In this article you will discover the definition of Trojan Emotet and also its negative effect on your computer system. Such ransomware is a form of malware that is elaborated by internet scams to demand paying ransom from a target.
What is Trojan Emotet?
Emotet is an incredibly innovative and also harmful banking Trojan made use of to download and install and also set up other malware. Initially taped in 2014, Emotet has gained advanced abilities over the course of its lifetime. Today Emotet is targeting governments, companies, small businesses as well as individuals, concentrating on Europe, America, as well as Canada.
What makes Emotet virus so hazardous? Emotet can act like a worm as well as spread utilizing neighborhood networks, which makes it exceptionally tough to clean up. The Trojan has advanced persistence and also anti-evasion technicians, such as the ability to discover sandboxes and digital machines with a choice to produce false indicators to toss investigations off. The Trojan has a polymorphic design– indicating that it can transform its code to bypass signature-based discovery, making this cyber defense technique ineffective versus its’ assaults. If that wasn’t enough, Emotet can obtain updates from the control web server, performing this operation as if an operating system update is being installed. This allows the Trojan to drop additional malware onto the contaminated device stealthily. It should also be noted that Emotet Trojan has a modular design that makes it feasible to adapt this malware to different tasks and also personalize it for every certain campaign, providing the opponents the maximum flexibility.
The first variation of Emotet malware which was identified in the wild completely back in 2014 was developed to swipe financial qualifications by intercepting net traffic and was a lot more basic than the beast of a Trojan which we know today. When Emotet was first detected in the wild, the malware targeted mainly financial institutions from Germany as well as Austria utilizing just its native information-taking toolset.
Version 2 adhered to quickly after, this moment bring several additional components such as a cash transfer, mail spam, DDoS and address book taking components. The third model of Emotet was released in 2015, this time around focusing on updating the anti-evasion capability of the malware as well as introducing financial institutions from Switzerland right into the listing of potential victims.
The next overhaul of the Emotet malware followed in December 2016, transforming the attack vector of the infection. At the beginning of its lifetime Version 4 greatly depended on the RIG 4.0 manipulate kit to make its method into the targets’ computer systems later on switching mainly to mail spam. The same version of the malware additionally noted the moment when the main use instance of the malware started changing from using its very own financial module to dropping other Trojans onto contaminated devices.
Speaking of components, Emotet malware can execute a great deal of destructive tasks that differ depending upon the components made use of in a certain campaign. Many variations of the infection consisted of a spam module which can be utilized to continue the spread of the malware by sending out a series of malicious emails from the infected device. Another normally included module is the one utilized for credential stealing, enabling Emotet to swipe delicate details from web browsers and mail clients.
Beginning with 2017, Emotet trojan began coming geared up with a spreader module, enabling the malware to contaminate all machines linked by means of a neighborhood network. The virus additionally obtained the personal digital assistant thief module– this set is interesting. It analyzes the relationship between e-mail senders and also receivers as well as uses the collected details to improve the performance of succeeding projects stemming from the individuals’ PC, enabling to target close friends, relative and also coworkers of the sufferer with individualized spam emails.
Not just does Emotet malware provide flexible capability through making use of modules as well as has a number of anti-evasion features, however it also places a heavy emphasis on perseverance. To ensure that the malware stays in the contaminated device, it infuses right into running processes, commonly targeting the Explorer.exe. The malware uses Scheduled Tasks and makes computer system registry keys adjustments.
It needs to be noted that the banking Trojan we are examining today is very devastating and its assaults can have numerous consequences, such as loss of personal information, failure to run the infected PC up to its total impairment and also financial losses associated with restoring the framework harmed by the malware. In fact, one business was compelled to spend an unwanted of one million bucks to manage the aftermath of an Emotet strike.
Trojan Emotet Overview
These adjustments can be as complies with:
- Executable code extraction. Cybercriminals often use binary packers to hinder the malicious code from reverse-engineered by malware analysts. A packer is a tool that compresses, encrypts, and modifies a malicious file’s format. Sometimes packers can be used for legitimate ends, for example, to protect a program against cracking or copying.
- Creates RWX memory. There is a security trick with memory regions that allows an attacker to fill a buffer with a shellcode and then execute it. Filling a buffer with shellcode isn’t a big deal, it’s just data. The problem arises when the attacker is able to control the instruction pointer (EIP), usually by corrupting a function’s stack frame using a stack-based buffer overflow, and then changing the flow of execution by assigning this pointer to the address of the shellcode.
- Possible date expiration check, exits too soon after checking local time;
- Mimics the system’s user agent string for its own requests;
- Repeatedly searches for a not-found process, may want to run with startbrowser=1 option;
- Drops a binary and executes it. Trojan-Downloader installs itself to the system and waits until an Internet connection becomes available to connect to a remote server or website in order to download additional malware onto the infected computer.
- HTTP traffic contains suspicious features which may be indicative of malware related traffic;
- Performs some HTTP requests;
- Deletes its original binary from disk;
- Attempts to remove evidence of file being downloaded from the Internet;
- Attempts to repeatedly call a single API many times in order to delay analysis time. This significantly complicates the work of the virus analyzer. Typical malware tactics!
- Installs itself for autorun at Windows startup.
There is simple tactic using the Windows startup folder located at:
C:\Users\[user-name]\AppData\Roaming\Microsoft\Windows\StartMenu\Programs\Startup Shortcut links (.lnk extension) placed in this folder will cause Windows to launch the application each time [user-name] logs into Windows.The registry run keys perform the same action, and can be located in different locations:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- Creates a copy of itself;
- Anomalous binary characteristics. This is a way of hiding virus’ code from antiviruses and virus’ analysts.
- Ciphering the documents situated on the victim’s hard drive — so the sufferer can no longer utilize the information;
- Preventing regular accessibility to the target’s workstation;
Trojan Emotet Virus
The most typical channels through which Trojan Emotet are injected are:
- By means of phishing emails;
- As a repercussion of customer winding up on a source that organizes a harmful software program;
As quickly as the Trojan is successfully injected, it will certainly either cipher the data on the target’s computer or prevent the gadget from operating in an appropriate manner – while also placing a ransom money note that points out the requirement for the targets to effect the payment for the function of decrypting the files or recovering the documents system back to the first condition. In a lot of instances, the ransom note will certainly come up when the customer reboots the COMPUTER after the system has actually currently been harmed.
Emotet Distribution
In numerous corners of the globe, Trojan Emotet grows by jumps and also bounds. Nevertheless, the ransom money notes and also tricks of obtaining the ransom money quantity might vary depending upon specific regional (regional) setups. The ransom notes and methods of extorting the ransom amount might differ depending on specific neighborhood (regional) settings.
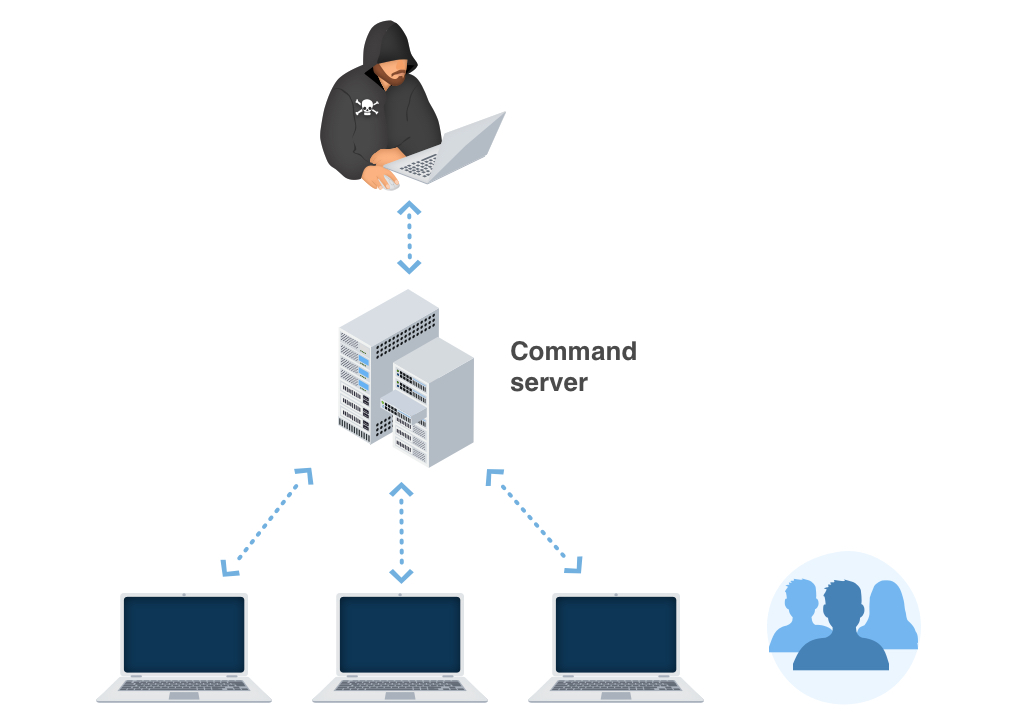
As an example:
Faulty alerts about unlicensed software program.
In specific locations, the Trojans usually wrongfully report having actually spotted some unlicensed applications allowed on the victim’s gadget. The sharp after that demands the customer to pay the ransom money.
Faulty declarations concerning illegal content.
In nations where software program piracy is much less popular, this technique is not as reliable for the cyber frauds. Additionally, the Trojan Emotet alert may incorrectly assert to be stemming from a law enforcement institution and will report having situated kid pornography or various other unlawful information on the tool.
Trojan Emotet alert might falsely assert to be deriving from a law enforcement establishment and will certainly report having situated child pornography or other prohibited data on the tool. The alert will in a similar way consist of a requirement for the customer to pay the ransom money.
Technical details
File Info:
crc32: E6330B5Emd5: 0f8a02352ff090cc2b5bde275e5dc11cname: 5ggtJ.exesha1: d28f3070c62a56d2bf87ddc7db390270a9ca179dsha256: 249cd6583dd09590841061d9b5cf8ef80924ac2c9d9fdf63065eb17d93e897c8sha512: 240f31782a1cd79bf3b13aa5218db394cbe81af8f94941f9d17c3f8cdc3c0311f18799afaa02842215c6974ef2aff884dc2322963e92cd216d20eb47c44b65e0ssdeep: 6144:uK1TL+6Rexa9WSU/BV5qVqc03x60Dhm+kEuS6QoJx5XpJqn3BTZe87tbiSj:umZ9WSlk13xRDhoS8x5gBU8JiSjtype: PE32 executable (GUI) Intel 80386, for MS WindowsVersion Info:
LegalCopyright: Copyright (C) 2001InternalName: WBPFileVersion: 1, 0, 0, 1ProductName: WBP ApplicationProductVersion: 1, 0, 0, 1FileDescription: WBP MFC ApplicationOriginalFilename: WBP.EXETranslation: 0x0409 0x04b0
Trojan Emotet also known as:
| MicroWorld-eScan | Trojan.GenericKD.42248165 |
| FireEye | Generic.mg.0f8a02352ff090cc |
| McAfee | Emotet-FPC!0F8A02352FF0 |
| Cylance | Unsafe |
| BitDefender | Trojan.GenericKD.42248165 |
| K7GW | Riskware ( 0040eff71 ) |
| Cybereason | malicious.0c62a5 |
| BitDefenderTheta | Gen:NN.ZexaF.34082.zq1@aKqZFqfi |
| Cyren | W32/Kryptik.AYJ.gen!Eldorado |
| Symantec | Trojan Horse |
| APEX | Malicious |
| Avast | Win32:Malware-gen |
| GData | Trojan.GenericKD.42248165 |
| Kaspersky | UDS:DangerousObject.Multi.Generic |
| Alibaba | Trojan:Win32/starter.ali1000037 |
| AegisLab | Trojan.Win32.Generic.4!c |
| Rising | Trojan.Detplock!8.4A0D (CLOUD) |
| Endgame | malicious (high confidence) |
| Sophos | Mal/Generic-S |
| DrWeb | Trojan.DownLoader32.47698 |
| McAfee-GW-Edition | BehavesLike.Win32.Ransomware.gh |
| Trapmine | suspicious.low.ml.score |
| Emsisoft | Trojan.Emotet (A) |
| Ikarus | Win32.Outbreak |
| F-Prot | W32/Kryptik.AYJ.gen!Eldorado |
| Webroot | W32.Trojan.Emotet |
| MAX | malware (ai score=82) |
| Microsoft | Trojan:Win32/Emotet!rfn |
| Arcabit | Trojan.Generic.D284A7E5 |
| ZoneAlarm | UDS:DangerousObject.Multi.Generic |
| AhnLab-V3 | Trojan/Win32.Emotet.C3889684 |
| Acronis | suspicious |
| Ad-Aware | Trojan.GenericKD.42248165 |
| Malwarebytes | Trojan.Emotet |
| ESET-NOD32 | a variant of Win32/GenKryptik.EBYL |
| SentinelOne | DFI – Suspicious PE |
| Fortinet | W32/TrickBot.CJ!tr |
| AVG | Win32:Malware-gen |
| Paloalto | generic.ml |
| CrowdStrike | win/malicious_confidence_90% (W) |
Trojan Emotet Removal Tool
Trojan Viruses has ofter come with other ransomware and spyware. This threats can steal account credentials, or crypt your documents for ransom.
Reasons why I would recommend GridinSoft1
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes.2.
Download GridinSoft Anti-Malware.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the install-antimalware-fix.exe file to install GridinSoft Anti-Malware on your system.
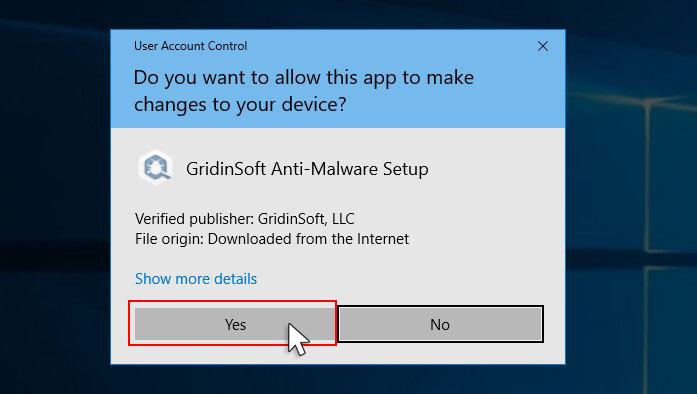
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Emotet files and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
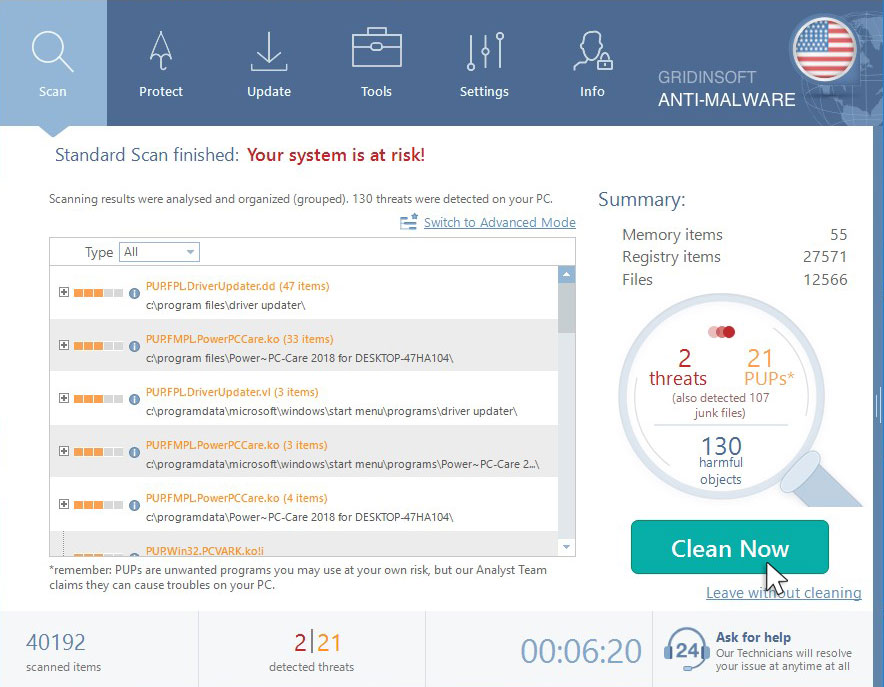
Click on “Clean Now”.
When the scan has finished, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
Are Your Protected?
GridinSoft Anti-Malware will scan and clean your PC for free in the trial period. The free version offer real-time protection for first 2 days. If you want to be fully protected at all times – I can recommended you to purchase a full version:
If the guide doesn’t help you to remove Trojan Emotet you can always ask me in the comments for getting help.
User Review
( votes)References
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison