Our research team discovered Chromnius, a rogue browser based on the Chromium open-source project1, while inspecting suspicious software-promoting websites.
Upon installing Chromnius on our virtual machine, we determined that it functions as adware and possesses typical qualities of browser hijackers. Additionally, it is highly probable that Chromnius collects private information. Moreover, unintentional downloads and installations by most users classify it as a Potentially Unwanted Application (PUA).
Overview of Chromnius browser
Adware allows the placement of third-party graphical content, such as pop-ups, banners, and advertisements, on visited websites and interfaces2.
These ads promote various types of websites, including questionable ones like gambling, adult-dating, pornography, etc.; scam-running sites like phishing, fake tech support, bogus prize giveaways, etc.; software-promoting sites like adware, fake anti-virus, browser hijacker, PUA, etc.; and malware-proliferation sites like trojans, ransomware, etc.
We observed Chromnius engaging in a typical function of browser hijackers, which involves promoting fake search engines. This rogue browser caused redirects to chromnius.download whenever users opened a new tab/window or entered search queries in the URL bar.
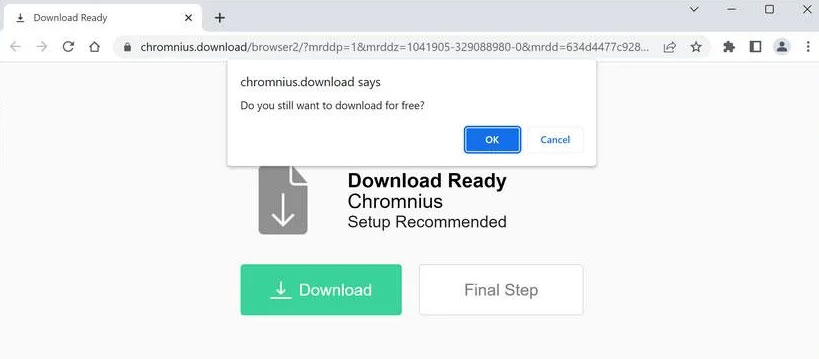
Chromnius.download
Illegitimate search engines usually fail to generate search results and redirect users to genuine ones. Chromnius.download is no exception; during our research, it redirected users to the legitimate Yahoo search engine (search.yahoo.com).
Furthermore, Chromnius likely gathers sensitive information since data tracking functionalities are common in PUAs, including adware and browser hijackers.
The collected information may include visited URLs, viewed webpages, searched queries, usernames/passwords, personally identifiable details, finance-related data, and more. This collected data can potentially be shared with or sold to third parties, including cyber criminals.
To summarize, the presence of software like Chromnius on devices can lead to system infections, serious privacy issues, financial losses, and even identity theft.
| Name | Ads by Chromnius |
| Detection | PUP.Optional.Chromnius |
| Sites | chromnius.download, zipsearch.xyz |
| Damage | System infections, privacy breaches, financial losses, and potential identity theft. |
| Fix Tool | See If Your System Has Been Affected by Chromnius Virus |
Examples of rogue browsers
We have analyzed numerous samples of untrustworthy software, including Wave Browser, Cent, and ShieldBrowser, among others.
Software like Chromnius typically disguises itself as legitimate and harmless, enticing users to download and install it by promising “handy” and “advantageous” functionalities. However, these functions rarely work as advertised and are often completely non-operational.
How did Chromnius get installed on my computer?
We downloaded Chromnius from its “official” download webpage, which turned out to be a deceptive site promoting this browser. Most users come across such websites due to redirects caused by mistyped URLs, pages using rogue advertising networks, intrusive ads, spam browser notifications, or installed adware with browser force-opening capabilities.
However, this type of software can also be distributed through other dubious and deceptive methods. “Bundling” is a marketing technique that involves pre-packaging regular installers with unwanted or malicious additions. Downloading from untrustworthy sources like unofficial and freeware sites, Peer-to-Peer sharing networks, etc., and rushing through installations using “Quick/Easy” settings increases the risk of allowing bundled content onto your device.
Intrusive advertisements are another common method of proliferating unwanted software. Clicking on these ads can trigger scripts that stealthily download and install the software.
How to avoid installing unwanted applications?
We strongly recommend researching software and downloading only from official and verified channels. When installing software, it is crucial to read the terms, examine available options, use the “Custom/Advanced” settings, and decline all supplementary apps, extensions, etc. Vigilance is advised while browsing, as fraudulent and malicious content often masquerades as legitimate.
If you encounter the aforementioned ads/redirects, inspect your device and promptly remove any suspicious applications, browser extensions, or plug-ins. If your computer is already infected with Chromnius, we recommend using Gridinsoft Anti-Malware to automatically eliminate this adware by running a scan.
How to remove the Chromnius from my PC?
Chromnius adware is difficult to delete by hand. It puts its data in multiple places throughout the disk, and can get back itself from one of the parts. Furthermore, countless modifications in the registry, networking settings and also Group Policies are pretty hard to discover and change to the initial. It is much better to use a special app – exactly, an anti-malware app. GridinSoft Anti-Malware will definitely fit the most ideal for malware elimination purposes.
Why GridinSoft Anti-Malware? It is pretty light-weight and has its databases updated practically every hour. Additionally, it does not have such problems and exploits as Microsoft Defender does. The combination of these details makes GridinSoft Anti-Malware ideal for getting rid of malware of any kind.
Remove the Chromnius with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of Chromnius the default option is “Delete”. Press “Apply” to finish the malware removal.



Frequently Asked Questions (FAQ)
This is a rogue browser based on the Chromium open-source project, known for its adware and browser hijacking functionalities.
It can impact your computer by displaying intrusive advertisements, promoting fake search engines, collecting sensitive information, and potentially leading to system infections and privacy issues.
It can be downloaded from deceptive websites or distributed through methods like mistyped URL redirects, rogue advertising networks, intrusive ads, spam browser notifications, and bundled software.
The risks of having Chromnius on your computer include system infections, compromised privacy, financial losses, and the potential for identity theft.
Yes, Chromnius is considered a Potentially Unwanted Application (PUA) due to its characteristics as adware and its tendency to be downloaded unintentionally by most users.
To avoid installing unwanted applications, it is recommended to research software, download from official and verified sources, carefully read terms and options during installation, use the “Custom/Advanced” settings, and decline any supplementary apps or extensions.
If your computer is infected with Chromnius, it is advisable to remove any suspicious applications, browser extensions, or plug-ins and consider running a scan with an anti-malware tool like Gridinsoft Anti-Malware.
Yes, it can pose a threat to your privacy as it has the ability to collect sensitive information, including visited URLs, search queries, usernames/passwords, personally identifiable details, and finance-related data.
Yes, other examples of rogue browsers similar to Chromnius include ClearBrowser, CryptoTab Browser, Cent, and ShieldBrowser, among others.
To protect your computer from threats like Chromnius, it is recommended to use reliable anti-malware software, keep your operating system and applications up to date, exercise caution when browsing the internet, and avoid downloading software from untrustworthy sources.
How to Remove Chromnius Malware
Name: Chromnius
Description:
Chromnius is a sophisticated and insidious rogue browser that operates as adware and exhibits characteristics commonly associated with browser hijackers. It is based on the Chromium open-source project, which adds to its deceptive nature. Chromnius is specifically designed to compromise users' browsing experiences, invade their privacy, and potentially expose them to various security risks.
Unlike legitimate browsers, Chromnius is intentionally developed to serve as a vehicle for intrusive advertising campaigns. It leverages adware functionalities to forcefully inject third-party graphical content, such as pop-ups, banners, and other forms of advertisements, into websites and user interfaces. These advertisements often promote questionable websites, including those involved in gambling, adult-dating, pornography, scam operations such as phishing and fake tech support, software promotion of adware, fake anti-virus, browser hijackers, and even sites associated with the proliferation of malware like trojans and ransomware.
Offer price: 0.0
Operating System: Windows
Application Category: Adware
User Review
( votes)References
- More about open-source Chromium project: https://www.chromium.org
- More about Adware: https://gridinsoft.com/adware


