Prevailion company warned that Russian hacker Evil Corp (aka TA505) is actively using legitimate tools (in addition to malware) to attack German companies.
Let me remind you that this grouping is primarily known for using the Dridex Trojan and Locky ransomware, though it also uses many other malicious programs, including BackNet, Cobalt Strike, ServHelper, Bart, FlawedAmmyy, SDBbot RAT and DoppelPaymer (whose operators refuse to attack medical institutions during current pandemic).Prevailion researchers have found that since summer 2019, the TA505 has been campaigning for German firms.
Hackers send out letters to their targets with fake resumes for hiring. These letters contain a malicious attachment designed to steal credentials and credit card information”, – say the researchers.
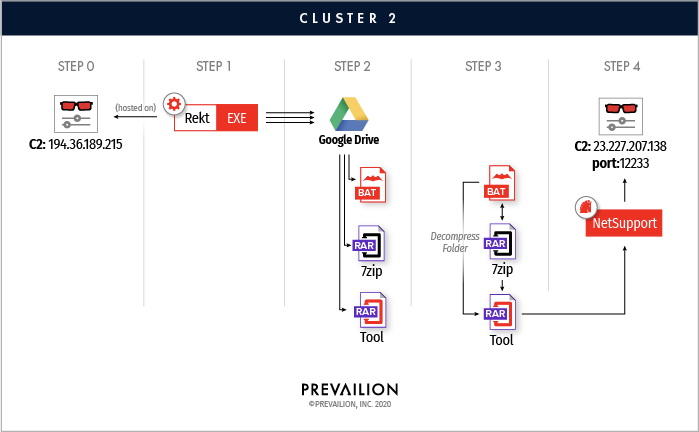
However, if in 2019, attackers used available on the market ransomware to encrypt victims’ files, in more recent operations they switched to the commercial tool for remote administration of NetSupport, hosted on Google Drive.
By using legitimate tools that are unlikely to be detected by traditional security solutions, attackers can perform a wide range of actions, including stealing files, taking screenshots, and recording sound”, – warn Prevailion experts.
So, at the initial stage of the attack, the code from the malicious resume launches a script to extract additional payloads and collect data about the victim’s computer (list of installed programs, name of computer, domain, and so on). Then the malware tries to collect stored credentials from browsers and email clients, cookies and credit card information.
The stolen credentials are archived and sent to the control server of the attackers, where then created a scheduled task, while the BAT file removes all traces of the attack.
Researchers note that in the summer 2019, attacks also had a ransomware component: disks on local machines were encrypted using the GPG public key, shadow copies were deleted, and some data was redirected to zalock[@]airmail.cc.
For new attacks is used the loader (apparently rekt), which was developed to communicate with Google Drive and download additional files. The payload of the second stage of the attack was identified as a commercial NetSupport application for remote work.
Some of the rekt options discovered date back to April 2019. Researchers also identified samples signed with a digital signature, which was also used to sign two FlawwedAmmy Trojans. They were also previously associated with TA505, so researchers confidently state that this hacking group stands behind the detected attacks.