Cobalt Strike is a powerful penetration testing tool that has gained popularity among both ethical hackers and malicious actors in recent years. In this article, we will explore the features and capabilities of Cobalt Strike, as well as its potential risks and how to mitigate them.
What is Cobalt Strike?
Cobalt Strike is commercial software developed by Fortra. It is designed to help security professionals simulate real-world attacks and test the security of computer networks. However, due to its advanced features and ease of use, Cobalt Strike is actively used by malicious actors for targeted attacks. One of the main features of Cobalt Strike is its ability to create and use custom Beacons. Beacons are a type of payload that allows attackers to maintain a persistent connection to a compromised system. With Cobalt Strike, attackers can create customized Beacons that can bypass common antivirus and endpoint detection and response (EDR) solutions.
Another feature of Cobalt Strike is its ability to mimic the behavior of legitimate software. This is accomplished through the use of “malleable profiles”. They allow attackers to modify the characteristics of their Beacons to make them appear as benign traffic. Profiles make it possible to fine-tune the behaviour pattern of a beacon. This makes it more difficult for security solutions to detect the presence of Cobalt Strike on a compromised system.
Cobalt Strike also includes a wide range of post-exploitation features. These features allow attackers to move laterally within a compromised network, escalate privileges, and gather sensitive information. Some of the most notable features of Cobalt Strike include file and directory management, remote command execution, and keylogging.
Cobalt Strike structure
The Cobalt Strike toolkit consists of several components, each of which plays a specific role in the platform’s functionality. These components include:
- Cobalt Strike Client. This is the graphical user interface (GUI) used to interact with the platform. It provides a variety of features and tools, including the ability to manage Beacon sessions, performs post-exploitation actions, and launch attacks.
- Cobalt Strike Server. This component provides the backend infrastructure for the platform, including the listener that receives incoming connections from the Beacon payload, as well as the communication channels used to send commands and data between the client and the Beacon.
- Beacon Payload. This is the agent that is deployed on the target system to establish communication with the Cobalt Strike server. The Beacon is designed to be stealthy and persistent, using various techniques to evade detection and maintain access to the compromised system.
- Malleable C2 Profiles. These are configuration files used to customize the behavior and characteristics of the Beacon payload, making it more difficult to detect and increasing its chances of bypassing security controls.
- Post-Exploitation Modules. These are modules that can be loaded into the Beacon payload to perform various actions on the compromised system. Commonly, it is used to execute commands, steal credentials, and exfiltrate data.
Infection stages
Since Cobalt Strike acts as malware, most infection stages repeat ones of regular malicious programs. They include initial access, C2 initiation, deployment of additional payload(s) and lateral movement. However, Cobalt Strike offers different variations to both the initial payload (a.k.a. beacon), and to its further instances.
Beacon and Stager
One of the most known parts of the Cobalt Strike toolkit is a beacon. Actually, this element acts like a classic backdoor that provides only one function – remote access to the attacked system. This access is commonly used to deploy other malware, or plug additional modules that allow to make the beacon more functional and stealthy.
Cobalt Strike’s beacon can be modified so it will be way less noticeable and functional. This form of him is called “stager”. Stager is a small executable or script that is used to establish an initial connection between the attacker and the target system. It serves as a “light” variant of a beacon that informs the server about the environment’s properties. The stager is convenient for delivery via a phishing email, a drive-by download, or some other means of social engineering. Once executed on the target system, the stager makes contact with the server and downloads the Beacon payload, which is then used to establish a persistent connection between the attacker and the compromised system.
C2 communication
One of the most important stages of action, present in any malware, is communication with the command and control server. For Cobalt Strike, it serves for orchestrating lateral movement, as well as delivering the payloads. As it usually happens to malware that aims at being stealthy in all aspects, it tries to make the network traffic look as normal as possible.
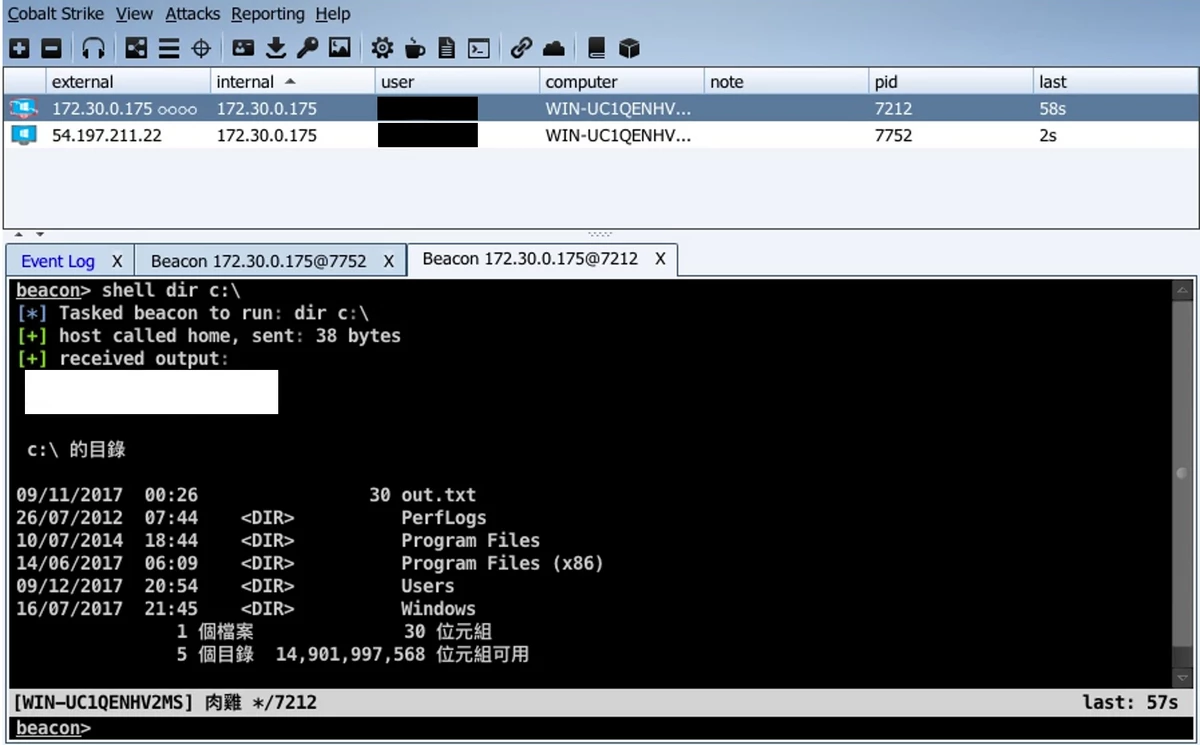
Control panel (also known as Client) of Cobalt Strike
Cobalt Strike uses several techniques to ensure that C2 communication is stealthy and difficult to detect by security solutions. One of the most important of these techniques is the use of encrypted communication channels. By default, the kit uses a custom encryption algorithm to encrypt all data sent between the client and the server, as well as between the server and the Beacon payload. This encryption helps to prevent detection by intrusion detection and prevention systems (IDS/IPS), as well as by endpoint protection solutions.
In addition to encryption, Cobalt Strike also provides several other features to help evade detection, such as the ability to use random or fake User-Agent strings, the ability to use alternate HTTP methods besides GET and POST, and the ability to customize HTTP headers and other network characteristics using Malleable C2 Profiles.
Cobalt Strike payload customisation
Cobalt Strike provides various ways to customize payloads. It makes them more difficult to detect and increases their chances of bypassing security controls. This customization can be achieved through the use of the aforementioned Malleable C2 profiles, which allow users to specify a set of attributes and characteristics. As the result, the Beacon will mimic legitimate traffic and blend in with the target environment. Moreover, it is possible to change the manner the beacon hooks up to the system.
One of the primary customization capabilities of Cobalt Strike is the ability to modify the communication protocol used by the Beacon payload. Users can specify the protocol used for communication, as well as the structure and format of the communication packets. This allows the payload to evade detection by security solutions that rely on known communication patterns or protocols.
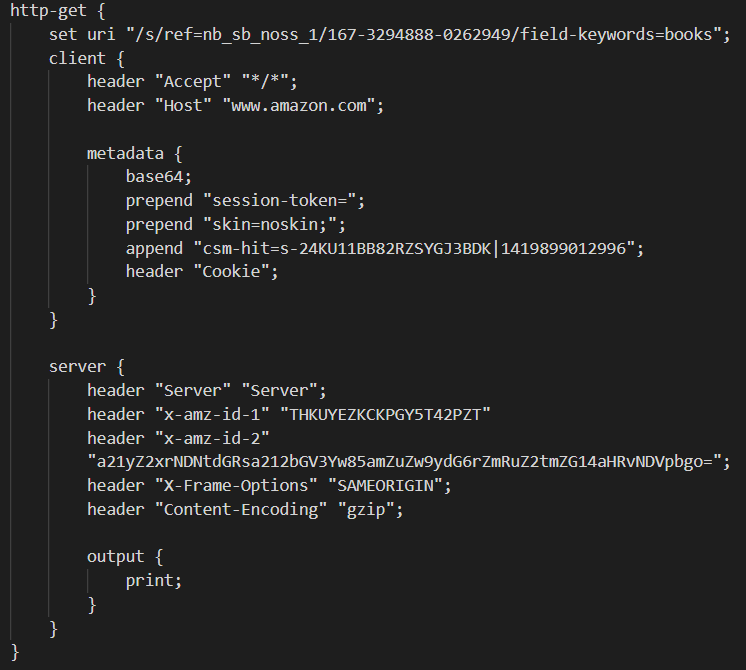
HTTP GET request formed by Cobalt Strike. It mimics a request to the server of Amazon
Another customization capability of Cobalt Strike is modifying the metadata of the Beacon payload. It includes changing its name, version, and publisher. Users can also specify the resources that are included in the payload – icons and strings. That makes it appear more legitimate. The toolkit also provides the ability to configure the behavior of the Beacon payload in response to certain events or conditions. Users can specify the actions to be taken at the payload launch, or in case of anti-malware software presence. This allows the payload to adapt to the target environment and avoid detection.
Finally, the toolkit allows customizing the Beacon with the additional functionality of post-exploitation modules. These modules can be used to perform various actions on the target system, such as executing commands, stealing credentials, and exfiltrating data. All these functions are offered as Arsenal kit.
Arsenal Kit
Cobalt Strike’s Arsenal Kit is a collection of post-exploitation tools and modules that are designed to extend the functionality of the Cobalt Strike platform. The Arsenal Kit includes a wide range of tools and modules that can be used to perform various actions on compromised systems, including privilege escalation, lateral movement, and data exfiltration. One of the most notable features of the Arsenal Kit is its ability to integrate with other tools and frameworks, such as Metasploit, PowerSploit, and Empire. This integration allows users to leverage the functionality of these tools and frameworks within the Cobalt Strike platform, further extending the capabilities of the platform.
Some of the most notable modules included in the Arsenal Kit include Mimikatz, a tool used for extracting credentials from compromised systems, and PsExec, a tool used for executing commands on remote systems. The Arsenal Kit also includes modules for performing network reconnaissance, manipulating Windows registry settings, and injecting code into remote processes. Additionally, users can add their own modules if the ones offered by the developer are not enough.
Use in cybercrime
It is obvious that such a powerful tool could not have been ignored by hackers. At some point, leaked builds of Cobalt Strike started appearing on the Darknet marketplaces. Despite some preventive measures implemented by Fortra to make it harder to use Cobalt Strike for malevolent hacking, crooks use it successfully. Here are some examples of cybercrime groups and threat actors that use this toolkit.
- FIN7 cybercrime gang. Also known as Carbanak, FIN7 is a financially motivated group known for its sophisticated attacks against businesses. It generally aims retail, restaurant, and hospitality industries. They use Cobalt Strike as a post-exploitation tool for maintaining persistence on compromised systems and stealing sensitive data.
- Lazarus Group. A North Korean state-sponsored APT group, best known for WannaCry ransomware attack. The group has been linked to several high-profile attacks, including the 2014 hack of Sony Pictures and the 2016 theft of $81 million from the Bangladesh Bank. Lazarus Group reportedly uses Cobalt Strike as part of its toolkit for cyber espionage and stealing financial data.
- Evil Corp a.k.a REvil group. Evil Corp is a cybercrime group that is likely based in Russia. The group has been known to use the article subject as part of its toolkit for conducting ransomware attacks and stealing financial data from businesses in the banking and financial services industries.
- APT41 hacker group. APT41 is a state-sponsored APT group from China. The group has been linked to the 2017 Equifax breach and the several attacks on various video game companies. This group uses Cobalt Strike to conduct cyber espionage and steal intellectual property from targets. They generally aim technology, telecommunications, and healthcare sectors.
How to protect against Cobalt Strike?
While Cobalt Strike can be a valuable tool for security professionals, its advanced features and ease of use make it a popular choice among malicious actors. As such, organizations should be aware of the potential risks associated with Cobalt Strike and take steps to mitigate them.
One of the most effective ways to mitigate the risk of Cobalt Strike is to implement strong endpoint security solutions. This includes using antivirus and EDR solutions that are capable of detecting and blocking malicious traffic. Organizations should also implement network segmentation and access controls to limit the lateral movement of attackers within their networks.
Another effective way to mitigate the risk of a Cobalt Strike attack is to implement a robust security training program. This should include regular training and education for employees on how to identify and report suspicious activity. Employees should also be encouraged to report any suspicious emails or messages to their IT department.
In conclusion, Cobalt Strike is a powerful tool that can be used for both ethical and malicious purposes. While its advanced features and ease of use make it a popular choice among attackers, organizations can mitigate the risks associated with this tool by implementing strong endpoint security solutions and a robust security awareness program. By taking these steps, organizations can better protect themselves from the threats posed by that toolkit and other advanced attack tools.

