Wacatac is a detection name used by Microsoft Defender to mark a range of threats that possess spyware-like capabilities conjoined with malware delivery functionality. Wacatac malware is exceptionally dangerous and should be treated with maximum caution.
What is Wacatac?
It’s a detection name of an entire selection of malware that operates as spyware. Another distinctive feature of this threat is the ability to deliver other malware, i.e. act as a dropper. A lot of modern malware contains both of these functions, that’s why seeing Wacatac detection became quite common.
There is a possibility that the threat detected is more of a dropper malware rather than a stealer or spyware. Since droppers collect certain info about the system as a fingerprint, Microsoft Defender may understand such behavior as data gathering. Even though this data amount is not nearly as all-encompassing and exposing, the reason for the detection is quite clear.
Threat Summary
| Name | Trojan:Win32/Wacatac |
| Behavior | Data stealing, Malware delivery |
| Malware class | Spyware, Infostealer, Banking Trojan, Dropper |
| Spreading Ways | Malicious email attachments, cracked programs from third-party sites |
| Variations | Trojan:Win32/Wacatac.B!ml (“B Ml” variant), Trojan:Win32/Wacatac.H!ml (“H ml” variant”), Trojan:Script/Wacatac.H!ml (“Script” variant) |
How Dangerous is Trojan:Win32/Wacatac?
Eventually, two main vectors of danger come from Wacatac malware. Spyware functions make it worrying for user privacy – it extracts passwords, and cookie files, and even grabs session tokens. Dropper capabilities make things even worse: by bringing other malware, hackers who operate it increase their profits.
Some of the malware samples detected as Wacatac may be aimed at specific topics, like cryptocurrency wallets or online banking accounts. Such threats trade broad-range stealing for inflicting severe financial damage. With that being said, nothing stops cybercriminals from starting with a “regular” spyware, and bringing banking trojans, cryptostealers or ransomware as a second-stage payload.
Examples of Malware Detected as Trojan Wacatac
Wacatac is not a specific malware family but a group of malware that falls under the same category due to its functionality. There are a couple of families that Microsoft Defender detects with this name the most.
| Amadey Dropper | An infamous malware, among the most active at the moment (late 2023). Is used to deliver Vidar, RedLine stealers and STOP/Djvu ransomware. May sporadically deliver cryptominers. Gathers basic data about the system. |
| Gozi Stealer | Originally a stealer, Gozi received malware delivery functionality as a plug-in. Though, it is mainly used as a spyware. |
| Emotet (Epoch 4 variants) | One of the most known malware samples over the last 6 years. Conjoins the functionality of dropper and stealer, being equally used for both purposes. Defender usually marks this malware family as Sabsik, though changes in Epoch 4 version probably altered its signature, making it more similar to Wacatac. |
| QakBot | Old-timer of malware scene, mostly used in targeted attacks as a tool for initial reconnaissance and lateral movement. Its network was recently shut down, so a new spreading wave may start quite soon. |
| FormBook | Also known as xLoader. Being active since 2016, it conjoins the functionality of a stealer and a dropper. Still, it is known far less than Emotet. |
How to Remove Wacatac Trojan?
Upon execution, this trojan creates quite strong anchors that make its manual removal nearly impossible. This, actually, is normal behavior for malware that relies on stealthy presence in the system. For that reason, a removal with an anti-malware tool is a recommended option.
GridinSoft Anti-Malware is a perfect solution for this case. Constant database updates and well-done heuristic mechanism make it proficient at detecting even the most modern malware samples.
Remove Wacatac Trojan with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common Trojans as shown from our tests with the software, and we assure you that it can remove Wacatac Trojan as well as other malware hiding on your computer.
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file.
3.Follow the installation setup wizard's instructions diligently.
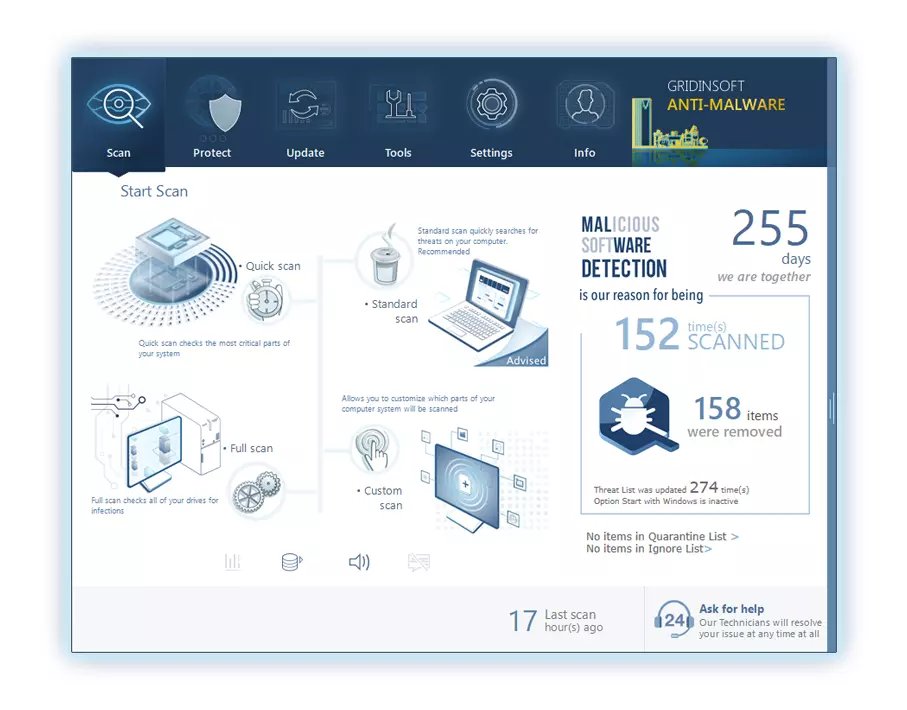
4. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
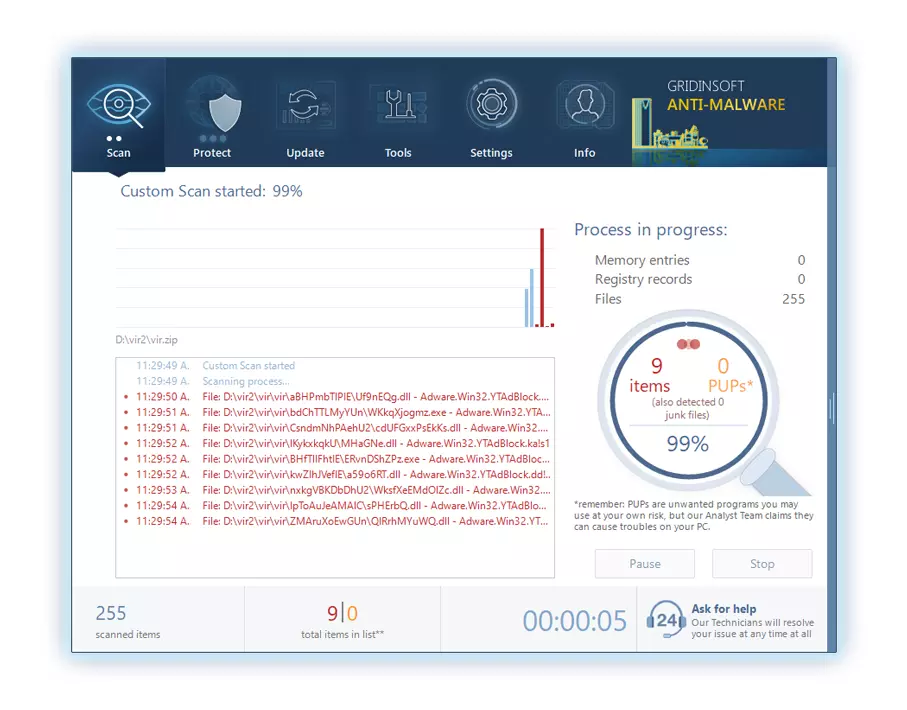
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
5. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
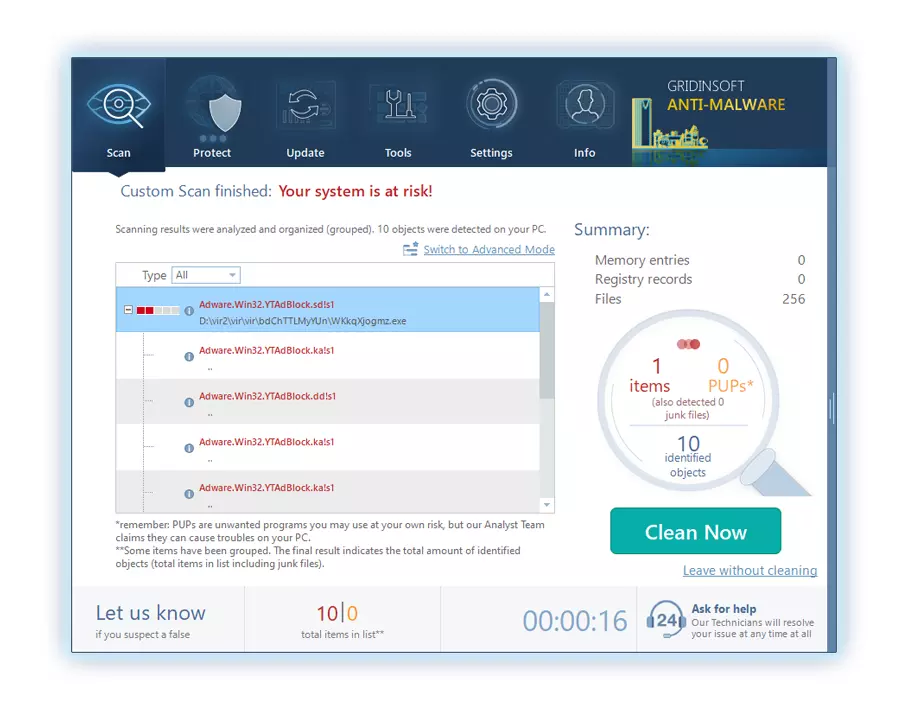
6. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
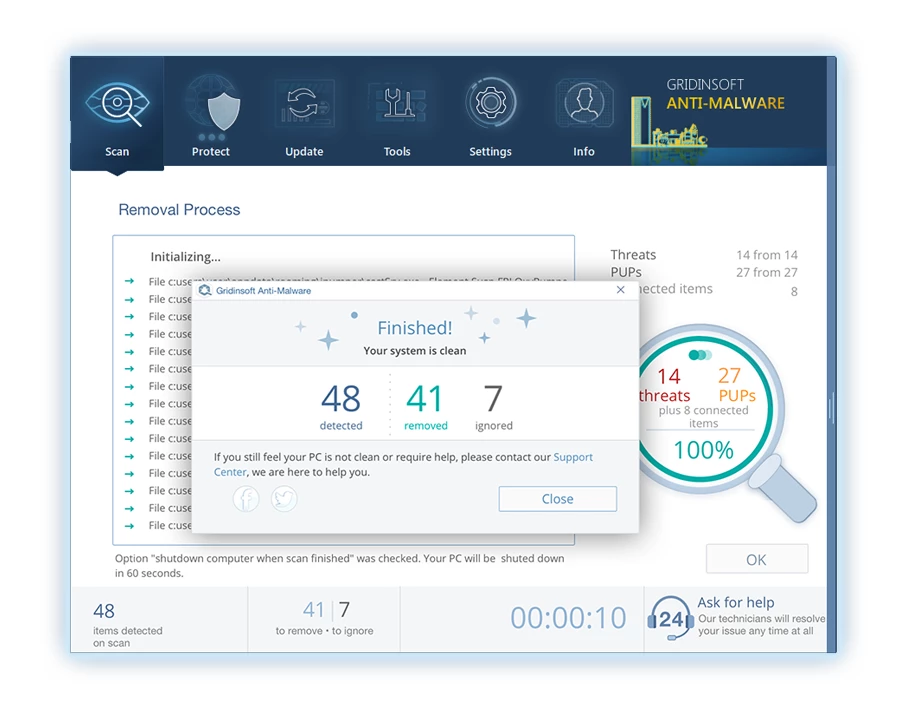
8. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.
Frequently Asked Questions
Wacatac, also known as Trojan:Win32/Wacatac, is a type of malware that infects computers and carries out malicious actions without the user’s knowledge.
It’s typically spread through spam email campaigns and fake software ‘cracks’. Users may unknowingly download or open infected email attachments or install cracked software, allowing the malware to infiltrate their systems.
It can cause extensive damage to the infected computer and the user’s digital life. It collects personal information such as logins, passwords, and banking details, leading to potential privacy breaches and significant financial loss.
Yes, it can result in significant financial loss. Cyber criminals behind the malware aim to generate revenue by exploiting hijacked accounts for online purchases, direct money transfers, and even attempting to borrow money from the victim’s contacts.
Yes, the presence of Wacatac and related malware can lead to permanent data loss. In some cases, trojan-type viruses initiate “chain infections,” injecting additional malware such as ransomware into the infected computer, making file restoration without involvement from the ransomware developers nearly impossible.
It can also result in hardware damage due to the excessive strain placed on computer components by cryptominers. Additionally, it may introduce browser hijackers and adware, causing unwanted redirects and displaying intrusive advertisements.
Yes, Wacatac and similar trojans can have the functionality of remote access tools (RATs), enabling cyber criminals to remotely control hijacked machines and carry out unauthorized activities.
To protect your computer it is crucial to practice safe browsing habits. Avoid opening suspicious email attachments or downloading software from untrusted sources. Keep your operating system and antivirus software up to date, and regularly scan your system for malware. Additionally, use strong and unique passwords for your accounts and consider using two-factor authentication for added security.
I need your help to share this article.
It is your turn to help other people. I have written this article to help people like you. You can use the buttons below to share this on your favorite social media Facebook, Twitter, or Reddit.
Brendan SmithUser Review
( votes) ![]() German
German ![]() Japanese
Japanese ![]() Spanish
Spanish ![]() Portuguese (Brazil)
Portuguese (Brazil) ![]() French
French ![]() Turkish
Turkish ![]() Chinese (Traditional)
Chinese (Traditional) ![]() Korean
Korean ![]() Indonesian
Indonesian ![]() Hindi
Hindi ![]() Italian
Italian
