What is Trojan:Win32/Glupteba!ml infection?
In this article you will certainly find regarding the description of Trojan:Win32/Glupteba!ml as well as the negative effects it carries. This trojan virus aims on your network settings, web browser and hardware devices that are used to connect to the Internet.
Most of the cases, Trojan:Win32/Glupteba!ml virus makes significant changes in the victim’s browser configuration, also changes the networking settings, and may be used to take control of the router used to get access to the internet.
Trojan:Win32/Glupteba!ml Summary
That virus can correctly be classified as stealer trojan. After the injection into your system, it makes changes in your networking settings, specifically – in HOSTS file. Next step it does is router hijacking. Glupteba virus takes control over your router, getting control of the whole traffic you have, and packing it into log files. Then, it sends these logs to the command server, where malware distributors can check it. Such logs can contain the information about your network activity, passwords you typed after the virus injection, online banking logs, and various other valuable information.
Besides overhearing the traffic, the Trojan:Win32/Glupteba!ml is also able to steal the data from the specific files of your web browsers. Various browsers keep the passwords and other secret information in the certain files. Of course, the information in those files is encrypted. The problem is that old versions of Opera, as well as some amateur web browsing tools on Chromium core use a very easy encryption algorithm. Fraudsters can easily decrypt these files and get your login credentials with no problems.
Similar behavior
Related domains
| z.whorecord.xyz | Trojan.Ransom.Stop |
| a.tomx.xyz | Trojan.Ransom.Stop |
| api.2ip.ua | Trojan.Ransom.Stop |
| xopq.top | Trojan.Ransom.Stop |
Trojan:Win32/Glupteba!ml
The most regular channels whereby Trojan:Win32/Glupteba!ml are injected are:
- Via email spamming
- Through malvertising
- With unlicensed software usage, software bundling
Email spamming became a viral malware distribution method since the users do not raise suspicion on notifications from DHL or Amazon about the incoming delivery. However, it is quite easy to distinguish the malevolent email from the original one. One which is sent by cybercriminals has a strange sender address – something like [email protected]. Simultaneously, the original email address has a specific domain name (@amazon.com or @dhl.us) and can also be checked on the official website in the “Contact us” tab.
Malicious advertisements on the web, however, is an old-timer of malware distribution. And the advice to stop clicking the blinking advertisements on untrustworthy websites exists as long as the ads on the Internet. You can also install ad-blocking plugins for your web browser – they will deal with any ads. However, if they are generated by adware already present on your PC, ad blockers will be useless.
Software bundling is a widespread practice among the virus developers. Users who hack the programs to make them usable without purchasing a license approve any offer to include another program in the pack because they are gaining money in such away. Check precisely the installation window for signs like “Advanced installation settings” or so. The ability to switch off the malware installation often hides under such items.
Trojan:Win32/Glupteba!ml visible effects
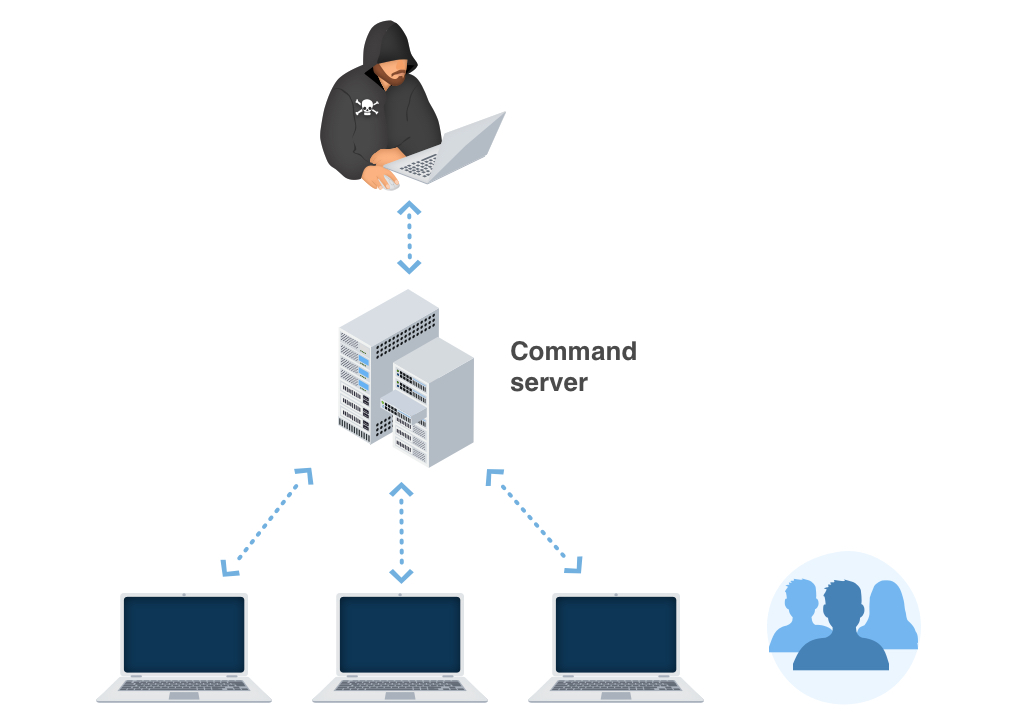
When the Trojan:Win32/Glupteba!ml virus is running, you can see the following visual signs of its activity:
- Browser search engine change
- Search queries redirection
- Freezes after the attempt to open the Settings tab
- Troubles with connecting to random websites
- Router rebooting without your intention
- Problems with connecting to Internet through Wi-Fi network established with your router
- Suspicious activity on your social network accounts
Technical details
File Info:
crc32: 6188AA43md5: 60d22219b7aad6ad3a43f68cd18602f0name: 60D22219B7AAD6AD3A43F68CD18602F0.mlwsha1: e0c84d0292089a7f5c86f10691b13e024fa22bacsha256: 5bf1d3cc2e187ff1dec1c4291b09869c8ac02712ea26c25d22674c14174d7b81sha512: b1a85a929f15829bd42a996817459cdb433b0f4e3288af028a59108e35a3295c14d5d0e1f00661c142b58cfc3a10b389721e239136aec64b90761bdbfc7f2ee6ssdeep: 12288:3dAdfKOWxLQNKXx1LMO2ejHU6Fh+LRAgED8Z6fbDd0u2n2qPaBiJUYHI5S:3TOWxLlrLMO2sHU6bACgED84fbDa/nEtype: PE32 executable (GUI) Intel 80386, for MS WindowsVersion Info:
Translations: 0x0147 0x01ed
Trojan:Win32/Glupteba!ml also known as:
| GridinSoft | Trojan.Ransom.Gen |
| Bkav | W32.CridexAgentPU.Trojan |
| Elastic | malicious (high confidence) |
| MicroWorld-eScan | Gen:Heur.Mint.Titirez.1.31 |
| McAfee | Trojan-FSWW!60D22219B7AA |
| Cylance | Unsafe |
| Sangfor | Malware |
| K7AntiVirus | Trojan ( 005720661 ) |
| BitDefender | Gen:Heur.Mint.Titirez.1.31 |
| K7GW | Trojan ( 005720661 ) |
| CrowdStrike | win/malicious_confidence_100% (D) |
| TrendMicro | TROJ_GEN.R002C0PKF20 |
| Cyren | W32/Kryptik.CGZ.gen!Eldorado |
| Symantec | ML.Attribute.HighConfidence |
| APEX | Malicious |
| ClamAV | Win.Packed.Generickdz-9785960-0 |
| Kaspersky | HEUR:Trojan.Win32.Zenpak.vho |
| Alibaba | Trojan:Win32/Zenpak.dcce3cc6 |
| ViRobot | Trojan.Win32.Z.Mint.742912 |
| Rising | Malware.Obscure/Heur!1.9E03 (CLASSIC) |
| Ad-Aware | Gen:Heur.Mint.Titirez.1.31 |
| Emsisoft | Trojan.Crypt (A) |
| Comodo | Malware@#3ek6h296znh90 |
| F-Secure | Heuristic.HEUR/AGEN.1131109 |
| DrWeb | Trojan.DownLoader35.9382 |
| VIPRE | Trojan.Win32.Generic!BT |
| Invincea | Mal/Generic-S |
| McAfee-GW-Edition | BehavesLike.Win32.Emotet.bc |
| FireEye | Generic.mg.60d22219b7aad6ad |
| Sophos | Mal/Generic-S |
| Ikarus | Trojan-Downloader.Win32.Zurgop |
| GData | Gen:Heur.Mint.Titirez.1.31 |
| Jiangmin | Trojan.Stop.fv |
| MaxSecure | Trojan.Malware.300983.susgen |
| Avira | HEUR/AGEN.1131109 |
| MAX | malware (ai score=86) |
| Gridinsoft | Trojan.Win32.Packed.oa |
| Arcabit | Trojan.Mint.Titirez.1.31 |
| ZoneAlarm | HEUR:Trojan.Win32.Zenpak.vho |
| Microsoft | Trojan:Win32/Glupteba!ml |
| Cynet | Malicious (score: 100) |
| AhnLab-V3 | Trojan/Win32.Glupteba.R354440 |
| Acronis | suspicious |
| BitDefenderTheta | Gen:NN.ZexaF.34634.TqW@amYvNKQG |
| ALYac | Trojan.Ransom.Stop |
| Malwarebytes | Trojan.MalPack |
| Panda | Trj/GdSda.A |
| ESET-NOD32 | a variant of Win32/Kryptik.HHCC |
| TrendMicro-HouseCall | TROJ_GEN.R002C0PKF20 |
| Tencent | Malware.Win32.Gencirc.11b1003c |
| SentinelOne | Static AI – Malicious PE |
| eGambit | Unsafe.AI_Score_92% |
| Fortinet | W32/Kryptik.HHGA!tr |
| AVG | Win32:TrojanX-gen [Trj] |
| Avast | Win32:TrojanX-gen [Trj] |
| Qihoo-360 | Win32/Trojan.0ea |
How to remove Trojan:Win32/Glupteba!ml virus?
Unwanted application has ofter come with other viruses and spyware. This threats can steal account credentials, or crypt your documents for ransom.
Reasons why I would recommend GridinSoft1
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes.2.
Download GridinSoft Anti-Malware.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When the setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your system.
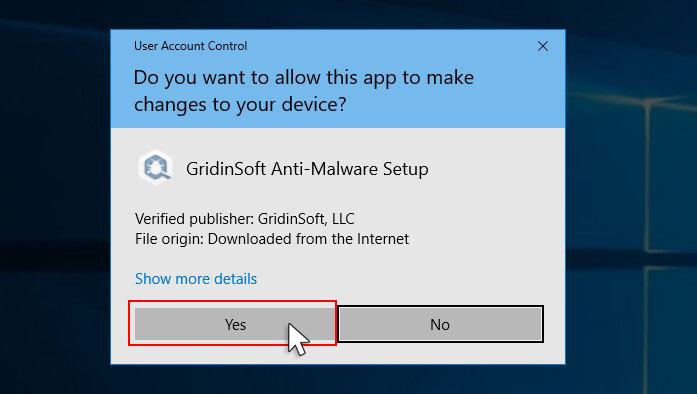
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

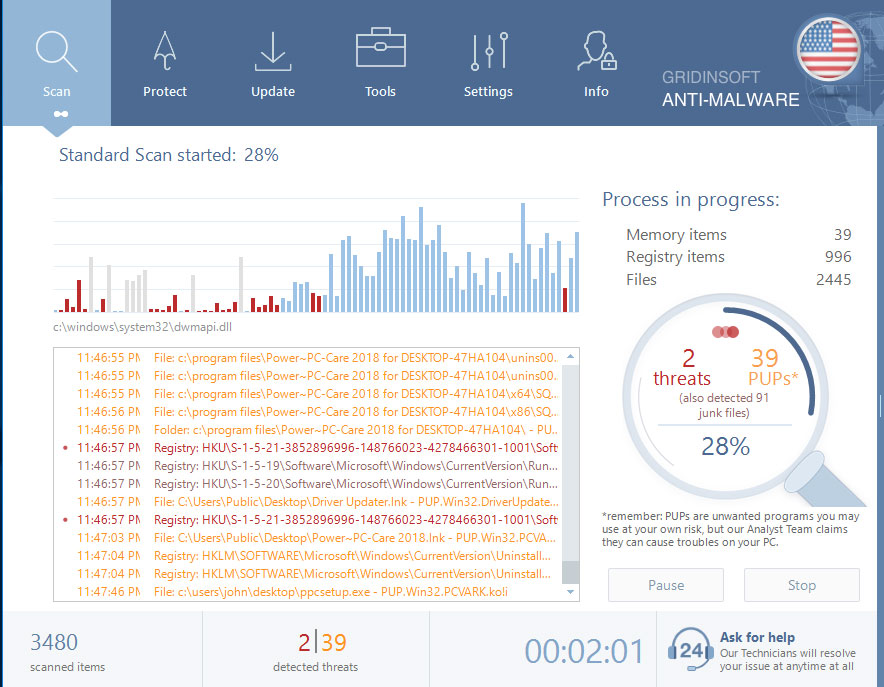
Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Trojan:Win32/Glupteba!ml files and other malicious programs. This process can take 20-30 minutes, so I suggest you periodically check on the status of the scan process.
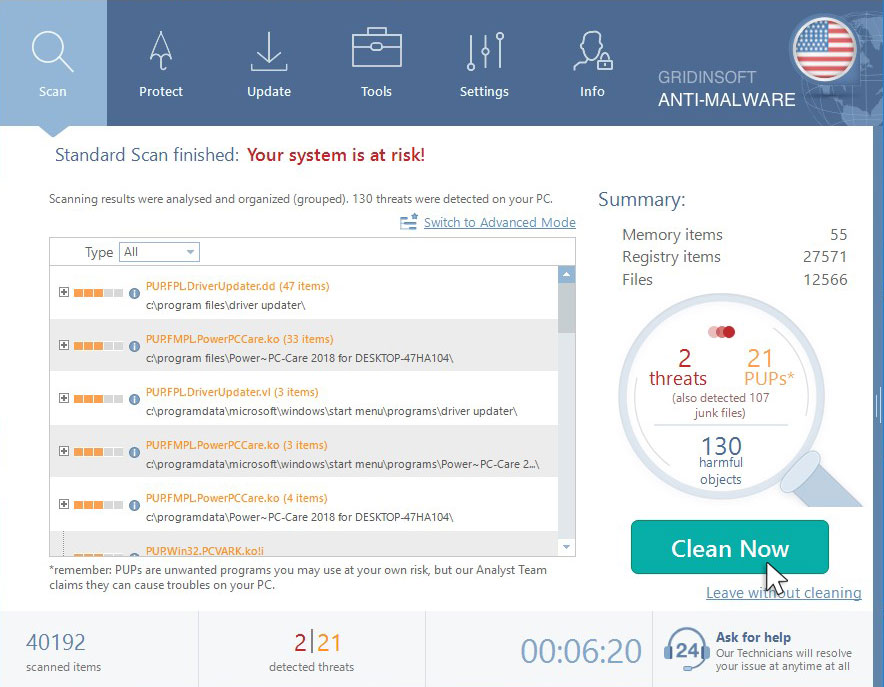
Click on “Clean Now”.
When the scan has finished, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in the right corner.
Are Your Protected?
GridinSoft Anti-Malware will scan and clean your PC for free in the trial period. The free version offer real-time protection for first 2 days. If you want to be fully protected at all times – I can recommended you to purchase a full version:
If the guide doesn’t help you remove Trojan:Win32/Glupteba!ml, you can always ask me in the comments to get help.
User Review
( votes)References
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison