Phonzy.C!ml
Trojan:Script/Phonzy.C!ml is a highly dangerous malware that poses significant risks to your computer’s security. Once infiltrated, Phonzy.C!ml can execute a range of harmful actions, including data theft and unauthorized session tracking. Phonzy Trojan has the potential to compromise your privacy and compromise the integrity of your system.
If your system detects the Trojan:Script/Phonzy.C!ml, it is a clear indication of trouble. Phonzy and other malware of its kind pose a significant threat as they can exploit your computer, allowing for the injection of additional malware. Phonzy.C!ml specifically belongs to the category of Downloader Trojans, which are designed to download and install malicious software onto the infected system.
Downloader Trojans, including the Trojan:Script/Phonzy.C!ml, aim to silently infiltrate your system and facilitate the injection of additional malware. When this particular Trojan is present, it puts you at risk of being exposed to various forms of malware, such as spyware or even ransomware. It is crucial to take immediate action to remove this threat from your system to safeguard your data and prevent further infections.
Malware, without exception, is designed with a single objective – to generate profits at your expense. The individuals behind these malicious entities are driven solely by their own gain and employ various tactics to achieve it. They exploit your private data, generate revenue through the ads you are exposed to, and exploit your computer’s resources, such as CPU and GPU, for cryptocurrency mining and other illicit activities. Clearly, becoming a means for their profits is not a choice anyone would willingly make. It is important to remain vigilant and take necessary measures to protect yourself against these threats.
What does the pop-up with Trojan:Script/Phonzy.C!ml detection mean?
Microsoft Defender presents the detection of Trojan:Script/Phonzy.C!ml in the lower right corner. This notification is displayed by Microsoft Defender, an anti-malware application that performs decent scans but tends to be generally unstable. Although it lacks protection against malware invasions and has a glitchy interface and faulty malware removal features, the pop-up related to Phonzy simply indicates that Defender has detected the malware. To remove it, you will likely need to utilize a separate anti-malware program.
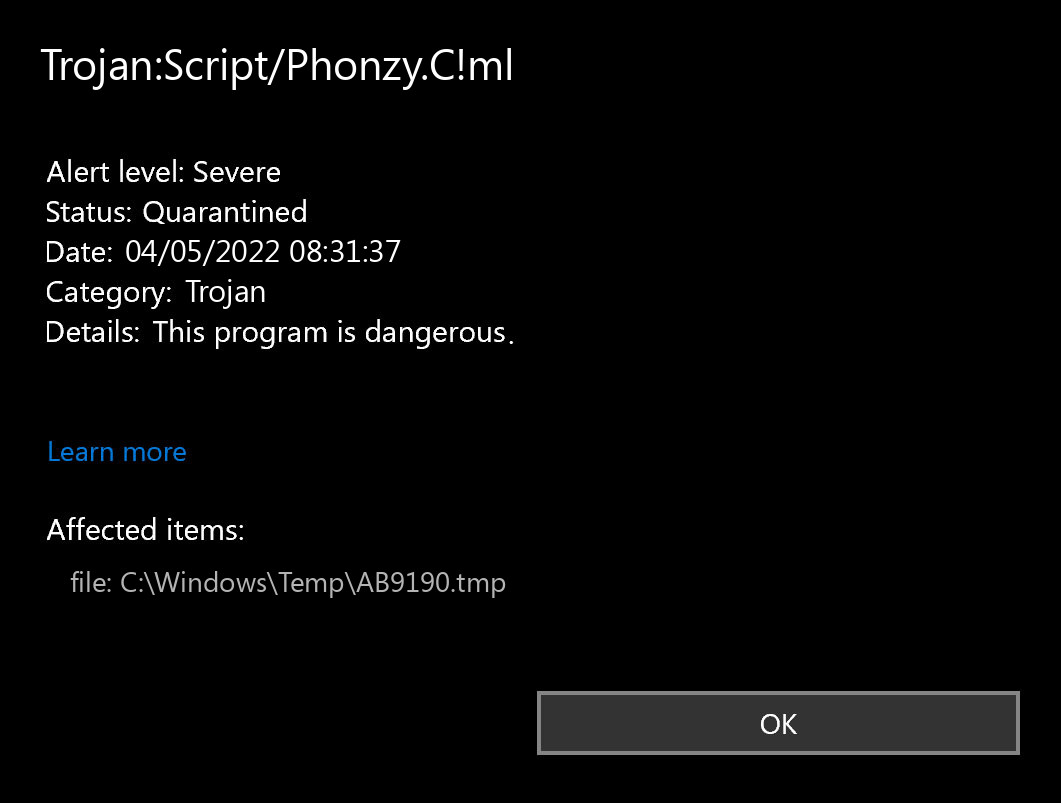
Trojan.Script/Phonzy.C!ml detection
The Trojan:Script/Phonzy.C!ml virus is highly undesirable. It infiltrates your system under the guise of something benign or as part of a program downloaded from a forum. Once inside, it actively weakens your system and ultimately injects other viruses desired by the criminals controlling this particular malware. Consequently, predicting the exact effects of Phonzy’s actions is likely impossible. The unpredictability associated with malware makes it advisable to intervene promptly and prevent the malware from fulfilling its malicious tasks.
Threat Summary:
| Name | Phonzy Trojan |
| Detection | Trojan:Script/Phonzy.C!ml |
| Details | Phonzy tool that looks legitimate but can take control of your computer. |
Technical details
Trojan:Script/Phonzy.C!ml also known as:
Is Trojan:Script/Phonzy.C!ml dangerous?
As I have mentioned before, non-harmful malware does not exist. And Trojan:Script/Phonzy.C!ml is no exception. This malware modifies the system setups and alters the Group Policies and Windows registry. All of these components are vital for proper system operation, even in cases when we are not talking about system safety. Therefore, the malware that Phonzy contains, or which it will download later, will squeeze out maximum revenue from you. Cybercriminals can grab your data and then sell it on the black market. Using adware and browser hijacker functionality, built-in Trojan:Script/Phonzy.C!ml virus, they can make a profit by showing you the banners. Each view gives them a penny, but 100 views per day = $1. 1000 victims who watch 100 banners daily – $1000. Easy math, but sad conclusions. It is a bad choice to be a donkey for crooks.
How did I get this virus?
It is difficult to trace malware’s origins on your computer. Nowadays, things are mixed, and spreading ways chosen by adware five years ago can be utilized by spyware nowadays. However, if we abstract from the exact spreading way and will think about why it has success, the reply will be very uncomplicated – low level of cybersecurity understanding. People click on promotions on weird sites, open the pop-ups they receive in their browsers, and call “Microsoft tech support”, believing that the odd banner that says about malware is true. It is very important to understand what is legitimate – to prevent misunderstandings when attempting to identify a virus.
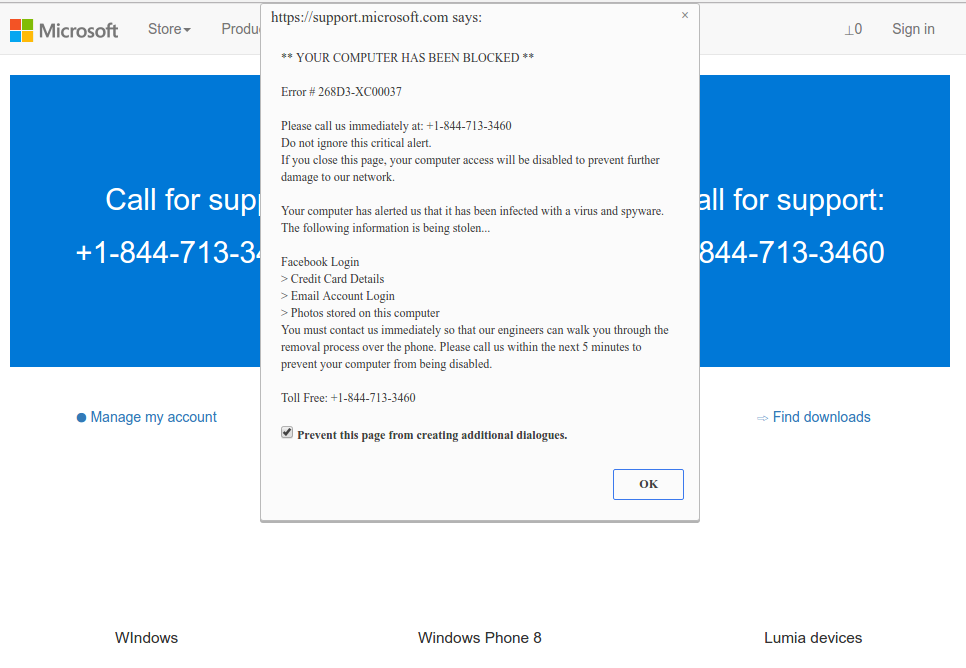
Microsoft Tech Support Scam
Nowadays, there are two of the most common tactics of malware spreading – lure emails and injection into a hacked program. While the first one is not so easy to evade – you must know a lot to understand a counterfeit – the 2nd one is easy to handle: do not use hacked programs. Torrent trackers and various other providers of “totally free” applications (which are, actually, paid, but with a disabled license checking) are a giveaway point of malware. And Trojan:Script/Phonzy.C!ml is just one of them.
How to remove the Trojan:Script/Phonzy.C!ml from my PC?
Trojan:Script/Phonzy.C!ml malware is tough to erase manually. It places its documents throughout the disk and can recover itself from one of the elements. Moreover, various changes in the registry, networking configurations and Group Policies are hard to discover and return to the initial. It is much better to use a special program – exactly, an anti-malware app. GridinSoft Anti-Malware will fit the best for malware removal goals.
Why GridinSoft Anti-Malware? It is lightweight and has its detection databases updated practically every hour. In addition, it does not have such bugs and weaknesses as Microsoft Defender does. The combination of these facts makes GridinSoft Anti-Malware ideal for getting rid of malware of any form.
Remove the viruses with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored and the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of Phonzy, the default option is “Delete”. Press “Apply” to finish the malware removal.




