Google Cloud Threat Intelligence announced the release of YARA rules, as well as a collection of indicators of compromise VirusTotal, which should facilitate the detection of Cobalt Strike components and prevent abuse of this pentest tool.
By the way, we wrote that some Hackers Are Switching from Cobalt Strike to Brute Ratel C4.Let me remind you that Cobalt Strike is a legitimate commercial tool created for pentesters and the red team and focused on exploitation and post-exploitation.
It is probably well known to most readers, but, unfortunately, hackers has long loved Cobalt Strike, ranging from government APT groups to ransomware operators (as we wrote, Ransomware operators use Cobalt Strike in 66% of cases). Although it is not available for ordinary users and the full version is estimated to cost several thousand dollars per installation, attackers still find ways to use it (for example, rely on old, pirated, hacked and unregistered versions).
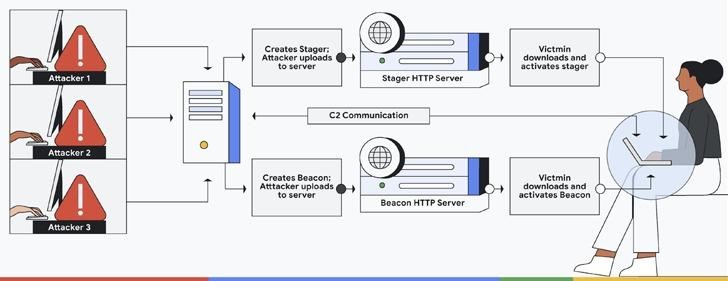
As explained by Google, the hacked and “leaked” variations of Cobalt Strike in most cases are at least one version behind, which allowed the company to collect hundreds of stagers, templates and samples of beacons used by hackers, and on the basis of them create YARA rules.
The experts found Cobalt Strike JARs from version 1.44 (released around 2012) to version 4.7 and then used the components to create YARA rules. According to experts, each version of Cobalt Strike contains from 10 to 100 binaries of attack patterns. They managed to find 34 different versions of Cobalt Strike with 275 unique JAR files. In total, more than 340 binaries were studied, for which detection signatures were created.
According to Sinclair, the idea was to “eliminate the bad versions while leaving the legitimate ones intact”. Google experts write that they want to return the tool to the red team and pentesters, making it more difficult for attackers to use it.
The experts also shared a set of signatures for detecting Sliver, a legitimate open-source platform for emulating the actions of attackers. It is also aimed at pentesters, but attackers often use it as an alternative to Cobalt Strike.

