Security professionals have been aware about the Smominru botnet (aka MyKings, WannaMine or Hexmen) since 2017, and in 2018 many companies conducted a detailed analysis of this threat. However, this did not stop the malware and it infected 90 thousand devices only in August 2019.
Recalling, in 2018 the botnet totaled more than 520,000 machines, and its operators at that time “earned” 8900 Monero (about $2 million at the exchange rate at the time of publication of the reports).“Smominru is notable for the fact that it used not only the RDP, MSSQL, Telnet and other open services bruteforce, but also the exploits of EternalBlue (CVE-2017-0144) and EsteemAudit (CVE-2017-0176), aimed against vulnerable Windows machines”, – citing the report from Securityweek correspondent Ionut Arghire.
The names of these exploits are well-known not only to information security specialists, but even to ordinary users, since it was EternalBlue that was used in the spring of 2017 to distribute the sensational WannaCry ransomware.
According to a new report released this week by Guardicore Labs, the botnet is still active at this time: in August 2019 alone, 90,000 machines became its victims (4,700 new infections per day). Worse, approximately 25% of compromised devices were re-infected more than once, that is, the machines were not properly patched and protected after being cleaned from infection.
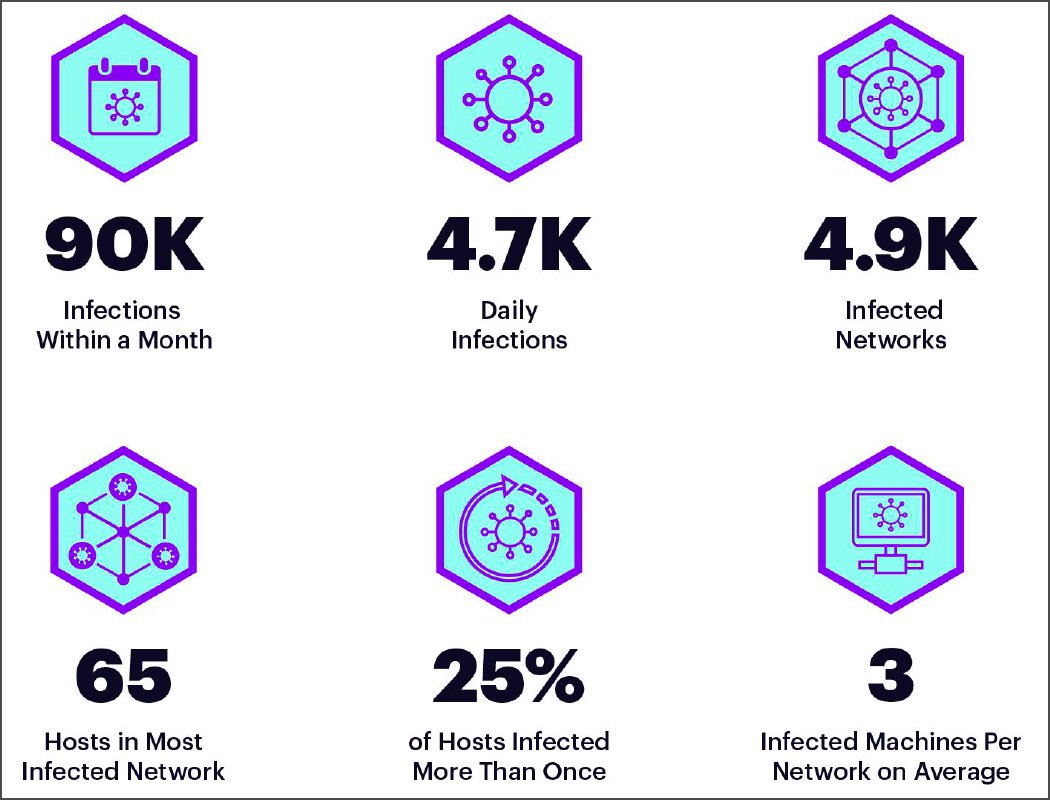
Stats by Guardicore Labs
As soon as Smominru gains access to the target machine, it tries to remove the competing malware, protect the system from further infections, and then installs mining malware, steals login credentials, installs backdoors and seeks to spread to other machines on the same network as a worm.
Most infected operating systems are Windows 7 and Windows Server 2008 (a total of 85% of all infections), which are still vulnerable to attacks using EternalBlue. Also attacked were Windows Server 2012, Windows XP, and Windows Server 2003.
Read also: Trojan Saefko compiles a victim’s profile and can spread via USB devices
China, Taiwan, Russia, Brazil, and the United States suffered most from Smominru attacks. Among the victims, researchers found American universities, medical firms and companies engaged in cybersecurity.
The current version of Malvari uses a huge collection of payloads during the attack.
“The Smominru group tends to use a large collection of payloads throughout the attack. In its current iteration, Smominru downloads and runs almost twenty distinct scripts and binary payloads”, – the researchers note.
Researchers also point out that the infrastructure of botnet operators includes more than 20 servers, each of which serves several files, and each file refers to another 2-3 additional servers. In addition, many files are hosted on multiple servers, which increases the flexibility and resilience of the infrastructure.
Mitigation:
The spreading of Smominru is heavily based on weak passwords, but it also relies on the existence of EternalBlue vulnerable machines. Unpatched systems allow the campaign to infect countless machines worldwide and propagate inside internal networks. Thus, it is crucial that operating systems be aligned with the currently-available software updates.

