777decoder777 is a brand-new ransomware called MedusaLocker is being proactively dispersed as well as victims have been seen from throughout the world. It is not known at this time, exactly how the cyber-criminals are distributing this infection.
What is MedusaLocker?
MedusaLocker is a piece of malicious software, classified as ransomware
The 777decoder777 ransomware is most commonly spread by means of a payload dropper. It runs the malicious script that eventually installs the file virus. The threat circulates actively on the web, considering the facts about the ransomware mentioned in the VirusTotal database. The 777decoder777 ransomware may also promote its payload files through popular social networks and via file-sharing platforms. Alternatively, some free applications hosted on many popular resources may also be disguised as helpful tools, whereas they instead may lead to the malicious scripts that injected the ransomware. Your personal caution to prevent the 777decoder777 virus attack matters a lot!
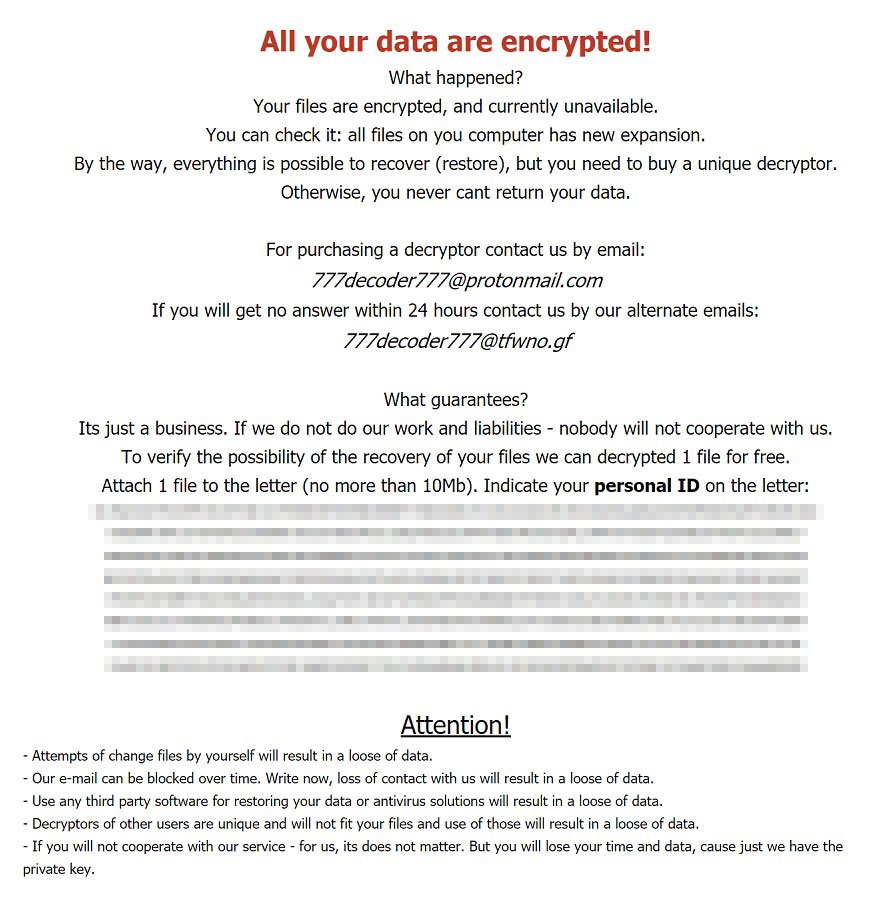
777decoder777 ransomware is a infection that encrypts your data and presents a frustrating ransomware notice. Below is the screenshot depicting the ransomware note:
Quotation of the RECOVER_INSTRUCTIONS.html scary message:
All your data are encrypted! What happened? Your files are encrypted, and currently unavailable. You can check it: all files on you computer has new expansion. By the way, everything is possible to recover (restore), but you need to buy a unique decryptor. Otherwise, you never cant return your data. For purchasing a decryptor contact us by email: 777decoder777@protonmail.com If you will get no answer within 24 hours contact us by our alternate emails: 777decoder777@tfwno.gf What guarantees? Its just a business. If we do not do our work and liabilities - nobody will not cooperate with us. To verify the possibility of the recovery of your files we can decrypted 1 file for free. Attach 1 file to the letter (no more than 10Mb). Indicate your personal ID on the letter: [XXXXX] Attention! - Attempts of change files by yourself will result in a loose of data. - Our e-mail can be blocked over time. Write now, loss of contact with us will result in a loose of data. - Use any third party software for restoring your data or antivirus solutions will result in a loose of data. - Decryptors of other users are unique and will not fit your files and use of those will result in a loose of data. - If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key.
777decoder777 – How did I get MedusaLocker?
When the MedusaLocker ransomware is mounted to your PC, it will do different startup routines to prepare your computer for encryption
Step 1
MedusaLocker will create the Registry value EnableLinkedConnections under the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System registry key and also established it to 1. This is done to make certain mapped drives come also in a UAC launched process.
Step 2
Next, ransomware will restart the LanmanWorkstation service in order to make certain that Windows networking is running which mapped network drives come.
Step 3
MedusaLocker will seek as well as end the complying with procedures in order to shut down security programs and to make certain all data files are closed and easily accessible for encrypting:
wrapper, DefWatch, ccEvtMgr, ccSetMgr, SavRoam, sqlservr, sqlagent, sqladhlp, Culserver, RTVscan, sqlbrowser, SQLADHLP, QBIDPService, Intuit.QuickBooks.FCS, QBCFMonitorService, sqlwriter, msmdsrv, tomcat6, zhudongfangyu, SQLADHLP, vmware-usbarbitator64, vmware-converter, dbsrv12, dbeng8, wxServer.exe, wxServerView, sqlservr.exe, sqlmangr.exe, RAgui.exe, supervise.exe, Culture.exe, RTVscan.exe, Defwatch.exe, sqlbrowser.exe, winword.exe, QBW32.exe, QBDBMgr.exe, qbupdate.exe, QBCFMonitorService.exe, axlbridge.exe, QBIDPService.exe, httpd.exe, fdlauncher.exe, MsDtSrvr.exe, tomcat6.exe, java.exe, 360se.exe, 360doctor.exe, wdswfsafe.exe, fdlauncher.exe, fdhost.exe, GDscan.exe, ZhuDongFangYu.exe
Step 4
Finally, it gets rid of the Shadow Volume Copies to ensure that they can not be made use of to bring back files, gets rid of back-ups made with Windows back-up, and also disables the Windows automatic start-up repair work making use of the complying with commands:
vssadmin.exe Delete Shadows /All /Quiet
wmic.exe SHADOWCOPY /nointeractive
bcdedit.exe /set {default} recoveryenabled No
bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
wbadmin DELETE SYSTEMSTATEBACKUP
wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest
Step 5
MedusaLocker will currently begin to scan the computer’s drives for files to encrypt. When encrypting documents, it will miss all data that have the extensions.exe,. dll,. sys,. ini,. lnk,. rdp,. encrypted (or other expansion utilized for encrypted files) in addition to data in the adhering to folders.
USERPROFILE PROGRAMFILES(x86) ProgramData \AppData WINDIR \Application Data \Program Files \Users\All Users \Windows \intel \nvidia
When encrypting documents, it will use AES file encryption to encrypt the data and afterwards the AES key will be encrypted by a RSA-2048 public key consisted of in the virus executable.
For every data that is encrypted, it will add among the adhering to extensions depending on the version of the ransomware.
- .encrypted
- .bomber
- .boroff
- .breakingbad
- .locker16
- .newlock
- .nlocker
- .skynet
When done, the ransomware will rest for 60 secs and afterwards scan the drives again for new files to encrypt.
When mounted, this ransomware will likewise duplicate itself to %UserProfile%\AppData\Roaming\svchostt.exe and also create a scheduled job that releases the program every 30 mins in order to continue to be resident.
Remove MedusaLocker Virus
Reasons why I would recommend GridinSoft1
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes2.
Download GridinSoft Anti-Malware.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the install-antimalware-fix.exe file to install GridinSoft Anti-Malware on your PC.
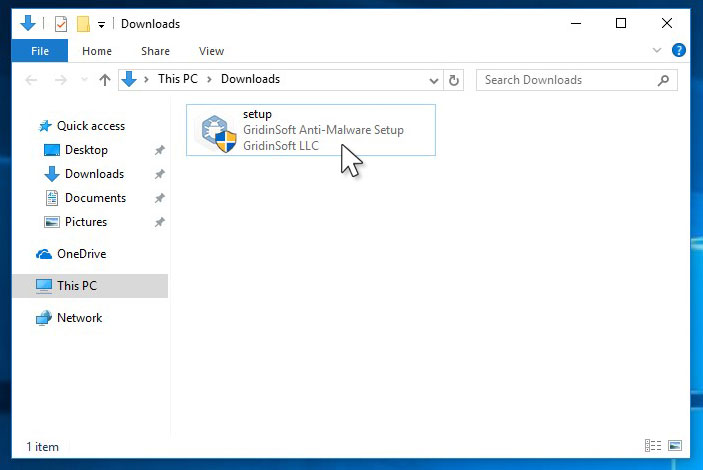
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
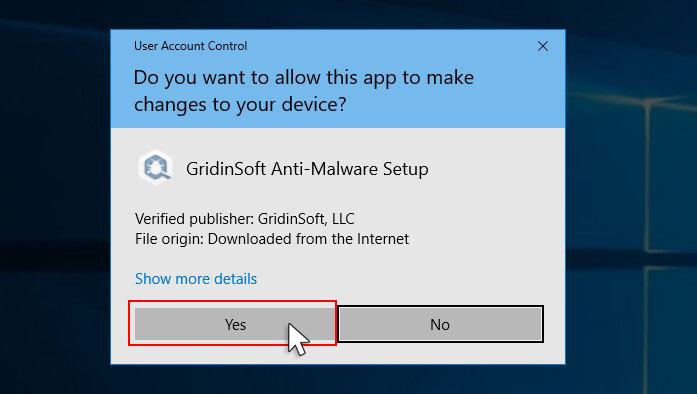
Press “Install” button.
Once installed, Anti-Malware will automatically run.

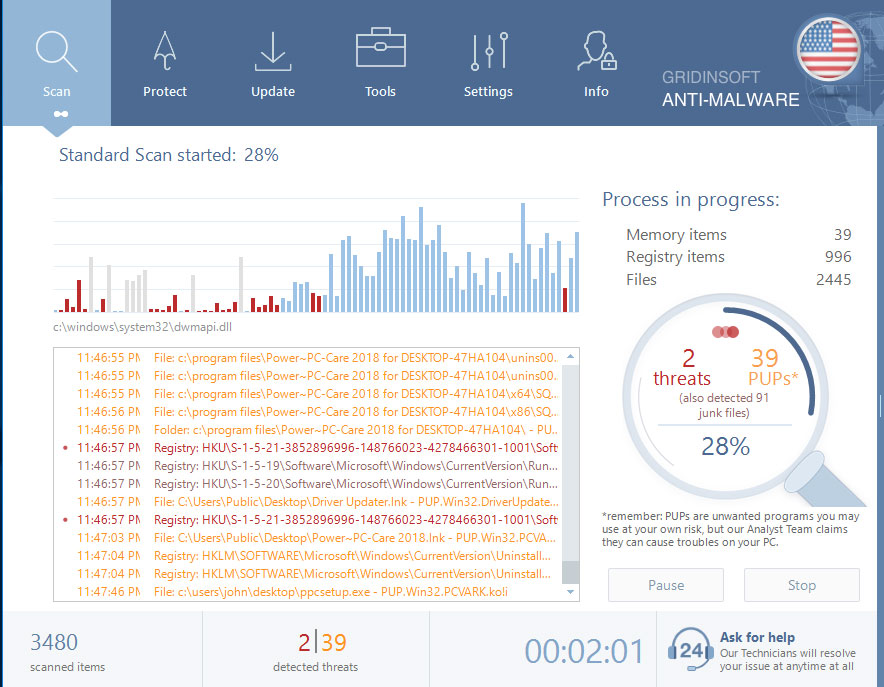
Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your computer for 77decoder777 infections and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
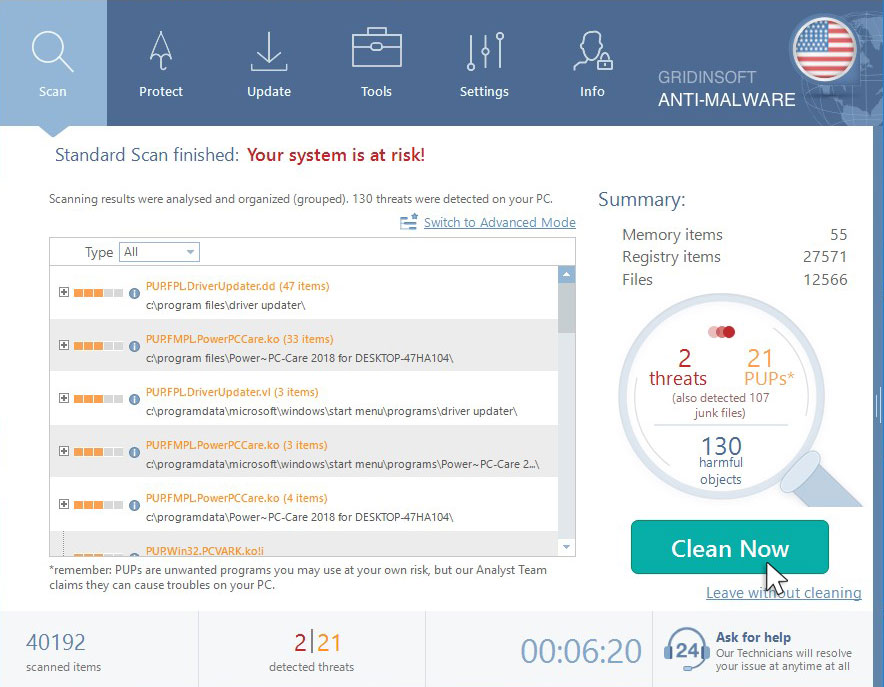
Click on “Clean Now”.
When the scan has completed, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
How to decrypt MedusaLocker files?
It is not understood at this time just how much the aggressors are requiring for a decryptor or if they actually supply one after paying.
This ransomware is still being looked into, so it is not known if it can be decrypted currently.
In the meantime, if you have any kind of inquiries or require help with this ransomware, you can leave a comment right here
What the next?
If the guide doesn’t help you to remove 777decoder777 infection, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments for getting help.
User Review
( votes)References
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison