Scientists from the Amsterdam Free University and the Swiss Higher Technical School of Zurich have discovered a new vulnerability. The bug was called CrossTalk, it threatens Intel processors and allows malicious code, which is running in one processor core, to leak data from other software running on a different core (including Intel SGX enclaves).
Researchers explain that CrossTalk is another variation of the MDS bug. Let me remind you that the problems of Microarchitectural Data Sampling (MDS) were discovered in Intel processors in the spring of 2019.Then the experts at once identified four new vulnerabilities and divided them into three groups: RIDL, Fallout and ZombieLoad (CVE-2018-12130, CVE-2018-12126, CVE-2018-12127 and CVE-2018-11091).
As well as the sensational vulnerabilities of Specter and Meltdown, the new bugs were associated with a proactive (or speculative) mechanism for executing commands“, – say the researchers.
They allowed an attacker to read data from places that he did not have access to (OS kernel, processes, Software Guard eXtensions enclaves), and then steal passwords, cryptographic keys and other data.
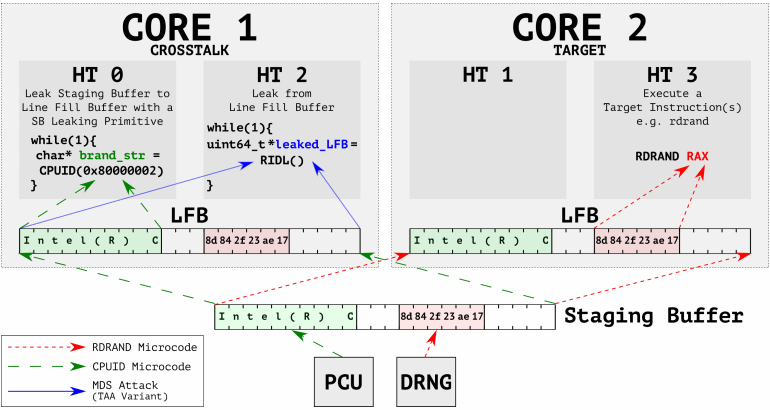
CrossTalk attacks data while Line Fill Buffer (LBF), one of the CPU’s cache systems, processes it. According to experts, the problem is that the LBF cache, in fact, works with the previously undocumented “intermediate buffer” (staging buffer), which is used by all processor cores.
Using CrossTalk, we found that various instructions execute offcore requests to read data from an intermediate buffer shared by all CPU cores. We noticed that this intermediate buffer contains confidential information, including the output of the Digital Random Number Generator (DRNG), a hardware random number generator, and that such data can be transmitted between the cores using RIDL attacks (aka MDS)”, — write the experts.
The video below demonstrates how CrossTalk is used to attack an intermediate buffer through the LBF cache, and then this leads to data leakage from other cores (the video presented an Intel SGX key leakage).
It is worth noting that the researchers not only created their own website for the CrossTalk problem, but also prepared a detailed technical report on the vulnerability and published a PoC exploit on GitHub.
The research team writes that it worked with Intel to fix the CrossTalk problem for more than 20 months (since September 2018).
Due to the complexity of the problem, fixing the vulnerability took far more than the standard 90 days, in addition, initially the possibility of an “internuclear” leak was not considered at all”, – said the experts.
Intel engineers, in turn, published their own report, which says that they have already made significant changes to their CPUs, and for most fresh products, CrossTalk is not a threat.
For older processors, updated CrossTalk firmware was released for them this week: Special Register Buffer Data Sampling update (SRBDS, CVE-2020-0543, Intel-SA-00320).
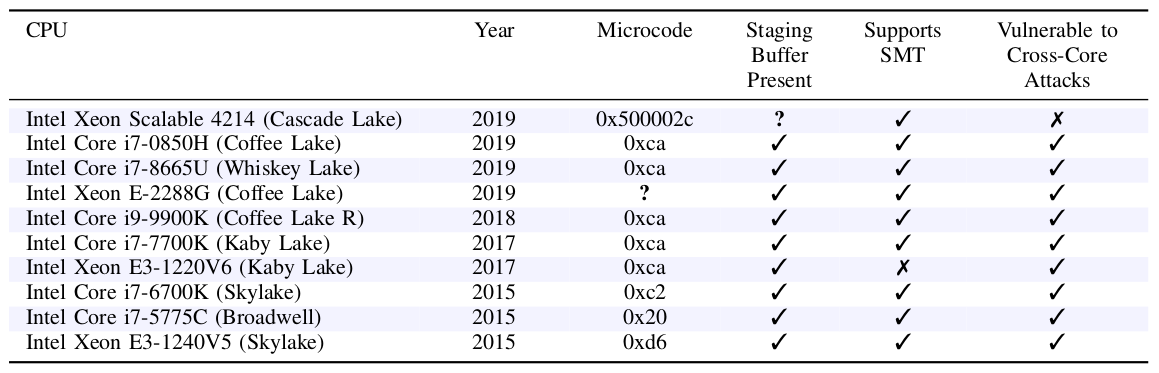
A complete list of over fifty vulnerable processors (mobile, desktop and server) can be found here. In particular, the attack is dangerous for Core processors from 3 to 10 generations, Core X-Series, Pentium, Celeron and Xeon E3.
At the same time, Intel representatives emphasize that today it is hardly possible to talk about any real attacks using CrossTalk outside a controlled test environment.
Recall that we also talked about the fact that some Intel processors are vulnerable to the new version of the Zombieload problem