Borat RAT (remote-access trojan) recently appeared on various Darknet malware selling forums. That threat appears to be an all-in-one RAT with a user-friendly interface. A large list of functions allows the threat actors to perform almost any actions with the infected machine(s), and the overall stealthiness of this malware makes it hard to get rid of.
Borat Trojan analysis
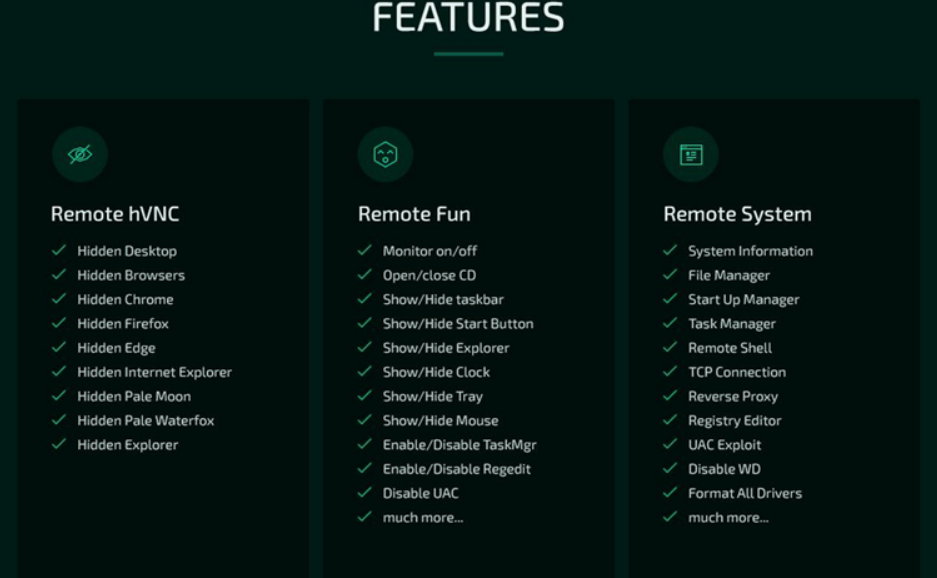
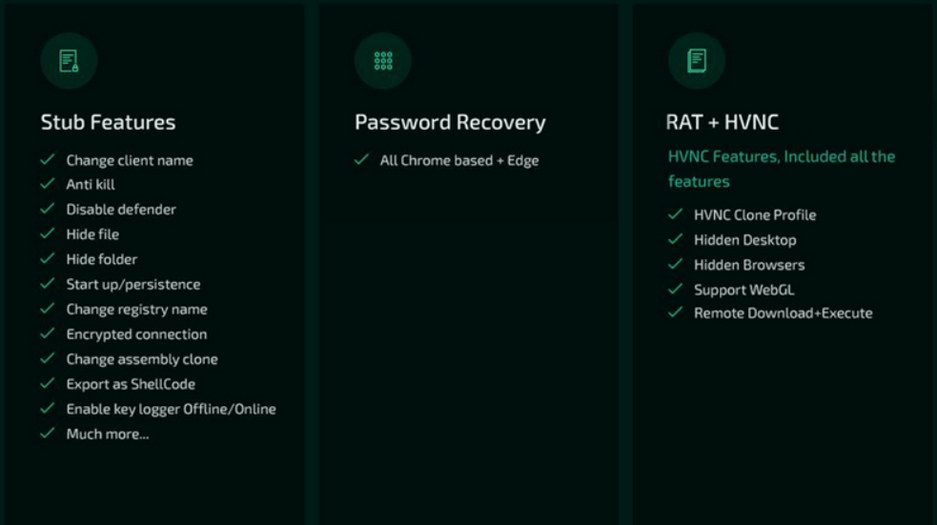
Analysts from the Cyble – threat intelligence organisation – released a large report regarding the Borat RAT. As they say, there have already been several attacks with this malware, and it is not going to stop. Its developers say that their malware can provide the capabilities to perform a DDoS-attack and ransomware injection. Along with these types of threats, it may offer some joking actions, as well as all specter of other cyberattack vectors. In particular, it also carries spyware, stealer, downloader and keylogger functions.
Additional stealthiness for Borat malware is provided by the ability to cut the payload into pieces that carry separated functions. For example, if you need only a DDoS module, you may cut off the rest and get a lightweight executable file that will be even harder to detect. A pretty useful thing for commencing an attack on both individuals and corporations. Moreover, you may choose which module to run even after the injection – the residue will not be installed. Such flexibility gives this malware an enormous advantage.
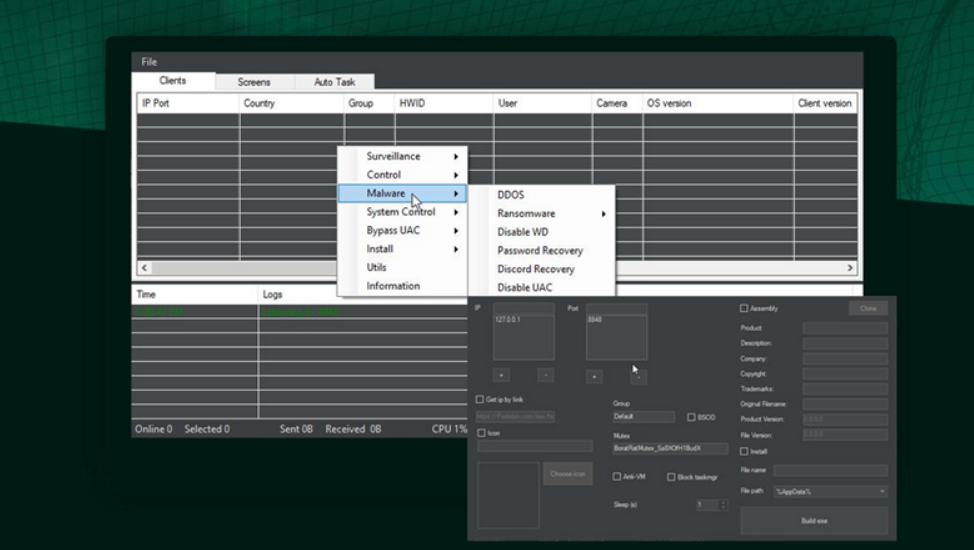
Web interface of Borat RAT
The distribution model of this remote-access trojan is still not clear. Cyble analysis found no evidence of paid subscription or single-time purchase of a ready product. But it is obvious that such a well-done product took a long time to create, and its author will be happy to receive a penny for its brainchild. Or maybe this person plays a dirty trick with the crooks who are using this trojan? Or someone from the executive authorities wants to know more about threat actors who are so active in the Darknet? Too many questions with no answers.
How dangerous is the Borat RAT?
Just as any other multi-functional malware, it carries a lot of danger to any kind of users. However, using it on individuals is just overkill – like hunting rabbits on a tank. Attacks on corporations are more likely, especially given the amount of functionality this RAT has. Remote-access trojans are dangerous not only because they act as a backdoor with multiple other functions. They may create an advanced persistent threat that is very hard to uproot. And once again – Borat RAT has all possible functions to do that. The easy interface will give the ability to commit the cyberattack even to the least experienced crooks.
Borat RAT offers the following functions:
- Keylogger – monitors and records keystrokes, storing all this data in a TXT file.
- Ransomware – deploys ransomware on the victim’s system, automatically generates a ransom note.
- DDoS – sends junk traffic to the attacked server using the resources of a compromised device.
- Audio stream recording – Records audio using a microphone on a compromised device, the corresponding files are stored in WAV format.
- Video recording – if a camera is available on the device, the malware can record a video stream.
- Remote Access – Provides remote desktop functionality to operators.
- Credential theft – Searches Chromium-based browsers files in an attempt to get usernames and passwords.
- Stealing Discord Tokens – Pulls Discord tokens from the victim’s system.
As you can see, the words about the massiveness of its functions are not an amplification of any sort. These functions along with ease of use already attract a lot of threat actors. RATs are not very hard to detect, but this one definitely has several aces up the sleeve. Anti-malware vendors must do their best to prevent this thing from spreading as massively as Emotet did, for example.
User Review
( votes)