X3ph initially analyzed ChromeLoader, and G-Data researchers later dubbed it the Choziosi loader. This malware aims to install malicious extension(s) onto browsers. Currently, there are two distinct variants of ChromeLoader that have been detected – one targets Windows Operating Systems, and the other targets MacOS.
It’s important to note that this piece of malicious software actively spreads through Twitter using QR codes that promote pirated software, primarily video games, and media such as movies and TV shows.
Overview of ChromeLoader malware
Infection chain starts with Tweets
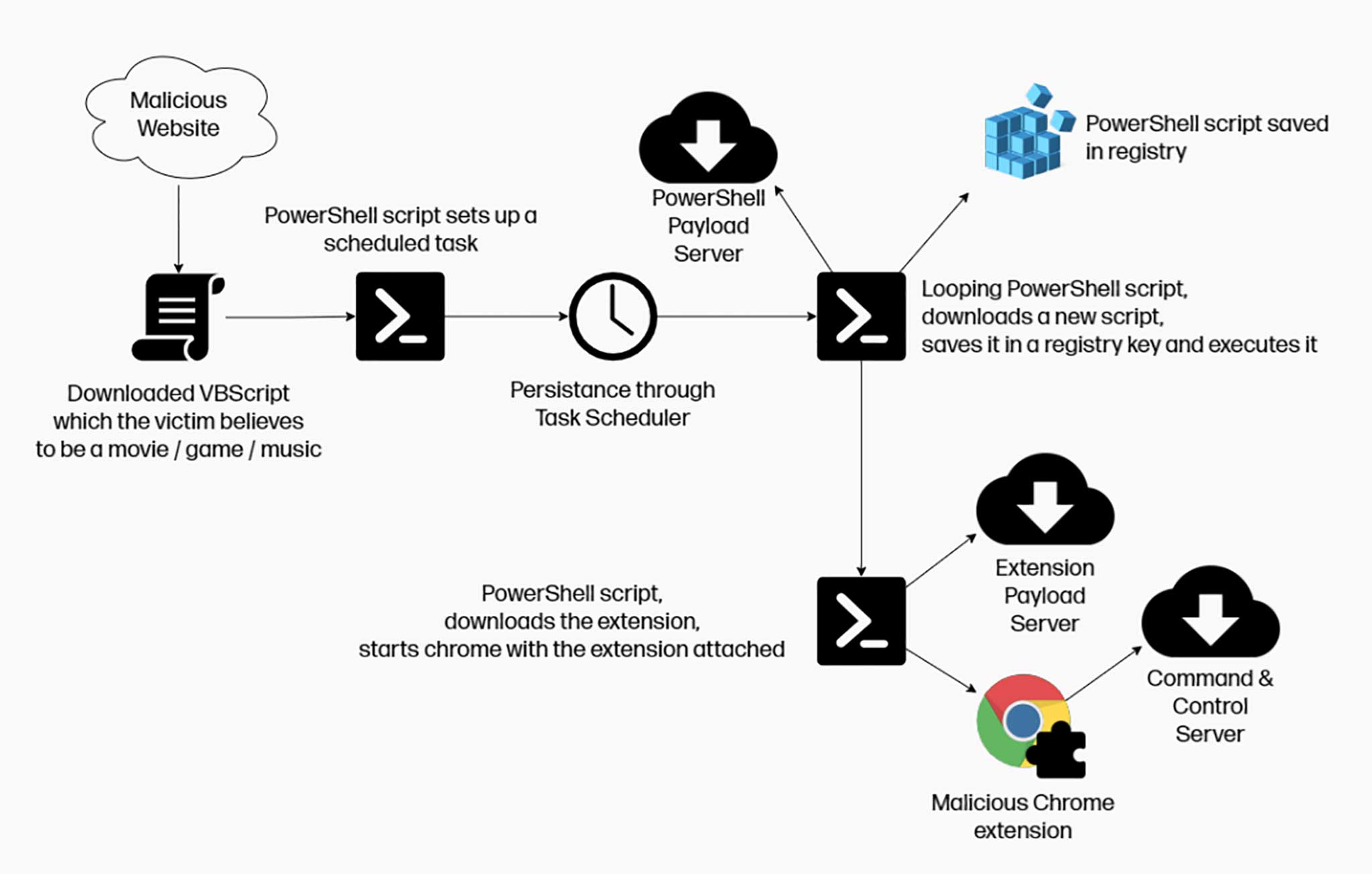
As mentioned earlier, ChromeLoader is designed to install malicious extensions onto browsers. The observed infection chain starts with Tweets (Twitter posts) that advertise pirated content through QR codes presented in meme format, tricking victims into downloading an ISO file.
G-Data researchers conducted an in-depth analysis of this loader and the malicious extension. Their research revealed that the ISO file consists of two components – “_meta.txt” and “downloader.exe“. The former contains an encrypted PowerShell script, while the latter is used to decrypt it.
PowerShell script
The PowerShell script creates a task named “ChromeTask” (may vary), which is scheduled to run every ten minutes. Additionally, the PowerShell script downloads the malicious Google Chrome browser extension “archive.zip“. However, due to the repetitive task, some victims have reported that their Chrome browsers continuously close themselves, which inadvertently facilitates the swifter detection of ChromeLoader.
It’s worth mentioning that “downloader.exe” may display an alert to users stating that the Operating System is incompatible with the software.
Malicious browser extension
G-Data’s analysis primarily focused on the malicious browser extension, as it had not been thoroughly researched before. The Chrome extension is heavily obfuscated, making the analysis more challenging.
This software utilizes techniques to ensure persistence, specifically by denying access to the Google Chrome extensions list (“chrome://extensions/”) and redirecting users to general settings (“chrome://settings”), thereby preventing them from removing the malicious extension.
The Chrome extension’s functionalities were found to include adware and browser hijacker activities. In other words, this malware aims to display deceptive and malicious advertisements and modify browser settings to cause redirects to fake search engines, potentially concluding with legitimate ones like Google, Yahoo, Bing, etc.
Using PowerShell and extensive obfuscation is uncommon for adware and browser hijackers, but it is standard for information-stealing programs, spyware, and other types of malware. However, it’s possible that ChromeLoader is still under development and may be updated with additional harmful functionalities. Nonetheless, ChromeLoader remains a significant threat in its current form (more information on new variants below).
Colin Cowie’s research determined that the Mac version of ChromeLoader operates similarly to the Windows variant, showing ads and causing redirects. Notably, this version can install malicious extensions on both Google Chrome and Safari browsers.
If you suspect that your device is infected with ChromeLoader malware, we strongly recommend using an anti-virus to promptly remove it.
| Name | ChromeLoader |
| Detection | Trojan:MSIL/Tnega!mclg |
| Similar behavior | Rustystealer, Puadlmanager |
| Damage | You may encounter several issues while browsing the internet, such as experiencing advertisements that do not originate from the sites you are visiting, intrusive pop-up ads, a decrease in internet browsing speed, and manipulation of your internet browser settings. In addition, you may be forced to visit the hijacker’s website and use their search engines to conduct internet searches. |
| Fix Tool | See If Your System Has Been Affected by ChromeLoader Virus |
How did ChromeLoader infiltrate my computer?
As we mentioned earlier, ChromeLoader has gained significant traction through Tweets that promote illegal content, such as pirated video games, editing software, movies, and TV series. These Tweets include QR codes that entice users into downloading an infectious ISO file. Additionally, ChromeLoader is distributed through malicious ads, browser redirects, and YouTube comments.
However, it’s important to note that ChromeLoader malware may also be distributed on other platforms and potentially using different disguises.
Malware is commonly spread using various techniques, with phishing and social engineering playing a significant role in the distribution of malicious software. Virulent files can take the form of archives, executables, PDF and Microsoft Office documents, JavaScript, and more. Once a malicious file is opened, the infection chain is initiated.
The most prevalent methods of malware proliferation include stealthy and deceptive drive-by downloads, spam emails and messages, online scams, freeware and third-party download websites, P2P sharing networks (such as Torrent clients and eMule), illegal program activation tools (commonly known as “cracks”), fake updates, and malvertising.
How to avoid installing malware?
We strongly recommend exercising caution while browsing the internet, as illegitimate and malicious content often appears harmless. It is essential to download software only from official and verified sources.
Equally important is the activation and updating of software using the functions and tools provided by genuine developers. Third-party sources can potentially include malware.
Another crucial recommendation is to handle incoming mail with care. Do not open attachments or click on links found in suspicious or irrelevant emails and messages, as they can lead to system infections.
We cannot emphasize enough the importance of having a reliable and up-to-date anti-virus program installed. Security software should be used to perform regular system scans and remove threats and issues. If you suspect that your computer is already infected, we recommend running a scan with Gridinsoft Anti-Malware, which can automatically eliminate infiltrated malware.
How to remove the ChromeLoader from my PC?
ChromeLoader malware is very difficult to delete manually. It stores its documents in multiple locations throughout the disk, and can get back itself from one of the elements. Moreover, a lot of modifications in the registry, networking setups and also Group Policies are really hard to find and change to the original. It is far better to make use of a specific tool – exactly, an anti-malware tool. GridinSoft Anti-Malware will fit the most ideal for malware removal objectives.
Why GridinSoft Anti-Malware? It is very lightweight and has its detection databases updated almost every hour. In addition, it does not have such bugs and weakness as Microsoft Defender does. The combination of these details makes GridinSoft Anti-Malware perfect for removing malware of any type.
Remove the ChromeLoader with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of ChromeLoader the default option is “Delete”. Press “Apply” to finish the malware removal.



Frequently Asked Questions (FAQ)
Reformatting your storage device should only be considered as a last resort for removing ChromeLoader malware. Prior to taking such drastic action, it is advisable to perform a comprehensive scan using trustworthy antivirus or anti-malware software.
Malware poses a significant risk to the security and privacy of sensitive information, potentially leading to identity theft, financial loss, and unauthorized access to personal accounts. Furthermore, it can disrupt the normal operation of a system, causing performance issues, system crashes, and data corruption.
The purpose of ChromeLoader is to enable remote access and control of compromised devices. It allows threat actors to perform various malicious activities, such as unauthorized access, data theft, system manipulation, and disabling security measures, potentially causing significant harm to individuals and organizations.
Gridinsoft Anti-Malware has the ability to identify and eliminate most malware infections. Nevertheless, it is crucial to recognize that sophisticated malware can remain hidden deep within the system. Consequently, conducting a complete system scan is imperative to detect and eradicate malware.
How to Remove ChromeLoader Malware
Name: ChromeLoader
Description: ChromeLoader is a type of malware that is specifically designed to install malicious browser extensions onto web browsers. It has been analyzed and identified by security researchers, initially by x3ph and later dubbed as Choziosi loader by G-Data researchers. This malware primarily targets users of Google Chrome and Safari browsers, infecting both Windows and Mac operating systems. ChromeLoader is known for its distribution through Twitter, where it spreads via QR codes disguised as memes. These QR codes are used to promote pirated content, such as video games, movies, and TV shows. When unsuspecting users scan these QR codes and download the associated ISO file, their systems become infected with ChromeLoader.
Operating System: Windows
Application Category: Malware