The developers of anti-malware programs are doing their best to make their products perfect. However, “perfect” is not always one that detects all viruses. It is a very hard job to get rid of all false positive detections – situations when an AV engine detects a thing that is not malicious.
What are false positives in anti-malware software?
First, anti-malware programs during normal scans generally rely on detection databases1. They consist of hashes of malicious files – literally, their digital footprints. A drop of difference in code – and the hash is completely different. When the hash of a file on your computer is the same as one in the database, antivirus marks it as malicious. But there are several moments when even this, the most reliable mechanism may malfunction.
Sometimes, virus creators may use the same files as the creators of legit apps do. In this case, some of the programs which have such files may be marked as dangerous. Antivirus engine does not care if you know this program well and use it every day – it sees something suspicious and marks it. In situations when the program has just been released or is even still in beta testing, anti-malware programs can mark it as malicious. That happens because the security tool does not have the security certificate of this program, and thinks it is dangerous.
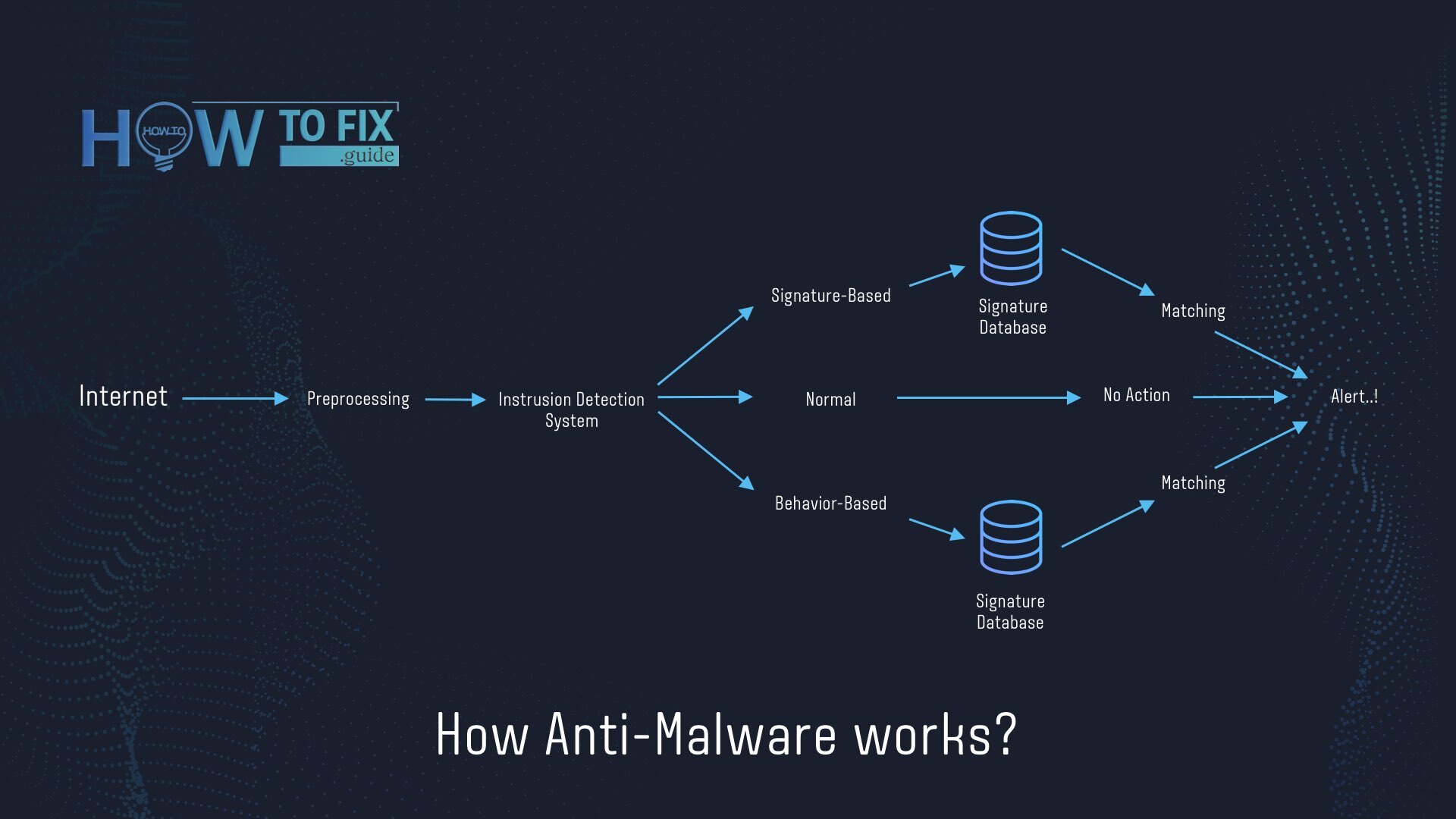
Scheme of anti-malware software detection entige algorithm
Heuristic engines and neural network detections
These things are the most often source of a problem. A heuristic engine checks the behavior of each process that is running in your system. When something does the suspicious action, an antivirus that uses heuristics marks it as suspicious and blocks its activity. However, it is pretty easy to get into the situation when a legit application is marked – just because antivirus considers this action malevolent. Those actions may be registry editing, editing the Group Policies, changes to network settings, et cetera. Sure, malware often makes such changes, but there are also plenty of programs that do the same things, but for benevolent reasons. Avoiding such detection is like catching a black cat in a dark room.
Neural networks are an even bigger mess. They are expectedly a magic pill that allows detecting even the newest malware – just based on the code, actions or files of the suspect2. At the same time, it is extremely hard to teach the neural network to set it up. Moreover, if it is teaching on-run, amidst the scans, or proactive protecting, there is a big chance that it will understand something wrongly. And the headache of correcting the neural network’s false detections can barely be compared with anything. They are like a separate brain based on the CPU, and retraining it takes hours and may lead to even worse results.
Types of false positive detection and their origins
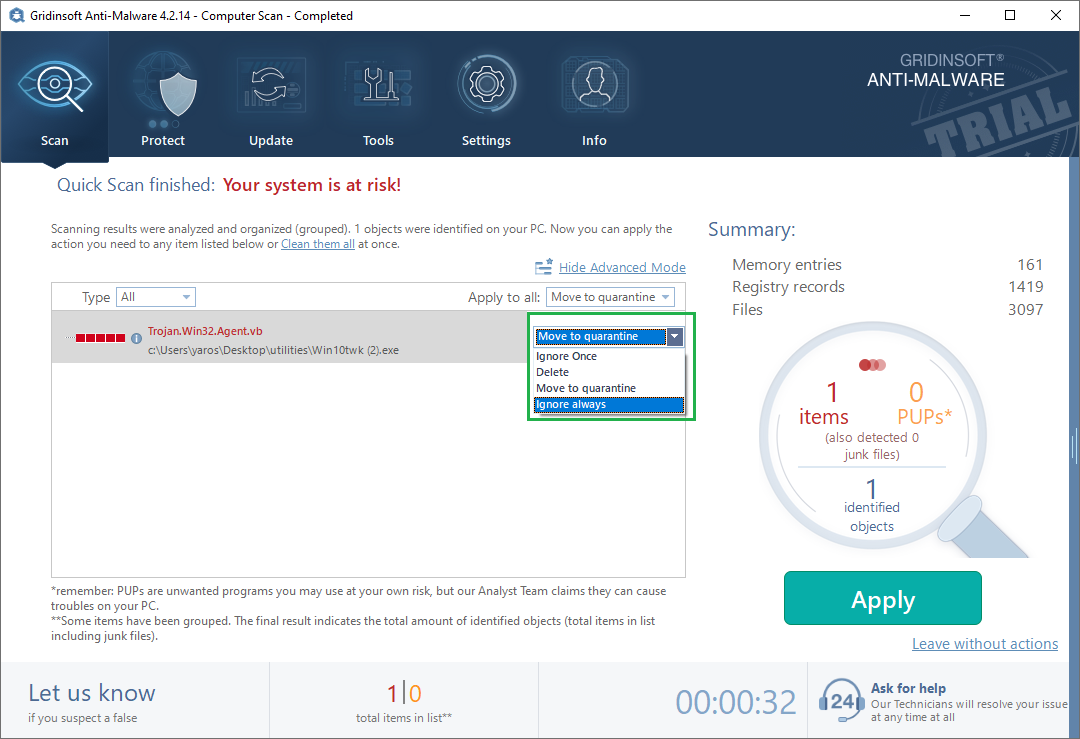
Anti-malware software scans numbers of different system elements. Depending on the name of the detection, it is quite easy to understand which subsystem got this detection. At least, most of the good anti-malware programs offer “readable” detects. For example, detection that was done by a heuristic engine contains a “Heur” part in its name. When it comes to the detection of possibly dangerous sites, it specifies a browser name and adds a “URL” part. If it detects something during the forced scanning, it marks the elements by the virus names and ones it is not certain about – as “Susp”.
Why am I telling you this? Just you to understand how to deal with these problems. Precisely, how to understand where the problem is. False-positive detections in antivirus software are classified just the same as regular detections. Hence, their name can say a lot to you.
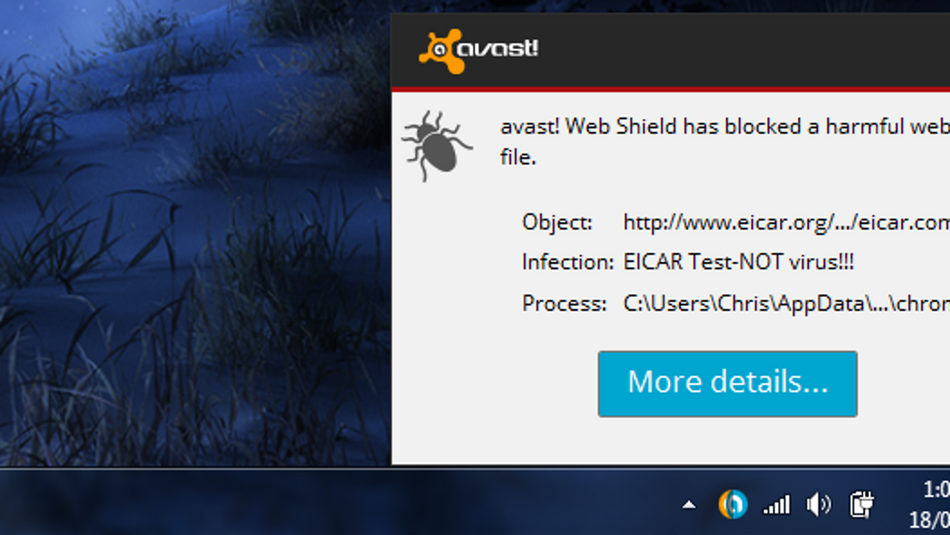
The example of antivirus false positive detection. It was called forcibly in Avast Antivirus
False detections with Heur part in their name are the toughest ones in fixing. Professionals who set up the heuristic engine must check every little thing to understand what is going wrong. Fixing it manually is likely impossible, the only thing you can do is to add this detection to the whitelist and report the false positive to the tech support.
Web browser detects
Web browser-related detections are different. Antivirus tools usually conduct them through two things: checking the status of the page and checking its HTTPS certificate. The status of the page is assigned through the global pools of fraudulent sites. HTTPS is checked by the certificate whitelist. If something goes wrong on a legitimate website – for example, YouTube or Twitter – the problem may be on both sides. You can have some wrong setups in your browser that prevent the correct recognition of the certificate or the website URL. Sometimes, the error may occur after the malware activity – adware and hijackers often change the browser settings. But possibly, the problem is concentrated on the side of the antimalware tool. In that case – if you are sure that the exact site is OK – contact the technical support.
How to understand that you are spectating a false positive?
In case when you see the detection, but are not sure if it is normal, or a false positive one, you need to perform several steps to ensure that what you see.
First advice is to google the name of the detected file (not the exact detection!). It is better to specify the name of a program to this file belongs. You will likely find threads on Reddit, or forum posts on the website of your antivirus software manufacturer.
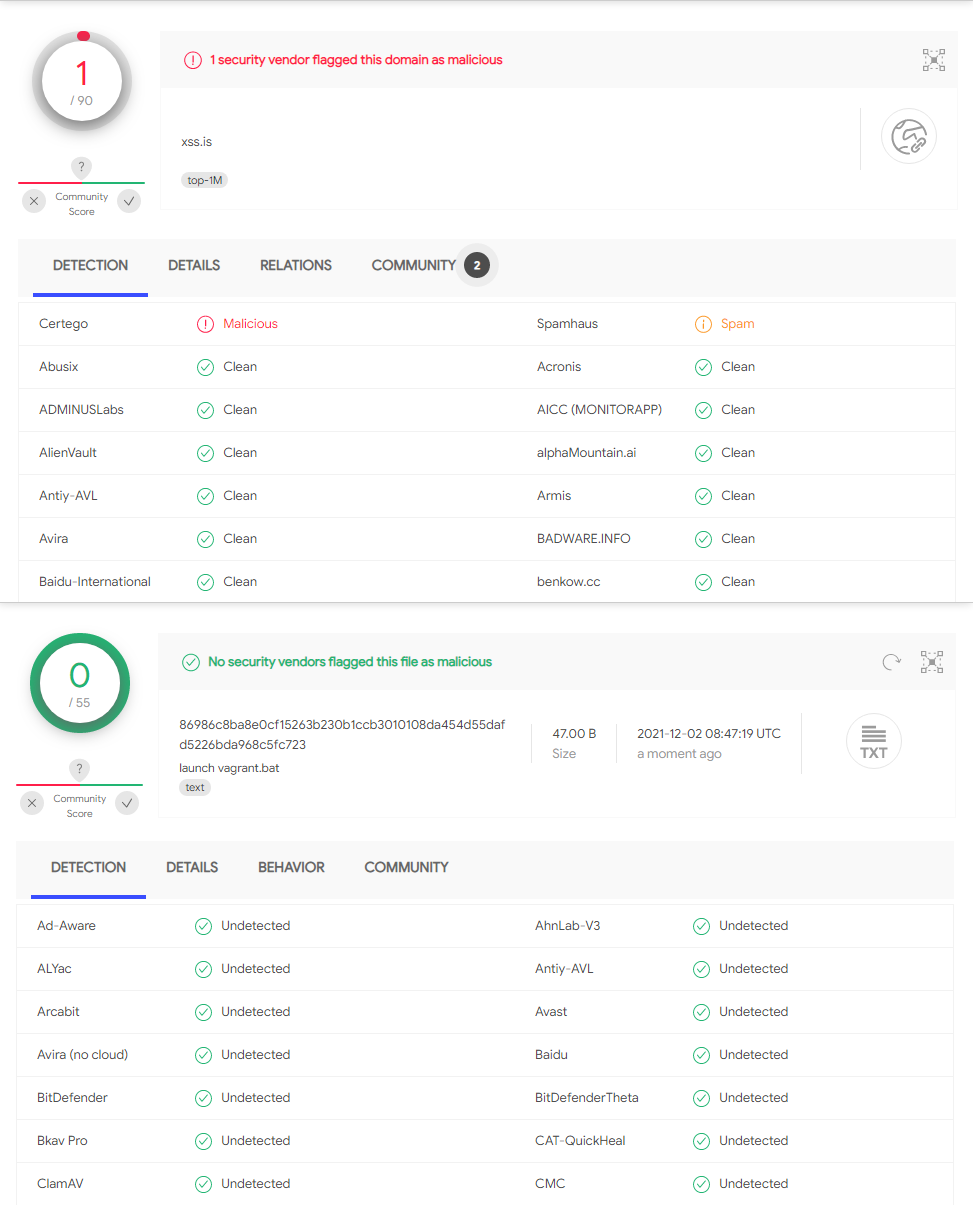
The second thing to do is to check the file through VirusTotal. It is a global database of malware detections, powered by all high-quality antiviruses. Here, you can upload the file and check it with high-level antivirus software. If it was already uploaded by someone else, you will just be redirected to the page of this file. It is a pretty effective way to understand if the file is really benevolent or malicious.
In case you are sure that you see the false detection, it is recommended to report the unpleasant find to the support team of your antivirus. Don’t be scared – this is just a part of their work. Malware analysts will thank you if the thing will really be just a false detection.
How do I fix antivirus false positives?
There are a very small number of things you can do with false detections. Since most of them appear because of internal AV-engine mistakes, you can only report them to the support team. Until the developers release a fix, you will likely need to add the false detect into the whitelist. Another thing to do is check for antivirus databases updates. Possibly, you can find a fresh patch but just did not install it yet. Almost the same things are with web browser detections.
First thing to do with your browser is to update it. Yep, anti-malware software usually interacts well with a wide range of browser versions. But sometimes, especially after large updates, browsers may struggle to give correct information to the security tool. Moreover, keeping it up to date is just a useful habit – it prevents various hacks and other unpleasant things. Another case is to stop the networking protection in your security tool and try to check if the site is accessible. Then, try to disable the security setups of the web browser, enable the networking security in anti-malware software and try again. There were a few cases when they were conflicting and creating situations with false alarms.
Regardless of whether you fixed the problem in the web browser or not, it is recommended to report the case to anti-malware tech support. The problem may exist on the side of the antivirus engine, so reporting any case will surely make the antivirus program better.
Any conclusions?
False positive detections are annoying. They can make some of your apps unusable unless you add the detected thing to the whitelist. And the worst part is that no anti-malware software can guarantee the 100% absence of false-positive alarms. Malware developers do their best to hide the viruses in the user systems, and they don’t hesitate to mimic other app files. Since security tools mostly act as “pursuing”, malware analysts must accept that dirty game.
User Review
( votes)References
- More on how antivirus and anti-malware software works.
- Read about the usage of neural networks in anti-malware software.


