What is Trojan:Win32/Sopinar.F!bit infection?
In this article you will certainly locate concerning the meaning of Trojan:Win32/Sopinar.F!bit and also its unfavorable impact on your computer system. Such ransomware are a form of malware that is specified by online frauds to demand paying the ransom money by a sufferer.
Most of the cases, Trojan:Win32/Sopinar.F!bit infection will certainly advise its victims to initiate funds transfer for the purpose of counteracting the changes that the Trojan infection has introduced to the sufferer’s device.
Trojan:Win32/Sopinar.F!bit Summary
These adjustments can be as follows:
- Executable code extraction;
- Creates RWX memory;
- The binary likely contains encrypted or compressed data.;
- Collects information about installed applications;
- Attempts to identify installed AV products by registry key;
- Collects information to fingerprint the system;
- Ciphering the files located on the target’s hard drive — so the sufferer can no longer utilize the information;
- Preventing regular accessibility to the victim’s workstation;
Related domains:
| z.whorecord.xyz | Ransom_HPLOCKY.SME |
| a.tomx.xyz | Ransom_HPLOCKY.SME |
| 42wykqkigqcy.org | Ransom_HPLOCKY.SME |
| uk2sq86oa4qs.com | Ransom_HPLOCKY.SME |
| cmcqk2o6sa0u.org | Ransom_HPLOCKY.SME |
| ys60qge8i0ac.com | Ransom_HPLOCKY.SME |
| wqo2cqky064m.net | Ransom_HPLOCKY.SME |
| ucewucq4mcy0.org | Ransom_HPLOCKY.SME |
| k28ugakmki4u.org | Ransom_HPLOCKY.SME |
| ysyc68ugiwe4.com | Ransom_HPLOCKY.SME |
| cmwi4egusacu.net | Ransom_HPLOCKY.SME |
| isq8m8aki4mw.net | Ransom_HPLOCKY.SME |
| gis6cakecmgq.org | Ransom_HPLOCKY.SME |
| qoewecawqsq8.org | Ransom_HPLOCKY.SME |
| 8aca8i4aoe4e.com | Ransom_HPLOCKY.SME |
| 2k6s64ukyoe0.net | Ransom_HPLOCKY.SME |
| s6oecaga86gu.net | Ransom_HPLOCKY.SME |
| uouom4y0y4iw.net | Ransom_HPLOCKY.SME |
| 8ag2k2s2se4y.com | Ransom_HPLOCKY.SME |
| 202ga0ekqcac.net | Ransom_HPLOCKY.SME |
| gykmca8e4u82.net | Ransom_HPLOCKY.SME |
| 6se4us2omsa8.com | Ransom_HPLOCKY.SME |
| wys6ga4is60a.net | Ransom_HPLOCKY.SME |
| m8es6w2gu4ew.com | Ransom_HPLOCKY.SME |
| s64a8i8u4mcu.org | Ransom_HPLOCKY.SME |
| 6s68eoyguoeo.net | Ransom_HPLOCKY.SME |
| 8y0aky8ecq82.com | Ransom_HPLOCKY.SME |
| asy0asa4yg6c.net | Ransom_HPLOCKY.SME |
| oy0ewe8m02s2.org | Ransom_HPLOCKY.SME |
| agmwa8m8m4i8.net | Ransom_HPLOCKY.SME |
| gecy8awa0uwa.org | Ransom_HPLOCKY.SME |
| q8i0i0y4iwe0.com | Ransom_HPLOCKY.SME |
| oeke8qsyou4u.com | Ransom_HPLOCKY.SME |
| q8ig24a460i8.com | Ransom_HPLOCKY.SME |
| oeoycege8e06.org | Ransom_HPLOCKY.SME |
| mcac68y428m0.com | Ransom_HPLOCKY.SME |
| 8e4uc64eo6ou.org | Ransom_HPLOCKY.SME |
| iwyoekygega8.org | Ransom_HPLOCKY.SME |
| ga8q0esucqc2.net | Ransom_HPLOCKY.SME |
| qomkmka86s24.org | Ransom_HPLOCKY.SME |
| s6sus6oike4i.net | Ransom_HPLOCKY.SME |
| ugygywewqsew.org | Ransom_HPLOCKY.SME |
| si8aom8u4ise.net | Ransom_HPLOCKY.SME |
| igec2sm8yg2g.com | Ransom_HPLOCKY.SME |
| 02o6wyo20ug6.com | Ransom_HPLOCKY.SME |
| e0ioakqsyc2g.com | Ransom_HPLOCKY.SME |
| oi0qwak2s682.net | Ransom_HPLOCKY.SME |
| e8us6s6424e8.net | Ransom_HPLOCKY.SME |
| oakq0qgmo6gy.org | Ransom_HPLOCKY.SME |
| ysyo6k64q4u0.org | Ransom_HPLOCKY.SME |
| sys2g6s6wmca.com | Ransom_HPLOCKY.SME |
| 2cekew60aoy4.org | Ransom_HPLOCKY.SME |
| s64ugykyoysu.com | Ransom_HPLOCKY.SME |
| y0y8qsyc2c2w.net | Ransom_HPLOCKY.SME |
| 0usm0qo2kegy.org | Ransom_HPLOCKY.SME |
| eseoy4ecyc20.org | Ransom_HPLOCKY.SME |
| ku06gege8uoy.net | Ransom_HPLOCKY.SME |
| 6wa864m020y0.net | Ransom_HPLOCKY.SME |
| 8usa8ukew6oq.org | Ransom_HPLOCKY.SME |
| qgikegi8asu8.com | Ransom_HPLOCKY.SME |
| 0igikygy0yci.net | Ransom_HPLOCKY.SME |
| y4yg6w6ga0yw.org | Ransom_HPLOCKY.SME |
| cqsyg2kuw2we.net | Ransom_HPLOCKY.SME |
| y0ig68ucec20.com | Ransom_HPLOCKY.SME |
| gmse0e4y4qkm.org | Ransom_HPLOCKY.SME |
| qouk6cag6ci8.org | Ransom_HPLOCKY.SME |
| g2g2s6w60icu.com | Ransom_HPLOCKY.SME |
| e4qkawugyke4.net | Ransom_HPLOCKY.SME |
| oiw6cigu0242.net | Ransom_HPLOCKY.SME |
| 28asyoe0aky4.org | Ransom_HPLOCKY.SME |
| 024y8u8qouoy.com | Ransom_HPLOCKY.SME |
| eoekm02w2oik.net | Ransom_HPLOCKY.SME |
| 02oqk68ek24e.com | Ransom_HPLOCKY.SME |
| ycqcmwmwywu8.com | Ransom_HPLOCKY.SME |
| guouci4ygqgu.org | Ransom_HPLOCKY.SME |
| mkmcewyc2g68.net | Ransom_HPLOCKY.SME |
| 4mk6guki0y8m.com | Ransom_HPLOCKY.SME |
| 2cygasm4ykus.net | Ransom_HPLOCKY.SME |
| omsq0uke464m.com | Ransom_HPLOCKY.SME |
| 6oy4u0eomkuo.org | Ransom_HPLOCKY.SME |
| sisaka0qs642.org | Ransom_HPLOCKY.SME |
| qseoisa42g6w.com | Ransom_HPLOCKY.SME |
| 8eoukew6g6cm.org | Ransom_HPLOCKY.SME |
| q4mgm8mwy0mg.net | Ransom_HPLOCKY.SME |
| 8ygqse4y4q4y.net | Ransom_HPLOCKY.SME |
| ysq8y8igyoq0.net | Ransom_HPLOCKY.SME |
| 0ysica8ew6oy.net | Ransom_HPLOCKY.SME |
| 2oeo2ka4yo2s.org | Ransom_HPLOCKY.SME |
| ce02wacmoecy.net | Ransom_HPLOCKY.SME |
| 6s6ku4ygas6g.com | Ransom_HPLOCKY.SME |
| 020i4eoegisq.org | Ransom_HPLOCKY.SME |
| isukigy8ycyk.org | Ransom_HPLOCKY.SME |
| 0i4asikqki8e.com | Ransom_HPLOCKY.SME |
| 6gacm4i068q8.org | Ransom_HPLOCKY.SME |
| k6we0ase0u4y.net | Ransom_HPLOCKY.SME |
| m068y4uca8is.org | Ransom_HPLOCKY.SME |
| oi8a0a86w6sy.com | Ransom_HPLOCKY.SME |
| 6we8aoiwywmo.com | Ransom_HPLOCKY.SME |
| 0u4qgio6oiki.com | Ransom_HPLOCKY.SME |
| 60esqgu0ycqc.com | Ransom_HPLOCKY.SME |
| syou4agyce4q.net | Ransom_HPLOCKY.SME |
| yom4a4io64mo.org | Ransom_HPLOCKY.SME |
| kmkawugm4uc2.org | Ransom_HPLOCKY.SME |
| ycewmk68ys6g.org | Ransom_HPLOCKY.SME |
| w6o2kek2gesi.com | Ransom_HPLOCKY.SME |
| 60msmouwekmk.net | Ransom_HPLOCKY.SME |
| 8u020qgysik6.net | Ransom_HPLOCKY.SME |
| agmouk28esyc.net | Ransom_HPLOCKY.SME |
| oa4mgagq820u.com | Ransom_HPLOCKY.SME |
| e4y0y0mwe8ec.com | Ransom_HPLOCKY.SME |
| cugqkucu42ki.com | Ransom_HPLOCKY.SME |
| is28yomcis24.net | Ransom_HPLOCKY.SME |
| 0ew2kik6gi42.net | Ransom_HPLOCKY.SME |
| isy4aw2wuci0.net | Ransom_HPLOCKY.SME |
| gq0qk6kisqse.org | Ransom_HPLOCKY.SME |
| msiku064qo2s.org | Ransom_HPLOCKY.SME |
| 8ugy4mg6cuky.com | Ransom_HPLOCKY.SME |
| mkysygyce0as.org | Ransom_HPLOCKY.SME |
| 4yce42sa0eg2.net | Ransom_HPLOCKY.SME |
| ism0qc6oqsmc.net | Ransom_HPLOCKY.SME |
| 0y8mcygqgaw2.com | Ransom_HPLOCKY.SME |
| awyoi8es20e0.net | Ransom_HPLOCKY.SME |
| km0ms20a8ici.net | Ransom_HPLOCKY.SME |
| mwuoy86wmk2w.net | Ransom_HPLOCKY.SME |
| oyou8m0qgu8i.org | Ransom_HPLOCKY.SME |
| ukm8y4qwmcus.com | Ransom_HPLOCKY.SME |
| s28e8a4awe8i.com | Ransom_HPLOCKY.SME |
| mkmcusa0q02k.net | Ransom_HPLOCKY.SME |
| kuousq0ik6oq.org | Ransom_HPLOCKY.SME |
| y8i4akiseweo.com | Ransom_HPLOCKY.SME |
| gm0awek2c6si.net | Ransom_HPLOCKY.SME |
| 2kqoqw2cmcuc.com | Ransom_HPLOCKY.SME |
| sigmsmkmguka.org | Ransom_HPLOCKY.SME |
| m4icqs20qwmo.net | Ransom_HPLOCKY.SME |
| kqwy0ucmk20a.com | Ransom_HPLOCKY.SME |
| 2kq8a02si8q4.com | Ransom_HPLOCKY.SME |
| k24qkycu02ga.com | Ransom_HPLOCKY.SME |
| 20qgyouce8m4.com | Ransom_HPLOCKY.SME |
| kice8qgycisu.com | Ransom_HPLOCKY.SME |
| igig2sy86o6o.net | Ransom_HPLOCKY.SME |
| su0m8m0qc602.net | Ransom_HPLOCKY.SME |
| you4iwucao2k.org | Ransom_HPLOCKY.SME |
| cioe4esism0u.org | Ransom_HPLOCKY.SME |
| 2sisy0qw6keg.net | Ransom_HPLOCKY.SME |
| sq4i460uwqgm.net | Ransom_HPLOCKY.SME |
| 2oic68u8eoe0.org | Ransom_HPLOCKY.SME |
| gi4u4e42cu8a.org | Ransom_HPLOCKY.SME |
| akm4ygus6oqo.org | Ransom_HPLOCKY.SME |
| kugqcqgaoe4y.org | Ransom_HPLOCKY.SME |
| 2oega02wasyw.org | Ransom_HPLOCKY.SME |
| 4mcqs64uwy4e.net | Ransom_HPLOCKY.SME |
| 60iwawi06cak.org | Ransom_HPLOCKY.SME |
| 0qcmwmgq0q0m.net | Ransom_HPLOCKY.SME |
| 2ki0uw6wqkm8.net | Ransom_HPLOCKY.SME |
| cmc2siwasmgu.org | Ransom_HPLOCKY.SME |
| 2s606828ecms.com | Ransom_HPLOCKY.SME |
| wicqwqg68uo6.com | Ransom_HPLOCKY.SME |
| i42cygmo6keg.com | Ransom_HPLOCKY.SME |
| 864qky0moy8a.net | Ransom_HPLOCKY.SME |
| ecyg6o6cisuw.net | Ransom_HPLOCKY.SME |
| om4usiky0yk2.org | Ransom_HPLOCKY.SME |
| i028usasmwek.com | Ransom_HPLOCKY.SME |
| 8awmwqk6wy0e.com | Ransom_HPLOCKY.SME |
| asasysy4yoe4.com | Ransom_HPLOCKY.SME |
| kak6wugio60i.net | Ransom_HPLOCKY.SME |
| ekywagugi0a0.com | Ransom_HPLOCKY.SME |
| cioes6oqky4y.net | Ransom_HPLOCKY.SME |
| y4qgiwikyoiw.org | Ransom_HPLOCKY.SME |
| kqku0i8mcyou.org | Ransom_HPLOCKY.SME |
| i8msqoe4a0uk.org | Ransom_HPLOCKY.SME |
| kmcq86kucys2.net | Ransom_HPLOCKY.SME |
| usigacu0moyo.com | Ransom_HPLOCKY.SME |
| s28a0eo2gisy.com | Ransom_HPLOCKY.SME |
| e4ecms2sag6c.org | Ransom_HPLOCKY.SME |
| ki4mgmc2s242.org | Ransom_HPLOCKY.SME |
| 2ci0a4e4m0as.net | Ransom_HPLOCKY.SME |
| sa8q4i4a8602.org | Ransom_HPLOCKY.SME |
| qgioi8y8qky4.com | Ransom_HPLOCKY.SME |
| we42k6wqsq4u.net | Ransom_HPLOCKY.SME |
| i42ciwioecug.org | Ransom_HPLOCKY.SME |
| gi4ukq06sqw6.net | Ransom_HPLOCKY.SME |
| a0i8e4q8a4qo.org | Ransom_HPLOCKY.SME |
| o2o2cqke460e.net | Ransom_HPLOCKY.SME |
| ikqsi0qsecug.com | Ransom_HPLOCKY.SME |
| 0e8ek2oe8ege.com | Ransom_HPLOCKY.SME |
| aoy8ykq0esa0.com | Ransom_HPLOCKY.SME |
| 8q4mguoy8u8u.net | Ransom_HPLOCKY.SME |
| acu0qsag2gak.net | Ransom_HPLOCKY.SME |
| 0us64i4e4m82.net | Ransom_HPLOCKY.SME |
| 28msm4qcqs2o.com | Ransom_HPLOCKY.SME |
| wyw206seku4y.com | Ransom_HPLOCKY.SME |
| eguge0ukeoqg.com | Ransom_HPLOCKY.SME |
| g2sywmk2428i.net | Ransom_HPLOCKY.SME |
| as24y0mkm0qs.net | Ransom_HPLOCKY.SME |
| 86wmg28q8u46.org | Ransom_HPLOCKY.SME |
| y0is24uomsas.org | Ransom_HPLOCKY.SME |
| 8mwa82w2oq8i.org | Ransom_HPLOCKY.SME |
| es6c6c60e0y8.com | Ransom_HPLOCKY.SME |
| 4agy4aoqcuoy.com | Ransom_HPLOCKY.SME |
| asik2wy020qc.org | Ransom_HPLOCKY.SME |
| wyouwqou4aga.net | Ransom_HPLOCKY.SME |
| 64qcugyci8qk.net | Ransom_HPLOCKY.SME |
Trojan:Win32/Sopinar.F!bit
The most normal channels whereby Trojan:Win32/Sopinar.F!bit are infused are:
- By means of phishing e-mails;
- As a repercussion of customer winding up on a source that organizes a malicious software program;
As quickly as the Trojan is effectively infused, it will certainly either cipher the data on the sufferer’s computer or avoid the gadget from functioning in an appropriate way – while also positioning a ransom note that discusses the need for the sufferers to effect the repayment for the objective of decrypting the files or bring back the documents system back to the initial condition. In most circumstances, the ransom money note will certainly turn up when the customer reboots the PC after the system has already been harmed.
Trojan:Win32/Sopinar.F!bit distribution networks.
In various edges of the globe, Trojan:Win32/Sopinar.F!bit grows by jumps and also bounds. Nonetheless, the ransom notes and also methods of obtaining the ransom money amount might differ relying on specific neighborhood (regional) settings. The ransom notes and also techniques of extorting the ransom quantity might vary depending on certain regional (regional) setups.
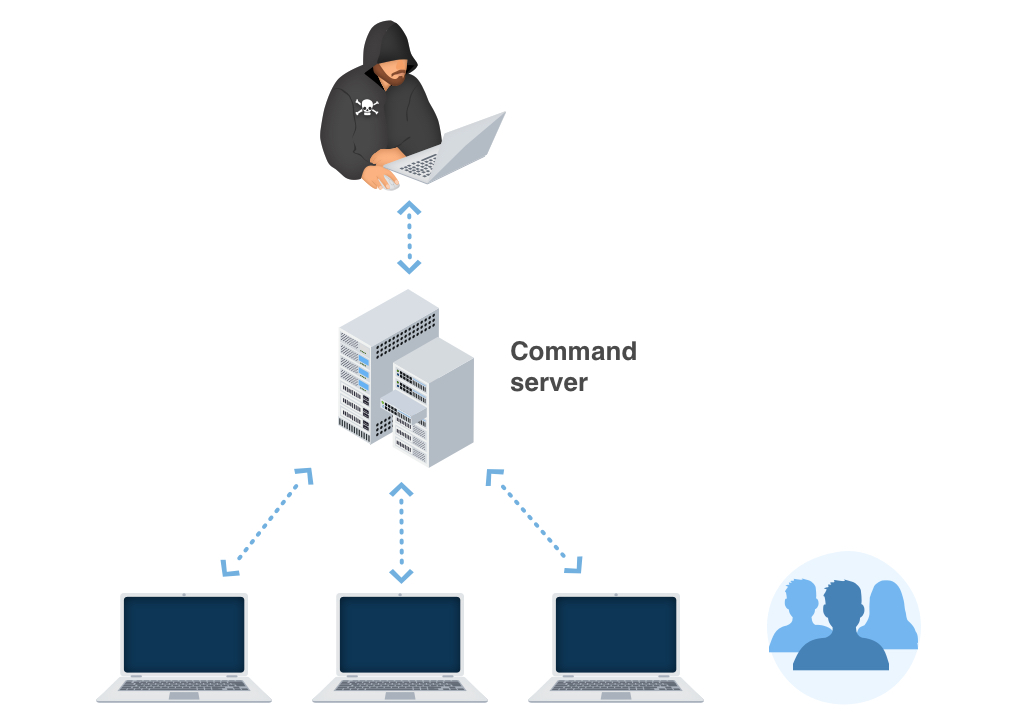
For example:
Faulty notifies concerning unlicensed software application.
In particular areas, the Trojans usually wrongfully report having found some unlicensed applications allowed on the target’s device. The alert after that requires the customer to pay the ransom money.
Faulty declarations concerning illegal content.
In countries where software application piracy is less prominent, this approach is not as reliable for the cyber fraudulences. Alternatively, the Trojan:Win32/Sopinar.F!bit popup alert might falsely assert to be stemming from a police establishment as well as will certainly report having situated kid pornography or other prohibited information on the device.
Trojan:Win32/Sopinar.F!bit popup alert may incorrectly declare to be obtaining from a law enforcement institution and also will certainly report having situated kid porn or other unlawful information on the device. The alert will similarly consist of a requirement for the customer to pay the ransom.
Technical details
File Info:
crc32: 332796E2md5: b5c1c8c31fa729eb6e2ce609d2daf8efname: B5C1C8C31FA729EB6E2CE609D2DAF8EF.mlwsha1: 72856256759ef943e2eafc44f7e5730549fcc2cfsha256: 1c35acdb6b8966569393af40886266b8501497555fe40fccb6ebbf62a711bf47sha512: 7e0b6eadd89b1e4ed60d041de38ccc44d2cbe50010ef0234b40dc322535e7453978b22364d246b70bf7a16bc523df4ce7cce4652d34759bb5809dd3d86b5944essdeep: 3072:YQOR+A7gBRba8X7SBI7STkERoM57GPy+vBB6wNJxt2p0w99oh+P5DSwBwn4jpH+F:Yp+A7gB48XT8kPu4y+vBBJJtMQ/k+Ftype: PE32 executable (GUI) Intel 80386, for MS WindowsVersion Info:
LegalCopyright: Copyright (C) 2010InternalName: Flash Memory ToolkitFileVersion: 2.0.0.0ProductName: Flash Memory Toolkit ApplicationProductVersion: 2.0.0.0FileDescription: Flash Memory Toolkit exeOriginalFilename: FlashMemoryToolkit.EXETranslation: 0x0409 0x04b0
Trojan:Win32/Sopinar.F!bit also known as:
| GridinSoft | Trojan.Ransom.Gen |
| Bkav | W32.AIDetect.malware1 |
| K7AntiVirus | Trojan ( 004f58b81 ) |
| Elastic | malicious (high confidence) |
| DrWeb | Trojan.PWS.Qadars.47 |
| Cynet | Malicious (score: 100) |
| CAT-QuickHeal | Trojan.Yakes |
| ALYac | Gen:Variant.Strictor.118336 |
| Cylance | Unsafe |
| Zillya | Trojan.Yakes.Win32.61180 |
| Sangfor | Trojan.Win32.Save.a |
| CrowdStrike | win/malicious_confidence_80% (D) |
| Alibaba | Trojan:Win32/Yakes.62014fa6 |
| K7GW | Trojan ( 004f58b81 ) |
| Cybereason | malicious.31fa72 |
| Cyren | W32/Trojan.SBSF-5950 |
| Symantec | Trojan Horse |
| ESET-NOD32 | Win32/Qadars.AZ |
| Zoner | Trojan.Win32.47197 |
| APEX | Malicious |
| Avast | Win32:Malware-gen |
| Kaspersky | Trojan.Win32.Yakes.rund |
| BitDefender | Gen:Variant.Strictor.118336 |
| NANO-Antivirus | Trojan.Win32.Yakes.eoprlw |
| ViRobot | Trojan.Win32.Yakes.282112 |
| MicroWorld-eScan | Gen:Variant.Strictor.118336 |
| Tencent | Win32.Trojan.Yakes.Pgwf |
| Ad-Aware | Gen:Variant.Strictor.118336 |
| Sophos | Mal/Kryptik-DC |
| Comodo | Malware@#2p0zfw6b2wis9 |
| BitDefenderTheta | Gen:NN.ZexaF.34050.ru0@aWD4P7mi |
| VIPRE | Trojan.Win32.Generic!BT |
| TrendMicro | Ransom_HPLOCKY.SME |
| McAfee-GW-Edition | Generic.aaf |
| FireEye | Generic.mg.b5c1c8c31fa729eb |
| Emsisoft | Gen:Variant.Strictor.118336 (B) |
| SentinelOne | Static AI – Malicious PE |
| Jiangmin | Trojan.Yakes.tlq |
| Webroot | W32.Trojan.Gen |
| Avira | TR/Crypt.XPACK.umxrj |
| eGambit | Unsafe.AI_Score_99% |
| Antiy-AVL | Trojan/Generic.ASSuf.1AC71 |
| Kingsoft | Win32.Troj.Yakes.ru.(kcloud) |
| Microsoft | Trojan:Win32/Sopinar.F!bit |
| Arcabit | Trojan.Strictor.D1CE40 |
| GData | Win32.Trojan.Agent.L66ODA |
| AhnLab-V3 | Trojan/Win32.Yakes.C1694286 |
| McAfee | Generic.aaf |
| MAX | malware (ai score=100) |
| VBA32 | BScope.Trojan.Yakes |
| Malwarebytes | Malware.AI.3902810538 |
| Panda | Trj/WLT.C |
| TrendMicro-HouseCall | Ransom_HPLOCKY.SME |
| Rising | Trojan.Win32.Sopinar.c (CLASSIC) |
| Yandex | Trojan.Yakes!fEQqyiYq/fI |
| Ikarus | Trojan-Ransom.GandCrab |
| Fortinet | W32/Yakes.RUND!tr |
| AVG | Win32:Malware-gen |
| Qihoo-360 | Win32/Botnet.Yakes.HwoCHvsA |
How to remove Trojan:Win32/Sopinar.F!bit ransomware?
Unwanted application has ofter come with other viruses and spyware. This threats can steal account credentials, or crypt your documents for ransom.
Reasons why I would recommend GridinSoft1
There is no better way to recognize, remove and prevent PC threats than to use an anti-malware software from GridinSoft2.
Download GridinSoft Anti-Malware.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your system.
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Trojan:Win32/Sopinar.F!bit files and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
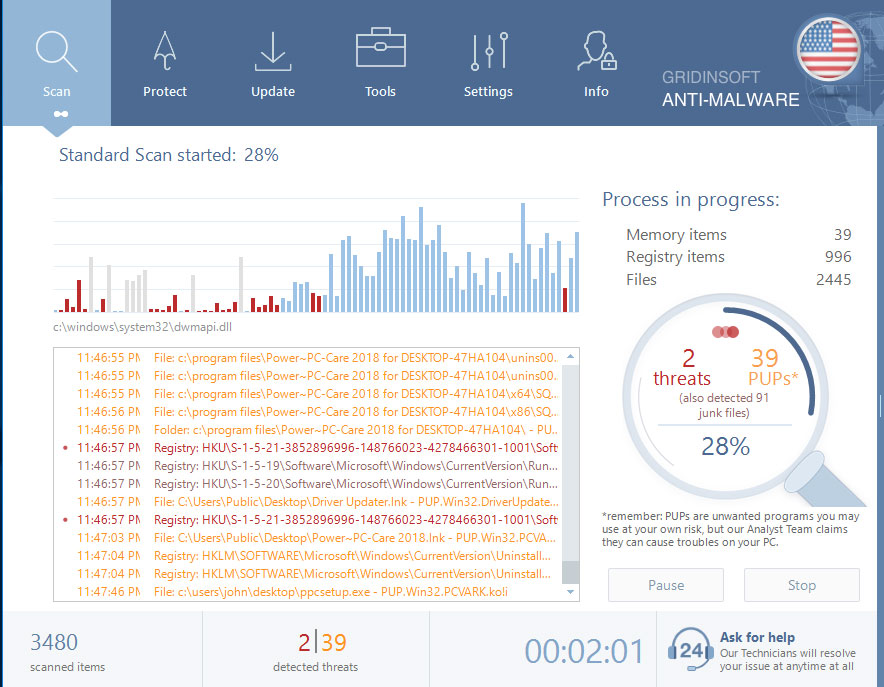
Click on “Clean Now”.
When the scan has finished, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
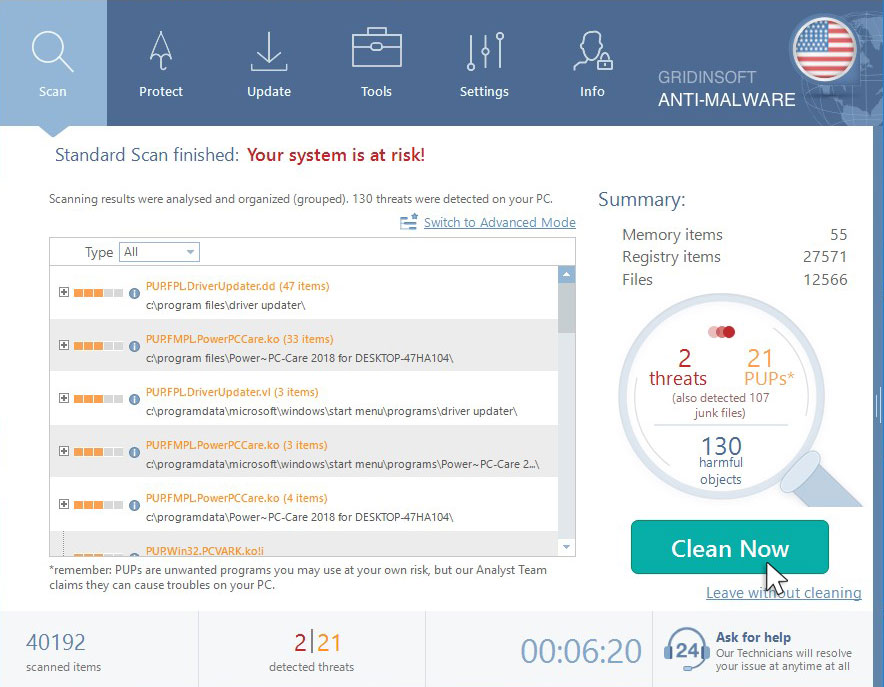
Are Your Protected?
GridinSoft Anti-Malware will scan and clean your PC for free in the trial period. The free version offer real-time protection for first 2 days. If you want to be fully protected at all times – I can recommended you to purchase a full version:
If the guide doesn’t help you to remove Trojan:Win32/Sopinar.F!bit you can always ask me in the comments for getting help.
User Review
( votes)References
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison