Coolzebra.net pop-up notices may appear unexpectedly, covering the content of the site you explored or opening your web browser when you don’t want it to be opened.
Clicking the Coolzebra.net ad can lead to the injection of other malware or unwanted programs. In this guide, you will see the guide of Coolzebra.net popups removal in various methods, and also examining your personal computer for other malware existence.
What are Coolzebra.net pop-ups?
Coolzebra.net popups are an effect of adware presence. Adware is a type of malware that shows you the pay-per-view of pay-per-click promotions, which generates a substantial volume of income for adware suppliers. These promotions may consist of sometimes shocking composition, or have a web link to malicious content/website, since adware maintainers have no purpose to examine the goodness of the web content they are going to reveal – their single target is money.
Pop-up promotions itself is a very good, low-priced and also extremely successful advertising tool1. It makes it possible for the seller to attach the customers’ attention to their website, and the buyers to get the dynamic updates on the goods they want to buy. When the consumer will receive a pop-up alert that the TV set he desires to buy is provided at the online shop he/she checked out previously with a 15% discount, one will undoubtedly use this opportunity and purchase it. Considering the extremely low cost for the popups and their targeting, such an advertising method is a favourite thing among the advertising departments of huge internet retailers.
However, such a rewarding system could not be missed by virus creators. Option to show the popup ads forcibly to the people of malware attack is an excellent basis for evil-minded tricks with the popup advertisements. And Coolzebra.net ads is just one of hundreds that are “employed” in this system.
Here is a summary for the Coolzebra.net
| Site | Coolzebra.net |
| Hosting | AS202053 UpCloud Ltd Germany, Frankfurt am Main |
| Infection Type | Adware, Push notifications, Unwanted Ads, Pop-up Ads |
| IP Address | 94.237.93.242 |
| Symptoms | Annoying pop-up ads in the right corner. |
| Similar behavior | Mediaforyour, News, Rplnd32 |
| Fix Tool | To remove possible virus infections, try to scan your PC |
How have I got the Coolzebra.net virus?
There are a huge amount of ways of becoming infected by the adware that result in the Coolzebra.net popups tornado. A lion’s part of this virus instances is after the freeware or cracked programs, that are spread on the peering networks. Free software may additionally be downloaded from the official website, and the adware is offered as a legal bundled program.
There is no need to blame yourself. A plenty of individuals regularly work with the uncertain programs from untrusted sources: abandonware, different utilities that are free of cost, or even hacked programs. Every one of these kinds of applications are unsafe, because it is quite easy to build in a Coolzebra.net malware under the cover of part of the license hacking script, or as a part of the self-made algoritm inside of the Windows optimization tool.
Coolzebra.net popup virus may likewise be concealed in the advertisement somewhere on the odd site. Such websites are in most cases full of intense and blinking advertisements, and their proprietors often permit any promotions to be placed on their page. Thus, clicking on such banners is a shot in the dark: only the ad contractor knows what will occur when you press this advertisement. Besides some “light” viruses, like adware or undesirable programs, you may also receive something a lot more hazardous, like ransomware or coin miner; the big share of coin miners circulation is exactly after the malicious ads.
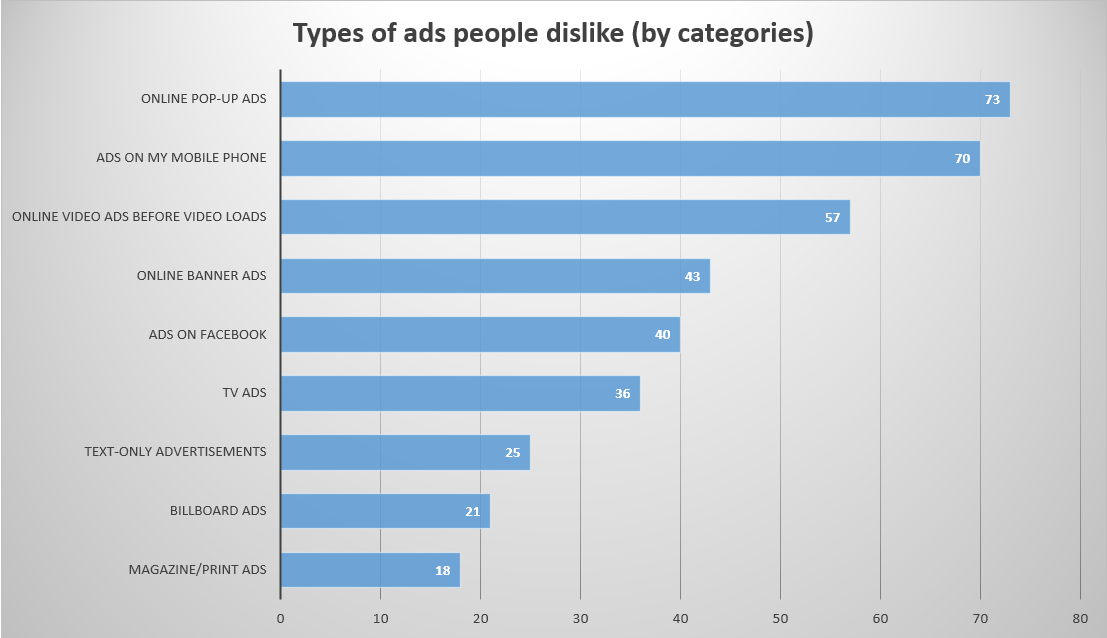
The statistic shows that people dislike popup advertising more than other types of promotions
Potentially unwanted applications, like Coolzebra.net pop-up virus can provoke a lot of problems on your PC. Distracting is not the single problem – pop-up notifications may display you the promotions, where you are offered to get one more strange application, or “a perfect anti-malware tool”. Scareware is usually spread with the last slogun. Potentially undesirable applications, in turn, can have spyware functions. And it is pretty hard to distinguish the unwanted app from a legit one, if you don’t know the exact names. Besides the PUPs and fake antiviruses, popup-related banners are also chosen as a spreading way by various trojan viruses, for example – coin miners. The consequences of activity of such malware is 100% unwanted, and can cost you hundreds or even thousands of dollars. And even if you are not interacting with these advertisements, they can be clicked by someone who also uses your personal computer – parents, children, spouse, etc. So the things may become much more serious, and it will be much harder to solve it without data loss. It is recommended to get rid of the viruses with antivirus applications as soon as possible.
How can I get rid of Coolzebra.net pop-up advertisements?
The manual of Coolzebra.net adware elimination consists of 2 sections. Initially, we need to remove the malware, and then deal with the results of its action. The removal process is pretty easy, due to the fact that it can be performed even with the use of Microsoft Defender – security software that is available on all personal computers with Windows 8/10. However, because of its substantial resources usage, along with some problems that can be pivotal for some types of individuals, Defender is often disabled by the users, so its usage is most likely impossible. What’s more, a wide range of trojan viruses have the ability to switch off the embedded antivirus. It is better to make use of the separated program that will not have such weakness.
I would certainly recommend you to utilize Gridinsoft Anti-Malware2 – a well-proven security tool that will undoubtedly remove the viruses from your PC and make an invulnerable shield with a Proactive protection feature. But let’s manage Coolzebra.net adware initially.
Removing Coolzebra.net popup virus with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of Coolzebra.net malware the default option is “Delete”. Press “Apply” to finish the malware removal.



Now, when the computer is clean of viruses, we can proceed to the browser reset. You can do this step manually, as well as with the use of GridinSoft Anti-Malware.
Reset browser settings to default
Manual method of browser reset
To reset Edge, do the following steps :
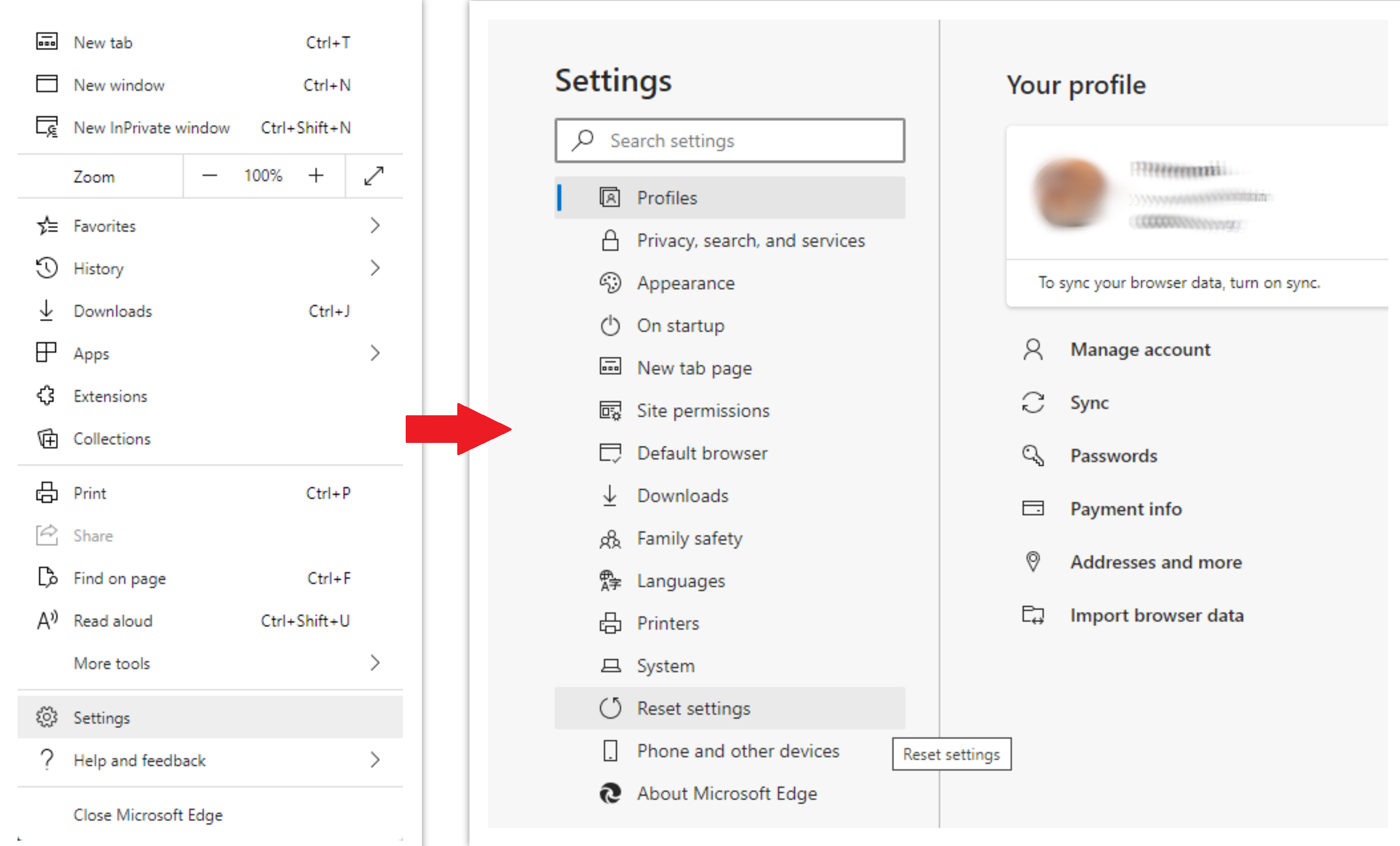
- Open “Settings and more” tab in upper right corner, then find here “Settings” button. In the appeared menu, choose “Reset settings” option :
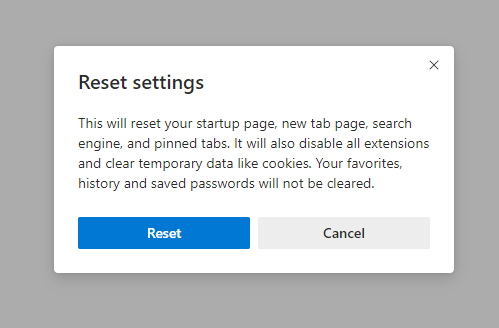
- After picking the Reset Settings option, you will see the following menu, stating about the settings which will be reverted to original :
For Mozilla Firefox, do the next actions :
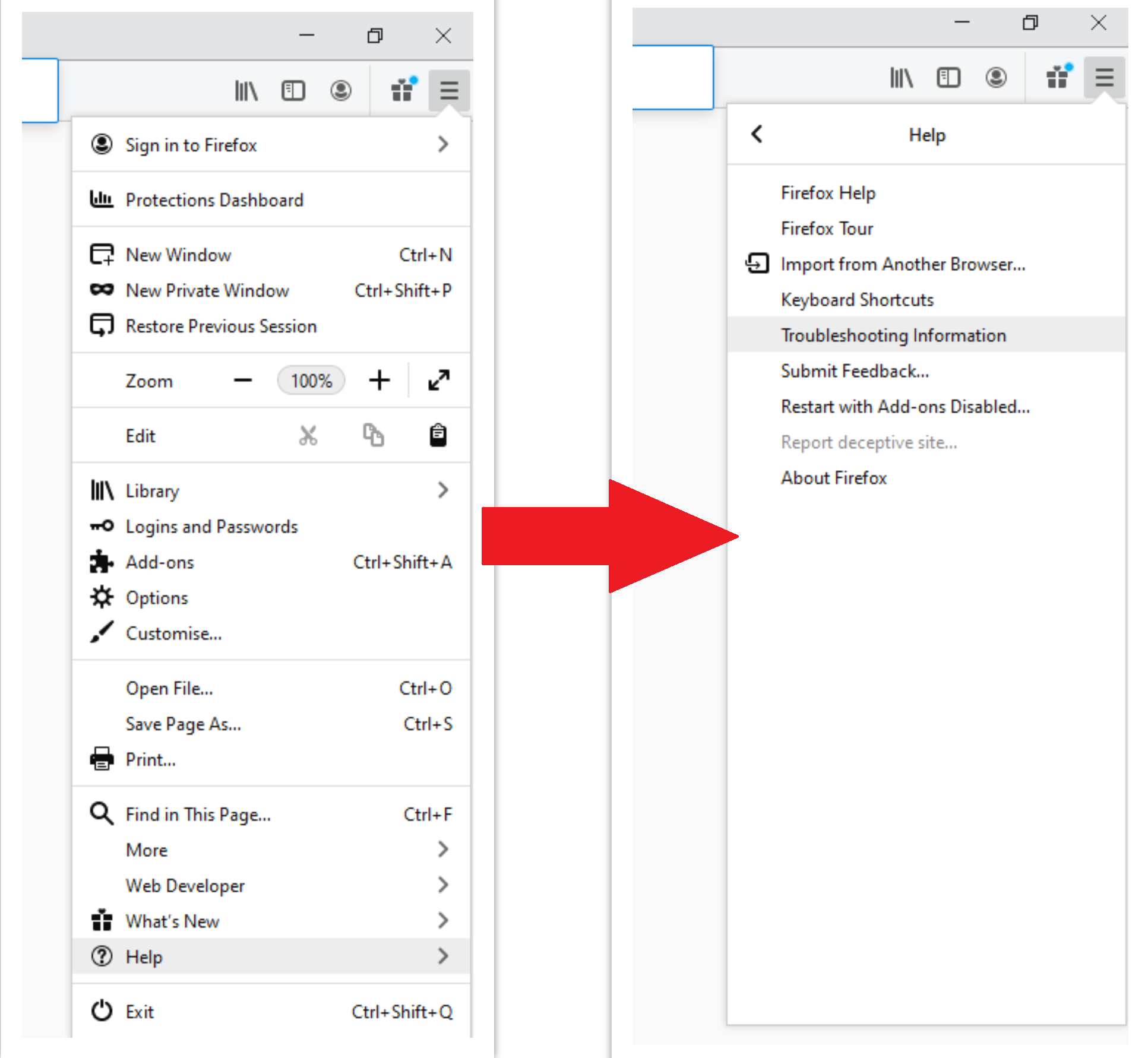
- Open Menu tab (three strips in upper right corner) and click the “Help” button. In the appeared menu choose “troubleshooting information” :
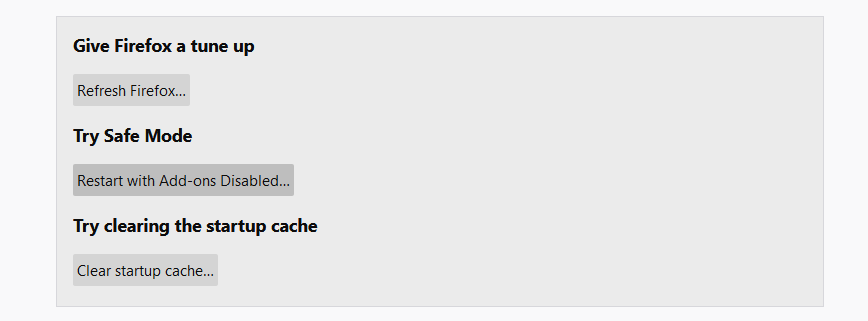
- In the next screen, find the “Refresh Firefox” option :
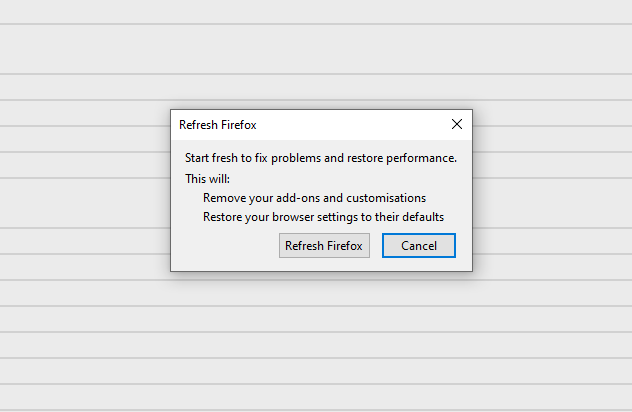
After choosing this option, you will see the next message :
If you use Google Chrome
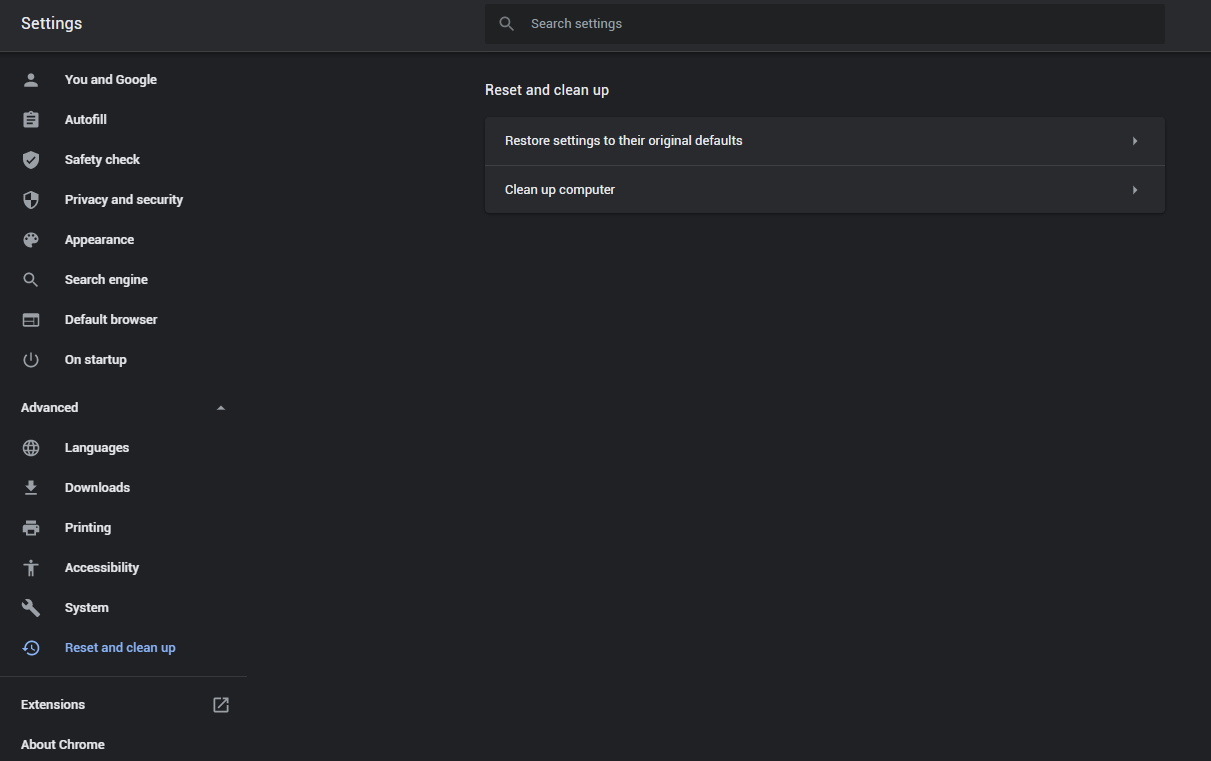
- Open Settings tab, find the “Advanced” button. In the extended tab choose the “Reset and clean up” button :
- In the appeared list, click on the “Restore settings to their original defaults” :
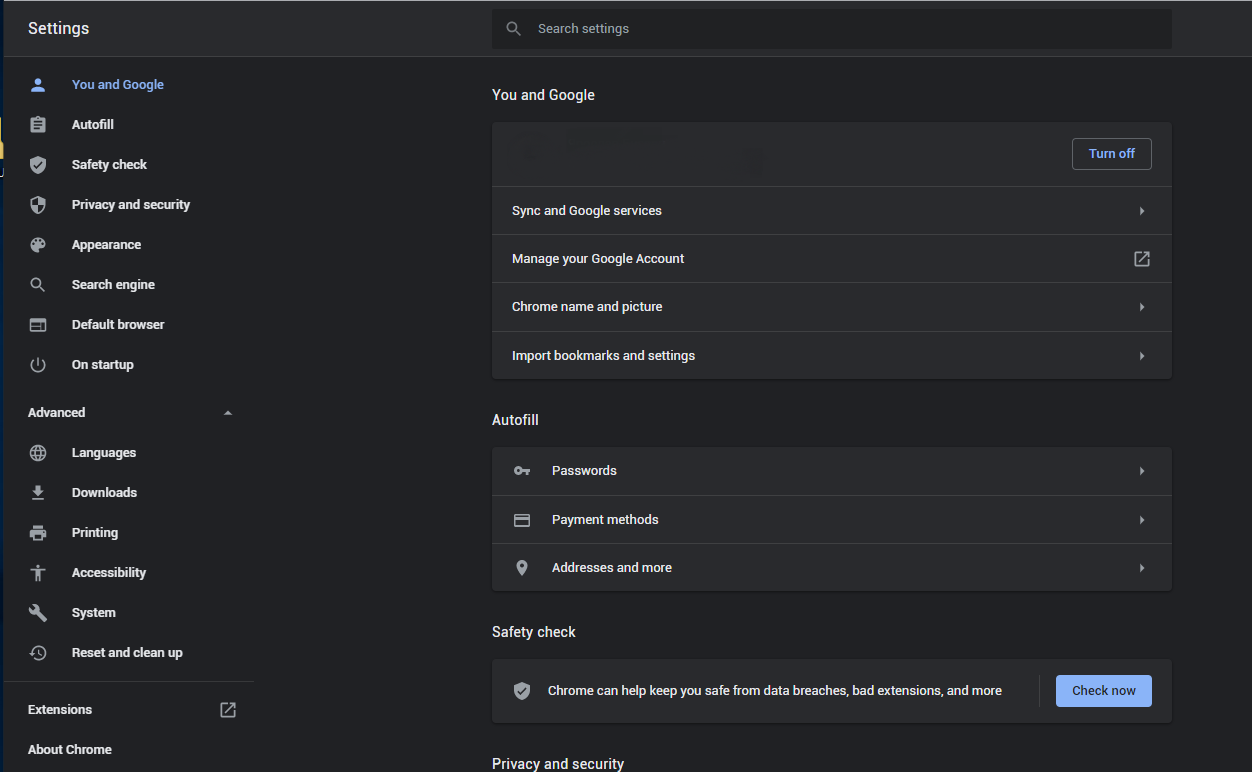
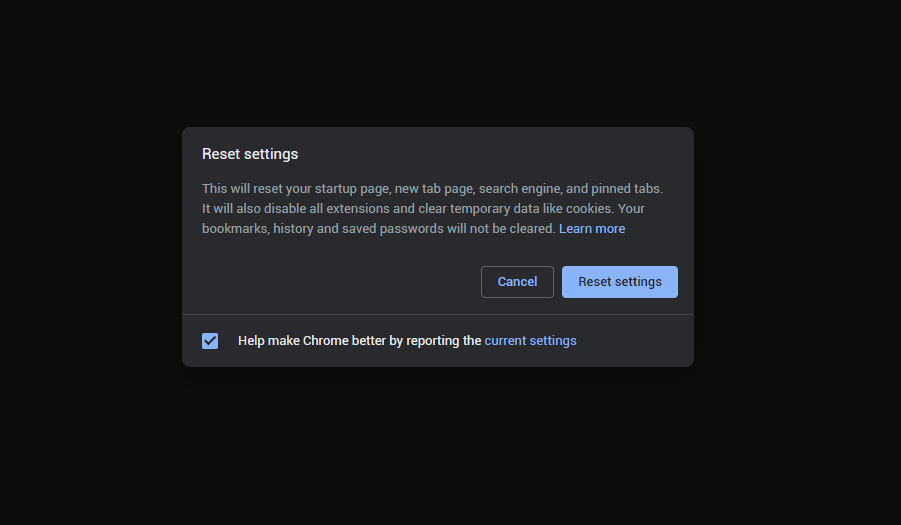
- Finally, you will see the window, where you can see all the settings which will be reset to default :
Opera can be reset in the next way
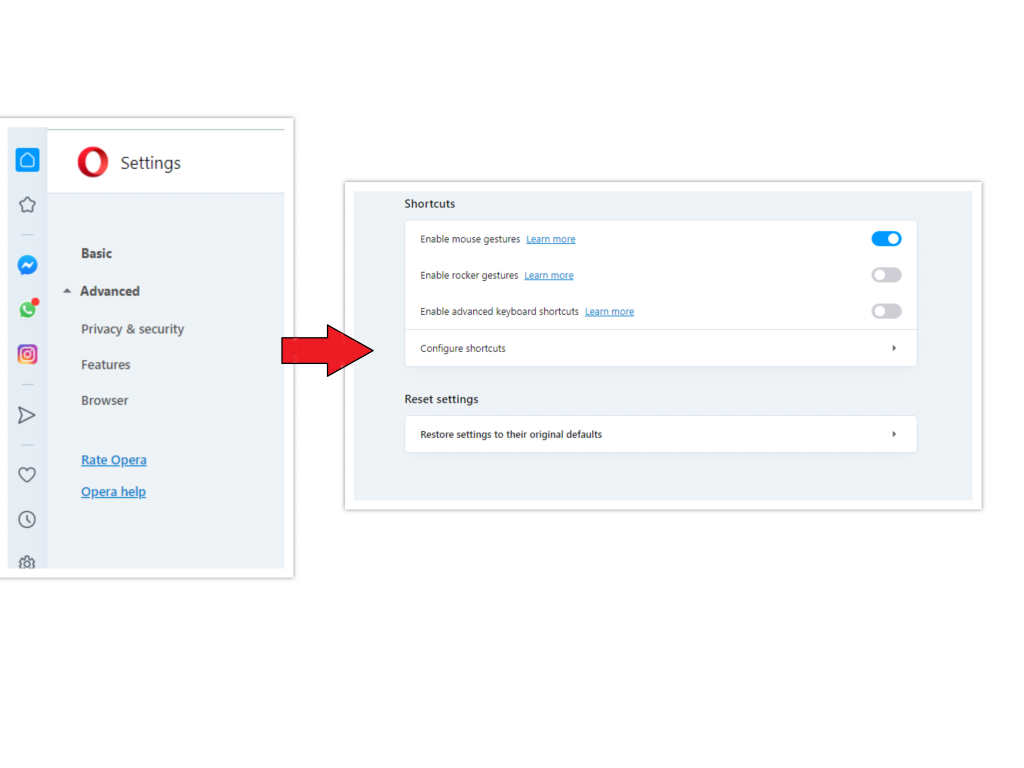
- Open Settings menu by pressing the gear icon in the toolbar (left side of the browser window), then click “Advanced” option, and choose “Browser” button in the drop-down list. Scroll down, to the bottom of the settings menu. Find there “Restore settings to their original defaults” option :
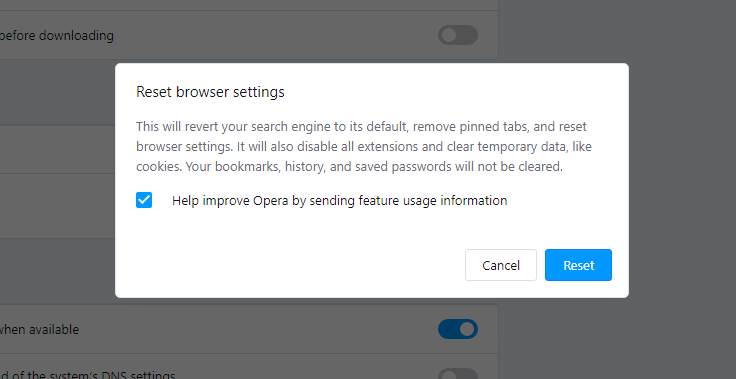
- After clicking the “Restore settings…” button, you will see the window, where all settings, which will be reset, are shown :
When the browsers are reset, you need to ensure that your web browser will definitely connect the right DNS while connecting to the web page you need. Make a text file named “hosts” on your pc’s desktop, then open it and fill it with the following text3:
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a ‘#’ symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handle within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
Find the hosts.txt file in C:/Windows/System32/drivers/etc directory. Rename this file to “hosts.old.txt” (to distinguish it from the new one), and then move the file you created on the desktop to this folder. Remove the hosts.old from this folder. Now you have your hosts file as good as new.
Nonetheless, there is one trouble that makes things much more difficult to repair, specifically without the anti-malware program. A lot of adware variants that are utilized to show you the Coolzebra.net pop-up promotions are changing the deep browser setups, disabling an access to the settings tab. So, if you attempt to change your browser settings after your PC was penetrated by pop-up-related malware, your browser will collapse quickly. Sometimes, you will see no crash, however, large lag spike after pressing the “settings” key. Browser will stop responding for ~ 30 seconds, and then it will be back to the normal, until you try to open settings once more.
Reset your browser settings with GridinSoft Anti-Malware
To reset your browser with GridinSoft Anti-Malware, open the Tools tab, and click the “Reset browser settings” button.
You can see the list of the options for each browser. By default, they are set up in the manner which fits the majority of users. Press the “Reset” button (lower right corner). In a minute your browser will be as good as new.
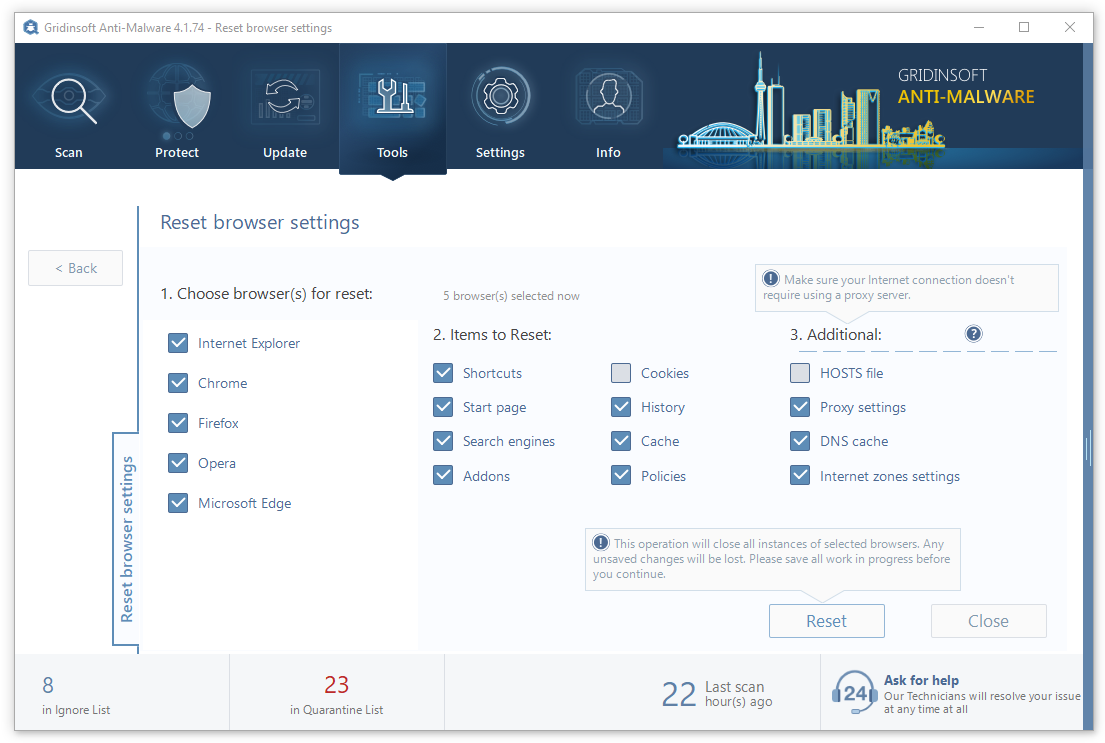
The browser reset is recommended to perform through the antivirus tool by GridinSoft, because last is also able to reset the HOSTS file without any additional commands.
How to Remove Coolzebra.net Pop-ups?

Name: Coolzebra.net
Description: Coolzebra.net - a lot of users became a target for the pop-up advertisements. I have a lot of friends who literally bombed me with the questions like “how to remove Coolzebra.net push notifications?” or “why do Coolzebra.net pop-ups keep appearing on Chrome even after AdBlock installation?”. In this article we will show you how to deal with Coolzebra.net pop-ups, which may corrupt your browser’s correct performance, and create a lot of troubles while you are working.
Operating System: Windows
Application Category: Adware
User Review
( votes)References
- More about pop-up ads on Wikipedia.
- GridinSoft Anti-Malware overview and the reasons why I suggest it for malware removal.
- Official Microsoft guide for hosts file reset.