Analysts at Wordfence have discovered a dangerous, even critical vulnerability in the wpDiscuz comment plugin for WordPress, which is installed on 70,000 sites.
The problem can be exploited after the files are uploaded to the servers hosting the vulnerable site. As a result, an attacker is able to execute arbitrary code.The wpDiscuz plugin for WordPress is an alternative to well-known solutions like Disqus and Jetpack Comments, as it provides the site with an Ajax-based commenting system that stores posts in a local database.
Wordfence experts say that they discovered the problem back on June 19, 2020, and rushed to notify the wpDiscuz developers. The bug is currently fixed in version 7.0.5, which was released on July 23, 2002 (an attempt to fix the problem in version 7.0.4 was unsuccessful).
Experts emphasize that the problem has a critical status and scored 10 points out of 10 possible on the CVSS vulnerability assessment scale.
This vulnerability was introduced in the plugin’s latest major version update. This is considered a critical security issue that could lead to remote code execution on a vulnerable site’s server”, — write Wordfence specialists.
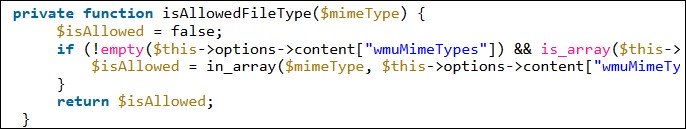
The root of the bug lies in the fact that although the plugin was designed to allow users to attach only image files to messages, vulnerable versions of wpDiscuz could not check types of files, and as a result, users were able to upload, for example, PHP files to the server.
Most files begin with several so-called “Magic Bytes” which are a specific signature that can be used to determine their Mime type. Unfortunately, due to how PHP processes files, it ignores everything in the file before the opening of
After uploading such a file to the host server of the vulnerable site, attackers could launch and execute it, which entailed remote execution of arbitrary code.
Although the patched version of the plugin was released on July 23rd, it has received just over 28,000 downloads in the last week (including both updates and new installations). That is, about 42,000 sites using wpDiscuz are still vulnerable to a dangerous bug and can be attacked.
Experts strongly recommend site owners to update the plugin to the latest version as soon as possible, since attackers often use known issues in WordPress plugins to hijack and even erase other people’s sites.
As a reminder, recently more than 100,000 sites are endangered due to problems in Popup Builder, a popular WordPress plugin.