WISE REMOTE Stealer has emerged as a malicious tool that combines the functionalities of an infostealer, remote access Trojan (RAT), DDoS bot, and ransomware. This sophisticated threat, discovered by experts at CYFIRMA1, operates under the guise of a Malware-as-a-Service (MaaS), offering its capabilities to cybercriminals seeking to compromise systems, steal data, and engage in illicit activities.
Since its initial appearance in the darknet, WISE REMOTE Stealer has gained notoriety, actively advertised and promoted on hacker forums, particularly on platforms like HF and cracked.io. The continuous refinement of this malware-as-a-service2 offering by its creators has led to widespread use, as evident from the vast user base and the alarming number of victims who have fallen prey to its insidious operations.
Proof of concept demonstrations conducted by the developers on popular communication platforms like Discord and Telegram have showcased the efficiency and effectiveness of WISE REMOTE Stealer. These demos have successfully targeted and compromised over 1,000 unsuspecting victims, demonstrating the real-world impact of this multifunctional malware.
WISE REMOTE: Technical Details
| Name | WISE REMOTE |
| Damage | Can gather system information, provide remote access, transform computers into DDoS bots, steal data from web browsers and cryptocurrency wallets, and even engage in ransomware activities. |
| Fix Tool | See If Your System Has Been Affected by this stealer |
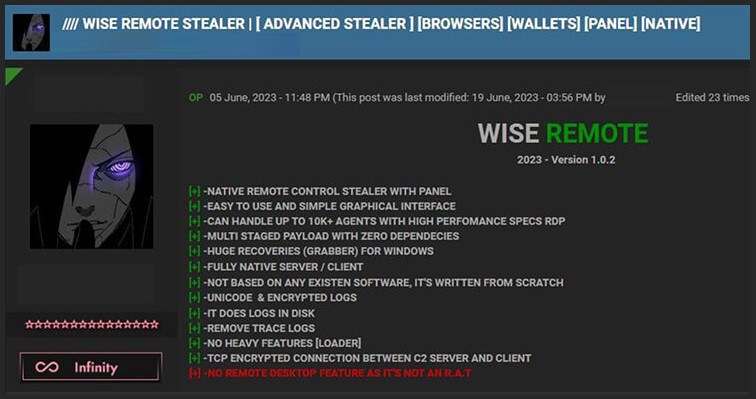
Wise Remote Stealer on hackers forum
Programming Languages and Targeted Systems
WISE REMOTE Stealer is predominantly developed using the Go programming language. However, the creators also incorporate elements of C++, C#, and Python in their codebase. It primarily targets Windows systems, specifically versions 8, 10, and 11, aiming to exploit vulnerabilities and gain unauthorized access to the targeted machines.
Evasion Techniques and Secure Communication
The developers of WISE REMOTE Stealer employ various evasion techniques to bypass antivirus software, ensuring that their malware can operate undetected. By utilizing encryption protocols, the malware establishes secure communication channels with its command-and-control (C2) server, which is located in Switzerland. This encryption ensures the confidentiality of communications and adds an additional layer of complexity for security analysts attempting to track and disrupt the malware’s operations.
A Comprehensive Range of Malicious Functionalities
WISE REMOTE Stealer boasts an extensive array of capabilities designed to facilitate cybercriminal activities:
- System Information Gathering: It collects detailed information about the compromised system, enabling cybercriminals to assess the value and potential for further exploitation.
- Remote Access Trojan (RAT) Functionality: It creates a backdoor, allowing attackers to gain remote control over the infected system and execute commands.
- DDoS Botnet Recruitment: This Stealer can transform infected machines into part of a larger botnet, orchestrating distributed denial-of-service (DDoS) attacks to disrupt targeted networks.
- Data Theft: The malware extracts sensitive information from web browsers, including saved passwords, cookies, banking data, bookmarks, browsing history, and installed extensions. It also targets cryptocurrency wallets, stealing digital assets.
- Ransomware Capabilities: WISE REMOTE Stealer can encrypt files on the infected system, demanding a ransom for their release.
Customization and Stealth Techniques
WISE REMOTE Stealer offers subscribers a builder tool that allows them to customize the appearance and behavior of the malware. This customization enables cybercriminals to tailor the malware to specific distribution methods and infection chains, increasing the chances of successful compromise. Additionally, the resulting malware payloads are typically compact, with sizes not exceeding 100 kilobytes, facilitating rapid distribution and reducing the risk of detection.
How to remove the WISE REMOTE?
WISE REMOTE malware is incredibly difficult to delete manually. It places its files in a variety of locations throughout the disk, and can restore itself from one of the parts. Furthermore, a range of changes in the registry, networking configurations and also Group Policies are really hard to discover and revert to the initial. It is better to make use of a special tool – exactly, an anti-malware app. GridinSoft Anti-Malware will fit the best for malware removal objectives.
Why GridinSoft Anti-Malware? It is pretty lightweight and has its databases updated just about every hour. Moreover, it does not have such bugs and vulnerabilities as Microsoft Defender does. The combination of these facts makes GridinSoft Anti-Malware suitable for eliminating malware of any type.
Remove the WISE REMOTE with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of WISE REMOTE the default option is “Delete”. Press “Apply” to finish the malware removal.



Frequently Asked Questions (FAQ)
It is a multifunctional malware that combines the capabilities of an infostealer, remote access Trojan (RAT), DDoS bot, and ransomware.
It is typically distributed through malicious websites, phishing emails, or compromised software downloads.
This stealer primarily targets Windows systems, including versions 8, 10, and 11.
It can extract various types of data from compromised systems, including saved passwords, cookies, banking information, browsing history, bookmarks, and cryptocurrency wallet details.
It employs evasion techniques to bypass antivirus detection. However, security solutions are constantly updated to detect and mitigate its presence.
It can gather system information, create a backdoor for remote access, recruit infected machines into a DDoS botnet, steal data, and even deploy ransomware to encrypt files.
To protect against stealers, it is essential to maintain up-to-date antivirus software, exercise caution when opening email attachments or visiting unfamiliar websites, and regularly update your operating system and applications.
Removing this stealer can be challenging due to its stealthy nature. It is recommended to seek assistance from cybersecurity professionals who can provide guidance and employ specialized tools for malware removal.
No, this stealer is a malicious tool developed for illegal activities. Its usage for any legitimate purposes is strictly prohibited.
Organizations can enhance their defenses against WISE REMOTE Stealer by implementing robust cybersecurity measures such as network monitoring, user education and awareness programs, regular system patching, and strong access controls.
Conclusion: A Multi-Faceted and Alarming Threat
WISE REMOTE Stealer presents a significant and growing threat in the realm of cybercrime. Its diverse functionalities, advanced evasion techniques, and widespread usage are evidence of its potency. The multifaceted nature of stealer demands increased awareness, robust security measures, and proactive defense strategies to mitigate the risks posed by this malicious tool.
How to Remove WISE REMOTE Malware
Name: WISE REMOTE
Description: WISE REMOTE Stealer can gather system information, provide remote access, steal data (including passwords and cryptocurrency information), transform computers into DDoS bots, and engage in ransomware activities.
Operating System: Windows
Application Category: Malware

