Seeing the Floxif.H malware detection means that your system is in big danger. This malware can correctly be named ransomware – a virus that encrypts your files and forces you to pay for their decryption. Removing it requires some unusual steps that must be taken immediately.
You may encounter the detection of the Floxif.H virus on your computer. This virus often emerges following certain initial actions on your PC, such as opening suspicious email messages, clicking online advertisements, or installing programs from unreliable sources. Once it appears, it is crucial to take prompt action to address the virus before it initiates its malicious activities. It is strongly advised not to delay in dealing with these harmful occurrences.
What is the Floxif.H virus?
The Floxif.H virus is a type of malware known as ransomware. Its main function is to search for documents on your hard drive, encrypt them, and demand a ransom payment in exchange for the decryption key. In addition to locking your documents, this virus also causes harm to your system. It modifies the networking configurations to prevent you from accessing removal tutorials or downloading anti-malware programs. In some cases, Floxif.H can even block the installation of anti-malware software.
Virus Floxif Summary
In total, Floxif.H malware activities in the infected computer are next:
- SetUnhandledExceptionFilter detected (possible anti-debug);
- Behavioural detection: Executable code extraction – unpacking;
- Sample contains Overlay data;
- Yara rule detections observed from a process memory dump/dropped files/CAPE;
- Creates RWX memory;
- A file with an unusual extension was attempted to be loaded as a DLL.;
- Checks adapter addresses which can be used to detect virtual network interfaces;
- Possible date expiration check, exits too soon after checking local time;
- A process attempted to delay the analysis task.;
- Dynamic (imported) function loading detected;
- Performs HTTP requests potentially not found in PCAP.;
- HTTPS urls from behavior.;
- Enumerates the modules from a process (may be used to locate base addresses in process injection);
- Enumerates running processes;
- Expresses interest in specific running processes;
- Repeatedly searches for a not-found process, may want to run with startbrowser=1 option;
- Reads data out of its own binary image;
- CAPE extracted potentially suspicious content;
- Drops a binary and executes it;
- Unconventionial language used in binary resources: Spanish (Guatemala);
- The binary contains an unknown PE section name indicative of packing;
- Authenticode signature is invalid;
- Detects the presence of Wine emulator via function name;
- Detects Sandboxie through the presence of a library;
- Detects SunBelt Sandbox through the presence of a library;
- Attempts to remove evidence of file being downloaded from the Internet;
- Network activity contains more than one unique useragent.;
- Fake User-Agent detected;
- Installs itself for autorun at Windows startup;
- Creates a hidden or system file;
- CAPE detected the FloodFix malware family;
- Attempts to modify proxy settings;
- Operates on local firewall’s policies and settings;
- Creates a copy of itself;
- Ciphering the documents kept on the target’s drives — so the victim cannot use these files;
- Blocking the launching of .exe files of security tools
- Blocking the launching of installation files of anti-virus programs
Ransomware has posed a significant threat for the past four years. It is difficult to imagine a more detrimental virus for both individual users and businesses. The encryption algorithms employed by Floxif.H (typically RHA-1028 or AES-256) are virtually unhackable, with only a few exceptions. Attempting to break the encryption through brute force would require more time than the current and foreseeable existence of our galaxy. However, the virus does not carry out its malicious actions instantaneously; it may take several hours to encrypt all of your documents. Therefore, detecting the presence of Floxif.H serves as a clear indication that you should initiate the cleaning process.
How did I acquire Floxif.H?
The methods used for the spread of Floxif.H are consistent with other examples of ransomware. These include the utilization of one-day landing sites, where victims are enticed to download free applications, as well as bait emails and hack tools. Bait emails represent a relatively modern tactic in malware distribution. You may receive an email that mimics official notifications regarding shipping or changes in bank service conditions. Within the email, a corrupted MS Office file or a link directs you to an exploit landing site.
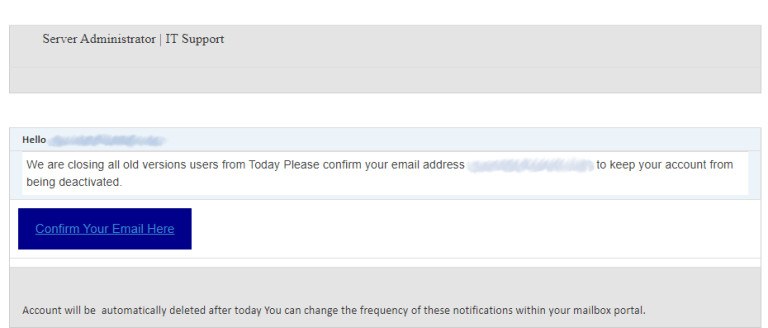
Malicious email message. This one tricks you into opening a phishing website.
Preventing it looks fairly uncomplicated, however, still needs tons of attention. Malware can hide in various places, and it is far better to prevent it even before it invades your system than to rely on an anti-malware program. Simple cybersecurity awareness is just an essential thing in the modern world, even if your relationship with a computer stays on YouTube videos. That may keep you a lot of money and time which you would spend while searching for a fixing guide.
Floxif Technical Details
File Info:
name: 87C10BC4827C8E0F1C64.mlwpath: /opt/CAPEv2/storage/binaries/519ea65476b036fcbfe5ed1a1564d488a83b1ee242601cff48466a19503825e6crc32: 884E8EF2md5: 87c10bc4827c8e0f1c64cf1ec0e6b610sha1: c0c8221e2f4595dacae66002744afd9d7390750csha256: 519ea65476b036fcbfe5ed1a1564d488a83b1ee242601cff48466a19503825e6sha512: 1de7ab3703e711493a727843f8d99e663ff8ef1c3bbbab327bfb6f0a28236493a49b34a54d66fcddee5427a22cf54b938e09601d3ef2d23e3b90ee1632afdcc0ssdeep: 6144:0pGJyHAOfyWgBF4kYjSjBV+UdvrEFp7hKz+gU:0pfkb4jj+BjvrEH7e+Rtype: PE32 executable (GUI) Intel 80386, for MS Windowstlsh: T1C844AFC172F29BF8D172053D382B959108B6FD7C092949BB274462DE0EFC1A15A91BFBsha3_384: d702ec597ef065e1881bd4821c5f9325918ca62831374e36b09ce3945062d32ecd881640af9b525242dda2171272889fep_bytes: e953350000e98efeffffff2534f14000timestamp: 2003-05-09 11:40:21Version Info:
FileVersion: 6.3.6.8LegalCopyright: Copyright (C) 2017, svezabpuekbProductVersion: 6.3.6.8Translation: 0x0809 0x04b0
Floxif.H also known as:
| Bkav | W32.FloxitNV.PE |
| MicroWorld-eScan | Win32.Floxif.A |
| FireEye | Generic.mg.87c10bc4827c8e0f |
| CAT-QuickHeal | W32.Pioneer.CZ1 |
| McAfee | Dropper-FIY!87C10BC4827C |
| Cylance | Unsafe |
| VIPRE | Win32.Floxif.A |
| Sangfor | Trojan.Win32.Save.a |
| K7AntiVirus | Virus ( 00521e9a1 ) |
| K7GW | Virus ( 00521e9a1 ) |
| Cybereason | malicious.4827c8 |
| Baidu | Win32.Virus.Floxif.a |
| VirIT | Win32.FloodFix.A |
| Cyren | W32/Floxif.B |
| Symantec | W32.Fixflo.B!inf |
| Elastic | malicious (high confidence) |
| ESET-NOD32 | Win32/Floxif.H |
| APEX | Malicious |
| ClamAV | Win.Virus.Pioneer-9111434-0 |
| Kaspersky | Virus.Win32.Pioneer.cz |
| BitDefender | Win32.Floxif.A |
| NANO-Antivirus | Virus.Win32.Pioneer.bvrqhu |
| SUPERAntiSpyware | Trojan.Agent/Gen-Kryptik |
| Avast | Win32:FloxLib-A [Trj] |
| Tencent | Virus.Win32.Pionner.tt |
| Ad-Aware | Win32.Floxif.A |
| Comodo | Virus.Win32.Floxif.A@7h5wha |
| DrWeb | Trojan.Encoder.24384 |
| Zillya | Virus.Floxif.Win32.1 |
| TrendMicro | PE_FLOXIF.D |
| McAfee-GW-Edition | BehavesLike.Win32.Corrupt.dc |
| Trapmine | malicious.high.ml.score |
| SentinelOne | Static AI – Malicious PE |
| Jiangmin | Win32/Pioneer.l |
| Avira | W32/Floxif.hdc |
| Antiy-AVL | Trojan/Generic.ASVirus.178 |
| Microsoft | Virus:Win32/Floxif.H |
| ViRobot | Trojan.Win32.GandCrab.280585.A |
| ZoneAlarm | Virus.Win32.Pioneer.cz |
| GData | Win32.Floxif.A |
| Cynet | Malicious (score: 100) |
| AhnLab-V3 | Trojan/Win.MalPe.X2055 |
| Acronis | suspicious |
| BitDefenderTheta | AI:FileInfector.207622A70E |
| ALYac | Win32.Floxif.A |
| MAX | malware (ai score=86) |
| VBA32 | Virus.Win32.Floxif.h |
| Malwarebytes | Gandcrab.Ransom.Encrypt.DDS |
| TrendMicro-HouseCall | PE_FLOXIF.D |
| Rising | Virus.Floxif!1.9BE6 (CLASSIC) |
| Yandex | Trojan.GenAsa!UyadntvZSLE |
| Ikarus | Trojan.Win32.CryptInject |
| MaxSecure | Ransomeware.CRAB.gen |
| Fortinet | W32/Floxif.E |
| AVG | Win32:FloxLib-A [Trj] |
| Panda | W32/Floxif.A |
| CrowdStrike | win/malicious_confidence_100% (W) |
How to remove Floxif.H?
Floxif.H malware is extremely hard to delete by hand. It puts its data in numerous locations throughout the disk and can recover itself from one of the elements. Furthermore, several alterations in the Windows registry, networking setups, and Group Policies are hard to find and change to the original. It is much better to use a special program – exactly, an anti-malware tool. GridinSoft Anti-Malware will fit the most ideal for virus elimination objectives.
Why GridinSoft Anti-Malware? It is lightweight and has its detection databases updated almost every hour. In addition, it does not have such problems and weaknesses as Microsoft Defender does. The combination of these details makes GridinSoft Anti-Malware perfect for clearing away malware.
Remove the viruses with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored and the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of Floxif.H, the default option is “Delete”. Press “Apply” to finish the malware removal.




