using RDP. Having finished their reconnaissance, the hackers carefully erase the traces of their activities using the BCWipe utility and launch the ransomware.
This malware written in Python 3.9 first archived files using WinRAR and then encrypted them using AES. However, the latter action often triggered antivirus protection tailored for this behavior, and Memento had to adjust its code.
Now the malware does not use the encryptor, it only uses WinRAR, assigning the .vaultz extension to the results. A password is generated for each archive, which is then encrypted using RSA.
The originals of the archived files are deleted, and a ransom note is placed on the admin’s desktop – a total of 15.95 BTC (about $ 1 million) or 0.099 BTC for each document. The format and text of this message, according to Sophos, are borrowed from REvil, for communication the hackers offer contacts in Telegram and Protonmail.
The victims of attacks that came to the attention of experts did not pay the ransom – they restored their files from backups, having worried about creating a backup in advance.