Cybercriminals began to use an interesting method to extract confidential data from the system of the attacked user. In this, they are helped by the direct injection of malicious extensions for the Google Chrome browser on Windows systems. The main goal of attackers in this campaign is to gain control and manipulate victim data that is used in internal web applications.
According to experts from the SANS Institute 1, attackers avoid using the Chrome Web Store 2 and implement add-ons with their own hands. The malicious extension for Google Chrome was named Forcepoint Endpoint Chrome Extension for Windows. Cybercriminals use the logo of Cybersecurity company Forcepoint to create legitimacy.
Unfortunately, the SANS Institute report does not mention the original way attackers entered the victim’s system. As the experts explained, it was not in vain that the attackers chose malicious extensions, and not standard binaries. The thing is that today almost everything can be controlled through web applications. This means that all data an attacker need is easily retrieved, even if the attack surface is narrowed down to web applications.
How to remove Fake Forcepoint Chrome Extension?
- Download and install GridinSoft Anti-Malware.
- Open GridinSoft Anti-Malware and perform a “Standard scan“.
- “Move to quarantine” all items.
- Open “Tools” tab – Press “Reset Browser Settings“.
- Select proper browser and options – Click “Reset”.
- Restart your computer.
Browser hijackers are usually pretty simple to remove. Most of the time, they have a separate application that can be located in the list of installed applications. Due to the certain marketing method of Fake Forcepoint hijacker, it can be conveniently tracked and erased manually. Nonetheless, if you got Fake Forcepoint in the bundle with a free program, your personal computer may be contaminated with much more dangerous malware – trojans, spyware and even ransomware. That’s why I’d recommend you utilize anti-malware programs to delete the Fake Forcepoint PUA and all various other malware.
You can utilize Microsoft Defender3 – it is capable of discovering and eliminating various malware, including mentioned hijacker. Nevertheless, significant malware, that might exist on your PC in the specified instance, can disable the Windows antivirus program by modifying the Group Policies. To minimize the chanse of such situations, it is better to use GridinSoft Anti-Malware.
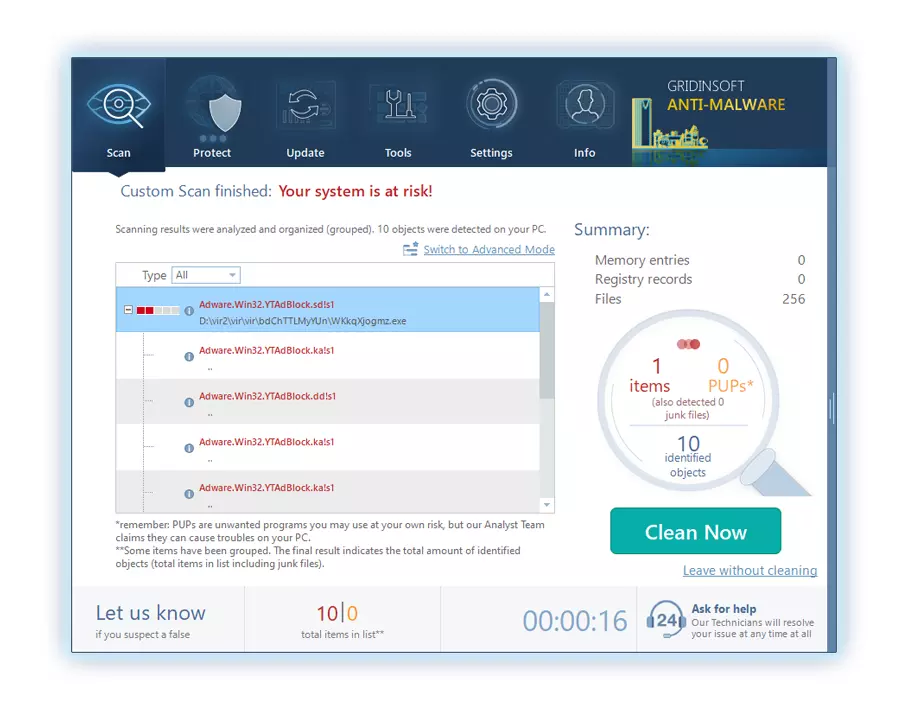
To detect and erase all malicious applications on your desktop with GridinSoft Anti-Malware, it’s better to use Standard or Full scan. Quick Scan is not able to find all the malware, because it checks only the most popular registry entries and folders.
You can spectate the detected malicious programs sorted by their possible hazard simultaneously with the scan process. But to perform any actions against the viruses, you need to wait until the scan is finished, or to stop the scan.
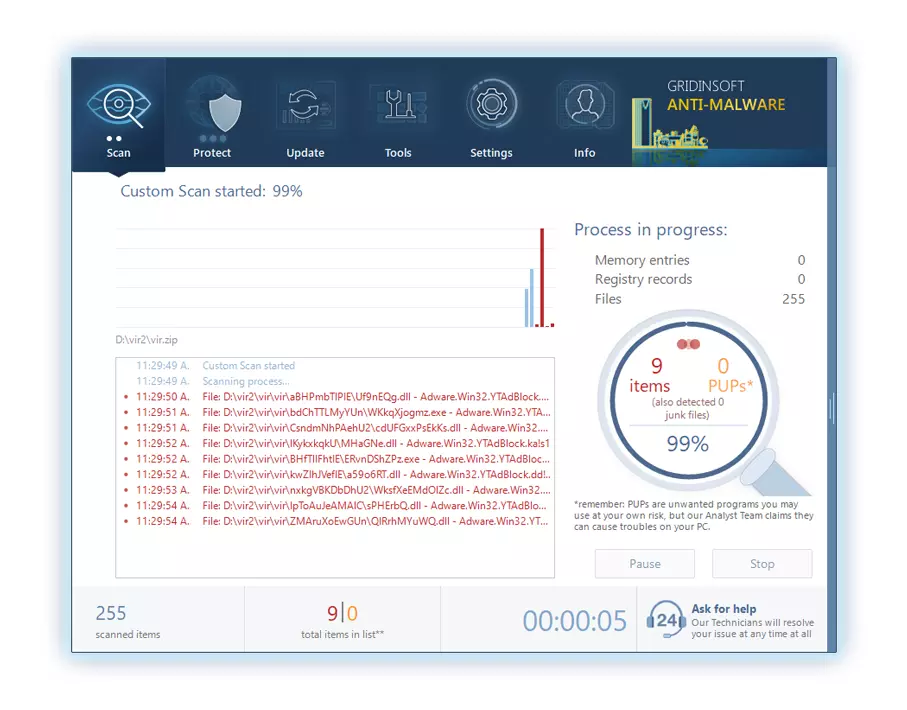
To choose the action for every spotted virus or unwanted program, click the arrow in front of the name of the detected malicious program. By default, all malware will be removed to quarantine.
Reset browser settings to original ones
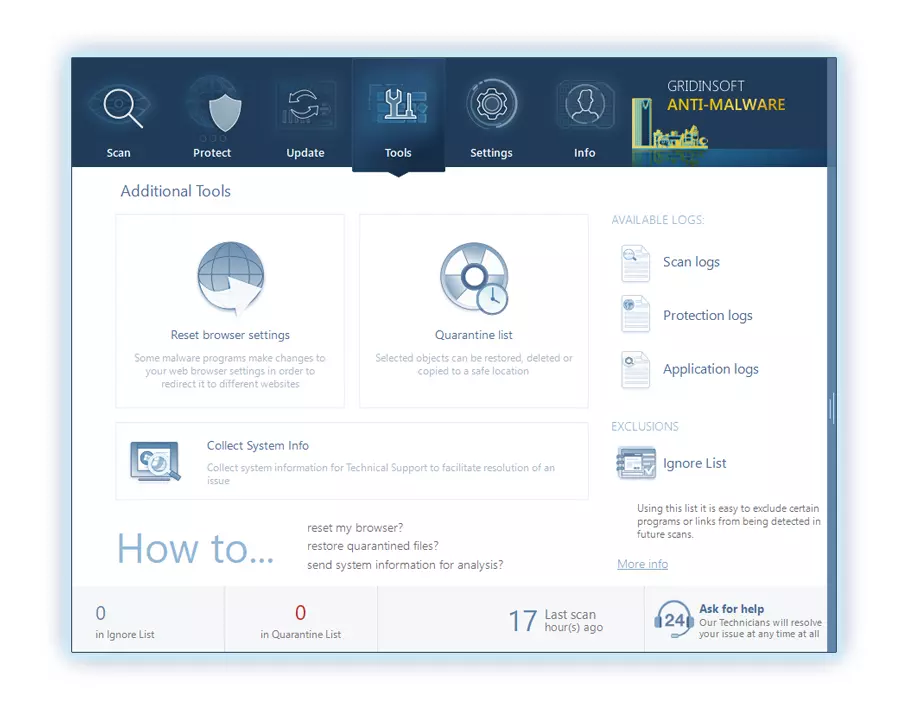
To revert your browser settings, you need to use the Reset Browser Settings option. This action is not able to be counteracted by any virus, hence, you will surely see the result. This option can be located in the Tools tab.
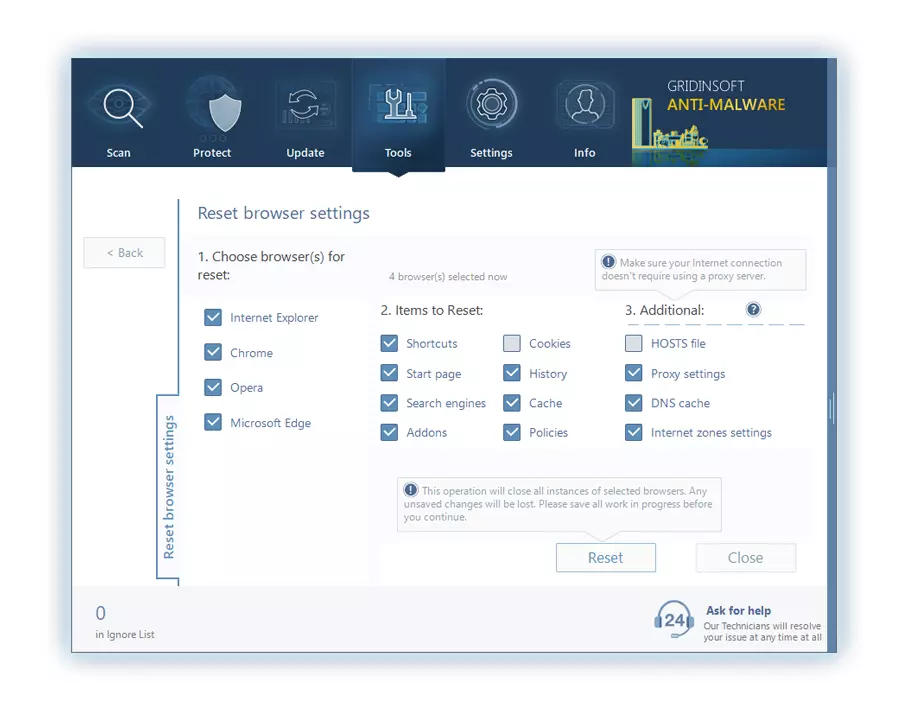
After pressing the Reset Browser Settings option, the menu will be displayed, where you can choose, which settings will be reverted to the original.
Deleteing Fake Forcepoint hijacker manually
Besides using anti-malware software for browser restoration, you may choose the “Reset browser settings” function, which is usually embedded in all popular browsers.
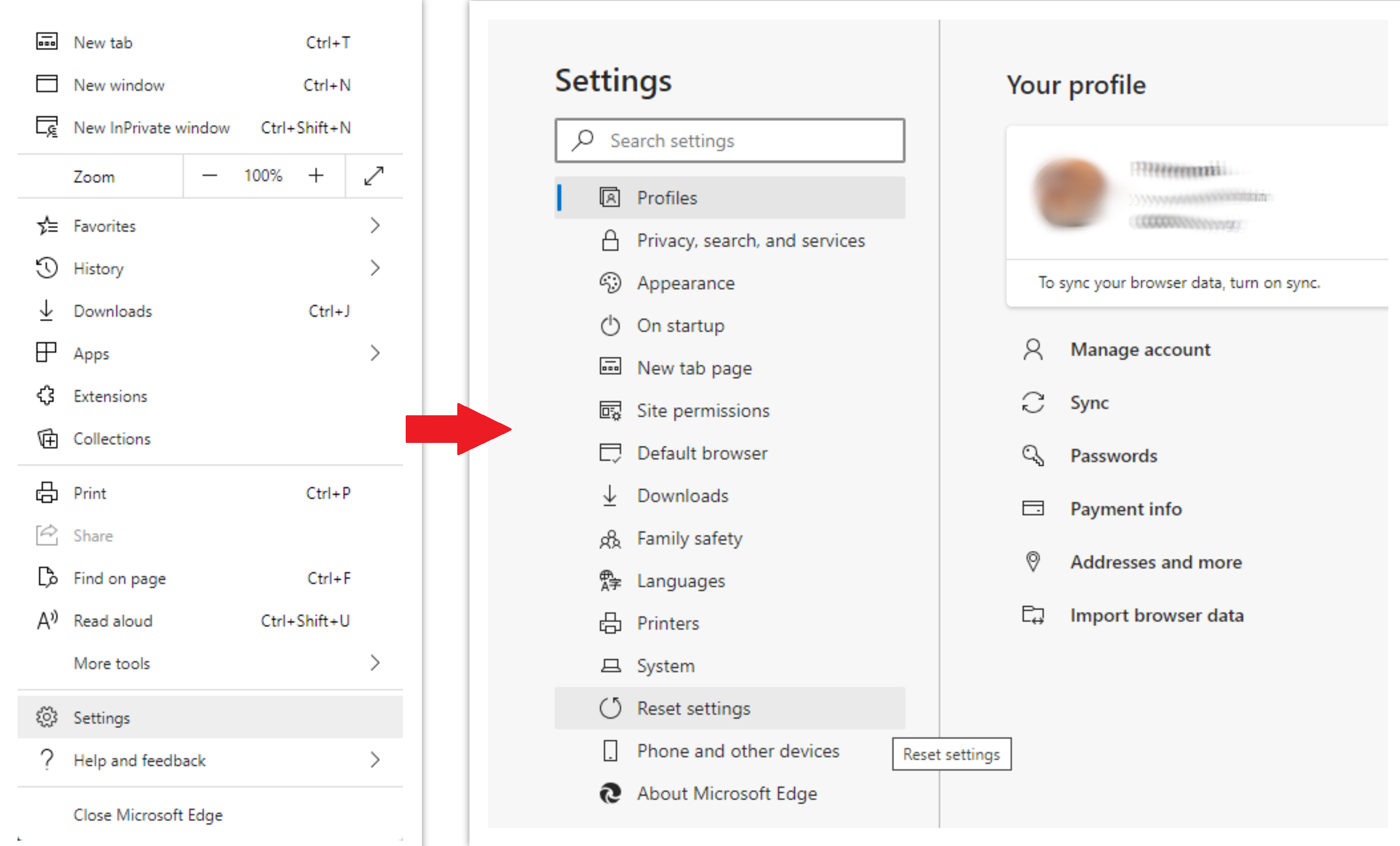
To reset Edge, do the following steps :
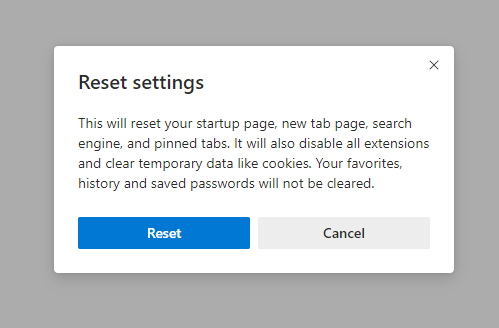
- Open “Settings and more” tab in upper right corner, then find here “Settings” button. In the appeared menu, choose “Reset settings” option :
- After picking the Reset Settings option, you will see the following menu, stating about the settings which will be reverted to original :
For Mozilla Firefox, do the next actions :
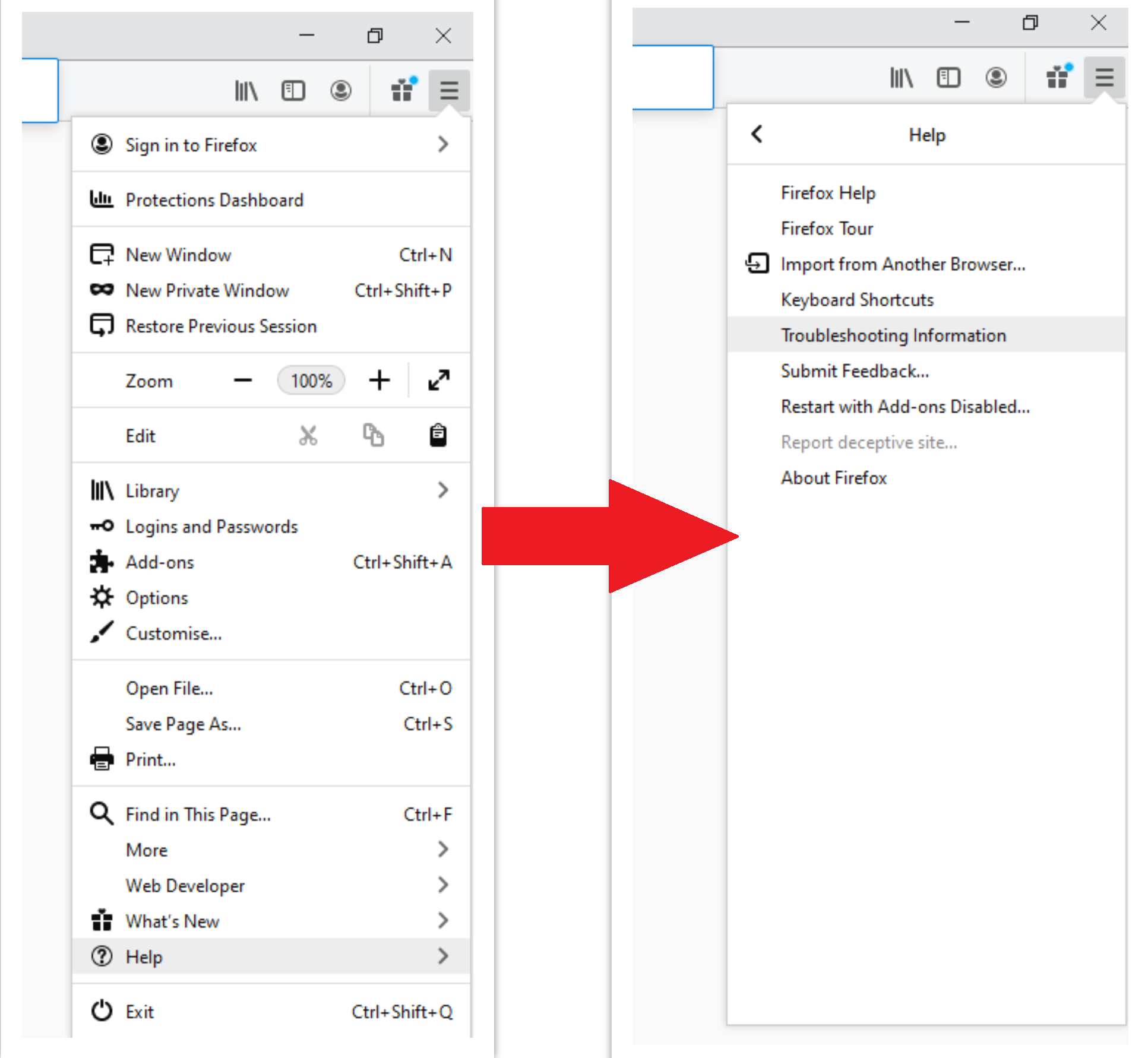
- Open Menu tab (three strips in upper right corner) and click the “Help” button. In the appeared menu choose “troubleshooting information” :
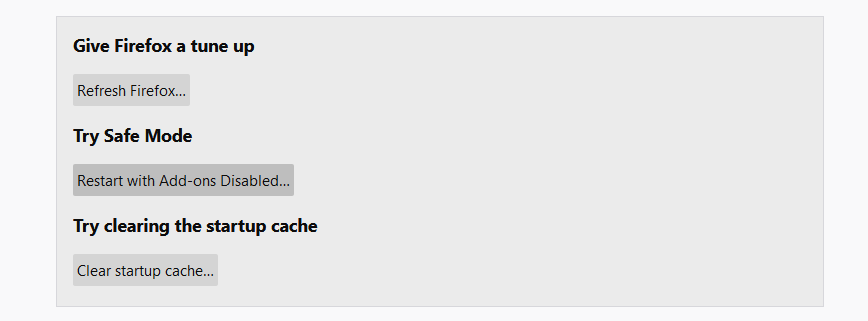
- In the next screen, find the “Refresh Firefox” option :
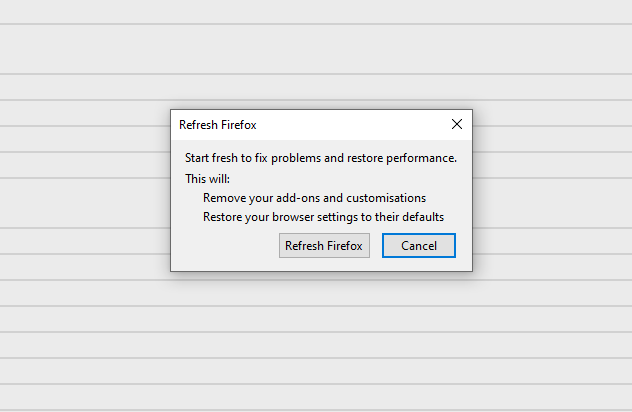
After choosing this option, you will see the next message :
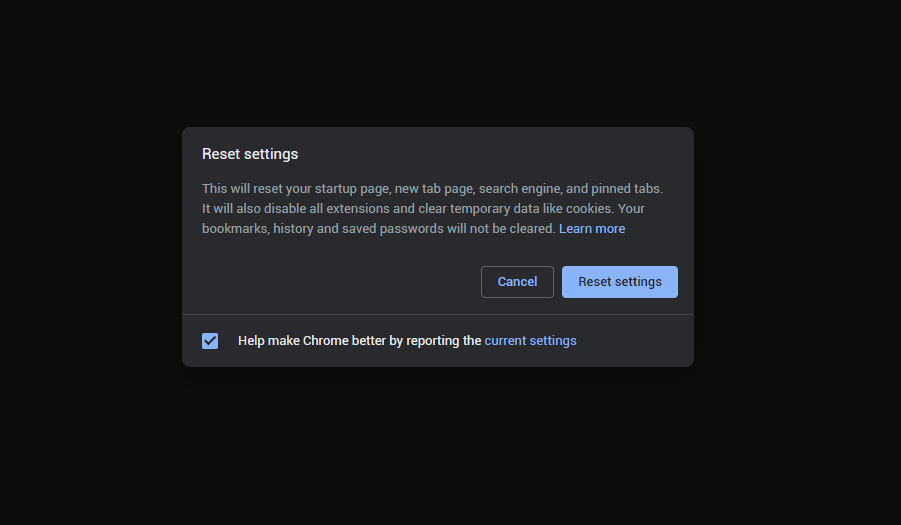
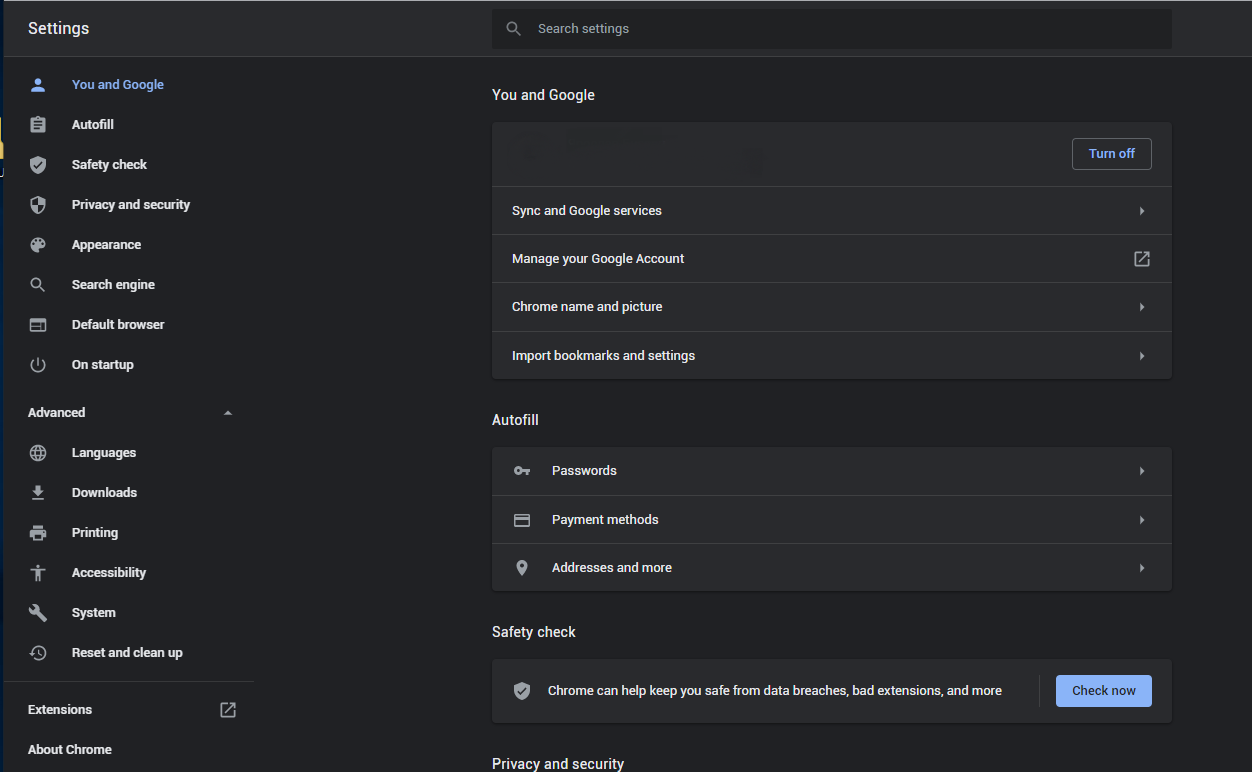
If you use Google Chrome
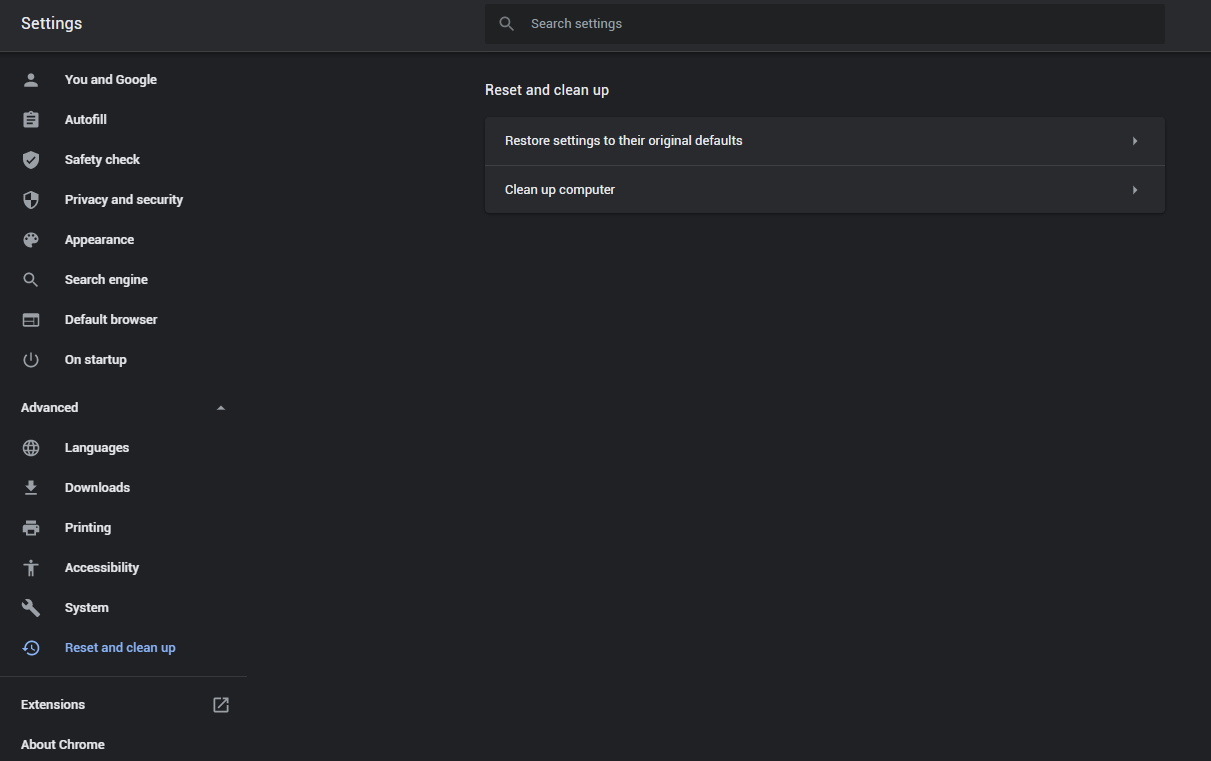
- Open Settings tab, find the “Advanced” button. In the extended tab choose the “Reset and clean up” button :
- In the appeared list, click on the “Restore settings to their original defaults” :
- Finally, you will see the window, where you can see all the settings which will be reset to default :
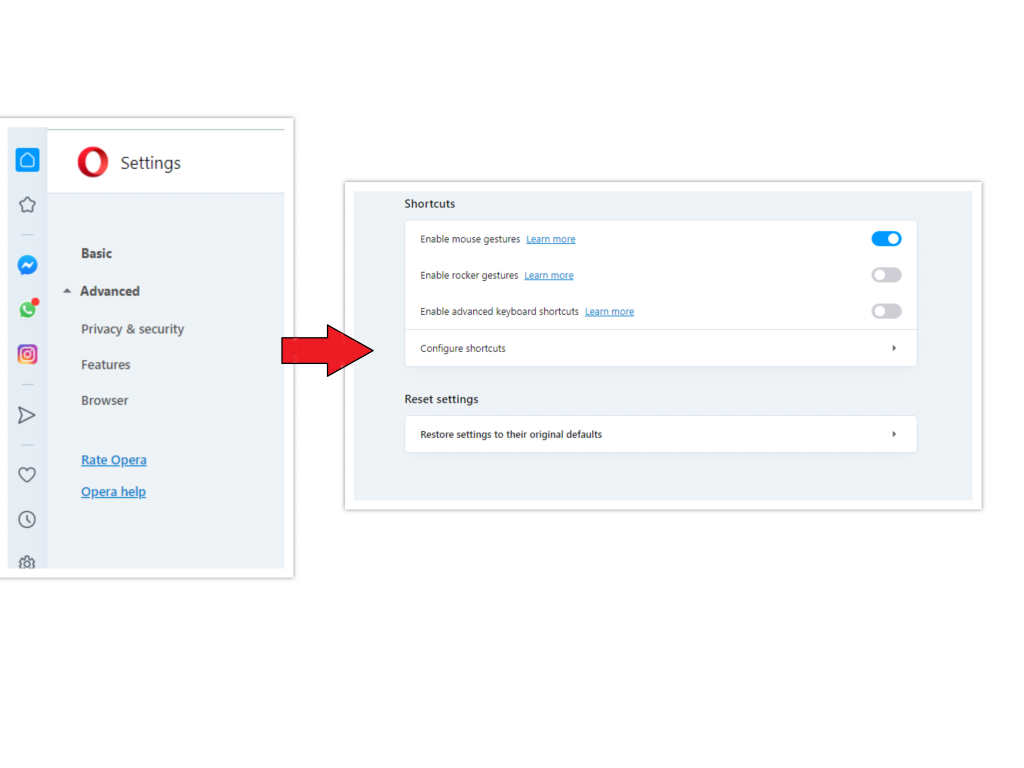
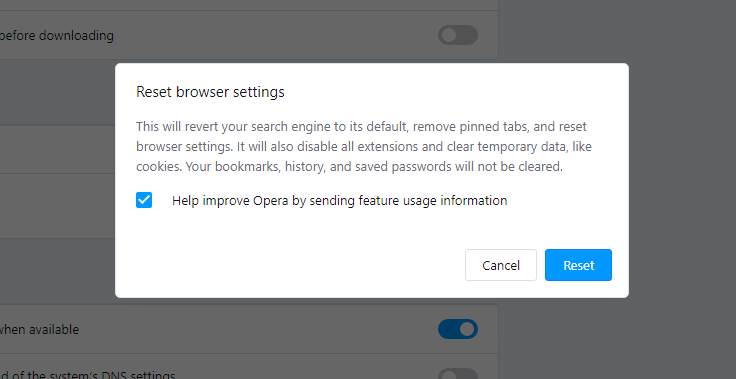
Opera can be reset in the next way
- Open Settings menu by pressing the gear icon in the toolbar (left side of the browser window), then click “Advanced” option, and choose “Browser” button in the drop-down list. Scroll down, to the bottom of the settings menu. Find there “Restore settings to their original defaults” option :
- After clicking the “Restore settings…” button, you will see the window, where all settings, which will be reset, are shown :
As an afterword, I want to say that time plays against you and your PC. The activity of browser hijacker must be stopped as soon as possible, because of the possibility of other malware injection. This malware can be downloaded autonomously, or offered for you to download in one of the windows with advertisements, which are shown to you by the hijacker. You need to act as fast as you can.
I need your help to share this guide.
Browser hijackers are among the largest and also disruptive kinds of malware. I published this article to help you, so I wish you will help me to make the computer world completely clean of malware. Please, share this article in the social networks you use – Twitter, Reddit, Facebook – wherever.
.
Emma DavisUser Review
( votes)References
- SANS Institute – Courses, Certifications & Research https://www.sans.org
- Chrome Web Store
- Detailed review of Microsoft Defender