A botnet is a network of compromised computers that are controlled remotely by a hacker or group of hackers. The term botnet is derived from the words robot and network. In a botnet, each computer, also known as a bot, is infected with malware that allows it to be controlled remotely. The botnet is typically used for malicious purposes – malware deployment, DDoS attacks, spamming campaigns and other stuff.
How are botnets created?
Botnets can be created in several ways. However, the most common method is to infect a large number of computers with malware, such as a backdoor, spyware or dropper. Depending on the type of used malware, these botnets will have different functionality. Though modern trends to make malware all-in-one samples allow making botnets omni-purpose. The malware is often spread through phishing attacks, social engineering, or exploiting vulnerabilities in software or hardware. Once the malware is installed, it communicates with a C&C server and notifies about its readiness. The C&C server sends instructions to the botnet, such as launching an attack, stealing data or deploying malware. Malware master can cease the network in one click – by sending self-destruction commands to all bots.
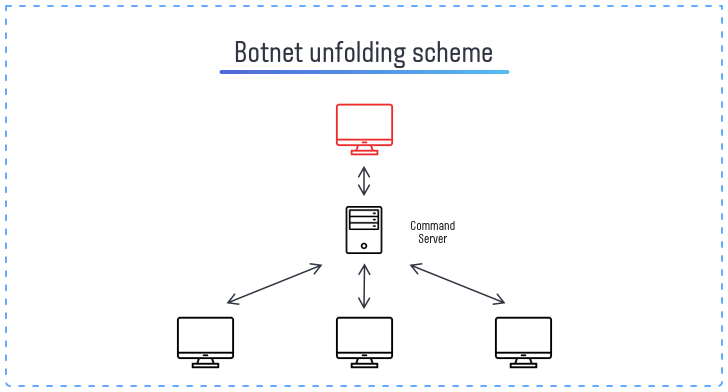
Application of Botnets
Botnets can be used by a variety of individuals or organisations, including cybercriminals, hacktivists, and nation-state actors. Cybercriminals may use botnets to carry out DDoS attacks, which overwhelm a website with traffic and cause it to crash. They’re also used to steal sensitive data, such as login credentials or financial information. Hacktivists may use botnets to launch attacks against websites or organisations that they disagree with politically or ideologically. Nation-state actors may use botnets to conduct cyber espionage or sabotage operations.
Error 404 is a typical sign of a website overload during a DDoS attack
Another widespread application of botnets is spamming. That requires more advanced functionality of a base malware – it should grant attackers with remote access to each system. Sure, they don’t really roam from one PC to another, as it is too long, and pass all the jobs to scripts, or exact malware is able to commit mailing. However, these botnets may be very effective when it comes to spamming. Some malware allows using the contact list of most popular mailing clients as a list of spam receivers. In conjunction with an email address that belongs to someone these people are familiar with, the efficiency is devastatingly good. Though, nothing obstructs using more common Darknet-bought email databases.
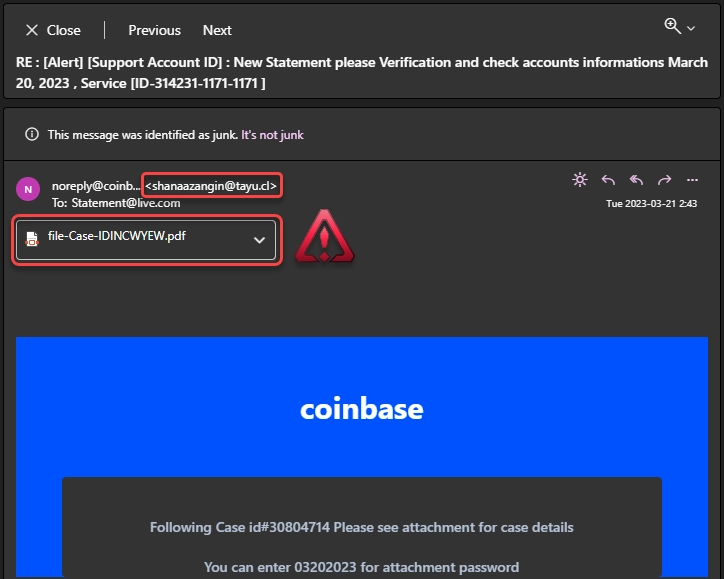
The classic example of email spam
Third possible use for botnets is malware deployment. It requires the use of a specific malware type – droppers a.k.a downloaders. Their sole purpose is to deliver other malware to the target device. Hackers may unfold a huge botnet based on a dropper, and then offer it in the Darknet for everyone who wants to deploy malware. Since such botnets are not easy to create, crooks often struggle to have effort-worthy results by using these networks to deliver their malware: they’re often flooded with other malware.
Is botnet illegal?
Yes, botnets are illegal under most circumstances. Botnets are typically used for malicious purposes, such as launching cyber attacks, stealing sensitive data, or sending spam emails. These activities violate various laws and regulations related to computer security, privacy, and cybercrime. For example, in the United States, the Computer Fraud and Abuse Act (CFAA) prohibits unauthorised access to protected computers and the distribution of malware. The CFAA also provides for criminal and civil penalties for those who violate its provisions.
In addition to being illegal under criminal and civil law, the use of botnets can also result in severe reputational damage and financial losses for organisations and individuals. Organisations that are targeted by botnets may suffer from loss of revenue, customer trust, and intellectual property. Individuals whose computers are infected with botnet malware may have their personal information compromised or their computers used to carry out further cyber attacks.
Attacks that Used Botnets
Sure, not all botnets are large enough to cause significant impact – one that is worth newsletters’ headlines. Though a couple became a worldwide phenomenon – let’s have a look at them.
- Mirai botnet’s DDoS attacks. In 2016, the Mirai botnet attacked the DNS provider Dyn with a chain of powerful DDoS attacks. The attacks disrupted a number of popular websites and caused significant Internet disruptions across the United States. The botnet was established in a pretty unusual manner: someone posted Mirai malware source code, allowing anyone to use it. As the result, numerous hackers used this code to spread their own Mirai samples and commence a DDoS.
- TrickBot trojan botnet. TrickBot is a banking trojan that is commonly distributed through other botnets. The malware can steal sensitive information, such as login credentials and financial data. Aside from that, TrickBot is capable of acting as a downloader. For that quality, it has been used in a variety of cyber attacks, including ransomware deployment and email compromise.
- Emotet botnet. Emotet is a modular malware that is commonly spread via email spam. The malware can be used to steal sensitive information, install additional malware, and carry out spam campaigns. Emotet has been used in a variety of cyber attacks, including targeted spyware and backdoor deployment. However, its most notable contractors are mass-market ransomware gangs – such as STOP/Djvu.
- QBot botnet ransomware attacks. QBot, also known as QakBot, is an infostealer that is also capable of malware delivery. It is one of the oldest active malware families, starting around 2008. The QBot botnet has been mainly used to distribute ransomware.
How to avoid becoming a part of a botnet?
Botnets are difficult to detect and mitigate because they are often spread across multiple computers and locations. To combat botnets, organisations can take several measures, such as using antivirus software, applying security patches, and implementing network security measures. Network security measures can include firewalls, intrusion detection and prevention systems, and security information and event management (SIEM) systems. Solitary users are not invincible to this fate either – actually, botnets generally consist of single-user systems.
- Applying security patches is essential when it comes to protecting the environment against vulnerability exploitation. Crooks use it for both initial access and lateral movement; responsible software vendors always haste to release a fix. Keep track of recent cybersecurity news to see if there are any widely-exploited vulnerabilities, especially in software used in your company.
- Network security measures may suppose both passive measures, like setting up firewalls, and active ones – such as implementing NDR solutions. The latter don’t only track and block suspicious connections, but also log all the events. It may be pretty useful for security improvement to analyse the logs of a recent attack – that uncovers a lot of information regarding attackers’ tactics.
User-specific anti-botnet advice
- Using anti-malware software is advice for all categories of users. In corporations, more complex and all-encompassing solutions are needed – ones that are able to keep track of the entire network. Modern EDR and XDR solutions are what will fulfil that need. Users, however, don’t need that much of a complexity, and can go with a classic reliable anti-malware program. GridinSoft Anti-Malware is worth trying out – it can boast of a complex three-component scanning system and a number of functions that can help you to customise the protection.
- Don’t trust the emails blindly. Most of the time, the emails you receive are genuine and benevolent. However, email spam has a huge share in malware distribution, and people may receive them daily without even paying attention. Fake emails can be recognised by the following signs:
- Suspicious sender. The sender’s email address may look strange, contain random characters, or be a mix of numbers and letters. The name of the sender may also be suspicious or unfamiliar.
- Generic greeting. Spam emails often use generic greetings, such as “Dear customer” or “Hello user,” rather than addressing the recipient by name.
- Poor grammar and spelling. Spam emails may contain typos, grammatical errors, or awkward sentence structure, which is often a sign that the email was not written by a native speaker.
Seeing at least 2 of 3 means you’re definitely dealing with a scam. Such emails may contain a malicious attachment, or a link to a phishing site/exploit landing page – an equally unpleasant thing. Never follow them, and never run attached files – that advice will save your money and time.
