Cisco Talos has published a study on Astaroth malware, which describes how Astaroth hides management servers.
Specialists first noticed the Astaroth infosteeler in 2018. For example, analysts from IBM and Cofense spoke about the malware. Then, just like now, Astaroth attacked mainly users from Brazil (less often from Europe) and employed various legitimate solutions, for example, exploited the WMIC command-line interface to secretly download and install malicious payloads.Since then, Astaroth has turned into one of the most complex and secretive types of malware: the infostiller uses many anti-analytical and anti-sandbox mechanics, which makes it very difficult to detect the malware and to study its operations”, — say Cisco Talos researchers.
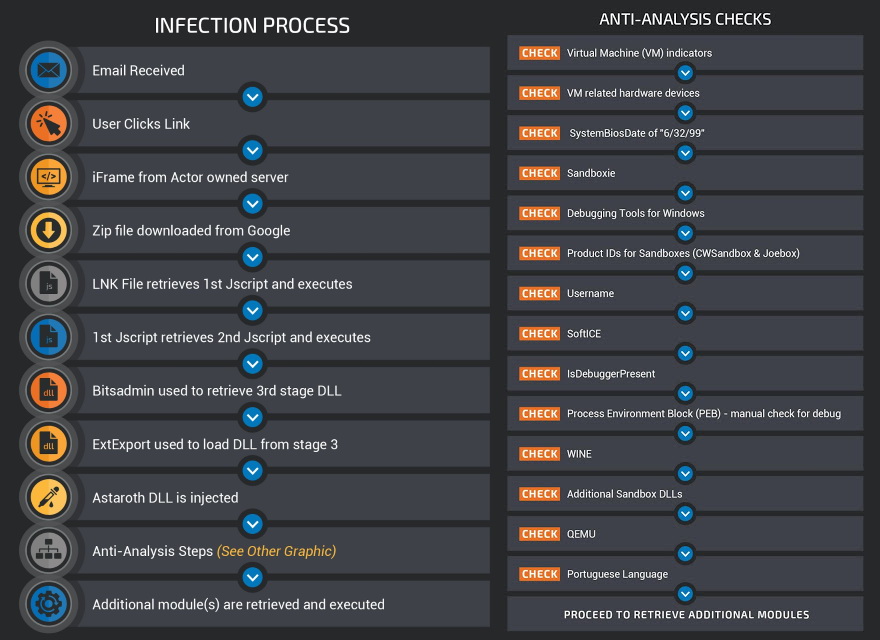
In a report released this week by Cisco Talos experts, Astaroth continues to evolve. Trojan still relies on email spam and fileless attacks (LOLbins) to spread the trojan, but it also received two important updates.
The first of these updates contained mentioned above large selection of anti-analytical and anti-sandbox mechanics.
So, the malware performs various checks before starting an operation to make sure it works on a real computer, and in the sandbox, where information security researchers can study it. This helps Astaroth hide their payloads and stay unnoticed.
Astaroth is secretive in nature, the developers did everything possible to ensure its successful operation,” experts say Cisco Talos. “They introduced [in Astaroth] a confused maze of antianalytic and anti-sandbox checks designed to prevent the detection or analysis of malware. It all starts with effective and efficient baits, continues with numerous layers of obfuscation, and this is before [Astaroth] shows any malicious intent. Then comes a series of full checks in search for various tools and techniques that can be used both by researchers and secure environments like sandboxes. This malware is very difficult to analyze because of its nature.”
However, the developers of the trojan were not limited to the described above obstacles. So, after the last update, Astaroth began to use channel descriptions on YouTube to hide the URLs of its control servers from prying eyes.
Researchers explain that after a trojan has infected a victim’s computer, it connects to a special YouTube channel and accesses the description field of that channel. The field contains encrypted and base64 encoded text with the URLs of the management servers. Having decrypted the data, Astaroth connects to these URLs in order to receive new commands from its operators and give them the stolen information.
Previously, similar tactics were already exploited by the authors of the Janicab malware (in 2015), as well as the operators of the Stantinko botnet (in 2019). However, with Astaroth, this way of hiding URLs is just one of three methods that the malware uses to discover and connect to its C&C servers.
According to Cisco Talos analysts, this once again demonstrates the high complexity of Astaroth compared to other malicious campaigns.
Recall that also researchers from Cisco Talos information security company found two vulnerabilities in the GoAhead web server.